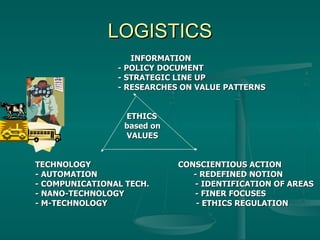
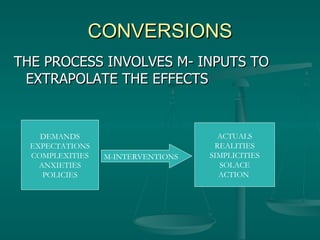
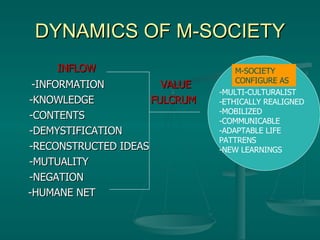
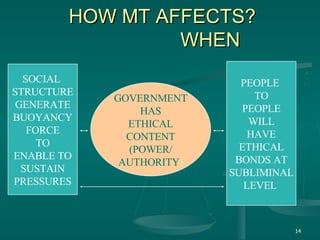
The document discusses using mobile technology (M-technology) to promote value-building in society. It argues that M-technology can help manage duality at a subliminal level, define individuals' ethical domains, and constitute society's moral fiber. M-technology refers to electronic devices, mobile devices, and implanted devices. It also discusses how M-technology can articulate expectations, connect various sectors of society, and consolidate research to rebuild confidence in humanity by circulating value-laden messages. The document outlines how M-technology and an M-society could utilize informational inputs, governance, and strategy to transform society in an ethically aligned manner.