Embed presentation
Download as PDF, PPTX




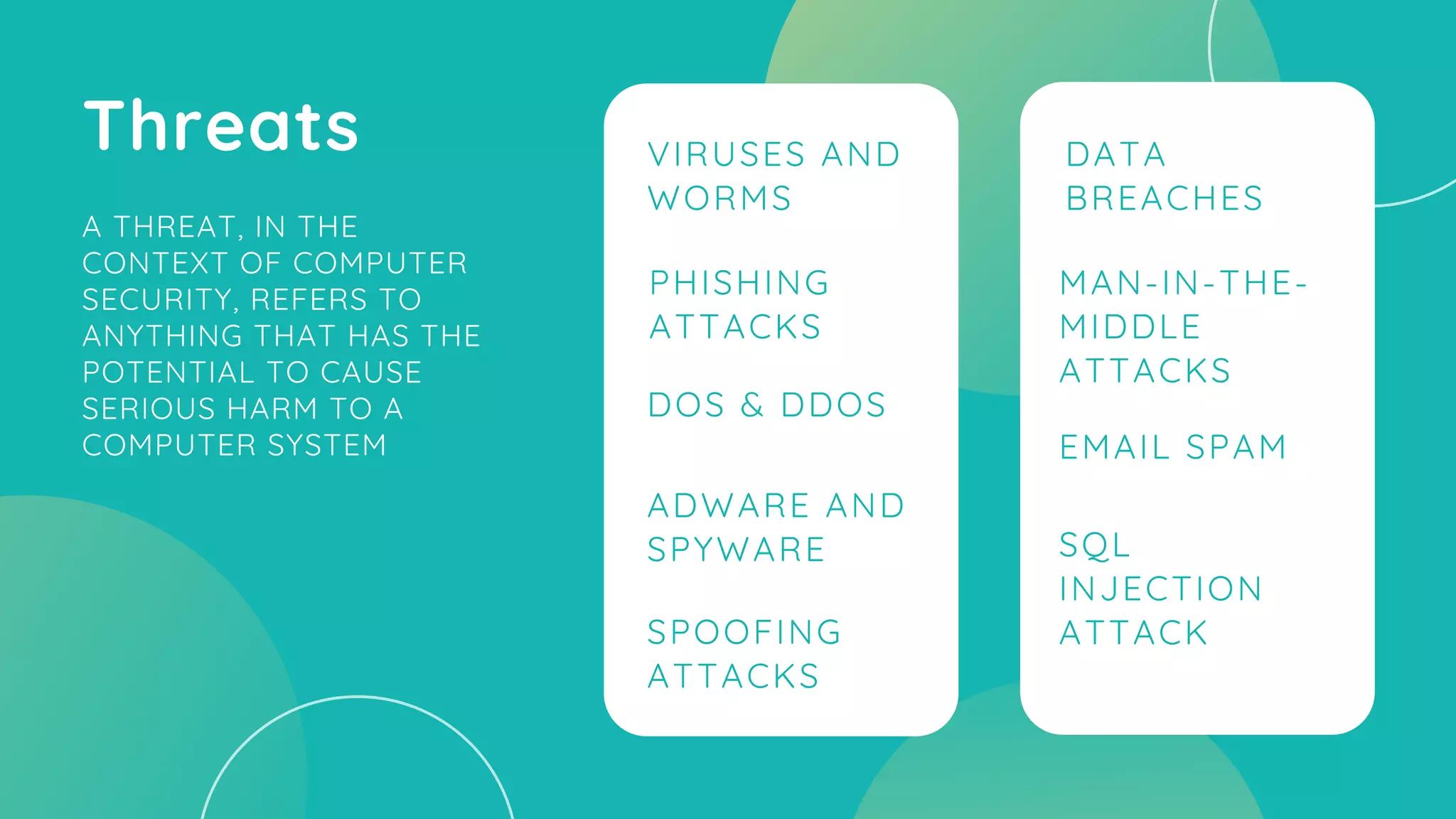







The document discusses unified threat management (UTM), which allows an administrator to monitor and manage various security applications and components through a single management console. It lists common threats like viruses, worms, data breaches, phishing attacks and DDoS attacks. The key features of UTM include firewall inspection, URL filtering, VPN, intrusion prevention and anti-virus/spam protection. UTM provides advantages such as reduced complexity, easy management and troubleshooting. However, it can also result in lower performance and vendor lock-in. Next generation UTM aims to address challenges of the modern internet.










