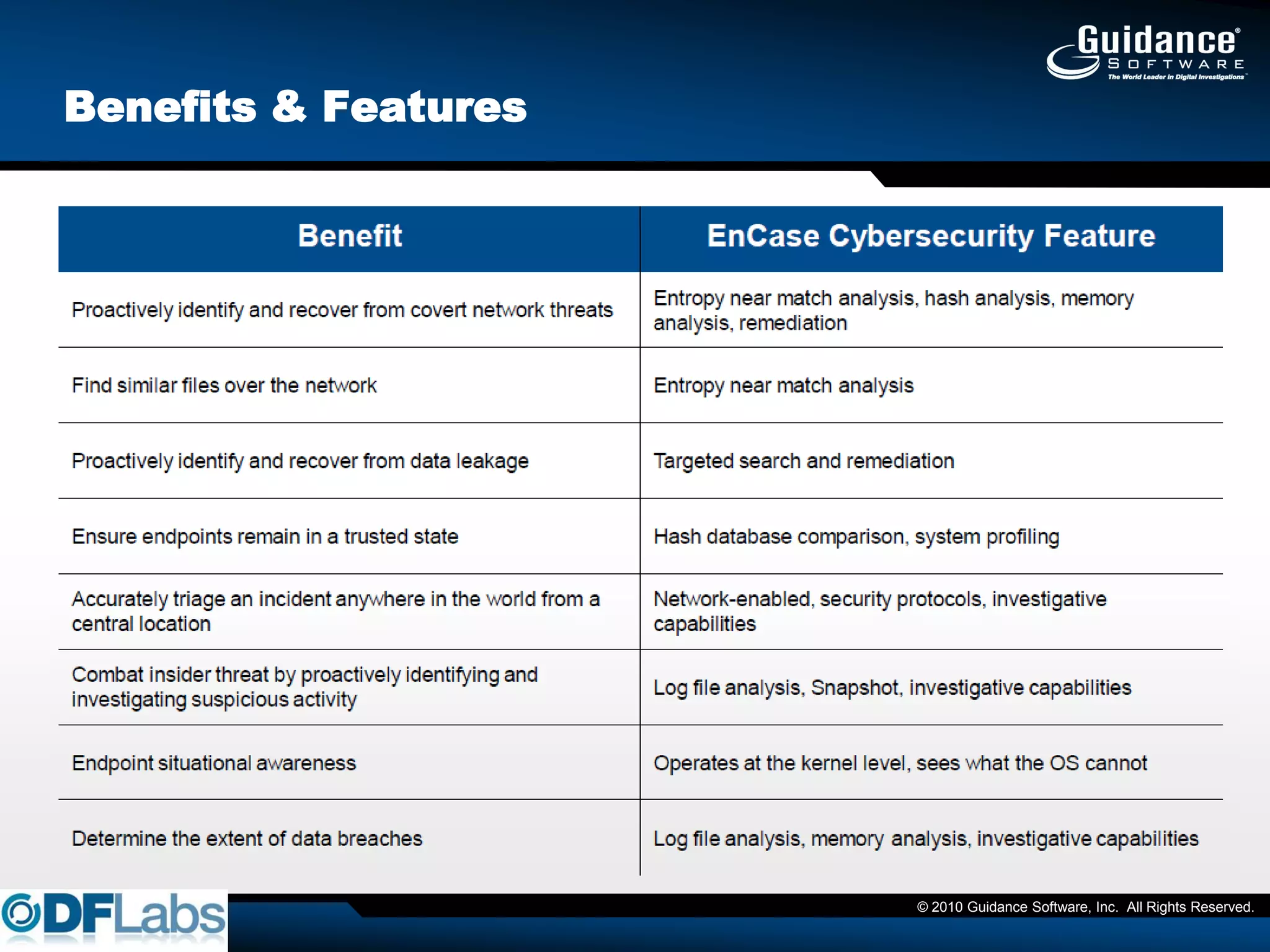
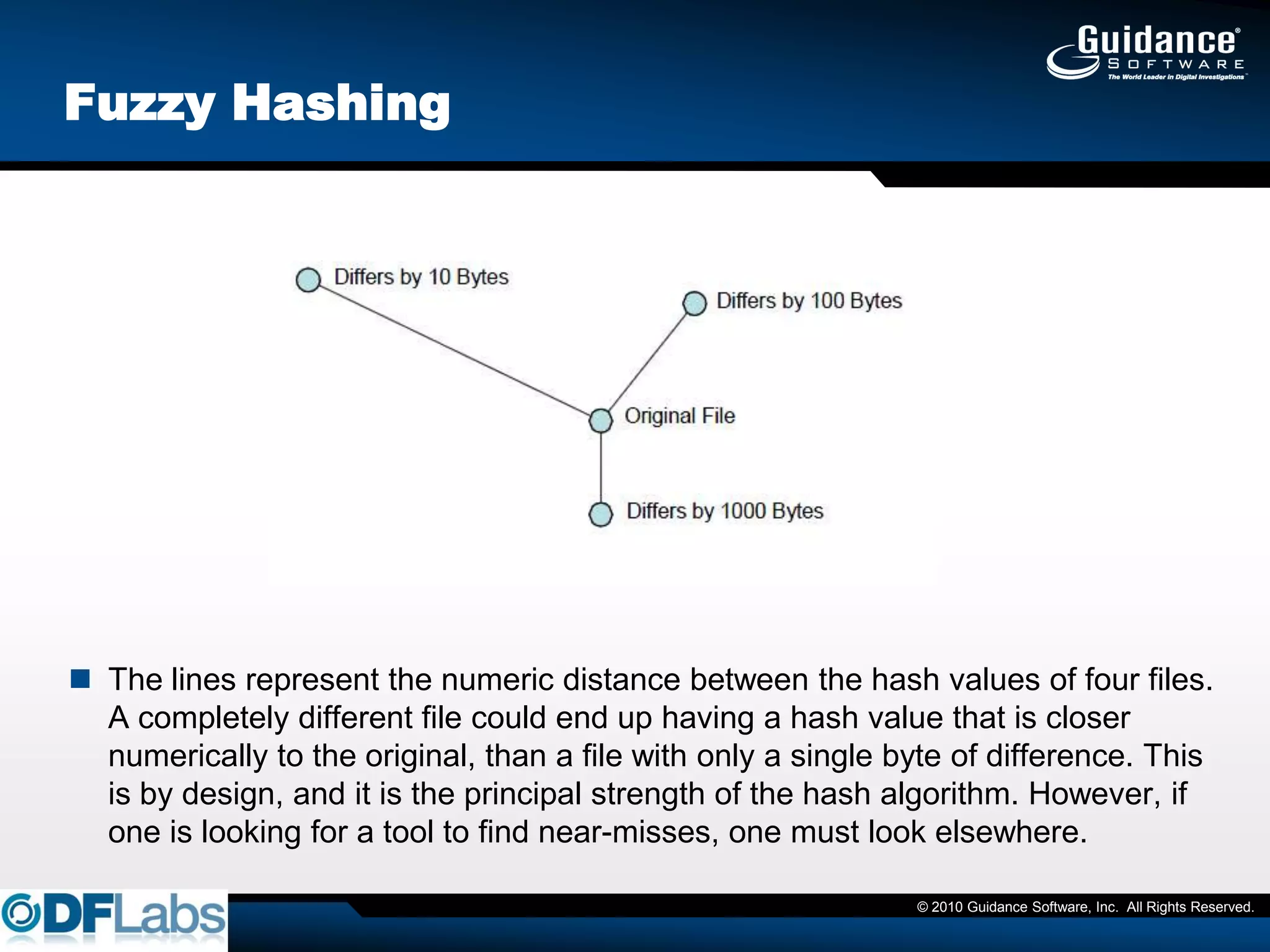
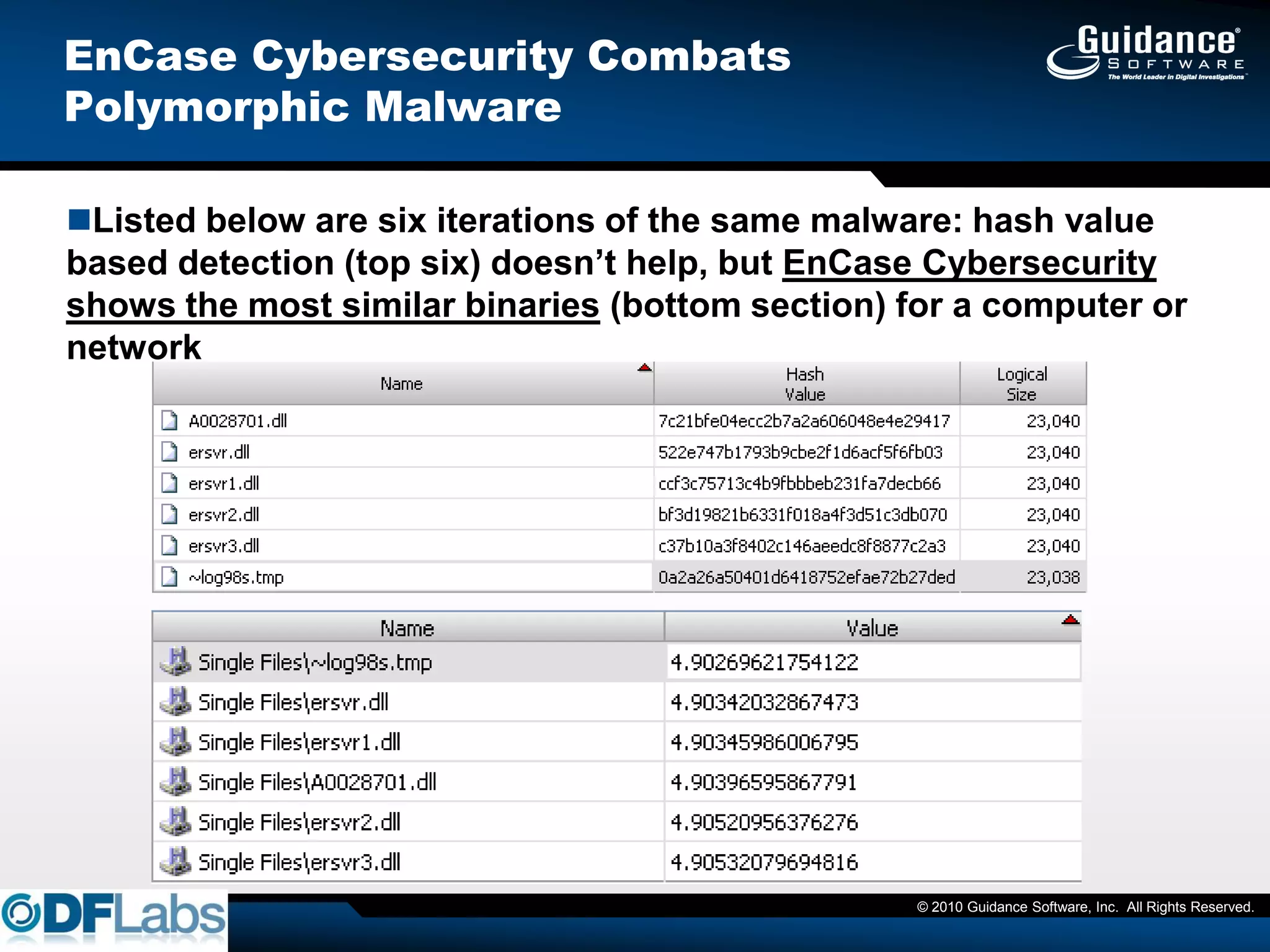
