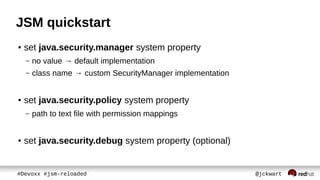
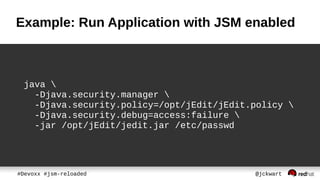
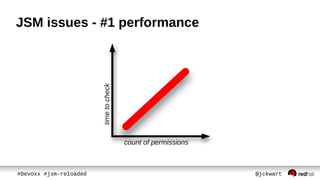
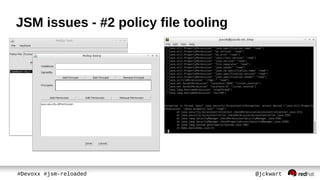
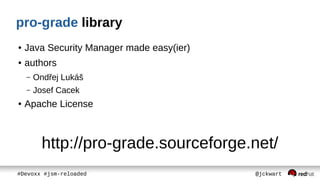
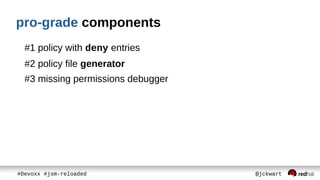
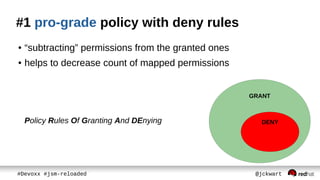
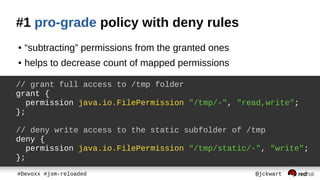
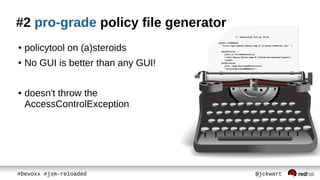
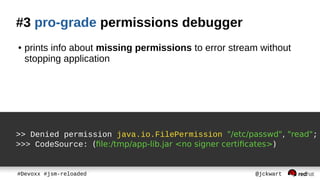
The document discusses Java Security Manager (JSM) and how it can be used to enforce security policies in Java applications. However, JSM has issues with performance and managing policy files. The Pro-Grade library aims to address these issues by providing components like a policy file generator and permissions debugger to make working with JSM easier. The presentation concludes by demonstrating how to generate a security policy for a Java EE server in just 3 minutes using Pro-Grade.








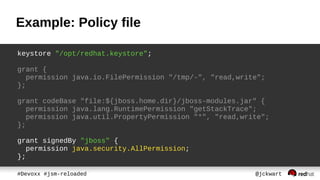
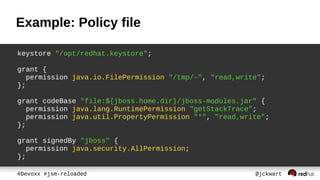
![Policy
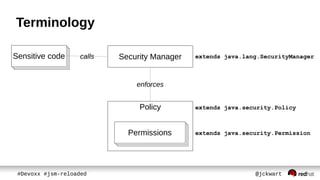
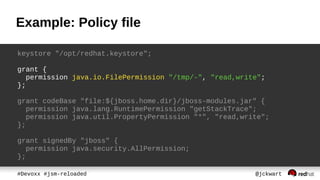
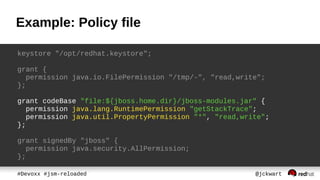
● keeps which protected actions are allowed
– No action by default
● defined in policy file
● grant entries assigns Permissions to
– code path [codeBase]
– signed classes [signedBy]
– authenticated user [principal]
#Devoxx #jsm-reloaded @jckwart](https://image.slidesharecdn.com/sec-man-reloaded-141112015137-conversion-gate01/85/Java-Security-Manager-Reloaded-Devoxx-2014-12-320.jpg)

![Example: Read a file
● App [app.jar] → Utils [app-lib.jar]→ FileReader(“/etc/passwd”)
#Devoxx #jsm-reloaded @jckwart](https://image.slidesharecdn.com/sec-man-reloaded-141112015137-conversion-gate01/85/Java-Security-Manager-Reloaded-Devoxx-2014-18-320.jpg)
![Example: Read a file
● App [app.jar] → Utils [app-lib.jar]→ FileReader(“/etc/passwd”)
Exception in thread "main" java.security.AccessControlException:
access denied ("java.io.FilePermission" "/etc/passwd" "read")
at java.security.AccessControlContext.checkPermission(AccessControlContext.java:372)
at java.security.AccessController.checkPermission(AccessController.java:559)
at java.lang.SecurityManager.checkPermission(SecurityManager.java:549)
at java.lang.SecurityManager.checkRead(SecurityManager.java:888)
at java.io.FileInputStream.<init>(FileInputStream.java:135)
at java.io.FileInputStream.<init>(FileInputStream.java:101)
at java.io.FileReader.<init>(FileReader.java:58)
at org.jboss.shared.Utils.getUserListInternal(Utils.java:36)
at org.jboss.shared.Utils.getUsersList(Utils.java:28)
at org.jboss.test.App.run(App.java:35)
at org.jboss.test.App.main(App.java:28)
system classes
app-lib.jar
app.jar
#Devoxx #jsm-reloaded @jckwart](https://image.slidesharecdn.com/sec-man-reloaded-141112015137-conversion-gate01/85/Java-Security-Manager-Reloaded-Devoxx-2014-19-320.jpg)
![Example: Read a file
● App [app.jar] → Utils [app-lib.jar]→ FileReader(“/etc/passwd”)
Exception in thread "main" java.security.AccessControlException:
access denied ("java.io.FilePermission" "/etc/passwd" "read")
