Embed presentation
Download to read offline




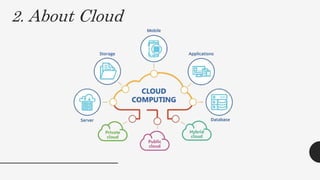
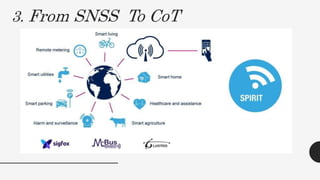





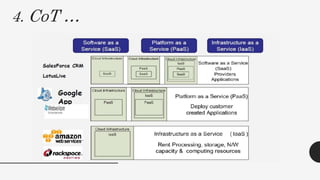

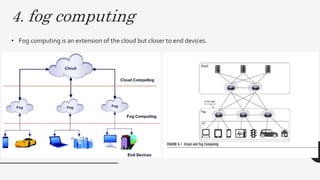
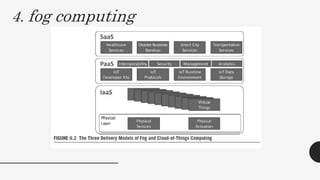



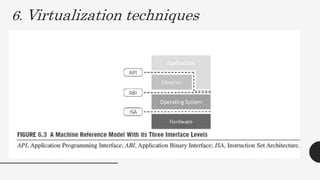

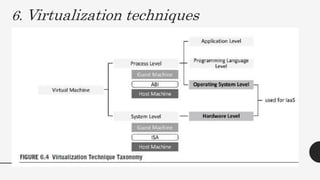

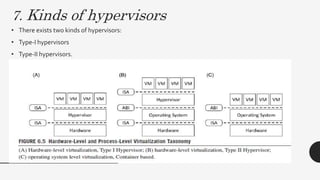


This document discusses virtualization techniques for embedded systems to enable the cloud of things (CoT). It begins by introducing CoT as the integration of the internet of things (IoT) and cloud computing to realize the vision of smart networked systems and societies. It then discusses fog computing as an extension of cloud computing that is better suited for IoT due to features like edge location. The document evaluates whether current embedded system hardware and virtualization techniques can support CoT/IoT and finds that full, para, and container virtualization as well as type-1 and type-2 hypervisors are appropriate options. Key frameworks like Xen and KVM that support ARM architecture are also mentioned.
























