The Enemy Within IoT - A Mirai DDoS Timeline
•
4 likes•3,023 views
A new devastating tool by the name of Mirai was used in the attack on Dyn - the largest DDoS in history. It achieved this by using Internet of Things (IoT) devices as a botnet to great effect. How did we get here?
Report
Share
Report
Share
Download to read offline
Recommended
Power of Pixels - Abridged

By 2019, we will be staring at a Data Explosion like none before. Big Data Big Bang is around the corner. This presentation is a thought starter that aim to give an idea of things to come from Internet of things(IoT) to Internet of everything (IoE). Are companies ready to harness the power? Are data vendors equipped to take on this challenge? What do they need to start doing? How do they appease the sometimes conflicting needs of CIO versus the CMO? All this and more.
[TestWarez 2017] Zmiana paradygmatu na scenie cyberataków i testowania zabezp...![[TestWarez 2017] Zmiana paradygmatu na scenie cyberataków i testowania zabezp...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[TestWarez 2017] Zmiana paradygmatu na scenie cyberataków i testowania zabezp...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[TestWarez 2017] Zmiana paradygmatu na scenie cyberataków i testowania zabezp...Stowarzyszenie Jakości Systemów Informatycznych (SJSI)
W ostatnich kilkunastu miesiącach mogliśmy obserwować, że scenariusze filmów science-fiction stawały się realnymi nagłówkami wiadomości. Wiele scenariuszy ataków wydarzyło się po raz pierwszy w realnym świecie. Wiele z nich oznacza nie tylko nowe techniki, ale wręcz zmianę paradygmatu cyberbezpieczeństwa. Internet rzeczy, wykorzystywanie hakerów do walki politycznej czy zupełnie nowa klasa ataków na algorytmy uczenia maszynowego, to tylko niektóre przykłady. Jako Eksperci i testerzy zabezpieczeń, musimy być gotowi.Tk Keanini, Cisco Systems: Not So Quiet on the Internet Front

Tk Keanini, Cisco Systems: Not So Quiet on the Internet Front at W2OatSXSW's PreCommerce Summit
Symantec Website Security Threats: March 2014 update.

Join us each month on https://www.brighttalk.com/channel/6331 for the Symantec Website security threat update webinar a short 25 mins of web threats and security update news.
Top 15 security predictions for 2017

Here are some of the best guesses about what we will see in 2017 from several dozen vendors and analysts. There are many more than 15 predictions out there, of course, but these are the ones we heard most frequently.
The Wannacry Effect - Provided by Raconteur

An overview provided by Raconteur on the effect of Wannacry on worldwide business
Recommended
Power of Pixels - Abridged

By 2019, we will be staring at a Data Explosion like none before. Big Data Big Bang is around the corner. This presentation is a thought starter that aim to give an idea of things to come from Internet of things(IoT) to Internet of everything (IoE). Are companies ready to harness the power? Are data vendors equipped to take on this challenge? What do they need to start doing? How do they appease the sometimes conflicting needs of CIO versus the CMO? All this and more.
[TestWarez 2017] Zmiana paradygmatu na scenie cyberataków i testowania zabezp...![[TestWarez 2017] Zmiana paradygmatu na scenie cyberataków i testowania zabezp...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[TestWarez 2017] Zmiana paradygmatu na scenie cyberataków i testowania zabezp...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[TestWarez 2017] Zmiana paradygmatu na scenie cyberataków i testowania zabezp...Stowarzyszenie Jakości Systemów Informatycznych (SJSI)
W ostatnich kilkunastu miesiącach mogliśmy obserwować, że scenariusze filmów science-fiction stawały się realnymi nagłówkami wiadomości. Wiele scenariuszy ataków wydarzyło się po raz pierwszy w realnym świecie. Wiele z nich oznacza nie tylko nowe techniki, ale wręcz zmianę paradygmatu cyberbezpieczeństwa. Internet rzeczy, wykorzystywanie hakerów do walki politycznej czy zupełnie nowa klasa ataków na algorytmy uczenia maszynowego, to tylko niektóre przykłady. Jako Eksperci i testerzy zabezpieczeń, musimy być gotowi.Tk Keanini, Cisco Systems: Not So Quiet on the Internet Front

Tk Keanini, Cisco Systems: Not So Quiet on the Internet Front at W2OatSXSW's PreCommerce Summit
Symantec Website Security Threats: March 2014 update.

