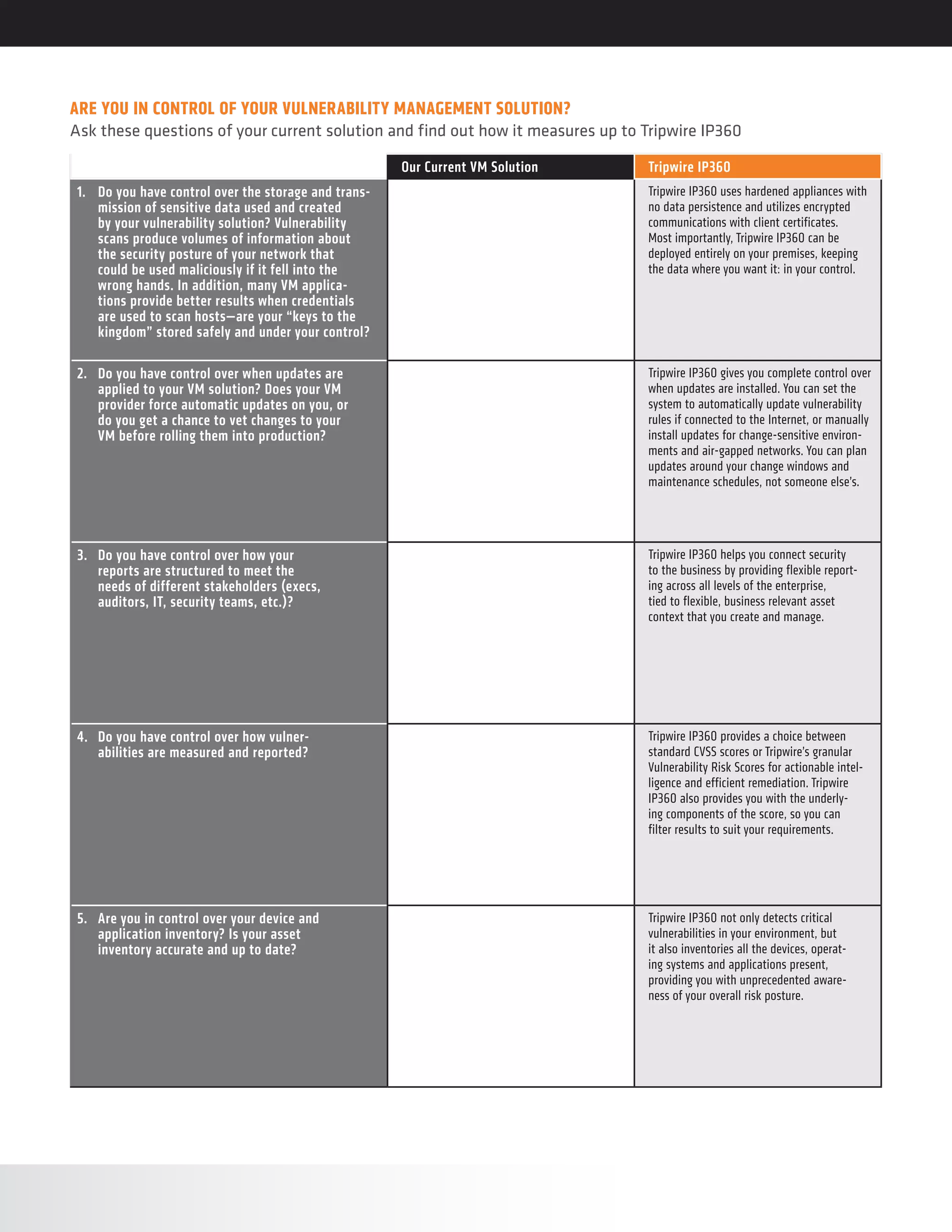
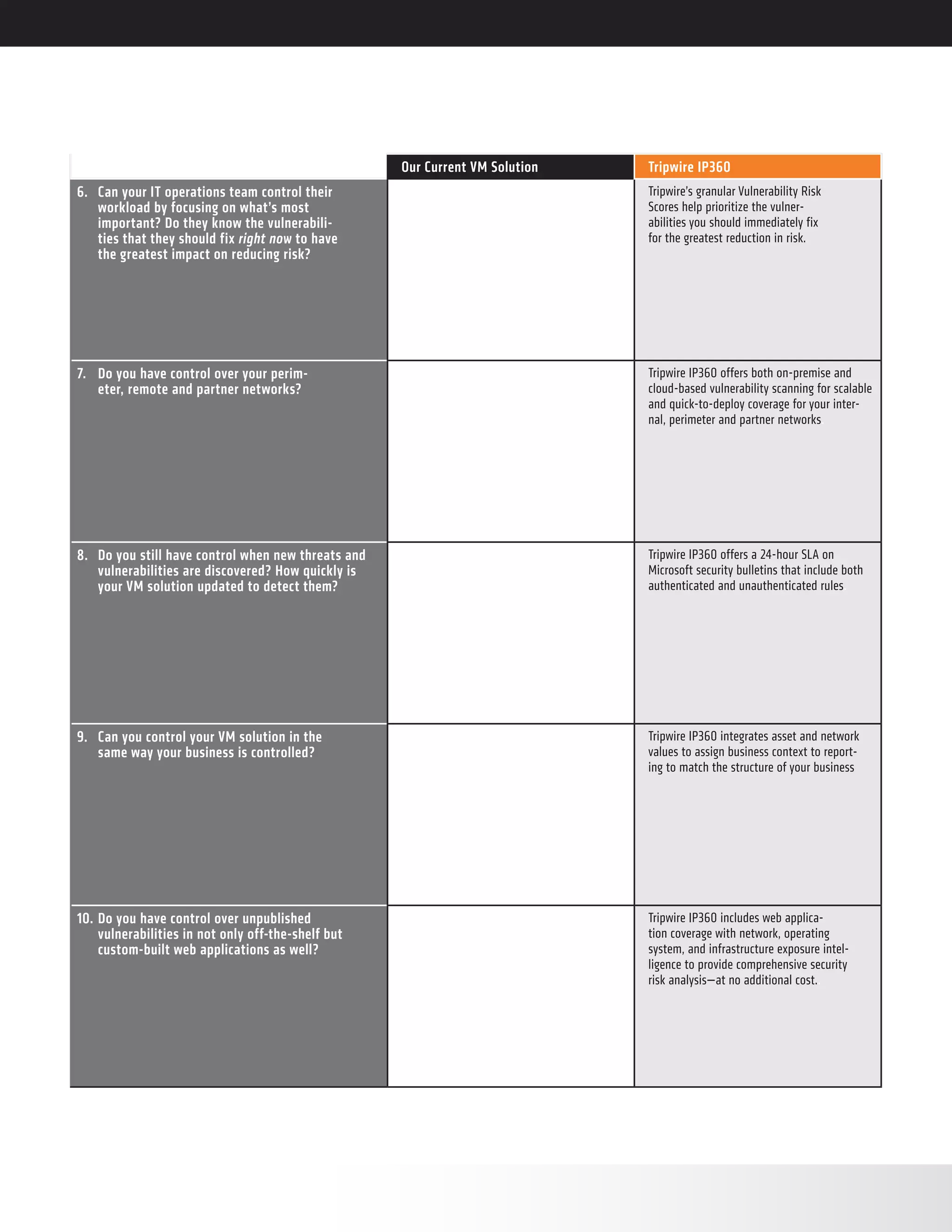
Tripwire IP360 is a vulnerability management solution that gives organizations control over their VM program. It addresses 10 key questions around control of sensitive data storage and updates, flexible reporting, accurate asset inventory, prioritizing vulnerabilities, and detecting both published and unpublished threats. Tripwire solutions are based on high-fidelity asset visibility and deep endpoint intelligence to enable security automation and comprehensive risk analysis.