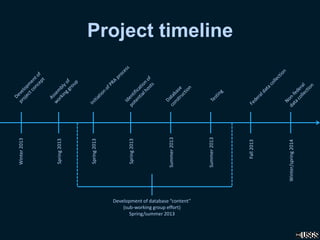
The document proposes creating a searchable vulnerability assessment database to address several issues:
1) There is currently no way to know about vulnerability assessments being conducted across different regions, species, and ecological elements.
2) New assessments are being undertaken without knowledge of previous relevant assessments.
3) Data and findings from completed assessments are not being shared across organizations.
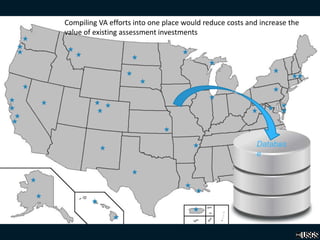
The database would compile vulnerability assessment efforts into a single location to reduce costs and increase the value of existing assessments by sharing information. It would include assessments from federal, state, and local agencies as well as universities and non-profits.