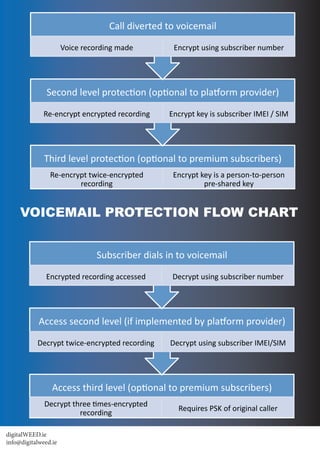
This document describes an invisible and transparent voicemail protection solution. The solution automatically encrypts all voicemails to prevent unauthorized access even if the mailbox or storage servers are compromised. It offers multiple layers of encryption including encrypting voicemails with the caller's phone number and encrypting that further with the recipient's IMEI/IMSI for added security. The solution can also flag attempted attacks and report the identity of attackers.