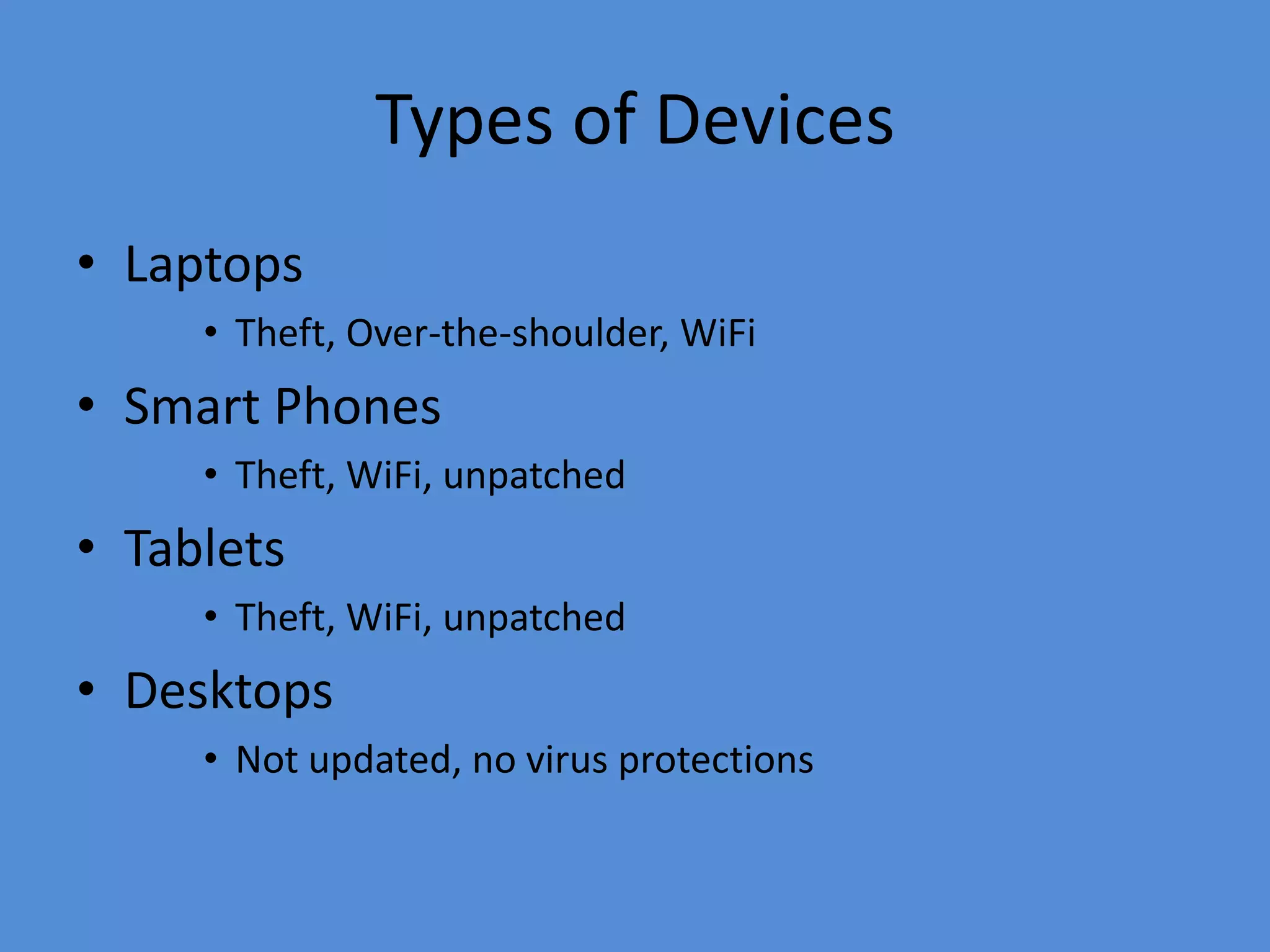
