This document provides an introduction to 4G integrated WiMAX technology. It discusses key topics such as:
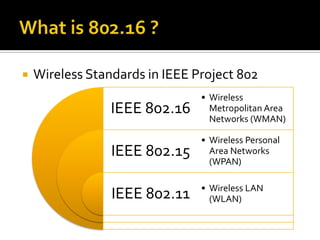
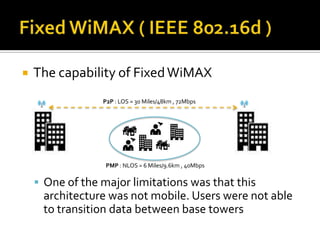
- What WiMAX is and the IEEE 802.16 standards that define it. WiMAX aims to provide long-distance wireless broadband similar to cellular networks.
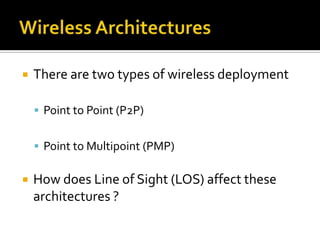
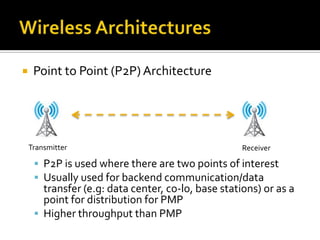
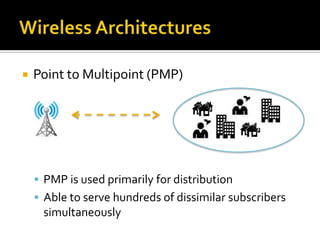
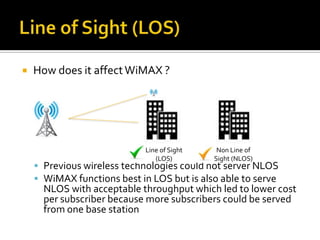
- The different WiMAX architectures including point-to-point and point-to-multipoint configurations. It also discusses how line of sight affects deployments.
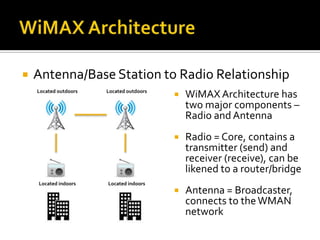
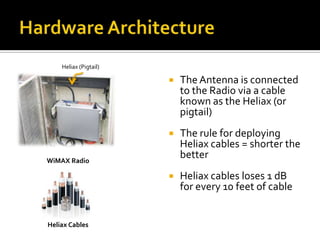
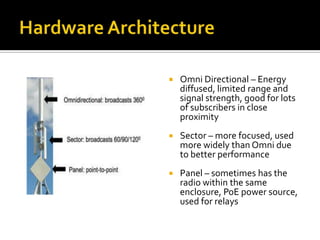
- Hardware considerations for WiMAX including antennas, radios, cables, and subscriber equipment.
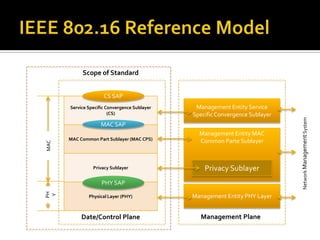
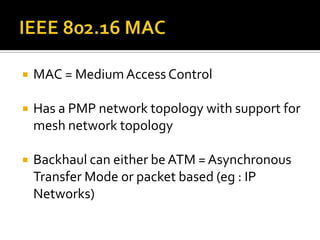
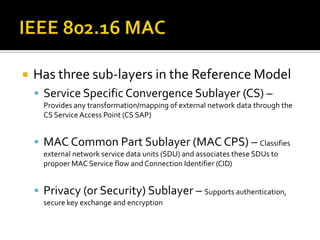
- The network architecture with the IEEE 802.16 reference model and details on the MAC layer and handover procedures for mobility.
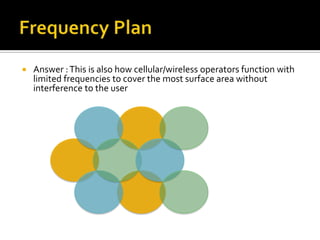
- Frequency planning challenges when deploying multiple