🚀 Understanding Collisions in Data Structures*🔍
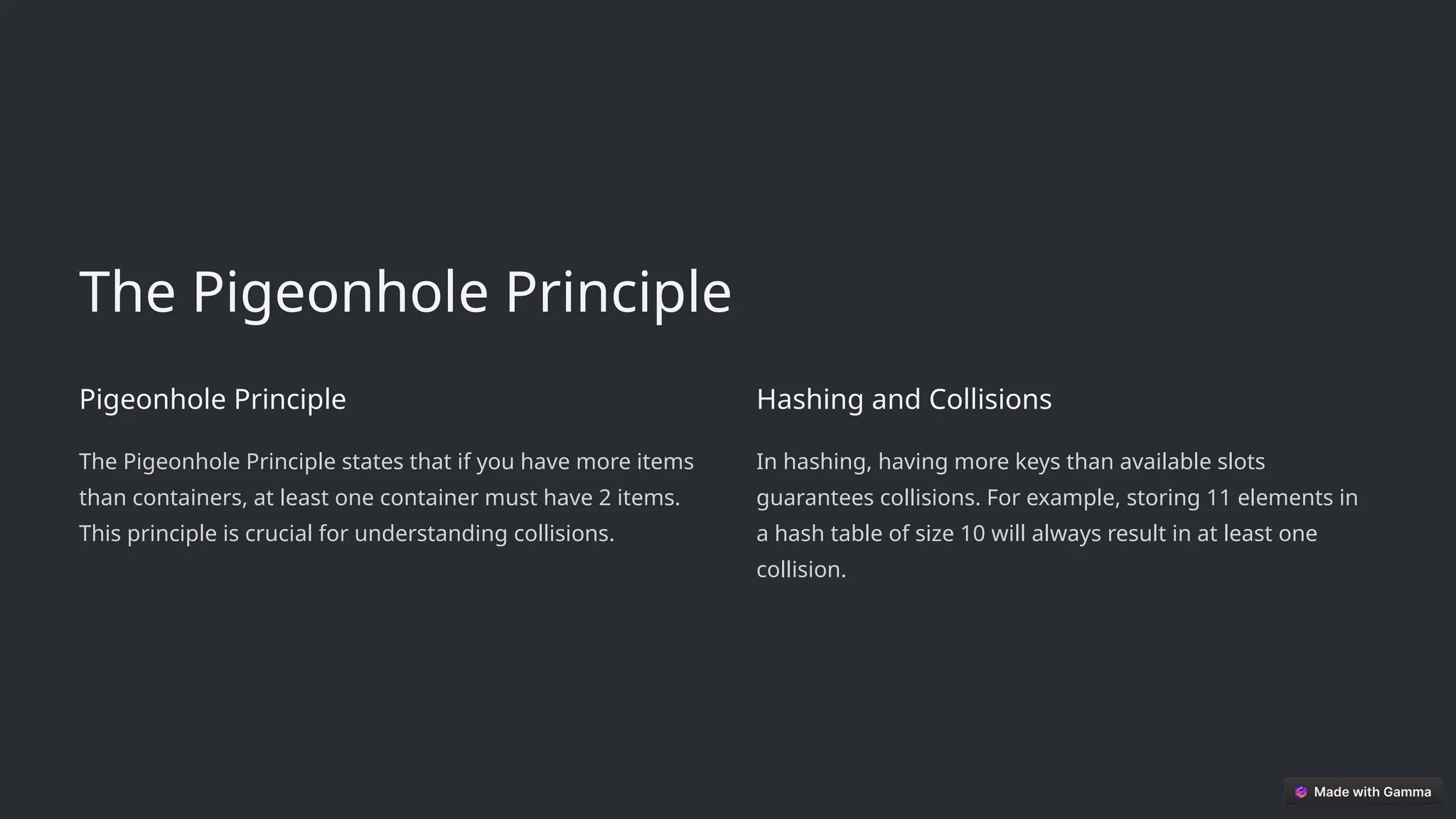
In data structures, especially hash tables, collisions occur when two different keys produce the same hash value, leading to data conflicts. How do we handle this efficiently?
