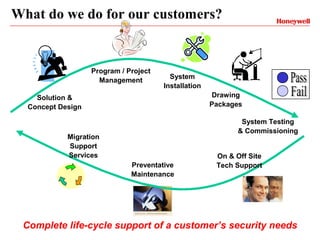
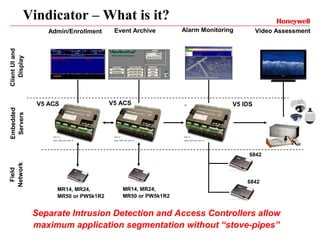
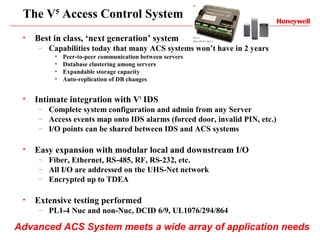
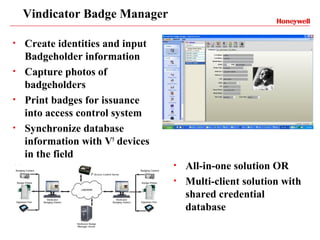
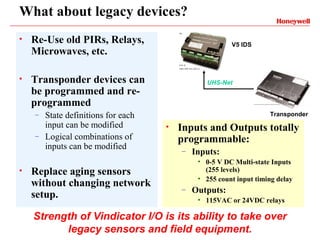
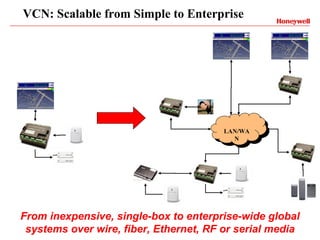
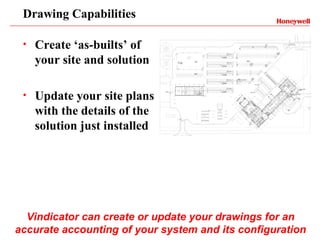
Vindicator Security Solutions provides comprehensive security solutions including intrusion detection, access control, and advanced security capabilities. They have nearly 30 years of experience and can handle all aspects of a security project from concept design to installation to long-term support. Their goal is to provide customized, scalable solutions tailored to each customer's specific needs and mission.