The Wannacry Effect - Provided by Raconteur
•
0 likes•44 views
The WannaCry ransomware attack in May 2017 was one of the largest and most widespread cyber attacks in history, infecting over 250,000 systems across 150 countries. It exploited a vulnerability in Microsoft Windows XP to encrypt files and demand ransom payments of $300 worth of bitcoin. Though victims were advised not to pay, some funds were sent to the attackers. The attack disrupted organizations like the UK's National Health Service, German railways, and Japanese companies like Hitachi and Nissan.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
What's hot
What's hot (20)
How to tackle the Ransomware threat "WannaCry" | Sysfore

How to tackle the Ransomware threat "WannaCry" | Sysfore
Dragonfly: Western energy sector targeted by sophisticated attack group

Dragonfly: Western energy sector targeted by sophisticated attack group
Crypto-Jacking, Ransomware & Worming Malware's Frightening Future (Keynote an...

Crypto-Jacking, Ransomware & Worming Malware's Frightening Future (Keynote an...
MLabs - Cyber Crime Tactics and Techniques Q2 2017

MLabs - Cyber Crime Tactics and Techniques Q2 2017
Protecting Your organization from WannaCry Ransomware

Protecting Your organization from WannaCry Ransomware
WannaCry ransomware outbreak - what you need to know

WannaCry ransomware outbreak - what you need to know
Shamoon attacks - Destructive malware targeting Middle East organizations

Shamoon attacks - Destructive malware targeting Middle East organizations
Istr number 23 internet security threat repor 2018 symantec

Istr number 23 internet security threat repor 2018 symantec
Lessons learned from 2017 cybersecurity incidents, 2018 and beyond

Lessons learned from 2017 cybersecurity incidents, 2018 and beyond
Similar to The Wannacry Effect - Provided by Raconteur
Briskinfosec - Threatsploit Report Augest 2021- Cyber security updates

Briskinfosec - Threatsploit Report Augest 2021- Cyber security updatesBriskinfosec Technology and Consulting
Similar to The Wannacry Effect - Provided by Raconteur (20)
Case Study: Wannacry Ransomware attacks Telefónica

Case Study: Wannacry Ransomware attacks Telefónica
Identify one cyberattack that occurred in the last 2 years. What cau.pdf

Identify one cyberattack that occurred in the last 2 years. What cau.pdf
Your Money or Your Data: Ransomware, Cyber Security and Today’s Threat Landsc...

Your Money or Your Data: Ransomware, Cyber Security and Today’s Threat Landsc...
External threats to information system: Malicious software and computer crimes

External threats to information system: Malicious software and computer crimes
Briskinfosec - Threatsploit Report Augest 2021- Cyber security updates

Briskinfosec - Threatsploit Report Augest 2021- Cyber security updates
In a digital age where computers are connected via network and data ar.pdf

In a digital age where computers are connected via network and data ar.pdf
More from Gary Chambers
More from Gary Chambers (20)
Recently uploaded
Recently uploaded (20)
The Parable of the Pipeline a book every new businessman or business student ...

The Parable of the Pipeline a book every new businessman or business student ...
5 Things You Need To Know Before Hiring a Videographer

5 Things You Need To Know Before Hiring a Videographer
Affordable Stationery Printing Services in Jaipur | Navpack n Print

Affordable Stationery Printing Services in Jaipur | Navpack n Print
Meaningful Technology for Humans: How Strategy Helps to Deliver Real Value fo...

Meaningful Technology for Humans: How Strategy Helps to Deliver Real Value fo...
Pitch Deck Teardown: RAW Dating App's $3M Angel deck

Pitch Deck Teardown: RAW Dating App's $3M Angel deck
ENTREPRENEURSHIP TRAINING.ppt for graduating class (1).ppt

ENTREPRENEURSHIP TRAINING.ppt for graduating class (1).ppt
RMD24 | Retail media: hoe zet je dit in als je geen AH of Unilever bent? Heid...

