Wireshark protocol analyzer
•
0 likes•1,994 views
Wireshark is an open source packet analyzer software that captures network packets and displays detailed protocol information to help network administrators troubleshoot problems, security engineers examine security issues, and developers debug protocols. The document provides step-by-step instructions on downloading, installing, and using Wireshark to capture packets from a network interface and find specific packet information.
Report
Share
Report
Share
Download to read offline
Recommended
Firewalls And its types in cyber security

The above document includes brief description about the Firewalls in Cyber Security.
Firewall and its Types

The slide show is about the Firewall , why we need firewall , its advantages, disadvantage and is common types - packet-filter firewall and proxy firewall .its working and advantages and didadvantages.
Recommended
Firewalls And its types in cyber security

The above document includes brief description about the Firewalls in Cyber Security.
Firewall and its Types

The slide show is about the Firewall , why we need firewall , its advantages, disadvantage and is common types - packet-filter firewall and proxy firewall .its working and advantages and didadvantages.
Wireshark network analysing software

it is a PPT on cyber security. one software Wireshark witch is use for the analyse the network protocols or packages.
Report on forensics tools

Report contains 3 tools as DEFT operating system, ClamTK Antivirus, pdfCracker.
VPN Monitoring Security Use Case Guide version 1.1 

VPN Monitoring Security Use Case Guide version 1.1
Anomalous Traffic Detection Security Use Case Guide 

Anomalous Traffic Detection Security Use Case Guide
Suspicious Outbound Traffic Monitoring Security Use Case Guide 

Suspicious Outbound Traffic Monitoring Security Use Case Guide
Two-For-One Talk: Malware Analysis for Everyone

Two short talks in one deck. One on automated analysis tools for the novice. The second on reverse engineering malicious PDF files.
OSTU - Quickstart Guide for Wireshark (by Tony Fortunato)

Tony Fortunato is a Senior Network Specialist with experience in design, implementation, and troubleshooting of LAN/WAN/Wireless networks, desktops and servers since 1989. His background in financial networks includes design and implementation of trading floor networks. Tony has taught at local high schools, Colleges/Universities, Networld/Interop and many onsite private classroom settings to thousands of analysts.
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

The publishing industry has been selling digital audiobooks and ebooks for over a decade and has found its groove. What’s changed? What has stayed the same? Where do we go from here? Join a group of leading sales peers from across the industry for a conversation about the lessons learned since the popularization of digital books, best practices, digital book supply chain management, and more.
Link to video recording: https://bnctechforum.ca/sessions/selling-digital-books-in-2024-insights-from-industry-leaders/
Presented by BookNet Canada on May 28, 2024, with support from the Department of Canadian Heritage.
Uni Systems Copilot event_05062024_C.Vlachos.pdf

Unlocking Productivity: Leveraging the Potential of Copilot in Microsoft 365, a presentation by Christoforos Vlachos, Senior Solutions Manager – Modern Workplace, Uni Systems
More Related Content
Similar to Wireshark protocol analyzer
Wireshark network analysing software

it is a PPT on cyber security. one software Wireshark witch is use for the analyse the network protocols or packages.
Report on forensics tools

Report contains 3 tools as DEFT operating system, ClamTK Antivirus, pdfCracker.
VPN Monitoring Security Use Case Guide version 1.1 

VPN Monitoring Security Use Case Guide version 1.1
Anomalous Traffic Detection Security Use Case Guide 

Anomalous Traffic Detection Security Use Case Guide
Suspicious Outbound Traffic Monitoring Security Use Case Guide 

Suspicious Outbound Traffic Monitoring Security Use Case Guide
Two-For-One Talk: Malware Analysis for Everyone

Two short talks in one deck. One on automated analysis tools for the novice. The second on reverse engineering malicious PDF files.
OSTU - Quickstart Guide for Wireshark (by Tony Fortunato)

Tony Fortunato is a Senior Network Specialist with experience in design, implementation, and troubleshooting of LAN/WAN/Wireless networks, desktops and servers since 1989. His background in financial networks includes design and implementation of trading floor networks. Tony has taught at local high schools, Colleges/Universities, Networld/Interop and many onsite private classroom settings to thousands of analysts.
Similar to Wireshark protocol analyzer (20)
VPN Monitoring Security Use Case Guide version 1.1 

VPN Monitoring Security Use Case Guide version 1.1
Anomalous Traffic Detection Security Use Case Guide 

Anomalous Traffic Detection Security Use Case Guide
Suspicious Outbound Traffic Monitoring Security Use Case Guide 

Suspicious Outbound Traffic Monitoring Security Use Case Guide
OSTU - Quickstart Guide for Wireshark (by Tony Fortunato)

OSTU - Quickstart Guide for Wireshark (by Tony Fortunato)
Recently uploaded
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

