Encryption works by using keys to scramble information before it is transmitted. There are two main types of encryption: symmetric and asymmetric.
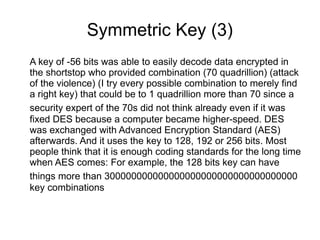
Symmetric encryption uses the same key to both encrypt and decrypt data. It is like two generals sending coded messages using the same cipher. Computers use long encryption keys for security. Early symmetric algorithms like DES used 56-bit keys, while the current standard AES uses 128-bit, 192-bit or 256-bit keys.
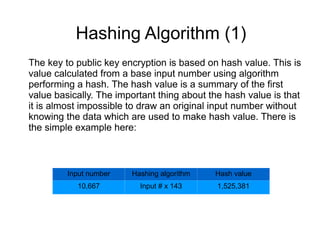
Hashing algorithms are used in public key encryption. A hash takes an input and generates a unique output value using an algorithm. It is very difficult to determine the original input from the hash value alone. Hashes are used to verify data integrity and in digital