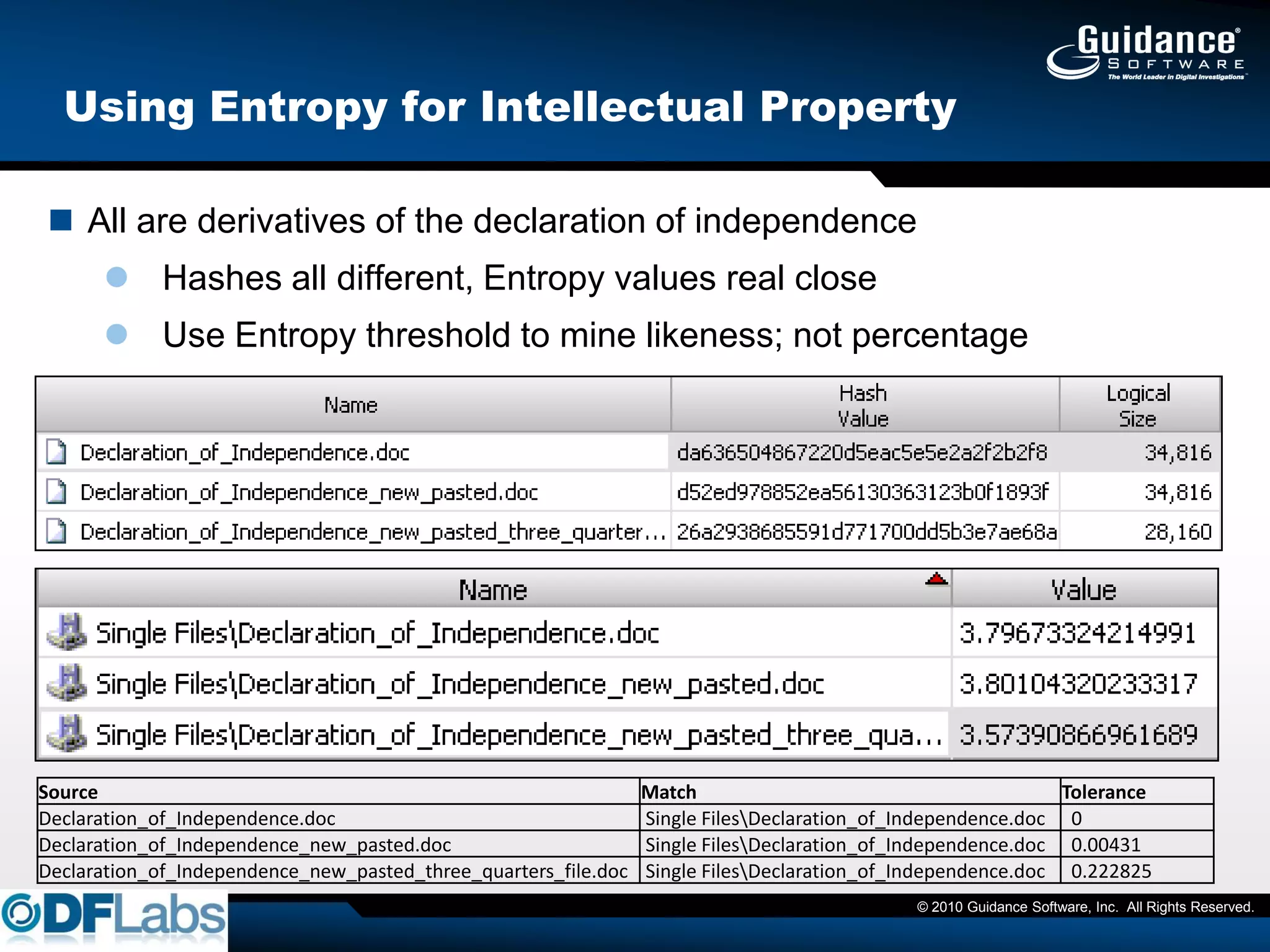
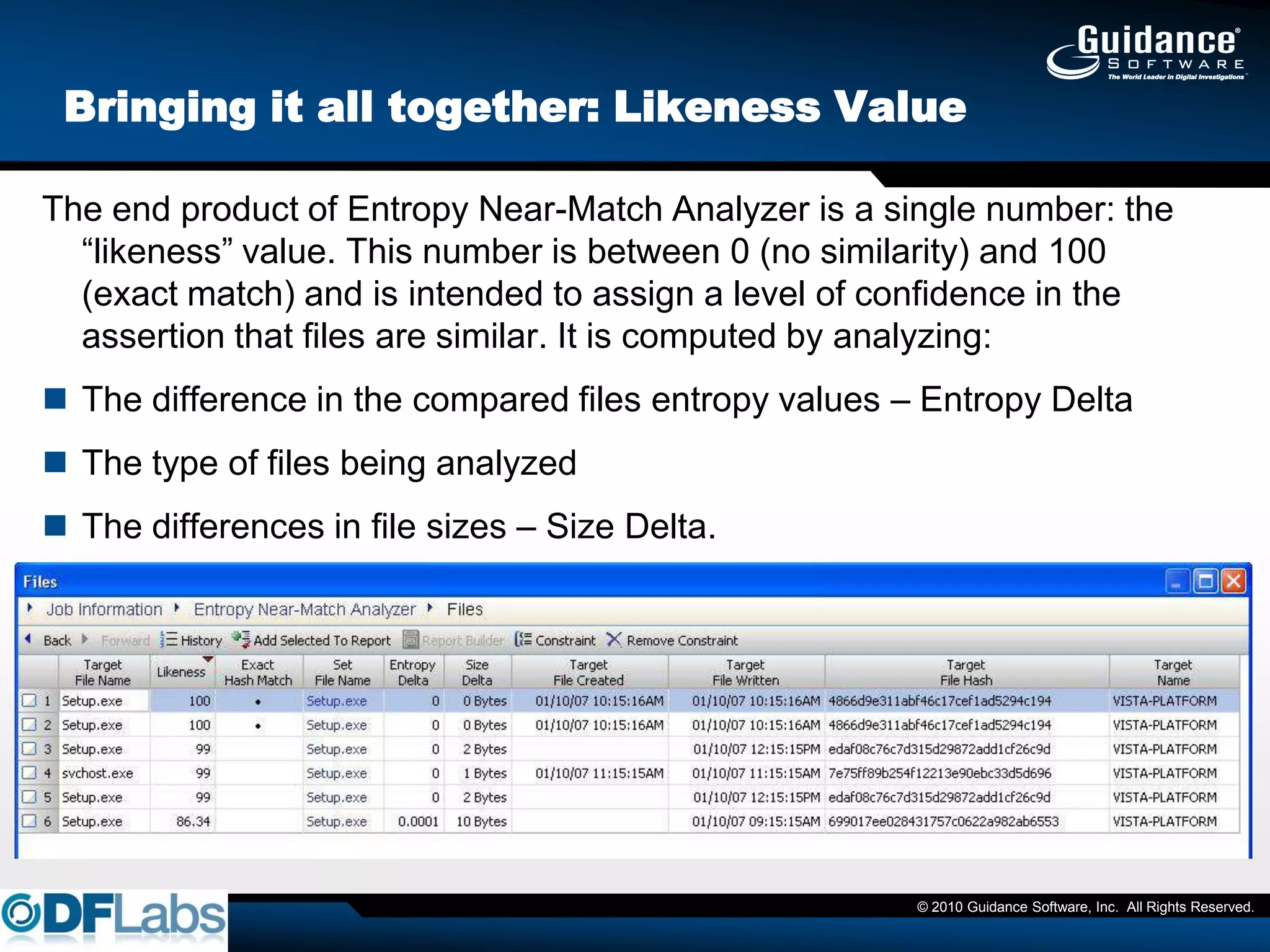
The document discusses the challenges and methodologies in cybersecurity, particularly in identifying and recovering from covert threats like polymorphic malware, which evades traditional detection methods. It introduces concepts such as fuzzy hashing and entropy analysis to enhance detection capabilities. Additionally, it emphasizes the importance of compliance with data protection laws and the need for effective risk management and data protection strategies.