Join us each month on https://www.brighttalk.com/channel/6331 for the Symantec Website security threat update webinar a short 25 mins of web threats and security update news.
Top 15 security predictions for 2017

Here are some of the best guesses about what we will see in 2017 from several dozen vendors and analysts. There are many more than 15 predictions out there, of course, but these are the ones we heard most frequently.
The Wannacry Effect - Provided by Raconteur

An overview provided by Raconteur on the effect of Wannacry on worldwide business
10 Signs data privacy is the new Wild West 

These slides provide insight into apps, web services, and devices designed to go unnoticed as they capture your sensitive personal data.
Why Privacy matters? 

Why our privacy is important for us and how our privacy has been compromised. Read privacy policy and terms and condition properly before using any services. ways of secure communication
Critical infrastructures brochure

Until recently, Cyber attacks were aimed at Service Providers and Enterprises. The agenda was mostly
economic – to hurt customers and ruin reputations. An infrastructure with such vulnerability also places their
customers’ valuable data at risk. Today, the situation is even more severe. Critical infrastructures are now the
preferred target for cyber terrorists who want to wage war within the comfort of their homes. If not addressed
properly, the massive increase in such attacks will reach new peaks, with catastrophic consequences.
Internet of Things, Connected Device Growth

IoT to pass mobile phones
as the largest category of connected devices by 2018. Overview of 'massive' and 'critical' applications of IoT and design considerations. Presentation by Slade Sherman of Creator Global, based on research by Ericsson Mobility. Industrial Design for Internet of Things.
Why Digital Forensics as a Career? 

We are living in a digital world rife with risks. This has led to a rise in digital crimes, increasing the need for digital forensics in turn.
Find out why you should choose a career in digital forensics: https://lnkd.in/ex2KmZp
Cisco Visual Networking Index Graphic--By the Numbers

Cisco Visual Networking Index Graphic--By the Numbers
Check out this graphical overview of the Visual Networking Index (VNI) Global Mobile Data Traffic high-level data points.
For more info, read http://cs.co/mvnib . Also, follow #VNI on Twitter to see what others are saying about this Visual Networking Index (VNI) forecast.
FIWARE MEXICO WorkShop 2016 - 7. Example of FIWARE Applications by INFOTEC

INFOTEC presents some FIWARE application developed in Mexico.
Palo Alto Networks 2016 Cybersecurity Predictions

Palo Alto Networks experts make their predictions for cybersecurity trends in 2016.
Introducción a Briar: inter-conectarse sin internet

Minitaller para instalar y aprender a usar Briar, una aplicación para conexión de dispositivo a dispositivo que no requiere servidores de internet. Impartido por Torsten Grote
Recap of 2017's biggest cyber-incidents so far

In today’s digital world, online safety should be of paramount concern for all individuals and organizations because the threats posed by cyber criminals can’t be ignored.
Let this recap of 2017's biggest cyber-incidents so far serve as a reminder and learn from this.
The Impact of IoT on Enterprise Wi-Fi by AirTight Networks via Slideshare

Companion to http://blog.airtightnetworks.com/impact-iot-enterprise-wi-fi "The Impact of IoT on Enterprise Wi-Fi." via AirTight blog.
Choose your wireless network carefully. Cloud and APs are not all created equal.
Clearly we’re not in Kansas anymore … According to IDC, the growing global Internet of Things (IoT) market is on course to hit $7.1 trillion by 2020. With the rapid rise of connected devices in the IoT landscape there is growing concern about elevated security risks associated with the sheer volume of new devices coming online.
John harrobin verizon wireless and skype to have news conference at ctia

Verizon Wireless and Skype To Have News Conference At CTIA
CE Cybersecurity Trends and Strategies for Hosting in the Cloud

Why does security feel like the most frustrating challenge in government IT? In part, because security in a cloud-first, mobile-first world calls for new approaches. Data is accessed, used and shared on-premises and in the cloud–erasing traditional security boundaries.
In this webinar, we’ll examine current trends in cybersecurity and some resulting strategy shifts that have the potential to greatly enhance public sector organizations’ ability to balance risk and access, better detect and respond to attacks and just make faster and more coordinated cybersecurity decisions overall. Finally, we’ll look at a common set of attacks occurring specifically in state and local government and steps you can take right now to help mitigate these.
Join Dean Iacovelli, Director for Secure Enterprise at Microsoft, as he discusses current trends and strategies to mitigate your cybersecurity risk.
Ijscs

