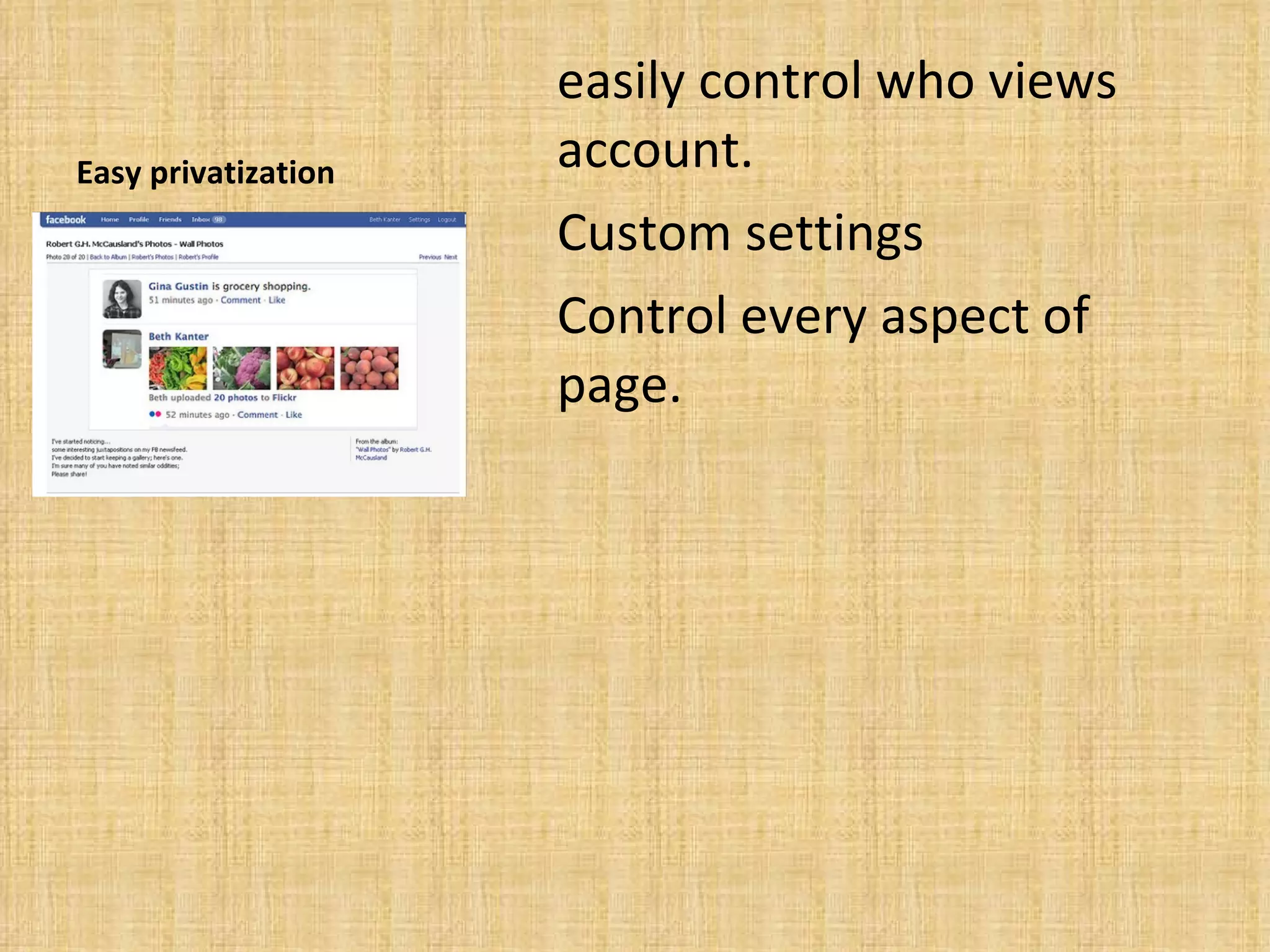
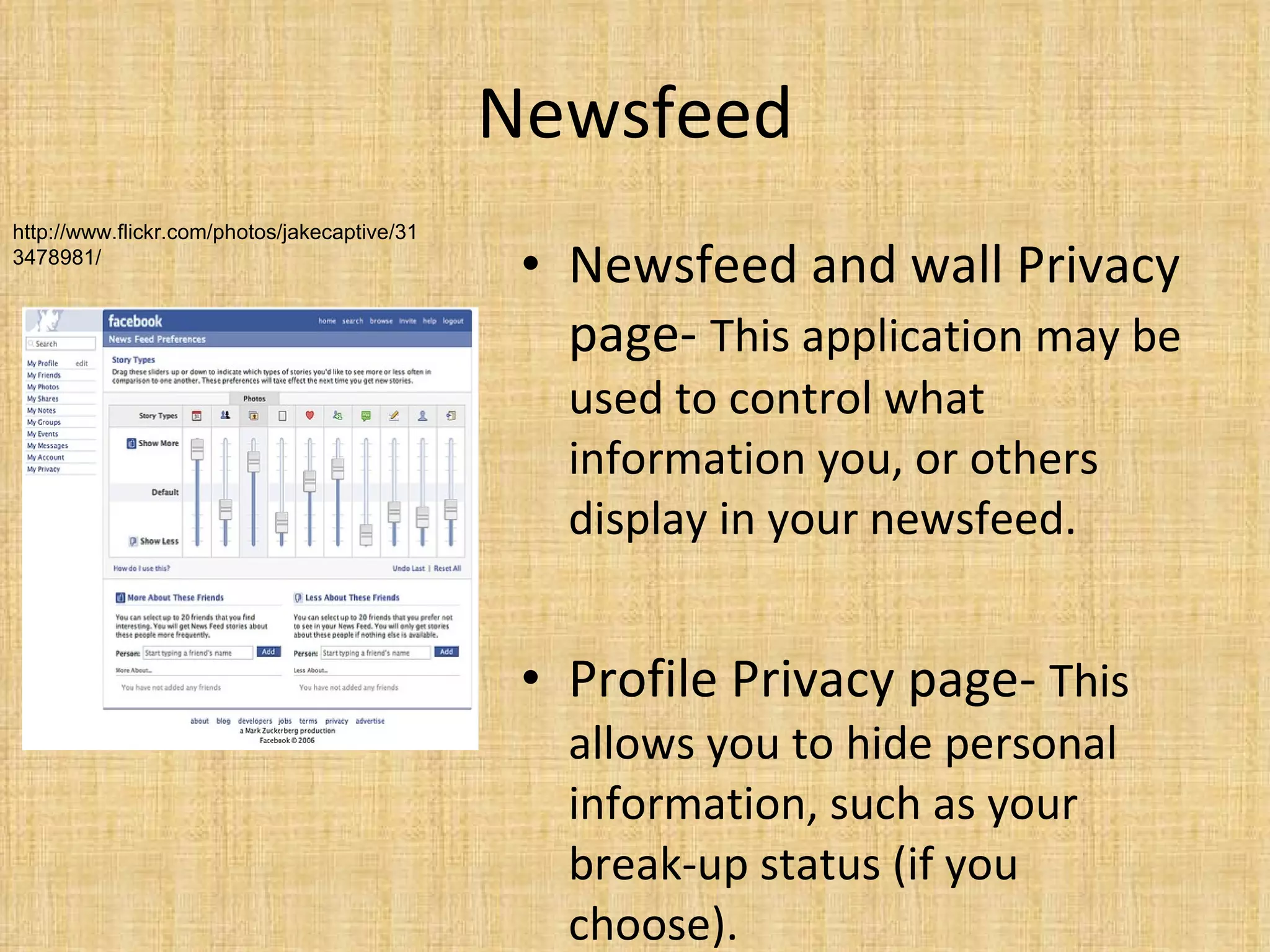
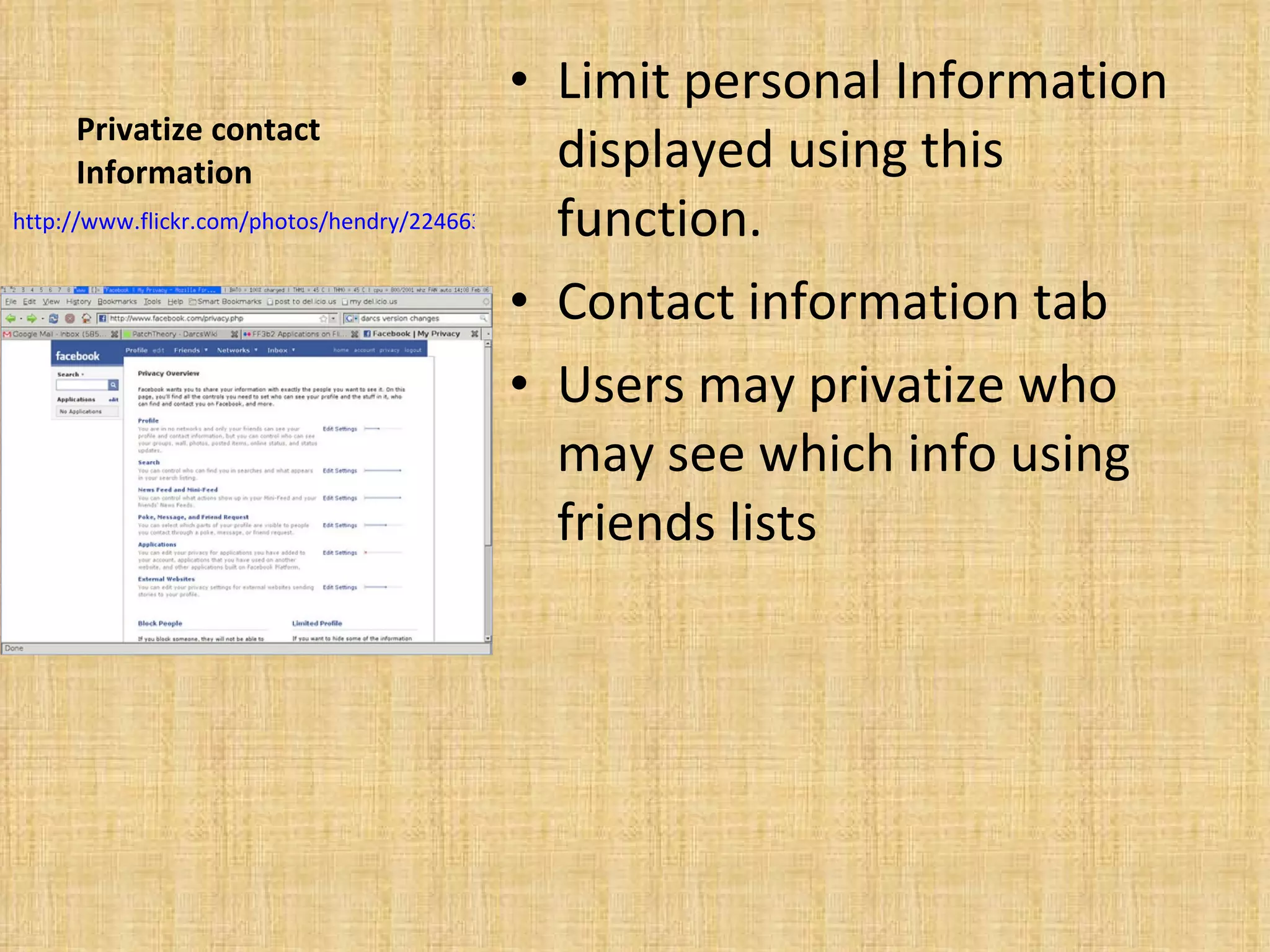
Using Social networking sites Facebook MySpace Twitter Focus on Facebook Social Networking advantages Stay connected Planning Meeting new people Instant communication Easy privatization Meet new people While this is a great advantage users must have discretion when making online friends. And in regards to what personal information they display. Over accessibility Large amounts- of private information are often displayed by users. This can be potentially hazardous to their well being. Viewed by anyone- If security precautions are not used users sites may be viewed by anyone. Negative repercussions possible-Users profiles are open to the public and may be viewed by anyone. Predators Schools Over accessibility Predators- Users of Social Networks often display too much personal information. Putting