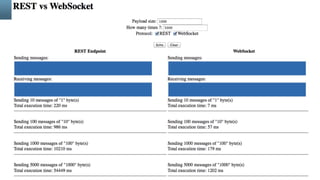
This document discusses building WebSocket applications in Java using JSR 356. It begins with an introduction to WebSockets and their advantages over traditional HTTP for interactive web applications. It then covers the JSR 356 specification for a Java API for WebSocket, including annotated and programmatic endpoints. The document provides examples of basic "hello world" clients and servers. It also discusses more advanced topics like custom payloads, URI template matching, security, and relationships with dependencies and Servlet APIs.



















![Copyright © 2013, Oracle and/or its affiliates. All rights reserved. Insert Information Protection Policy Classification from Slide 1327
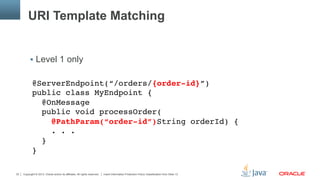
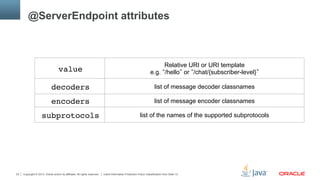
Custom Payloads – Binary Decoder
public class MyMessageDecoder implements Decoder.Binary<MyMessage> {
public MyMessage decode(byte[] bytes) {
. . .
return myMessage;"
}"
public boolean willDecode(byte[] bytes) {
. . .
return true; // Only if can process the payload
}"
. . .
}"](https://image.slidesharecdn.com/websocket-1-0-130514032348-phpapp02/85/Java-API-for-WebSocket-1-0-Java-EE-7-and-GlassFish-27-320.jpg)
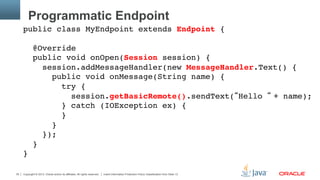
![Copyright © 2013, Oracle and/or its affiliates. All rights reserved. Insert Information Protection Policy Classification from Slide 1328
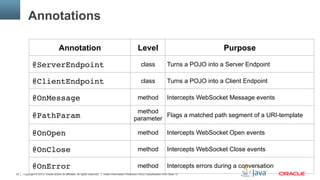
Which methods can be @OnMessage ?
§ Exactly one of the following
– Text: String, Java primitive or equivalent class, String and boolean,
Reader, any type for which there is a decoder
– Binary: byte[], ByteBuffer, byte[] and boolean, ByteBuffer and
boolean, InptuStream, any type for which there is a decoder
– Pong messages: PongMessage"
§ An optional Session parameter
§ 0..n String parameters annotated with @PathParam"
§ Return type: String, byte[], ByteBuffer, Java primitive or class
equivalent or any type for which there is a encoder](https://image.slidesharecdn.com/websocket-1-0-130514032348-phpapp02/85/Java-API-for-WebSocket-1-0-Java-EE-7-and-GlassFish-28-320.jpg)
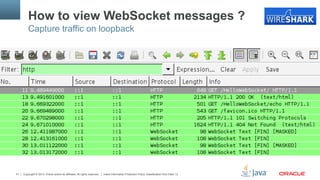
![Copyright © 2013, Oracle and/or its affiliates. All rights reserved. Insert Information Protection Policy Classification from Slide 1329
Sample Messages
§ void m(String s);"
§ void m(Float f, @PathParam(“id”)int id);"
§ Product m(Reader reader, Session s);"
§ void m(byte[] b); or void m(ByteBuffer b);"
§ Book m(int i, Session s, @PathParam(“isbn”)String
isbn, @PathParam(“store”)String store);"](https://image.slidesharecdn.com/websocket-1-0-130514032348-phpapp02/85/Java-API-for-WebSocket-1-0-Java-EE-7-and-GlassFish-29-320.jpg)