🔹 Collision Handling Techniques:
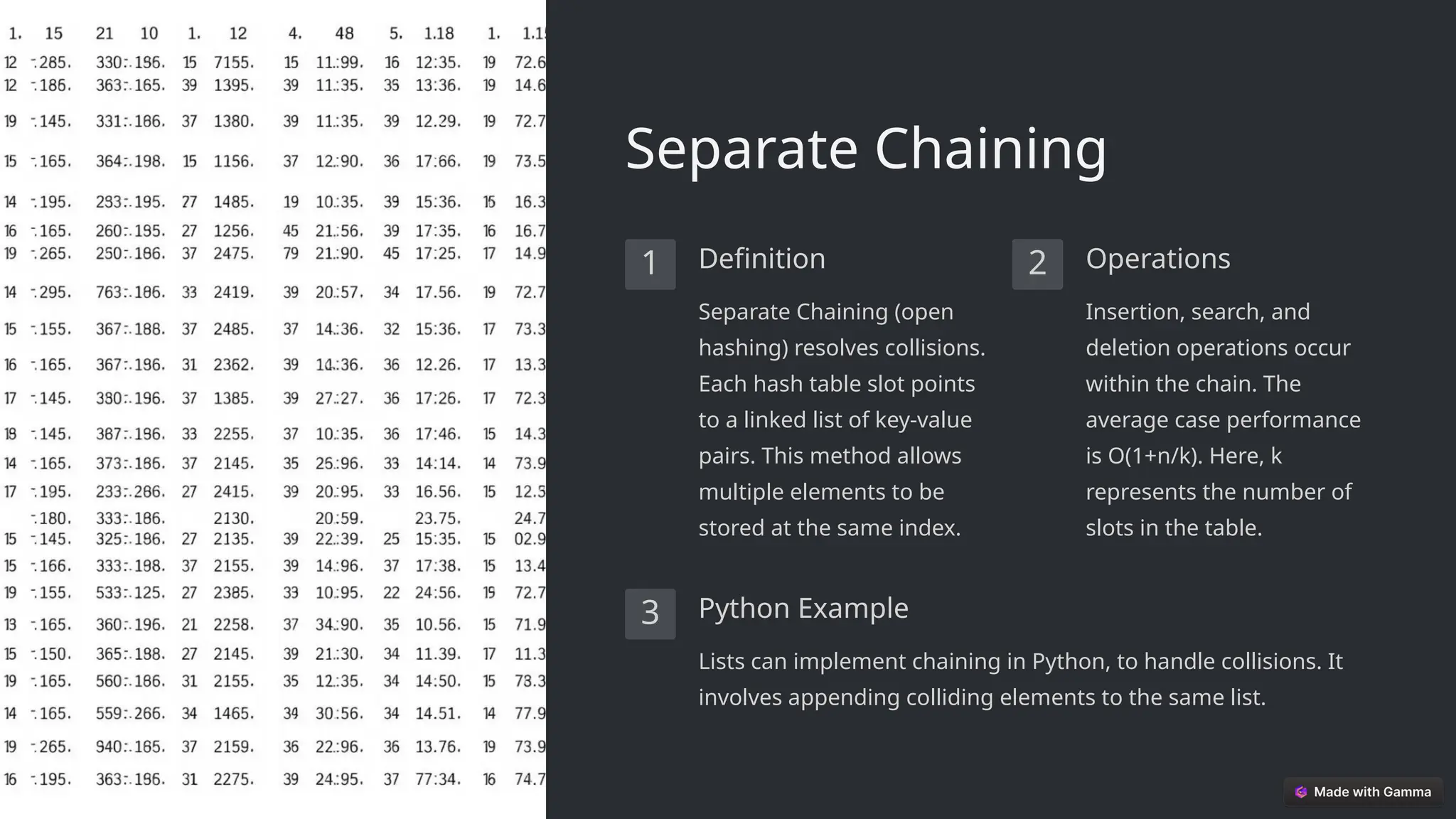
✅ Chaining: Storing multiple values at the same index using linked lists.
✅ Open Addressing: Finding another available slot using techniques like linear probing or quadratic probing.
✅ Double Hashing: Using a second hash function to resolve conflicts.