International Journal of Security and Communication Networks(IJSCS) is a bi monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of Security and Communication Networks. The journal focuses on all technical and practical aspects of Security and Communication Networks. The goal of this journal is to bring together researchers and practitioners from academia and industry to focus on advanced Security and Communication Networks concepts and establishing new collaborations in these areas.
HR's Critical Role in Protecting Company Data

Parsons Behle & Latimer Employment Law Seminar - Boise, Idaho - October 19, 2017
Crypto-Jacking, Ransomware & Worming Malware's Frightening Future (Keynote an...

In the last nine months, crypto-mining malware and crypto-jacking have taken center stage in cybercrime news. We’ll discuss the most recent events and see how this links to ransomware, which dominated the cybercrime news last year, where one outbreak cost seven companies over one billion dollars.
Both crypto-mining malware and ransomware, aside from gathering headlines, demonstrate that cybercriminals and nation state actors are building capabilities for worming malware that could have the ability to do far greater damage than has yet been seen.
Come to this talk, learn what’s been going on, where it’s likely going, and how to avoid being a victim of a headline-generating event.
Cybersecurity awesome mix vol. II

A collection of musical masterpieces that may have very well been inspired by the best (or the worst, it depends how you look at it) hacks recorded in the second half of 2016.
More Related Content
What's hot
10 Signs data privacy is the new Wild West 

These slides provide insight into apps, web services, and devices designed to go unnoticed as they capture your sensitive personal data.
Why Privacy matters? 

Why our privacy is important for us and how our privacy has been compromised. Read privacy policy and terms and condition properly before using any services. ways of secure communication
Critical infrastructures brochure

Until recently, Cyber attacks were aimed at Service Providers and Enterprises. The agenda was mostly
economic – to hurt customers and ruin reputations. An infrastructure with such vulnerability also places their
customers’ valuable data at risk. Today, the situation is even more severe. Critical infrastructures are now the
preferred target for cyber terrorists who want to wage war within the comfort of their homes. If not addressed
properly, the massive increase in such attacks will reach new peaks, with catastrophic consequences.
Internet of Things, Connected Device Growth

IoT to pass mobile phones
as the largest category of connected devices by 2018. Overview of 'massive' and 'critical' applications of IoT and design considerations. Presentation by Slade Sherman of Creator Global, based on research by Ericsson Mobility. Industrial Design for Internet of Things.
Why Digital Forensics as a Career? 

We are living in a digital world rife with risks. This has led to a rise in digital crimes, increasing the need for digital forensics in turn.
Find out why you should choose a career in digital forensics: https://lnkd.in/ex2KmZp
Cisco Visual Networking Index Graphic--By the Numbers

Cisco Visual Networking Index Graphic--By the Numbers
Check out this graphical overview of the Visual Networking Index (VNI) Global Mobile Data Traffic high-level data points.
For more info, read http://cs.co/mvnib . Also, follow #VNI on Twitter to see what others are saying about this Visual Networking Index (VNI) forecast.
FIWARE MEXICO WorkShop 2016 - 7. Example of FIWARE Applications by INFOTEC

INFOTEC presents some FIWARE application developed in Mexico.
Palo Alto Networks 2016 Cybersecurity Predictions

Palo Alto Networks experts make their predictions for cybersecurity trends in 2016.
Introducción a Briar: inter-conectarse sin internet

Minitaller para instalar y aprender a usar Briar, una aplicación para conexión de dispositivo a dispositivo que no requiere servidores de internet. Impartido por Torsten Grote
Recap of 2017's biggest cyber-incidents so far

In today’s digital world, online safety should be of paramount concern for all individuals and organizations because the threats posed by cyber criminals can’t be ignored.
Let this recap of 2017's biggest cyber-incidents so far serve as a reminder and learn from this.
The Impact of IoT on Enterprise Wi-Fi by AirTight Networks via Slideshare

Companion to http://blog.airtightnetworks.com/impact-iot-enterprise-wi-fi "The Impact of IoT on Enterprise Wi-Fi." via AirTight blog.
Choose your wireless network carefully. Cloud and APs are not all created equal.
Clearly we’re not in Kansas anymore … According to IDC, the growing global Internet of Things (IoT) market is on course to hit $7.1 trillion by 2020. With the rapid rise of connected devices in the IoT landscape there is growing concern about elevated security risks associated with the sheer volume of new devices coming online.
John harrobin verizon wireless and skype to have news conference at ctia

