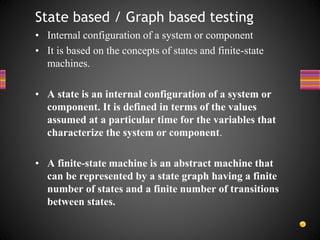
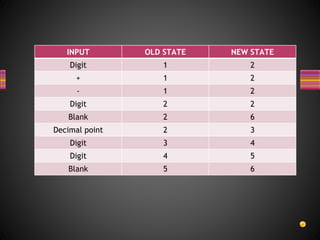
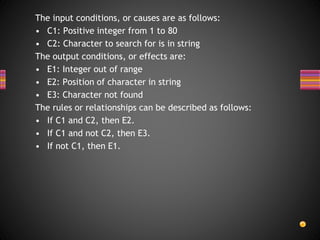
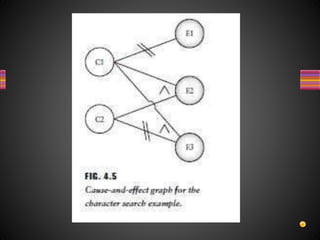
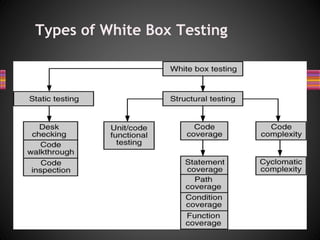
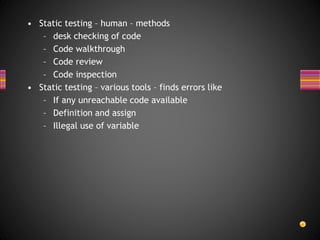
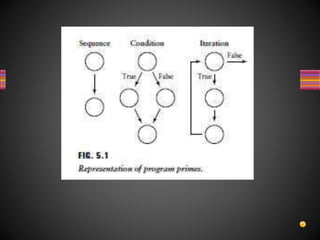
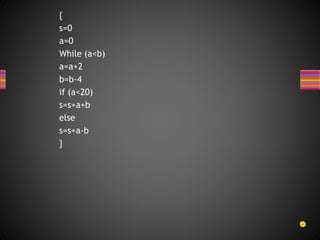
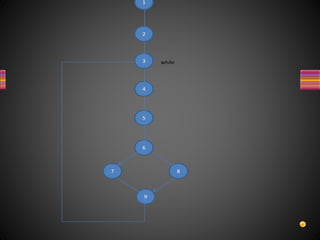
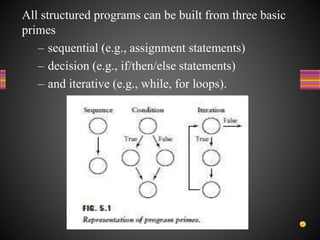
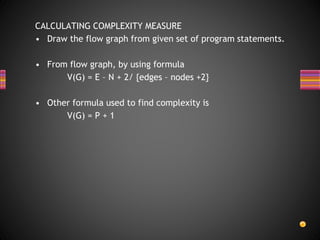
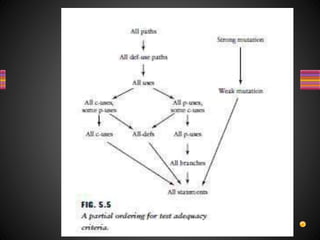
The document discusses various techniques for white box testing including static testing and structural testing. Static testing involves techniques like desk checking, code walkthroughs, and code inspections that do not require executing the code. Structural testing techniques execute the code and include unit testing, code coverage testing, and complexity testing. Code coverage criteria like statement coverage and branch coverage are discussed as ways to measure how thoroughly the code has been tested. Control flow graphs are presented as a way to represent program logic and control flow.