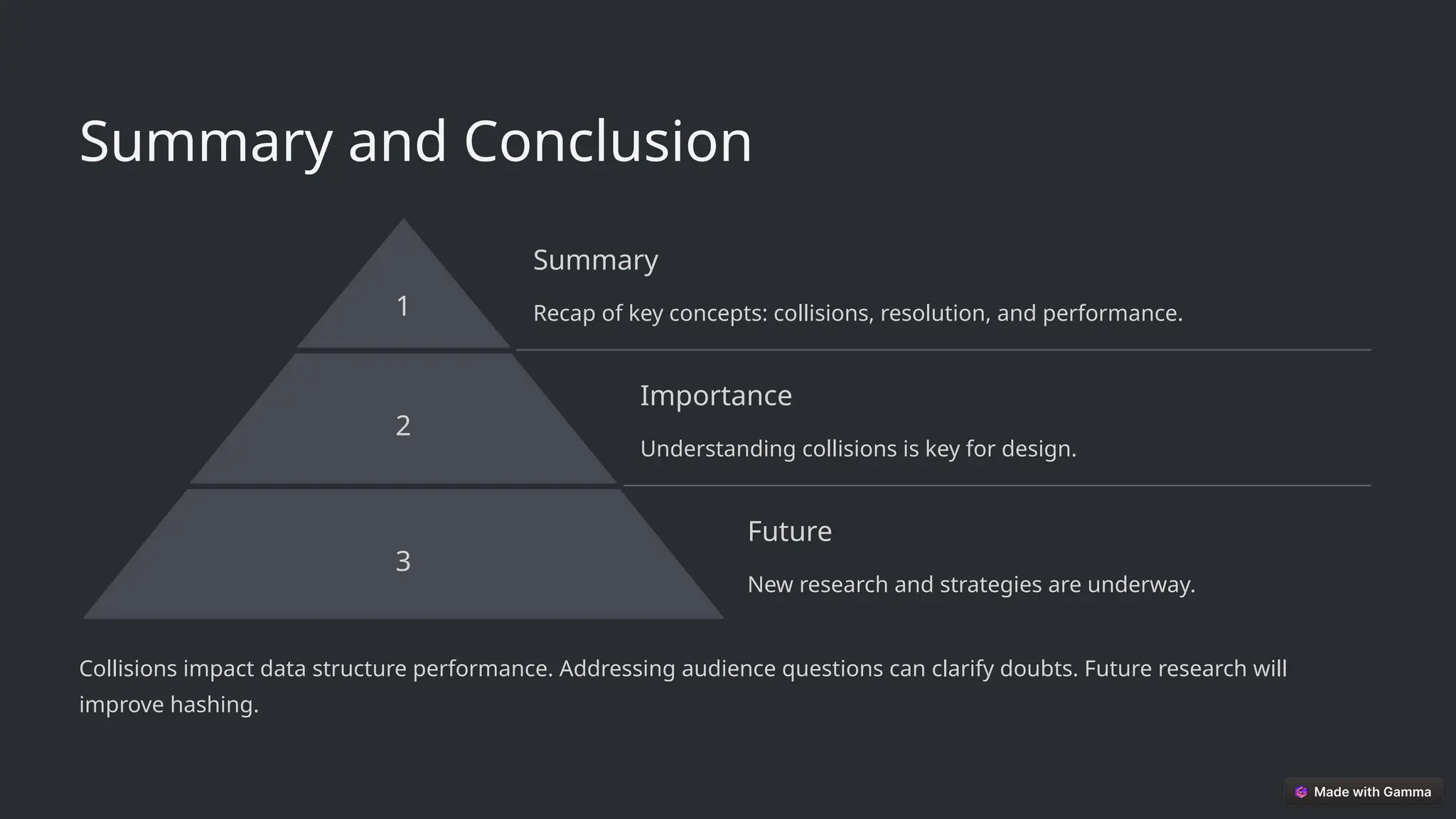
💡 Why is this important?