Verizon Wireless and Skype To Have News Conference At CTIA
CE Cybersecurity Trends and Strategies for Hosting in the Cloud

Why does security feel like the most frustrating challenge in government IT? In part, because security in a cloud-first, mobile-first world calls for new approaches. Data is accessed, used and shared on-premises and in the cloud–erasing traditional security boundaries.
In this webinar, we’ll examine current trends in cybersecurity and some resulting strategy shifts that have the potential to greatly enhance public sector organizations’ ability to balance risk and access, better detect and respond to attacks and just make faster and more coordinated cybersecurity decisions overall. Finally, we’ll look at a common set of attacks occurring specifically in state and local government and steps you can take right now to help mitigate these.
Join Dean Iacovelli, Director for Secure Enterprise at Microsoft, as he discusses current trends and strategies to mitigate your cybersecurity risk.
Ijscs

International Journal of Security and Communication Networks(IJSCS) is a bi monthly open access peer-reviewed journal that publishes articles which contribute new results in all areas of Security and Communication Networks. The journal focuses on all technical and practical aspects of Security and Communication Networks. The goal of this journal is to bring together researchers and practitioners from academia and industry to focus on advanced Security and Communication Networks concepts and establishing new collaborations in these areas.
What's hot (16)
Cisco Visual Networking Index Graphic--By the Numbers

Cisco Visual Networking Index Graphic--By the Numbers
FIWARE MEXICO WorkShop 2016 - 7. Example of FIWARE Applications by INFOTEC

FIWARE MEXICO WorkShop 2016 - 7. Example of FIWARE Applications by INFOTEC
Introducción a Briar: inter-conectarse sin internet

Introducción a Briar: inter-conectarse sin internet
The Impact of IoT on Enterprise Wi-Fi by AirTight Networks via Slideshare

The Impact of IoT on Enterprise Wi-Fi by AirTight Networks via Slideshare
John harrobin verizon wireless and skype to have news conference at ctia

John harrobin verizon wireless and skype to have news conference at ctia
CE Cybersecurity Trends and Strategies for Hosting in the Cloud

CE Cybersecurity Trends and Strategies for Hosting in the Cloud
Similar to The Enemy Within IoT - A Mirai DDoS Timeline
HR's Critical Role in Protecting Company Data

Parsons Behle & Latimer Employment Law Seminar - Boise, Idaho - October 19, 2017
Crypto-Jacking, Ransomware & Worming Malware's Frightening Future (Keynote an...

In the last nine months, crypto-mining malware and crypto-jacking have taken center stage in cybercrime news. We’ll discuss the most recent events and see how this links to ransomware, which dominated the cybercrime news last year, where one outbreak cost seven companies over one billion dollars.
Both crypto-mining malware and ransomware, aside from gathering headlines, demonstrate that cybercriminals and nation state actors are building capabilities for worming malware that could have the ability to do far greater damage than has yet been seen.
Come to this talk, learn what’s been going on, where it’s likely going, and how to avoid being a victim of a headline-generating event.
Cybersecurity awesome mix vol. II

A collection of musical masterpieces that may have very well been inspired by the best (or the worst, it depends how you look at it) hacks recorded in the second half of 2016.
Briskinfosec - Threatsploit Report Augest 2021- Cyber security updates

Briskinfosec - Threatsploit Report Augest 2021- Cyber security updatesBriskinfosec Technology and Consulting
Welcome to the Threatsploit Report of covering some of the important cybersecurity events, incidents and exploits that occurred this month such as Application Security, Mobile App Security, Network Security, Website Security, API Security, Cloud Security, Host Level Security, Cyber Intelligence, Thick Client Security, Threat Vulnerability, Database Security, IOT Security, Wireless Security.Cyber Security

Cybersecurity refers to a set of techniques used to protect the integrity of networks, programs and data from attack, damage or unauthorized access.
The Real Threat of CyberattacksEmmanuel .docx

