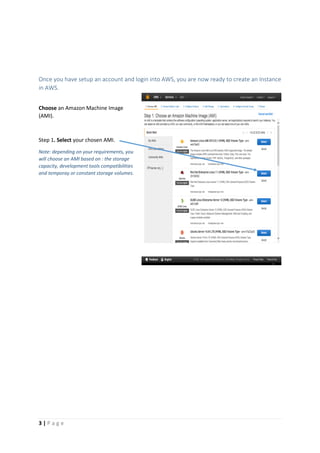
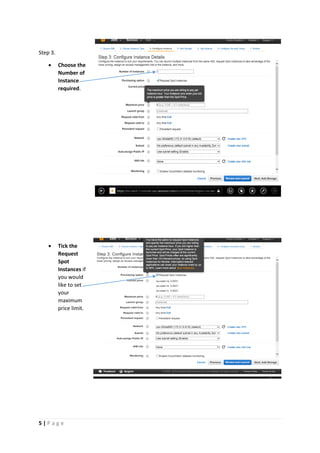
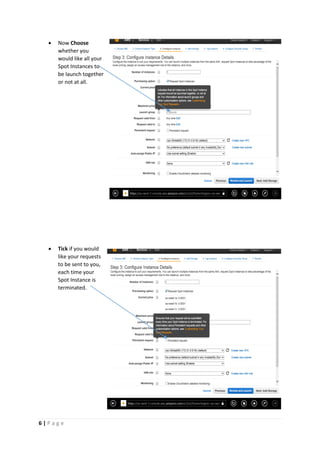
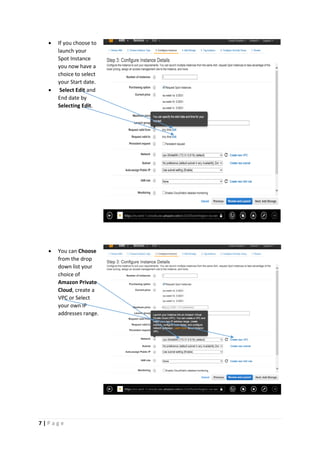
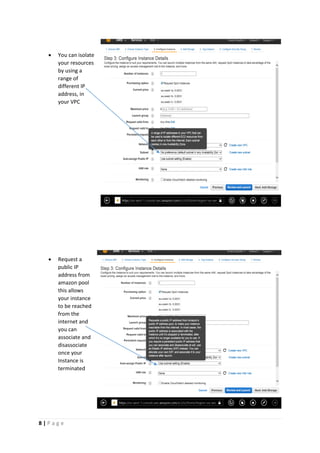
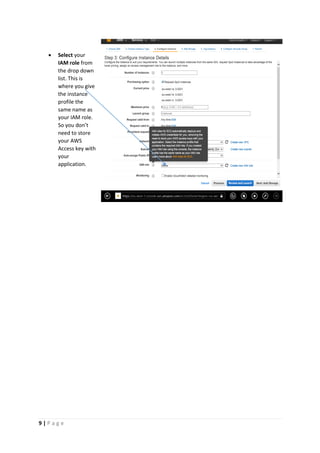
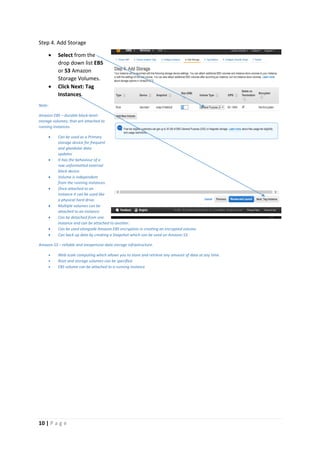
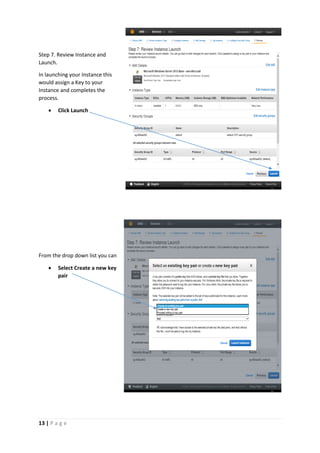
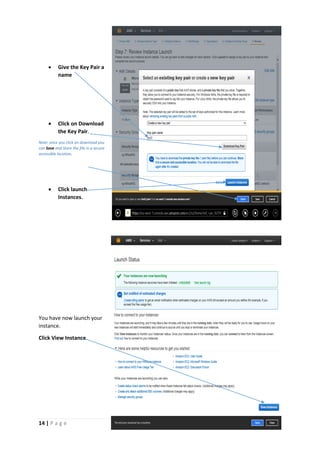
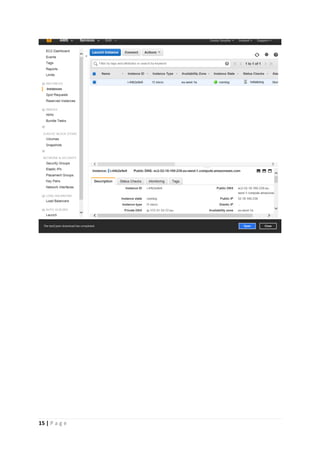
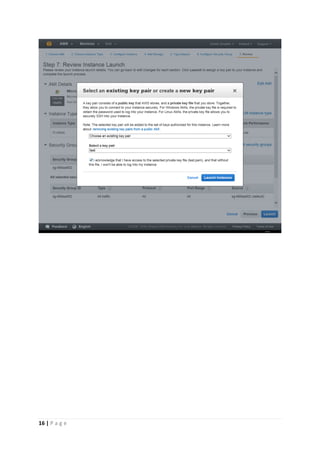
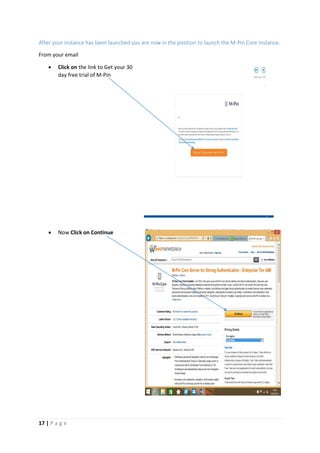
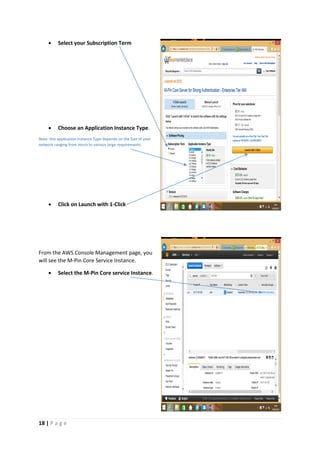
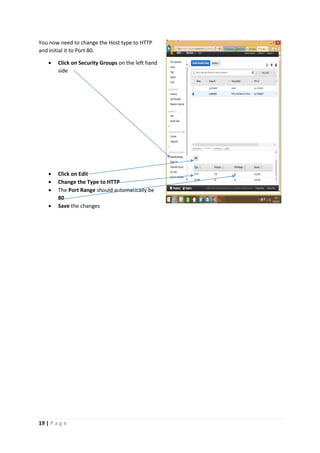
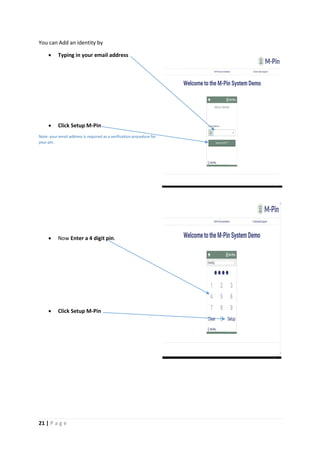
The document provides instructions for launching an M-Pin Core service instance on Amazon EC2. It describes choosing an Amazon Machine Image, instance type, storage options, and configuring security groups. The steps also cover accessing the M-Pin Core trial demo and configuring the instance host and port. Once launched, the M-Pin Core service can be accessed in a browser to create identities and pins for strong authentication testing.






![22 | P a g e
You have now Setup your M-Pin Core Cloud
Encryption system.
You can now Login to check your Login process
Type your Pin in
Click Login
e[Gr
ab
your
read
er’s
atten
tion
with
a
great
quot
e
from
the
docu
ment
or
use
this
spac
e to
emp
hasiz
e a
key
point
. To
place
this
text
box
anyw
here
on
the
page
, just
drag
it.]
[Gr
ab
you
r
rea
der
’s
att
ent
ion
wit
h a
gre
at
quo
te
fro
m
the](https://image.slidesharecdn.com/amazoncloudintancelaunch3-151016113223-lva1-app6891/85/Amazon-cloud-intance-launch3-23-320.jpg)
![23 | P a g e
This is now your Strong Authentication Protection
email@bt.com
[Grab your
reader’s
attention
with a
great
quote from
the
document
or use this
space to
emphasize
a key
point. To
place this
text box
anywhere
on the
page, just
drag it.]](https://image.slidesharecdn.com/amazoncloudintancelaunch3-151016113223-lva1-app6891/85/Amazon-cloud-intance-launch3-24-320.jpg)