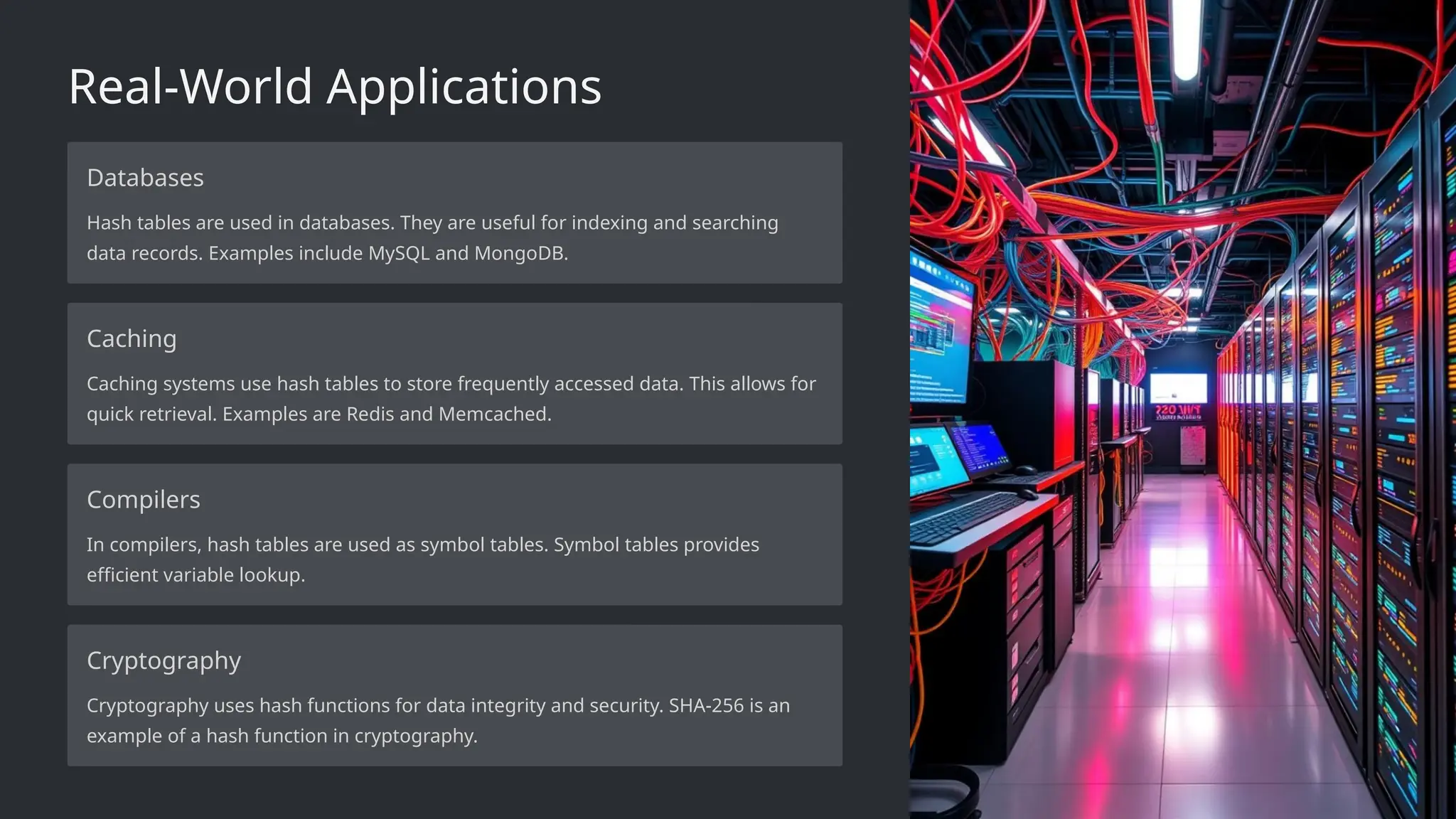
Collisions affect the efficiency of searching, inserting, and deletingoperations. Proper handling ensures faster data retrieval and optimal performance in applications like databases, caching, and cryptography.
📂 Want to learn more? Check out our presentation "Understanding Collisions in Data Structures" for a deep dive into real-world examples and best practices.
#DataStructures #Hashing #Collisions #ComputerScience #Programming #Algorithms