The Real Threat of Cyberattacks
Emmanuel Domenech
University of Maryland
The Real Threat of Cyberattacks
Hackers, in the past have developed a modern and sophisticated way of creating income for themselves. Hackers as the top of the line in software development, have move up the chain of technology. Adopting cloud computing, artificial intelligence, software as a service and encryption, they created a non-stop threat to major companies. Most of the companies fail to take the most basic protective measures against cyberattacks. While the cybercriminals use simple and advance technology to target unsecure organizations, is unlikely for them to stop this attack. Hackers understand the power they possess, it is too easy and rewarding, and the chances of being punished is too low. The Center for Strategic and International Studies (CSIS) estimated that cybercrime costs the world’s economy almost $500 billion, or about 0.7% of global income (Lewis, 2018). These numbers are positioning cybercrimes on the top profitable employment. People and companies adopt new advance technology, more protective software’s and more sophisticated. The problem is like the experts on security protocols continue to update their tools, hackers fast learn how to break them. There are high expectations on cybercrimes to increase, and with the help of new and easy devices like Internet of Things (IoT). We have seen that IoT is used not only to steal personal information or to gain access to data or networks, but also to enable Distribute Denial-of-Service (DDoS) attacks. The impacts of cyberattacks on nation’s economy includes global costs of cyberattacks; ransomware attack implications; additional costs on financial institutions, while the recent cyberattacks being WannaCry; NotPetya; GitHub DDoS; Yahoo attack aided by the tor network, bitcoin and cyberattack-as-a-service.
One of the impacts of cyberattacks is the global cost. The cyberspace has created an avenue for criminals to launch their criminal activities with the help of different cybercrimes. Reports from British officials indicate that almost half of reported crimes in the United Kingdom are cyber-related. The global cost of cybercrime has risen to a staggering $600 billion from recent CSIS estimates (Lewis, 2018). In 2014, cybercrime cost the global economy 0.62 percent of the global Gross Domestic Product (GDP). In 2016, cybercrime cost the global economy 0.8 percent of the global GDP (Lewis, 2018). The global cost of cybercrime is brought about by the following elements: intellectual property loss and loss of business confidential data; hacked personal identifiable information leading to fraud and financial crimes; high costs to secure networks and systems; companies risk reputational damage and the cost associated with opportunity costs that a business suffers after cyberattacks like lack of trust.
Another economic threat of cyberattacks is estimation issues. The cost estimation of cyberattacks.
Digital Threat Landscape

This brief presentation gives you a quick overview on how the Cyber Threat Landscape is shaping up in 2017 for individuals and business owners alike. It puts forth some important trends and predictions.
When web 2.0 sneezes, everyone gets sick

Web 2.0 applications have become increasingly popular among Internet users in the past few years. This trend is very unlikely to come to an end soon. More and more 'classic' websites are shifting towards web 2.0 concepts, start-ups are all about web 2.0 and new users are adopting the web 2.0 lifestyle every day.
This paper aims to address the following questions:
What exactly is web 2.0?
What are the concepts and technologies that make web 2.0 what it is?
Why does web 2.0 attract malware authors?
How did malware spread over the Internet before web 2.0?
What are the new attack vectors created by web 2.0 technologies?
What social engineering tactics emerge over the web 2.0 concepts?
How dangerous is the combination of human & technological vulnerabilities?
Are web 2.0 attacks more efficient?
How difficult is it to protect ourselves?
How are web 2.0 threats going to evolve?
Web 2.0 applications are not only being used at home, but also in the corporate environment. The new attack vectors are raising the stakes, both for malware authors and security professionals. The user is somewhere in between the two sides, unwittingly helping the attackers while also suffering from the attacks.
News Bytes

News Byte session on 29 oct 2017 at Null Meet Bhopal.
In which we discuss about latest attacks , ransomware and some vulnerability
Case Study: Wannacry Ransomware attacks Telefónica

Brief study of Wannacry and the massive attack that took place on May 12, 2017, where the Spanish telecommunications company Telefónica was one of the first victims of this ransomware. The timeline of the events, the vulnerabilities of the company, the costs left by the attack and the possible prevention measures are reviewed.
Author: Sergio Renteria Nuñez
Similar to The Enemy Within IoT - A Mirai DDoS Timeline (20)
Crypto-Jacking, Ransomware & Worming Malware's Frightening Future (Keynote an...

