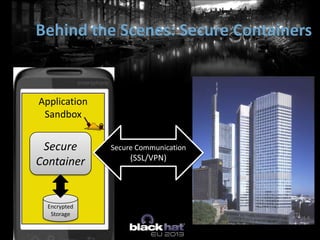
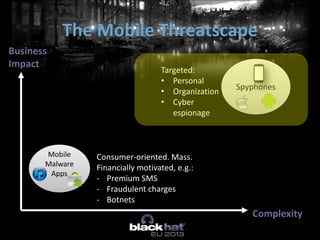
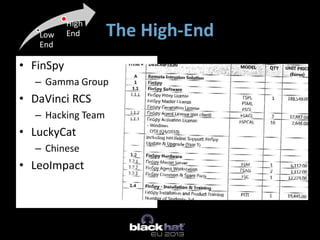
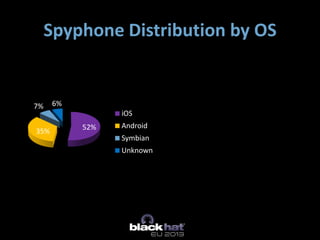
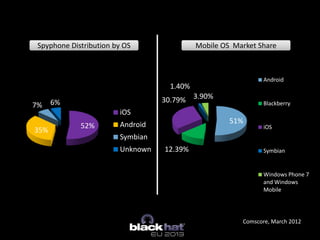
The document discusses the vulnerabilities of Mobile Device Management (MDM) systems and the rise of spyphones, emphasizing that secure containers are not entirely secure against sophisticated attacks. It highlights the prevalence of mobile malware and the effectiveness of low-end spy tools that can compromise both personal and corporate data. The conclusion advocates for a multi-layered security approach, noting that while MDM can separate business and personal data, it cannot guarantee absolute security.