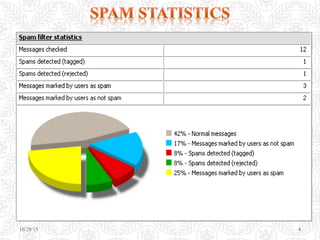
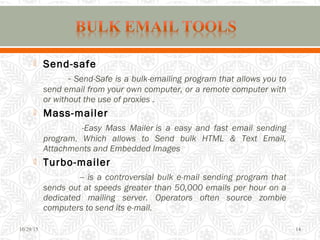
The document discusses spam, including its definition as unsolicited commercial email, statistics on its prevalence, and various types like email spam, web search engine spam, image spam, and blank spam. It also covers how spammers earn money, techniques for sending spam like using botnets and open relays, and anti-spam techniques like using filters and reporting spam messages. The conclusion emphasizes staying informed about spam characteristics to protect systems and data from potential dangers.