Crypto-Jacking, Ransomware & Worming Malware's Frightening Future (Keynote an...
Briskinfosec - Threatsploit Report Augest 2021- Cyber security updates

Briskinfosec - Threatsploit Report Augest 2021- Cyber security updates
Case Study: Wannacry Ransomware attacks Telefónica

Case Study: Wannacry Ransomware attacks Telefónica
More from InterQuest Group
InterQuest Core Values Booklet

Our Vision, Mission and Values and the behaviour we commit to, to ensure we live by them.
A Day In The Life Of A Delivery Consultant

Thinking of a career in recruitment? Our latest infographic will give you an insight into what it's like to be a Delivery Consultant.
Top 10 Strategic Tech Trends 2018 Pt 2

Part 2 of our top tech trends 2018. If you missed part 1 of the infographic then please check out our SlideShare account!
Top 10 Strategic Tech Trends 2018 Pt 1

2018 is well underway. CES has brought some great ideas to the table. Our latest blog on self-disruption states the big tech giants are going to cannibalise themselves by finding new innovations. So what are the top 10 trends to look out for in 2018?
Motivation In The Work Place

Struggling for motivation in January? We’ve got you covered in our newest infographic. You perform at your best when you're motivated. However, this is easier said than done. Here's how to stay motivated at work!
AI Machine Learning: A Forecast

Part 2 of our AI Machine Learning Forecast updated for 2018. What is the future looking like for our jobs and who is at risk?
Top 10 Tech Jobs 2018

With 2017 coming to a close, many employees and active job seekers wish to start their year with a fresh role to begin a new chapter. There are also various sources which state the New Year is the best time to look for a new job as the most decision makers are in the office at one time.
So whether you are looking for a new tech role in 2018 or are an employer who has a skill gap, here are the top 10 tech jobs in 2018 to look out for!
Is The World Prepared For GDPR?

In May 2018 General Data Protection Regulation comes into effect but are businesses ready to comply with this new law?
Top 6 Data Centre Trends For 2017

Mega-Data Centres, SDDC, NV & SND, Big Data, Security, IoT and the Skills Gap.
What are the biggest Data Centre trends for 2017?
Biometric Security: Consumer Demand

Consumers are losing trust in traditional security methods in the wake of recent cyber-attacks and data breaches - could biometric security be the answer? The demand for biometric technology speaks for itself…
What Is Universal Basic Income? 

Universal Basic Income (UBI) is being touted as a solution to a major concern that arises with automation in the workplace - mass unemployment.
What is UBI? What are the benefits and drawbacks?
The Robots Among Us

Robots are everywhere, even where you would not expect. Artificial intelligence is already part of our daily lives. What are the robots among us past and present - and what is yet to come?
How To Make DevOps Work For You

As a discipline, DevOps brings order to the complex world of application and service development, testing, deployment, scaling and monitoring. DevOps enables a unified approach to enterprise software development and delivery that reflects the needs of the entire application life cycle. DevOps strives for more collaborative, productive relationships between development and operations teams, with faster development cycles and reduced production risks.
How can you make DevOps work for you organisation?
For more insights, visit www.interquestgroup.com
IoT Growth: A Forecast

The Internet of Things is set to be a defining technology of our time. Where will it take us in the next few years?
How To Stay Motivated At Work

You perform at your best when you're motivated.
However, this is easier said than done.
Here's how to stay motivated at work!
[Infographic] Future Tech In The Workplace![[Infographic] Future Tech In The Workplace](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] Future Tech In The Workplace](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
We're living in exciting times in terms of technology. IoT, VR and wearables are increasingly becoming more involved in our day to lives, some even set to become to mainstays in our homes.
However, one area that is often overlooked is how these future technologies will impact upon our working lives.
How will future tech such as VR, IoT and wearables shape the future working environment?
UX with George Crotty

UX and digital designer consultant, George Crotty, discusses the current UX digital landscape and opportunities for job seekers.
Top 10 Highest Paying Analytics Jobs 

Are you interested or do you already have a career in analytics? In our latest infographic we show you the top 10 analytics jobs for 2016.
Most In Demand Information Security Skills

Do you have information security skills and want to know what wage you could be earning and what role you could have? In our latest infographic we show you the top information security skills with the corresponding wage and role.
Top 10 Tech Jobs for 2016

Are you interested or do you already have a career in tech? In our latest infographic we show you the top 10 tech jobs for 2016.
More from InterQuest Group (20)
Recently uploaded
This 7-second Brain Wave Ritual Attracts Money To You.!