The publishing industry has been selling digital audiobooks and ebooks for over a decade and has found its groove. What’s changed? What has stayed the same? Where do we go from here? Join a group of leading sales peers from across the industry for a conversation about the lessons learned since the popularization of digital books, best practices, digital book supply chain management, and more.
Link to video recording: https://bnctechforum.ca/sessions/selling-digital-books-in-2024-insights-from-industry-leaders/
Presented by BookNet Canada on May 28, 2024, with support from the Department of Canadian Heritage.
Uni Systems Copilot event_05062024_C.Vlachos.pdf

Unlocking Productivity: Leveraging the Potential of Copilot in Microsoft 365, a presentation by Christoforos Vlachos, Senior Solutions Manager – Modern Workplace, Uni Systems
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

Neha Bajwa, Vice President of Product Marketing, Neo4j
Join us as we explore breakthrough innovations enabled by interconnected data and AI. Discover firsthand how organizations use relationships in data to uncover contextual insights and solve our most pressing challenges – from optimizing supply chains, detecting fraud, and improving customer experiences to accelerating drug discoveries.
Pushing the limits of ePRTC: 100ns holdover for 100 days

At WSTS 2024, Alon Stern explored the topic of parametric holdover and explained how recent research findings can be implemented in real-world PNT networks to achieve 100 nanoseconds of accuracy for up to 100 days.
GridMate - End to end testing is a critical piece to ensure quality and avoid...

End to end testing is a critical piece to ensure quality and avoid regressions. In this session, we share our journey building an E2E testing pipeline for GridMate components (LWC and Aura) using Cypress, JSForce, FakerJS…
Elizabeth Buie - Older adults: Are we really designing for our future selves?

Elizabeth Buie - Older adults: Are we really designing for our future selves?
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Monitoring and observability aren’t traditionally found in software curriculums and many of us cobble this knowledge together from whatever vendor or ecosystem we were first introduced to and whatever is a part of your current company’s observability stack.
While the dev and ops silo continues to crumble….many organizations still relegate monitoring & observability as the purview of ops, infra and SRE teams. This is a mistake - achieving a highly observable system requires collaboration up and down the stack.
I, a former op, would like to extend an invitation to all application developers to join the observability party will share these foundational concepts to build on:
Microsoft - Power Platform_G.Aspiotis.pdf

Revolutionizing Application Development
with AI-powered low-code, presentation by George Aspiotis, Sr. Partner Development Manager, Microsoft
Generative AI Deep Dive: Advancing from Proof of Concept to Production

Join Maher Hanafi, VP of Engineering at Betterworks, in this new session where he'll share a practical framework to transform Gen AI prototypes into impactful products! He'll delve into the complexities of data collection and management, model selection and optimization, and ensuring security, scalability, and responsible use.
Communications Mining Series - Zero to Hero - Session 1

This session provides introduction to UiPath Communication Mining, importance and platform overview. You will acquire a good understand of the phases in Communication Mining as we go over the platform with you. Topics covered:
• Communication Mining Overview
• Why is it important?
• How can it help today’s business and the benefits
• Phases in Communication Mining
• Demo on Platform overview
• Q/A
UiPath Test Automation using UiPath Test Suite series, part 5

Welcome to UiPath Test Automation using UiPath Test Suite series part 5. In this session, we will cover CI/CD with devops.
Topics covered:
CI/CD with in UiPath
End-to-end overview of CI/CD pipeline with Azure devops
Speaker:
Lyndsey Byblow, Test Suite Sales Engineer @ UiPath, Inc.
By Design, not by Accident - Agile Venture Bolzano 2024

As presented at the Agile Venture Bolzano, 4.06.2024
SAP Sapphire 2024 - ASUG301 building better apps with SAP Fiori.pdf

Building better applications for business users with SAP Fiori.
• What is SAP Fiori and why it matters to you
• How a better user experience drives measurable business benefits
• How to get started with SAP Fiori today
• How SAP Fiori elements accelerates application development
• How SAP Build Code includes SAP Fiori tools and other generative artificial intelligence capabilities
• How SAP Fiori paves the way for using AI in SAP apps
GraphRAG is All You need? LLM & Knowledge Graph

Guy Korland, CEO and Co-founder of FalkorDB, will review two articles on the integration of language models with knowledge graphs.
1. Unifying Large Language Models and Knowledge Graphs: A Roadmap.
https://arxiv.org/abs/2306.08302
2. Microsoft Research's GraphRAG paper and a review paper on various uses of knowledge graphs:
https://www.microsoft.com/en-us/research/blog/graphrag-unlocking-llm-discovery-on-narrative-private-data/
20240607 QFM018 Elixir Reading List May 2024

Everything I found interesting about the Elixir programming ecosystem in May 2024
Securing your Kubernetes cluster_ a step-by-step guide to success !

