Unlocking New Doorways to Multi-channel Scams
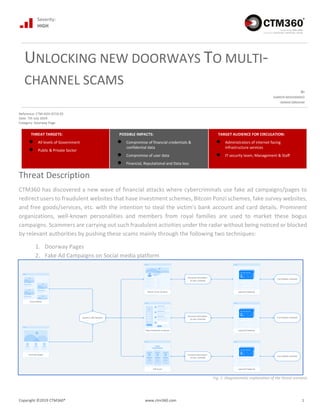
- 1. Severity: HIGH Copyright ©2019 CTM360® www.ctm360.com 1 UNLOCKING NEW DOORWAYS TO MULTI- CHANNEL SCAMS BY SAMEER MOHAMMAD ADNAN EBRAHIM Reference: CTM-ADV-0719-01 Date: 7th July 2019 Category: Doorway Page THREAT TARGETS: ● All levels of Government ● Public & Private Sector POSSIBLE IMPACTS: ● Compromise of financial credentials & confidential data ● Compromise of user data ● Financial, Reputational and Data loss TARGET AUDIENCE FOR CIRCULATION: ● Administrators of internet facing infrastructure services ● IT security team, Management & Staff Threat Description CTM360 has discovered a new wave of financial attacks where cybercriminals use fake ad campaigns/pages to redirect users to fraudulent websites that have investment schemes, Bitcoin Ponzi schemes, fake survey websites, and free goods/services, etc. with the intention to steal the victim's bank account and card details. Prominent organizations, well-known personalities and members from royal families are used to market these bogus campaigns. Scammers are carrying out such fraudulent activities under the radar without being noticed or blocked by relevant authorities by pushing these scams mainly through the following two techniques: 1. Doorway Pages 2. Fake Ad Campaigns on Social media platform Fig. 1: Diagrammatic explanation of the threat scenario
- 2. Severity: HIGH Copyright ©2019 CTM360® www.ctm360.com 2 Doorway pages Doorway pages, also called as bridge pages are performing ‘Spamdexing’ on the search engines. This is the art of having your website optimized or made attractive to the major search engines for optimal indexing. CTM360 has discovered that 99% of these doorway pages are registered on free domains. Ad campaigns leveraging free domains on ccTLDs such as .tk, .ga, .gq, .ml, .cf have been on the rise for the last few years. Fraudsters are bulk registering such domains and using them to generate revenue. Fig. 1: Doorway pages using financial brands 2. Fake Ad campaigns on Social Media Cybercriminals are using social media platforms like Facebook and Instagram to push ads to users globally. Facebook adverts, which points to fraudulent websites, tend to attract users by using prominent institutions like ministries, financial institutions, royal members and well-known personalities in the region and include fake quotes about their earnings and extravagant lifestyle. Facebook allows advertisers to use what is called ‘dark posts’. These are targeted ads on social media which unlike boosted and organic posts don’t appear on your timeline and feed of your followers. Dark posts are more formally known on Facebook as unpublished posts. They instead show up as sponsored content in the feeds of users who are specifically targeted.
- 3. Severity: HIGH Copyright ©2019 CTM360® www.ctm360.com 3 Fig. 3: Prominent personalities in the Middle East used in dark posts. Dynamic URL redirect Doorway pages/fake ads created and ingeniously placed by scammers online, redirect victims to a pool of different landing pages via dynamic URL redirects. This means that when the doorway page is accessed, the users are taken to a random landing page upon each visit. In some cases, users may also end up on different websites based on their search preferences. CTM360 have come across are listed below: - Free Gift sites which give mobile phones, airline tickets, watches - Free survey scam - Free airline ticket - Adult Websites - Various Investment schemes like Binary options, Bitcoin, Gold, trading =
- 4. Severity: HIGH Copyright ©2019 CTM360® www.ctm360.com 4 Fig 4. Fake Landing Page Bogus Checkout page Once a victim’s personal information is collected by the landing page, the user is taken to a bogus checkout page with a fake payment gateway. The payment gateway collects all the necessary card details including card number, expiry date and CVV. Fig 5. Bogus Payment gateway
- 5. Severity: HIGH Copyright ©2019 CTM360® www.ctm360.com 5 Conclusion In summary, the goal of these malicious operations is to attain a victim’s bank card details. The card details are captured by luring users to fake pages which the gets redirected (not accessible directly via URL) to bogus payment platforms. Once a victim’s card details have been collected, the criminals wait for a certain amount of time before any operations are conducted with the stolen card details. This could be purchases, ATM bulk amount withdrawals from different geolocations. This is usually carried out like a coordinated operation after enough victims have been compromised. These operations are usually conducted during off hours, public holidays and weekends to avoid any unnecessary detections. While some of these doorway pages are poorly designed and obvious scams, others are sophisticated and look very to the impersonated brand. Always look at website URL to make sure the site is legitimate before initiating communications or making any kind of financial transaction. CTM360's Cyber Blind Spot is actively monitoring these campaigns and other related threats and will continue to update once further information is available. Disclaimer The information contained in this document is meant to provide general guidance and brief information to the intended recipient pertaining to the incident and recommended action. Therefore, this information is provided "as is" without warranties of any kind, express or implied, including accuracy, timeliness, and completeness. Consequently, under NO condition shall CTM360®, its related partners, directors, principals, agents or employees be liable for any direct, indirect, accidental, special, exemplary, punitive, consequential or other damages or claims whatsoever including, but not limited to: loss of data, loss in profits/business, network disruption…etc., arising out of or in connection with this advisory. For more information: Email: monitor@ctm360.com Tel: (+973) 77 360 360