Discover the power of a simple 7-second brain wave ritual that can attract wealth and abundance into your life. By tapping into specific brain frequencies, this technique helps you manifest financial success effortlessly. Ready to transform your financial future? Try this powerful ritual and start attracting money today!
test test test test testtest test testtest test testtest test testtest test ...

salamsasalamlamsalamsalamsalamsalamsalamsalamsalam
History+of+E-commerce+Development+in+China-www.cfye-commerce.shop

History+of+E-commerce+Development+in+China-www.cfye-commerce.shop
急速办(bedfordhire毕业证书)英国贝德福特大学毕业证成绩单原版一模一样

原版纸张【微信:741003700 】【(bedfordhire毕业证书)英国贝德福特大学毕业证成绩单】【微信:741003700 】学位证,留信认证(真实可查,永久存档)offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原海外各大学 Bachelor Diploma degree, Master Degree Diploma
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
原版仿制(uob毕业证书)英国伯明翰大学毕业证本科学历证书原版一模一样

原版纸张【微信:741003700 】【(uob毕业证书)英国伯明翰大学毕业证】【微信:741003700 】学位证,留信认证(真实可查,永久存档)offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原海外各大学 Bachelor Diploma degree, Master Degree Diploma
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
Multi-cluster Kubernetes Networking- Patterns, Projects and Guidelines

Talk presented at Kubernetes Community Day, New York, May 2024.
Technical summary of Multi-Cluster Kubernetes Networking architectures with focus on 4 key topics.
1) Key patterns for Multi-cluster architectures
2) Architectural comparison of several OSS/ CNCF projects to address these patterns
3) Evolution trends for the APIs of these projects
4) Some design recommendations & guidelines for adopting/ deploying these solutions.
The+Prospects+of+E-Commerce+in+China.pptx

The Prospects of E-commerce in China,www.cfye-commerce.shop
ER(Entity Relationship) Diagram for online shopping - TAE

https://bit.ly/3KACoyV
The ER diagram for the project is the foundation for the building of the database of the project. The properties, datatypes, and attributes are defined by the ER diagram.
1.Wireless Communication System_Wireless communication is a broad term that i...

Wireless communication involves the transmission of information over a distance without the help of wires, cables or any other forms of electrical conductors.
Wireless communication is a broad term that incorporates all procedures and forms of connecting and communicating between two or more devices using a wireless signal through wireless communication technologies and devices.
Features of Wireless Communication
The evolution of wireless technology has brought many advancements with its effective features.
The transmitted distance can be anywhere between a few meters (for example, a television's remote control) and thousands of kilometers (for example, radio communication).
Wireless communication can be used for cellular telephony, wireless access to the internet, wireless home networking, and so on.
1比1复刻(bath毕业证书)英国巴斯大学毕业证学位证原版一模一样

原版纸张【微信:741003700 】【(bath毕业证书)英国巴斯大学毕业证学位证】【微信:741003700 】学位证,留信认证(真实可查,永久存档)offer、雅思、外壳等材料/诚信可靠,可直接看成品样本,帮您解决无法毕业带来的各种难题!外壳,原版制作,诚信可靠,可直接看成品样本。行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备。十五年致力于帮助留学生解决难题,包您满意。
本公司拥有海外各大学样板无数,能完美还原海外各大学 Bachelor Diploma degree, Master Degree Diploma
1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。材料咨询办理、认证咨询办理请加学历顾问Q/微741003700
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
How to Use Contact Form 7 Like a Pro.pptx

Contact Form 7 is a popular plugins for WordPress. This is an introduction into its features and usage.
Recently uploaded (16)
This 7-second Brain Wave Ritual Attracts Money To You.!

This 7-second Brain Wave Ritual Attracts Money To You.!
test test test test testtest test testtest test testtest test testtest test ...

test test test test testtest test testtest test testtest test testtest test ...
History+of+E-commerce+Development+in+China-www.cfye-commerce.shop

History+of+E-commerce+Development+in+China-www.cfye-commerce.shop
Multi-cluster Kubernetes Networking- Patterns, Projects and Guidelines

Multi-cluster Kubernetes Networking- Patterns, Projects and Guidelines
ER(Entity Relationship) Diagram for online shopping - TAE

ER(Entity Relationship) Diagram for online shopping - TAE
1.Wireless Communication System_Wireless communication is a broad term that i...