RMD24 | Retail media: hoe zet je dit in als je geen AH of Unilever bent? Heid...
Filing Your Delaware Franchise Tax A Detailed Guide

Filing Your Delaware Franchise Tax A Detailed Guide
12 Conversion Rate Optimization Strategies for Ecommerce Websites.pdf

12 Conversion Rate Optimization Strategies for Ecommerce Websites.pdf
Lars Winkelbauer — Sustainable Development in the Era of Air Cargo Technology

Lars Winkelbauer — Sustainable Development in the Era of Air Cargo Technology
What are the main advantages of using HR recruiter services.pdf

What are the main advantages of using HR recruiter services.pdf
20240425_ TJ Communications Credentials_compressed.pdf

20240425_ TJ Communications Credentials_compressed.pdf
The Wannacry Effect - Provided by Raconteur
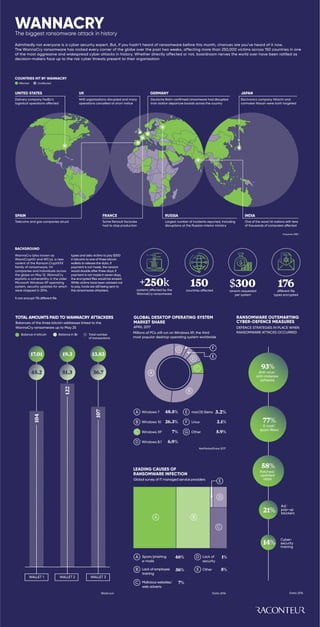
- 1. WANNACRY Admittedly not everyone is a cyber security expert. But, if you hadn’t heard of ransomware before this month, chances are you’ve heard of it now. The WannaCry ransomware has rocked every corner of the globe over the past two weeks, affecting more than 250,000 victims across 150 countries in one of the most aggressive and widespread cyber attacks in history. Whether directly affected or not, boardroom nerves the world over have been rattled as decision-makers face up to the risk cyber threats present to their organisation Kaspersky/BBC BACKGROUND WannaCry (also known as WanaCrypt0r and WCry), a new varient of the Ransom.CryptXXX family of ransomware, hit companies and individuals across the globe on May 12. WannaCry exploits a vulnerability in the older Microsoft Windows XP operating system, security updates for which were stopped in 2014. It can encrypt 176 different file types and asks victims to pay $300 in bitcoins to one of three bitcoin wallets to release the data. If payment is not made, the ransom would double after three days; if payment is not made in seven days, the encrypted files would be erased. While victims have been advised not to pay, funds are still being sent to the ransomware attackers. UNITED STATES UK GERMANY JAPAN RUSSIA INDIA Delivery company FedEx’s logistical operations affected NHS organisations disrupted and many operations cancelled at short notice Deutsche Bahn confirmed ransomware had disrupted train station departure boards across the country FRANCE Some Renault factories had to stop production Electronics company Hitachi and carmaker Nissan were both targeted Largest number of incidents reported, including disruptions at the Russian interior ministry One of the worst hit nations with tens of thousands of computers affected 150countries affected SPAIN Telecoms and gas companies struck Unaffected $300ransom requested per system Affected 176different file types encrypted +250ksystems affected by the WannaCry ransomware COUNTRIES HIT BY WANNACRY The biggest ransomware attack in history RANSOMWARE OUTSMARTING CYBER-DEFENCE MEASURES Datto 2016 DEFENCE STRATEGIES IN PLACE WHEN RANSOMWARE ATTACKS OCCURRED Bitref.com LEADING CAUSES OF RANSOMWARE INFECTION TOTAL AMOUNTS PAID TO WANNACRY ATTACKERS GLOBAL DESKTOP OPERATING SYSTEM MARKET SHARE APRIL 2017 Global survey of IT managed service providers Balances of the three bitcoin addresses linked to the WannaCry ransomware up to May 25 Datto 2016 NetMarketShare 2017 Anti-virus/ anti-malware software E-mail/ spam filters Patched/ updated apps Ad/ pop-up blockers Cyber- security training 93% 77% 58% 21% 14% Millions of PCs still run on Windows XP, the third most popular desktop operating system worldwide A B C D E F WALLET 3 G Spam/phishing e-mails WALLET 1 A 46% Lack of security D 1% Windows 7 macOS SierraA E48.5% 3.2% WALLET 2 Windows 10B 26.3% LinuxF 2.1% Windows XPC OtherG 5.9%7% Malicious websites/ web adverts C 7% Windows 8.1D 6.9% A B C E D 104 122 107 Balance in bitcoin Balance in $k Total number of transactions 17.01 45.2 19.3 51.3 13.83 36.7 Lack of employee training B 36% OtherE 5%
