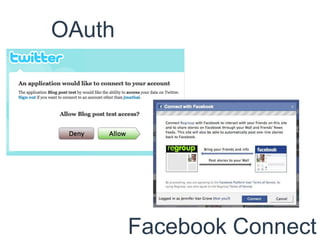
The document discusses privacy and control on the web. It states that while total control is impossible, the best approach is to choose how, when and where personal information appears online. It then provides tips on strong passwords, including being at least 7 characters with uppercase and lowercase letters, numbers, and symbols in multiple positions. OAuth and Facebook Connect are mentioned as solutions. The document is authored by Steven Mandzik, director of Green IT at Navstar Inc.












![Passwords
Strong Password Definition, Requirements and Guidelines
•A strong password is a password that meets the following guidelines:
•Be 7 or 14 characters long.
•Contain both uppercase and lowercase letters.
•Contain numbers.
•Contain symbols, such as ` ! " ? $ ? % ^ & * ( ) _ - + = { [ } ] : ; @ ' ~ # | < , > . ? /
•Contain a symbol in the second, third, fourth, fifth or sixth position (due to the way in which encryption
works).
•Not resemble any of your previous passwords.
•Not be your name, your friend's or family member's name, or your login.
•Not be a dictionary word or common name.](https://image.slidesharecdn.com/web20security-100413145740-phpapp01/85/Web20security-20-320.jpg)