1.Wireless Communication System_Wireless communication is a broad term that i...
guildmasters guide to ravnica Dungeons & Dragons 5...

guildmasters guide to ravnica Dungeons & Dragons 5...
Living-in-IT-era-Module-7-Imaging-and-Design-for-Social-Impact.pptx

Living-in-IT-era-Module-7-Imaging-and-Design-for-Social-Impact.pptx
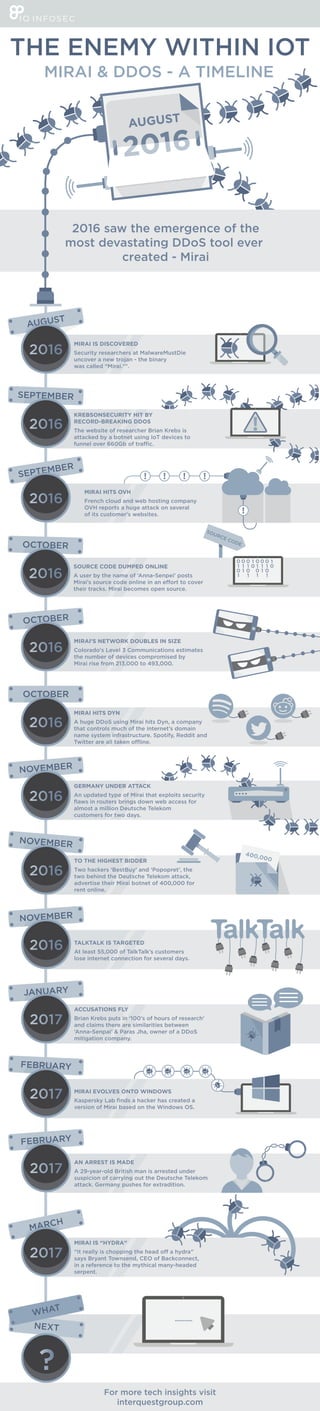
The Enemy Within IoT - A Mirai DDoS Timeline
- 1. SEPTEMBER KREBSONSECURITY HIT BY RECORD-BREAKING DDOS The website of researcher Brian Krebs is attacked by a botnet using IoT devices to AUGUST MIRAI IS DISCOVERED Security researchers at MalwareMustDie uncover a new trojan - the binary was called “Mirai.*”. SEPTEMBER OCTOBER SOURCE CODE DUMPED ONLINE A user by the name of ‘Anna-Senpei’ posts their tracks. Mirai becomes open source. OCTOBER MIRAI’S NETWORK DOUBLES IN SIZE Colorado's Level 3 Communications estimates the number of devices compromised by Mirai rise from 213,000 to 493,000. SOURCE CODE OCTOBER MIRAI HITS DYN A huge DDoS using Mirai hits Dyn, a company that controls much of the internet’s domain name system infrastructure. Spotify, Reddit and MIRAI HITS OVH French cloud and web hosting company OVH reports a huge attack on several of its customer's websites. NOVEMBER GERMANY UNDER ATTACK An updated type of Mirai that exploits security flaws in routers brings down web access for almost a million Deutsche Telekom customers for two days. NOVEMBER TO THE HIGHEST BIDDER Two hackers ‘BestBuy’ and ‘Popopret’, the two behind the Deutsche Telekom attack, advertise their Mirai botnet of 400,000 for rent online. NOVEMBER TALKTALK IS TARGETED At least 55,000 of TalkTalk’s customers lose internet connection for several days. JANUARY ACCUSATIONS FLY Brian Krebs puts in ‘100’s of hours of research’ and claims there are similarities between ‘Anna-Senpai’ & Paras Jha, owner of a DDoS mitigation company. FEBRUARY MIRAI EVOLVES ONTO WINDOWS Kaspersky Lab finds a hacker has created a version of Mirai based on the Windows OS. FEBRUARY AN ARREST IS MADE A 29-year-old British man is arrested under suspicion of carrying out the Deutsche Telekom attack. Germany pushes for extradition. MARCH MIRAI IS “HYDRA” says Bryant Townsend, CEO of Backconnect, in a reference to the mythical many-headed serpent. THE ENEMY WITHIN IOT MIRAI & DDOS - A TIMELINE 2016 saw the emergence of the most devastating DDoS tool ever created - Mirai NEXT WHAT For more tech insights visit interquestgroup.com ...........
