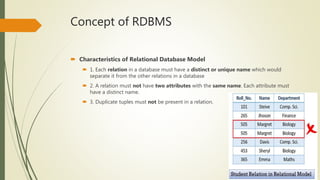
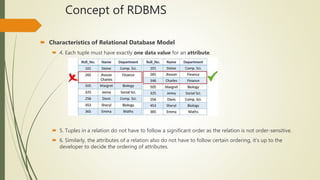
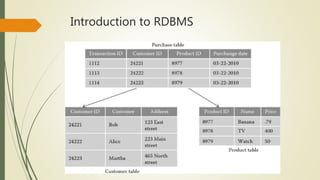
This document discusses relational database management systems (RDBMS). It defines RDBMS and describes their key characteristics, including that each relation must have a unique name, attributes cannot be duplicated, and tuples cannot be duplicated. Codd's 12 rules for RDBMS are presented, which a database must follow to be considered relational. Database security concepts like confidentiality, integrity and availability (CIA) are covered. Common security threats from people, malicious code and disasters are discussed. Requirements for database protection like authentication, authorization and data integrity are also outlined.