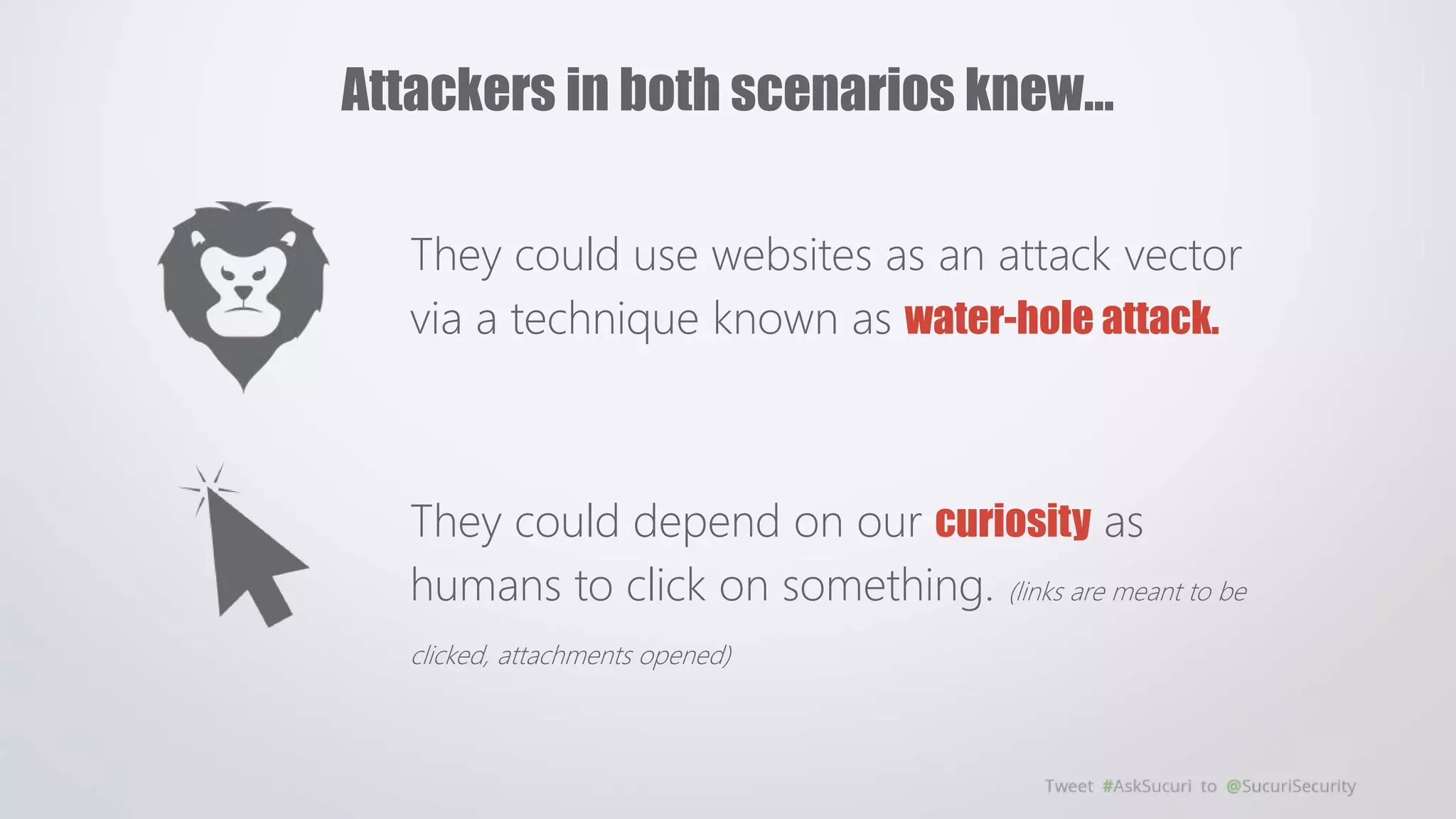
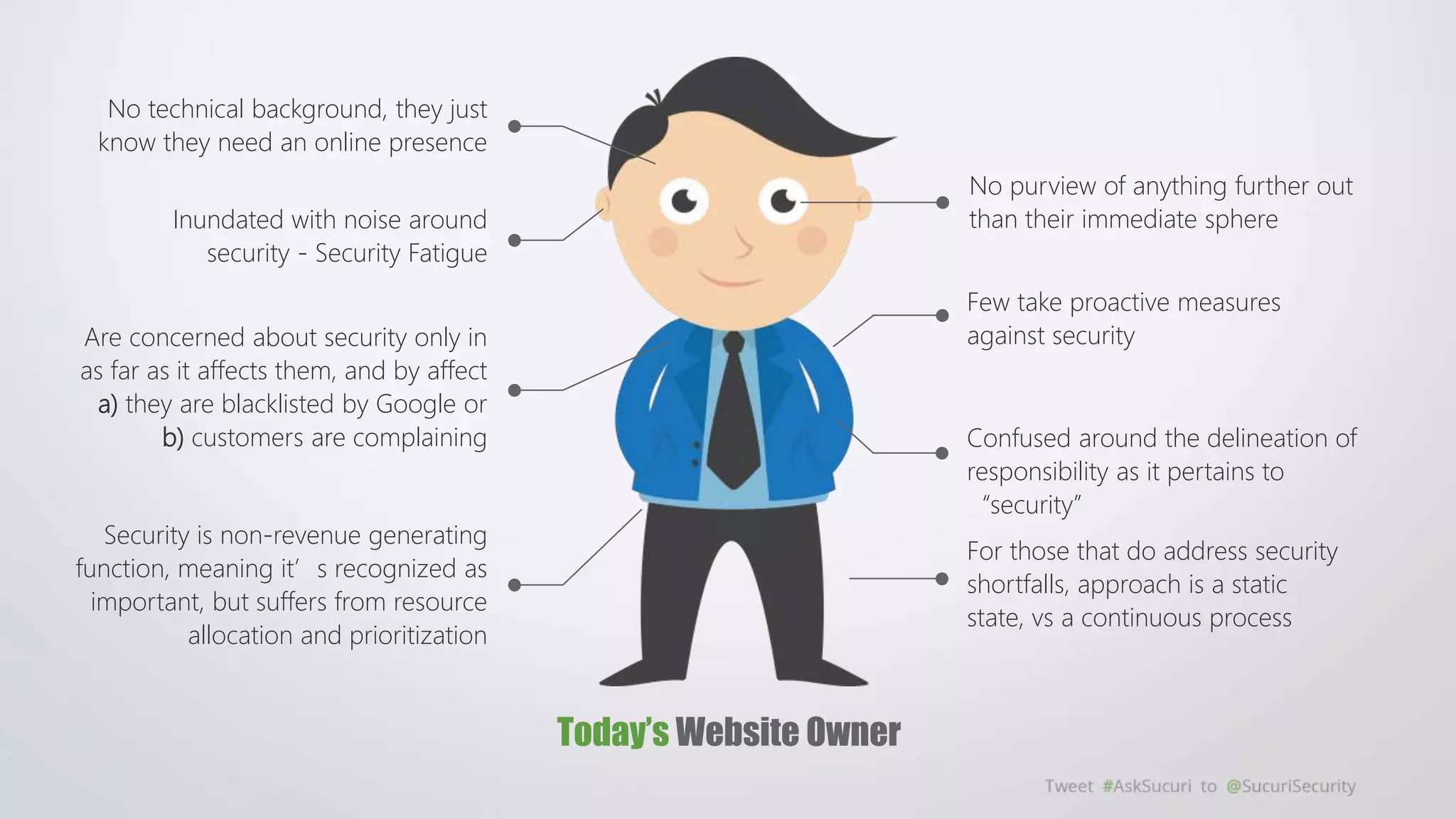
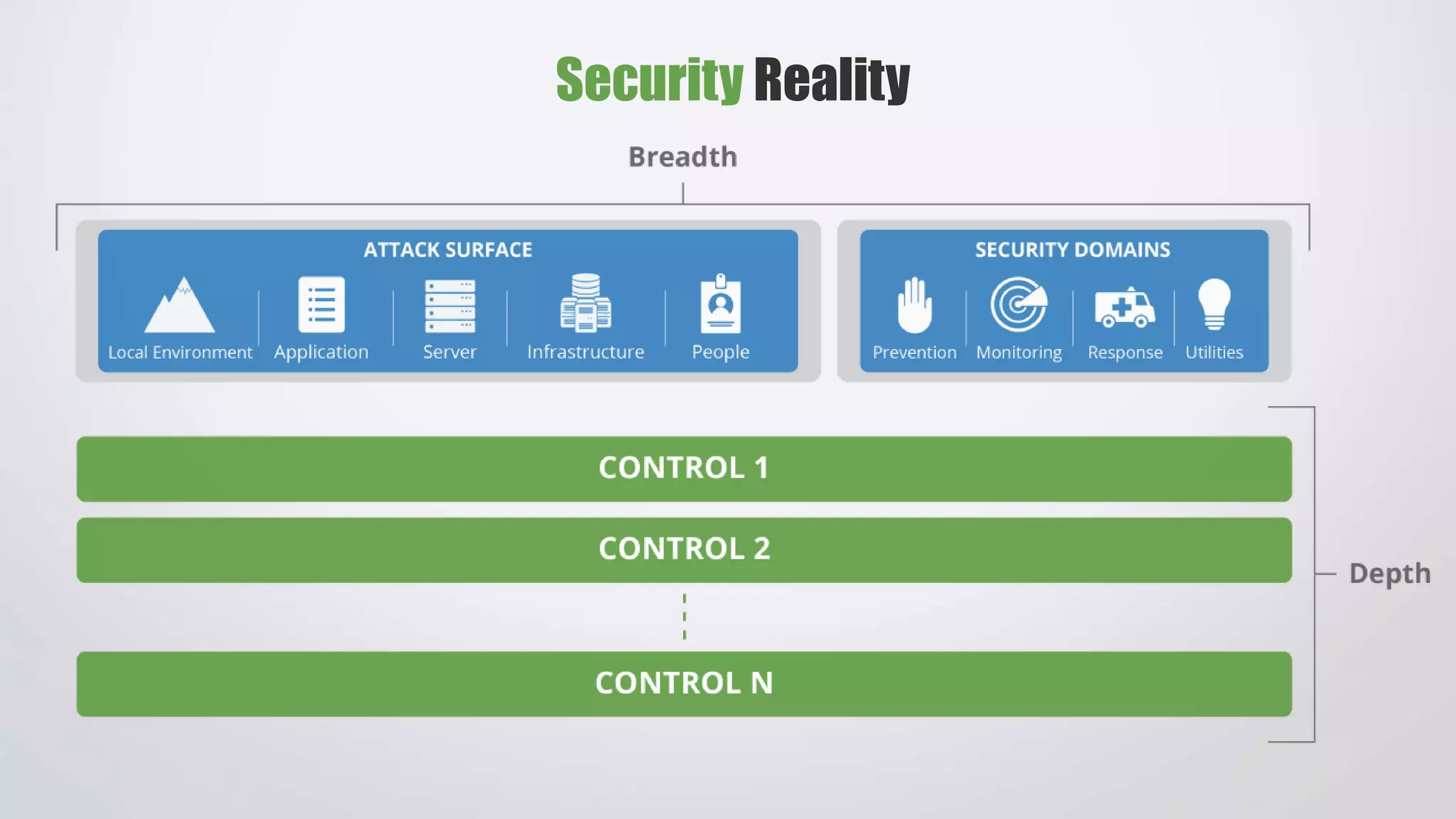
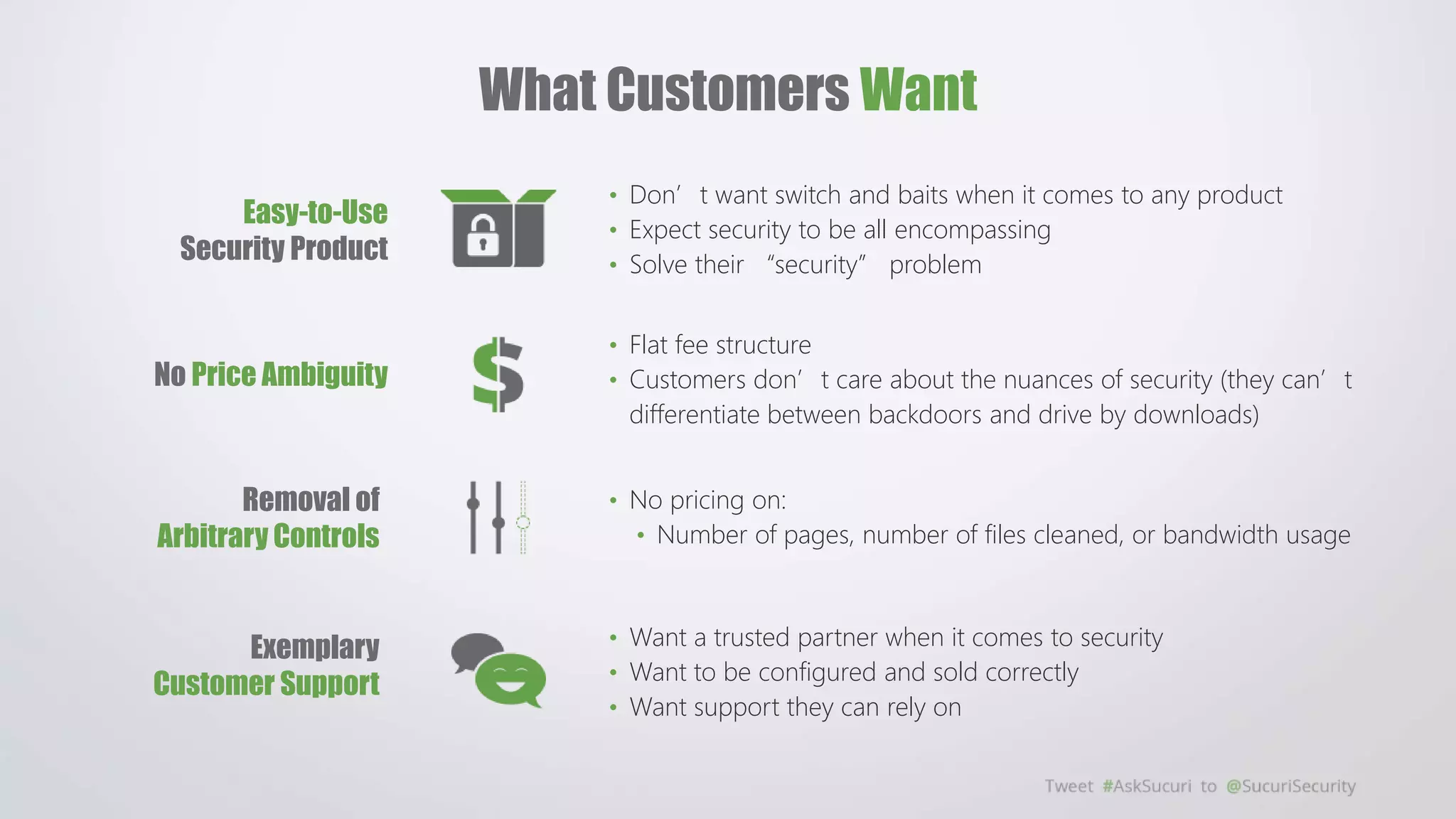
The document outlines security challenges faced by website owners with limited technical knowledge and emphasizes the need for simplification in security processes. It highlights the prevalence of security fatigue among users and the importance of transparent, easy-to-use security solutions that meet customer expectations without ambiguity. Additionally, it calls for collaboration among service providers to create a safer online environment through shared security practices and continuous improvement.