at java.security.AccessControlContext.checkPermission(AccessControlContext.java:372)
at java.security.AccessController.checkPermission(AccessController.java:559)
at java.lang.SecurityManager.checkPermission(SecurityManager.java:549)
at java.lang.SecurityManager.checkRead(SecurityManager.java:888)
at java.io.FileInputStream.<init>(FileInputStream.java:135)
at java.io.FileInputStream.<init>(FileInputStream.java:101)
at java.io.FileReader.<init>(FileReader.java:58)
at org.jboss.shared.Utils.getUserListInternal(Utils.java:36)
at org.jboss.shared.Utils.getUsersList(Utils.java:28)
at org.jboss.test.App.run(App.java:35)
at org.jboss.test.App.main(App.java:28)
system classes
app-lib.jar
app.jar
#Devoxx #jsm-reloaded @jckwart](https://image.slidesharecdn.com/sec-man-reloaded-141112015137-conversion-gate01/85/Java-Security-Manager-Reloaded-Devoxx-2014-20-320.jpg)
![Example: Read a file
● App [app.jar] → Utils [app-lib.jar]→ FileReader(“/etc/passwd”)
Exception in thread "main" java.security.AccessControlException:
access denied ("java.io.FilePermission" "/etc/passwd" "read")
at java.security.AccessControlContext.checkPermission(AccessControlContext.java:372)
at java.security.AccessController.checkPermission(AccessController.java:559)
at java.lang.SecurityManager.checkPermission(SecurityManager.java:549)
at java.lang.SecurityManager.checkRead(SecurityManager.java:888)
at java.io.FileInputStream.<init>(FileInputStream.java:135)
at java.io.FileInputStream.<init>(FileInputStream.java:101)
at java.io.FileReader.<init>(FileReader.java:58)
at org.jboss.shared.Utils.getUserListInternal(Utils.java:36)
at org.jboss.shared.Utils.getUsersList(Utils.java:28)
at org.jboss.test.App.run(App.java:35)
at org.jboss.test.App.main(App.java:28)
system classes
app-lib.jar
app.jar
#Devoxx #jsm-reloaded @jckwart](https://image.slidesharecdn.com/sec-man-reloaded-141112015137-conversion-gate01/85/Java-Security-Manager-Reloaded-Devoxx-2014-21-320.jpg)
![Example: Read a file
● App [app.jar] → Utils [app-lib.jar]→ FileReader(“/etc/passwd”)
Exception in thread "main" java.security.AccessControlException:
access denied ("java.io.FilePermission" "/etc/passwd" "read")
at java.security.AccessControlContext.checkPermission(AccessControlContext.java:372)
at java.security.AccessController.checkPermission(AccessController.java:559)
at java.lang.SecurityManager.checkPermission(SecurityManager.java:549)
at java.lang.SecurityManager.checkRead(SecurityManager.java:888)
at java.io.FileInputStream.<init>(FileInputStream.java:135)
at java.io.FileInputStream.<init>(FileInputStream.java:101)
at java.io.FileReader.<init>(FileReader.java:58)
at org.jboss.shared.Utils.getUserListInternal(Utils.java:36)
at org.jboss.shared.Utils.getUsersList(Utils.java:28)
at org.jboss.test.App.run(App.java:35)
at org.jboss.test.App.main(App.java:28)
system classes
app-lib.jar
app.jar
#Devoxx #jsm-reloaded @jckwart](https://image.slidesharecdn.com/sec-man-reloaded-141112015137-conversion-gate01/85/Java-Security-Manager-Reloaded-Devoxx-2014-22-320.jpg)