The Pulse of European Social Media-Unveiling Consumer Identity Trends 2023
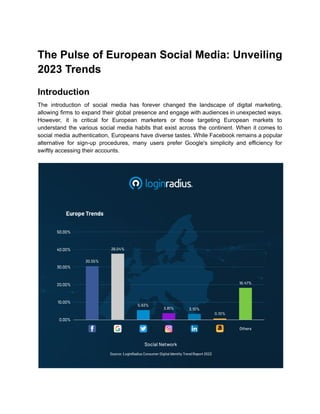
- 1. The Pulse of European Social Media: Unveiling 2023 Trends Introduction The introduction of social media has forever changed the landscape of digital marketing, allowing firms to expand their global presence and engage with audiences in unexpected ways. However, it is critical for European marketers or those targeting European markets to understand the various social media habits that exist across the continent. When it comes to social media authentication, Europeans have diverse tastes. While Facebook remains a popular alternative for sign-up procedures, many users prefer Google's simplicity and efficiency for swiftly accessing their accounts.
- 2. Marketers must embrace data-driven tactics to survive in the digital-first era, using reliable statistics, in-depth customer behavior analysis, and identifiable patterns. Marketers can adjust their tactics and assure concrete results by understanding their target audience's distinct social media inclinations, especially when targeting specific European demographics. The European Choice: Google as the Preferred Social Media Platform An in-depth analysis of Europeans' social media usage uncovers surprising patterns about the preferred platforms for authentication. Facebook and Google both play significant roles, but Google emerges as the user preference in Europe, earning the trust of 38.04% of people. Facebook retains a strong presence despite intense competition, with a preference rate of 30.55%. These numbers highlight the significance of these two platforms for users' authentication needs and offer insight into the complex landscape of social media usage across Europe. Furthermore, the study reveals that Europeans use a variety of social media sites other than Facebook and Google, exhibiting a wide range of interests that include sites like Twitter and Instagram. The Consumer Digital Identity Trend Report 2023 delivers a comprehensive analysis of these patterns, equipping marketers and professionals with valuable insights to navigate and optimize their social media strategies in Europe. Conclusion The Consumer Digital Identity Trend Report 2023 acts as a compass for marketers attempting to navigate the complexities of customer identity management in today's fast-changing digital world. Marketers may identify worldwide trends and preferences surrounding users' digital identities by delving into the report's in-depth analysis and insights. This research provides marketers with the resources they need to alter their tactics and cater to the individual needs and expectations of their target audience, from preferred authentication methods to user behavior. Businesses may improve their customer experience, develop meaningful connections, and promote long-term success by integrating the insights of this report. Don't miss out on this excellent resource; get your free copy of the study immediately.
