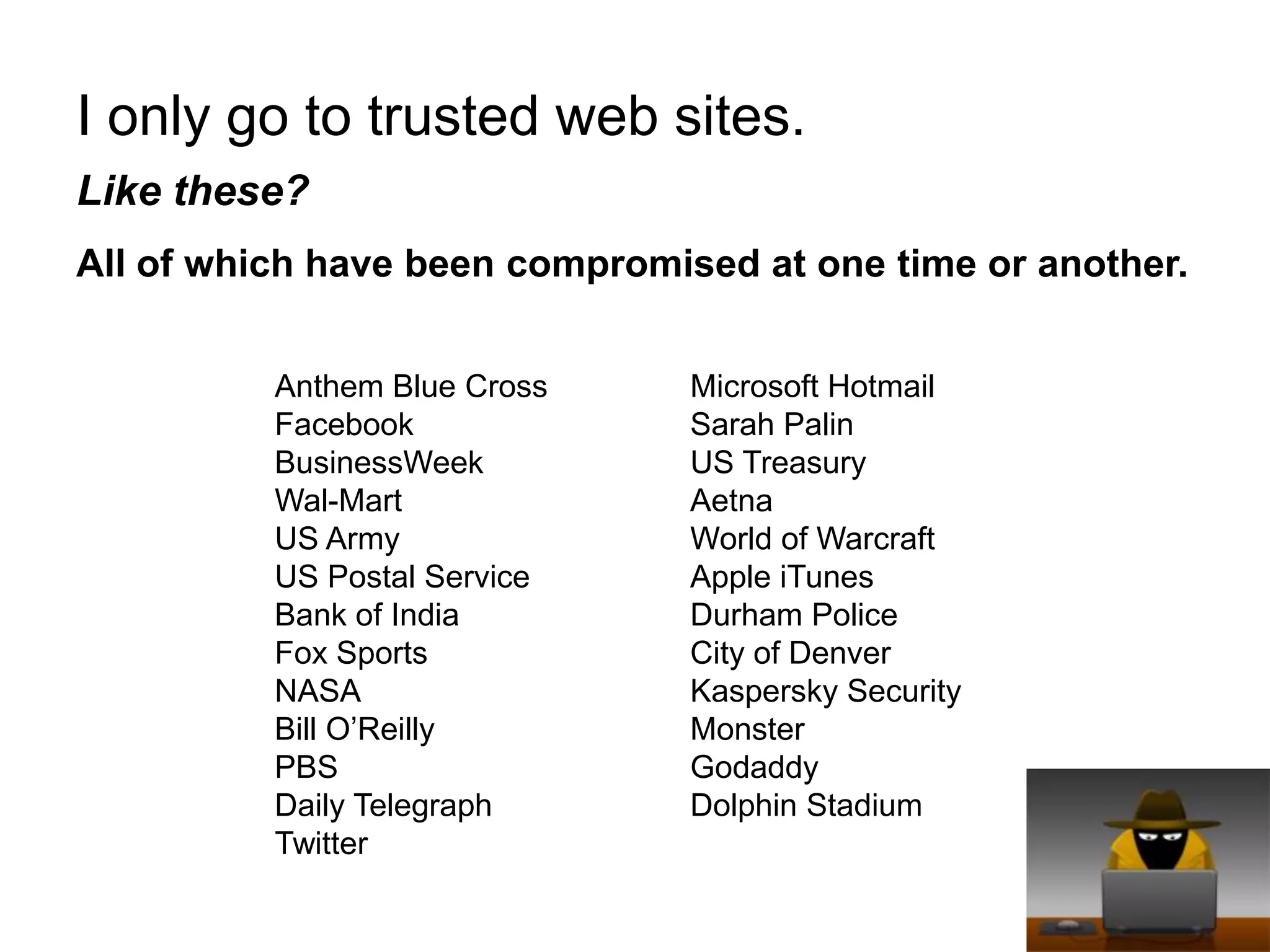
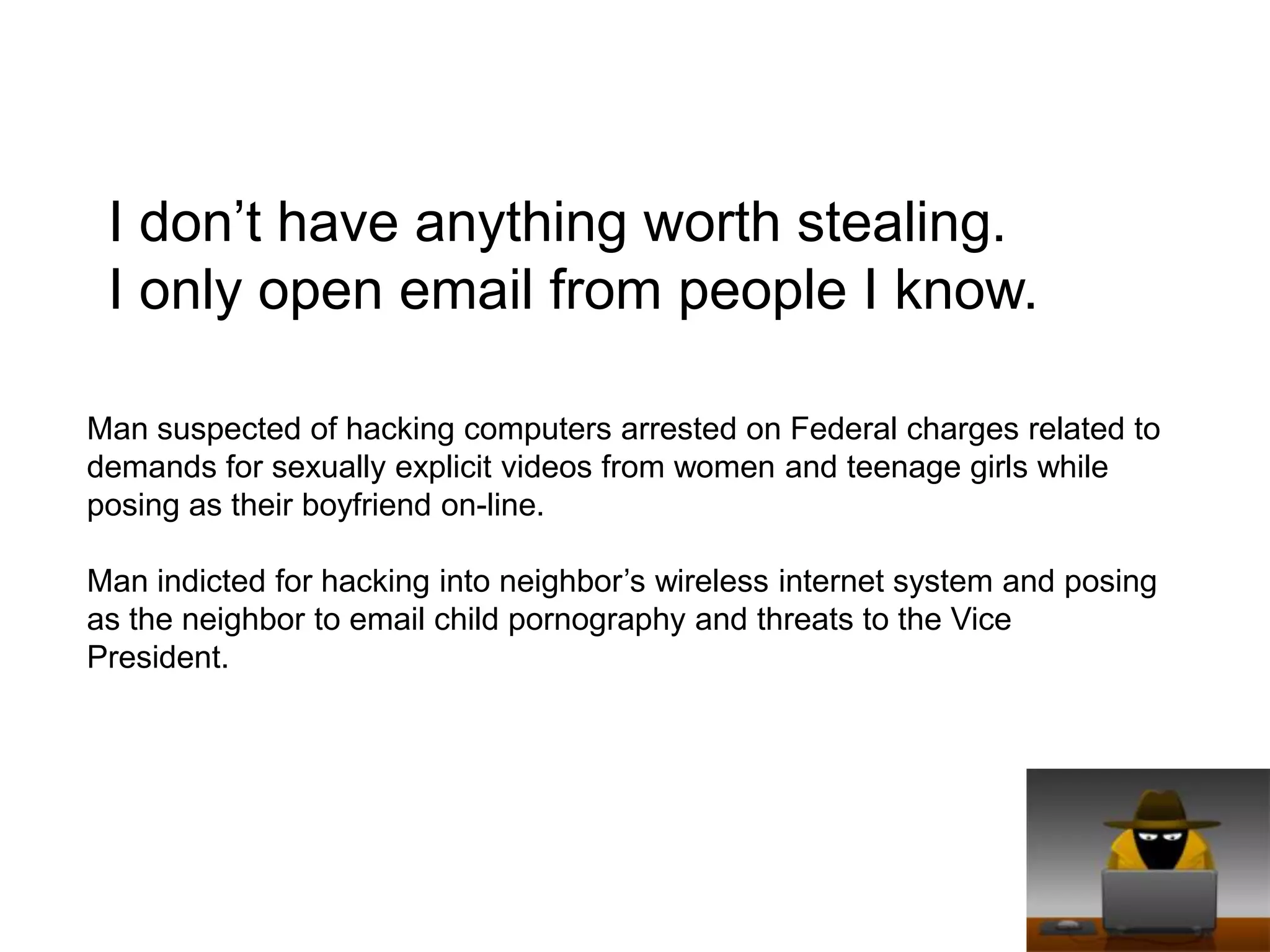
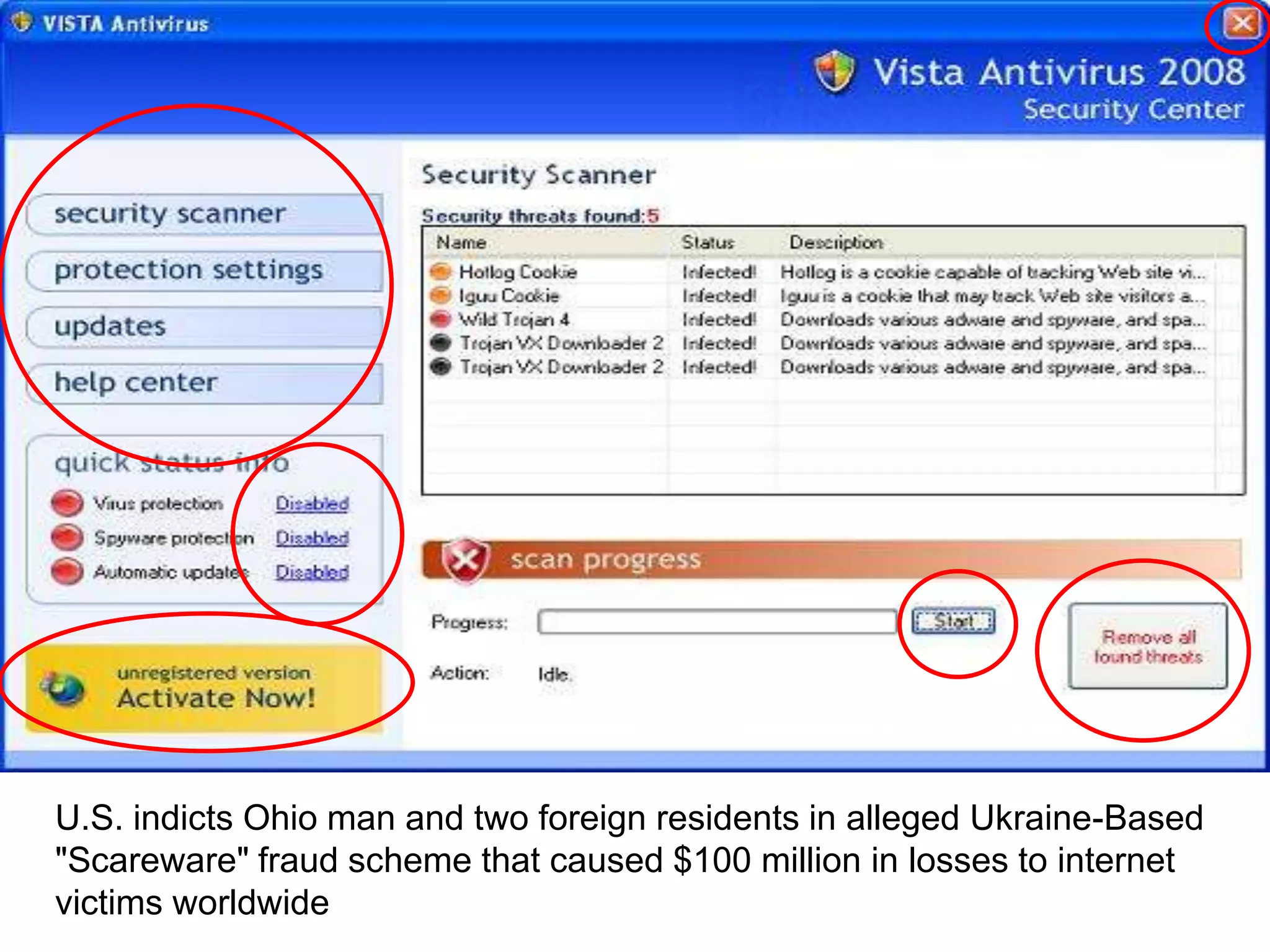
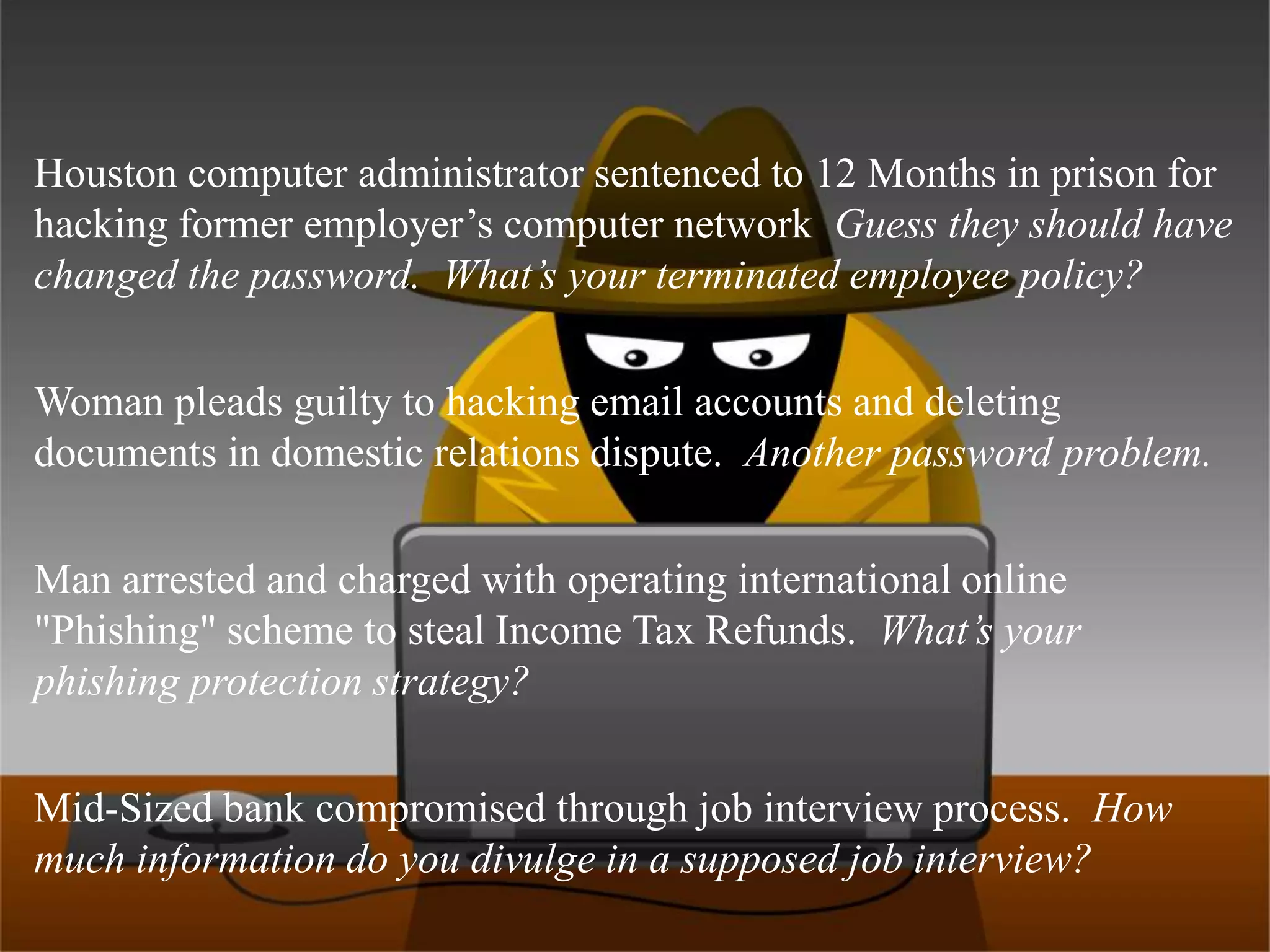
Small businesses lose $2 million per week to cybercrime according to FBI estimates, while cybercrime profits totaled $1 trillion in 2009 according to MacAfee. Common misconceptions are that antivirus software and only visiting trusted sites ensure safety, but antivirus only catches 25-40% of malware and trusted sites like Anthem and Facebook have been compromised. Having "nothing worth stealing" is also a misconception, as criminals hack to demand sexually explicit videos or send child pornography and threats. Self-auditing security is not advisable, as IT providers prioritize uptime over safety and lack specialized security skills. Businesses should keep systems patched, limit network content, teach skepticism, and disconnect suspicious devices to call