Today, after several years of existence, an extremely active community and an ultra-dynamic ecosystem, Kubernetes has established itself as the de facto standard in container orchestration. Thanks to a wide range of managed services, it has never been so easy to set up a ready-to-use Kubernetes cluster.
However, this ease of use means that the subject of security in Kubernetes is often left for later, or even neglected. This exposes companies to significant risks.
In this talk, I'll show you step-by-step how to secure your Kubernetes cluster for greater peace of mind and reliability.
GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...

Leonard Jayamohan, Partner & Generative AI Lead, Deloitte
This keynote will reveal how Deloitte leverages Neo4j’s graph power for groundbreaking digital twin solutions, achieving a staggering 100x performance boost. Discover the essential role knowledge graphs play in successful generative AI implementations. Plus, get an exclusive look at an innovative Neo4j + Generative AI solution Deloitte is developing in-house.
Recently uploaded (20)
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

Transcript: Selling digital books in 2024: Insights from industry leaders - T...
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024
Pushing the limits of ePRTC: 100ns holdover for 100 days

Pushing the limits of ePRTC: 100ns holdover for 100 days
GridMate - End to end testing is a critical piece to ensure quality and avoid...

GridMate - End to end testing is a critical piece to ensure quality and avoid...
Elizabeth Buie - Older adults: Are we really designing for our future selves?

Elizabeth Buie - Older adults: Are we really designing for our future selves?
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf
Generative AI Deep Dive: Advancing from Proof of Concept to Production

Generative AI Deep Dive: Advancing from Proof of Concept to Production
Communications Mining Series - Zero to Hero - Session 1

Communications Mining Series - Zero to Hero - Session 1
FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf

FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf
UiPath Test Automation using UiPath Test Suite series, part 5

UiPath Test Automation using UiPath Test Suite series, part 5
Free Complete Python - A step towards Data Science

Free Complete Python - A step towards Data Science
Monitoring Java Application Security with JDK Tools and JFR Events

Monitoring Java Application Security with JDK Tools and JFR Events
By Design, not by Accident - Agile Venture Bolzano 2024

By Design, not by Accident - Agile Venture Bolzano 2024
SAP Sapphire 2024 - ASUG301 building better apps with SAP Fiori.pdf

SAP Sapphire 2024 - ASUG301 building better apps with SAP Fiori.pdf
Securing your Kubernetes cluster_ a step-by-step guide to success !

Securing your Kubernetes cluster_ a step-by-step guide to success !
GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...

GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...
Wireshark protocol analyzer
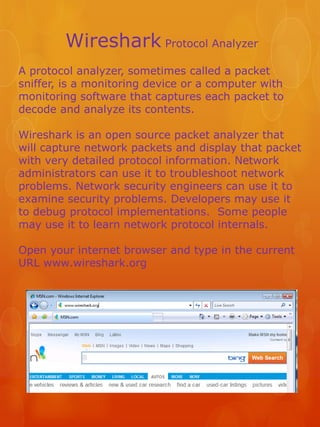
- 1. Wireshark Protocol Analyzer A protocol analyzer, sometimes called a packet sniffer, is a monitoring device or a computer with monitoring software that captures each packet to decode and analyze its contents. Wireshark is an open source packet analyzer that will capture network packets and display that packet with very detailed protocol information. Network administrators can use it to troubleshoot network problems. Network security engineers can use it to examine security problems. Developers may use it to debug protocol implementations. Some people may use it to learn network protocol internals. Open your internet browser and type in the current URL www.wireshark.org
- 2. Click on Download Wireshark.
- 3. Click on Windows Installer (32 bit). Click on Save.
- 4. In the Save As dialog box, click Save to a location such as your desktop. Wait for the file to download.
- 5. After Download Complete appears, click Run. In the IE Security Warning window, click Run.
- 6. In the User Account Control window, click Allow. Close this window.
- 7. Click Next. Click I Agree.
- 8. Click Next. Click Next.
- 9. Choose your install location, click Next. Click Install.
- 11. Click I Agree. Click Next.
- 13. Place a checkmark next to Run Wireshark 1.8.0 (32-bit) then click Finish. Click the Capture menu, and select Interfaces.
- 14. Put a check in this box. Click Start. You will now see packets captured.
- 15. You can view usernames, passwords, and other information using Wireshark. Open an internet browser and enter the URL www.yahoo.com then search for the word treasure. Return to Wireshark and Click Edit and Find Packet
- 16. Click String, after Filter enter Treasure, click Find. Treasure is found on a page that was just visited.
- 17. Double-click on the highlighted packet for more information. Click the capture menu and select Stop.