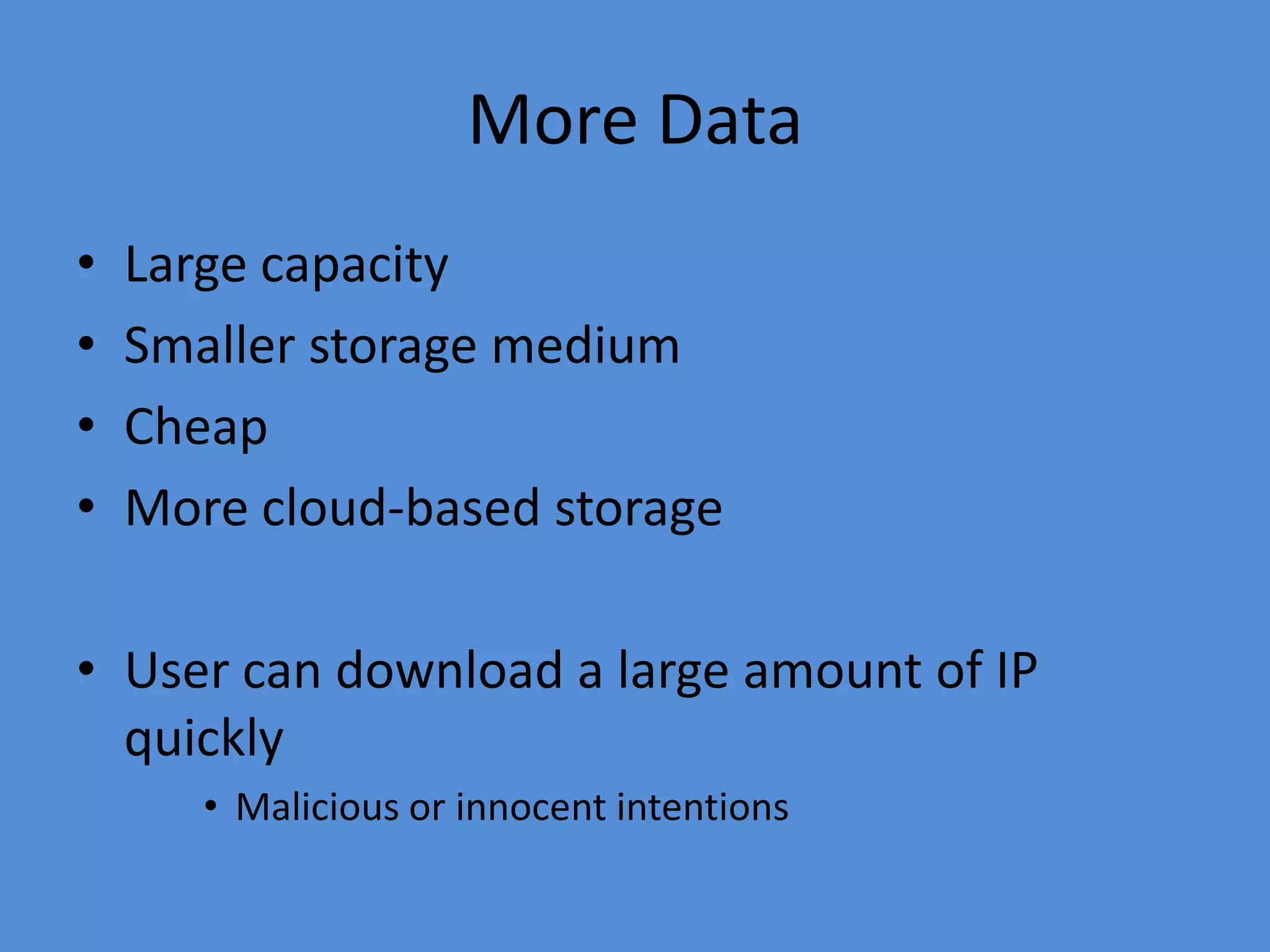
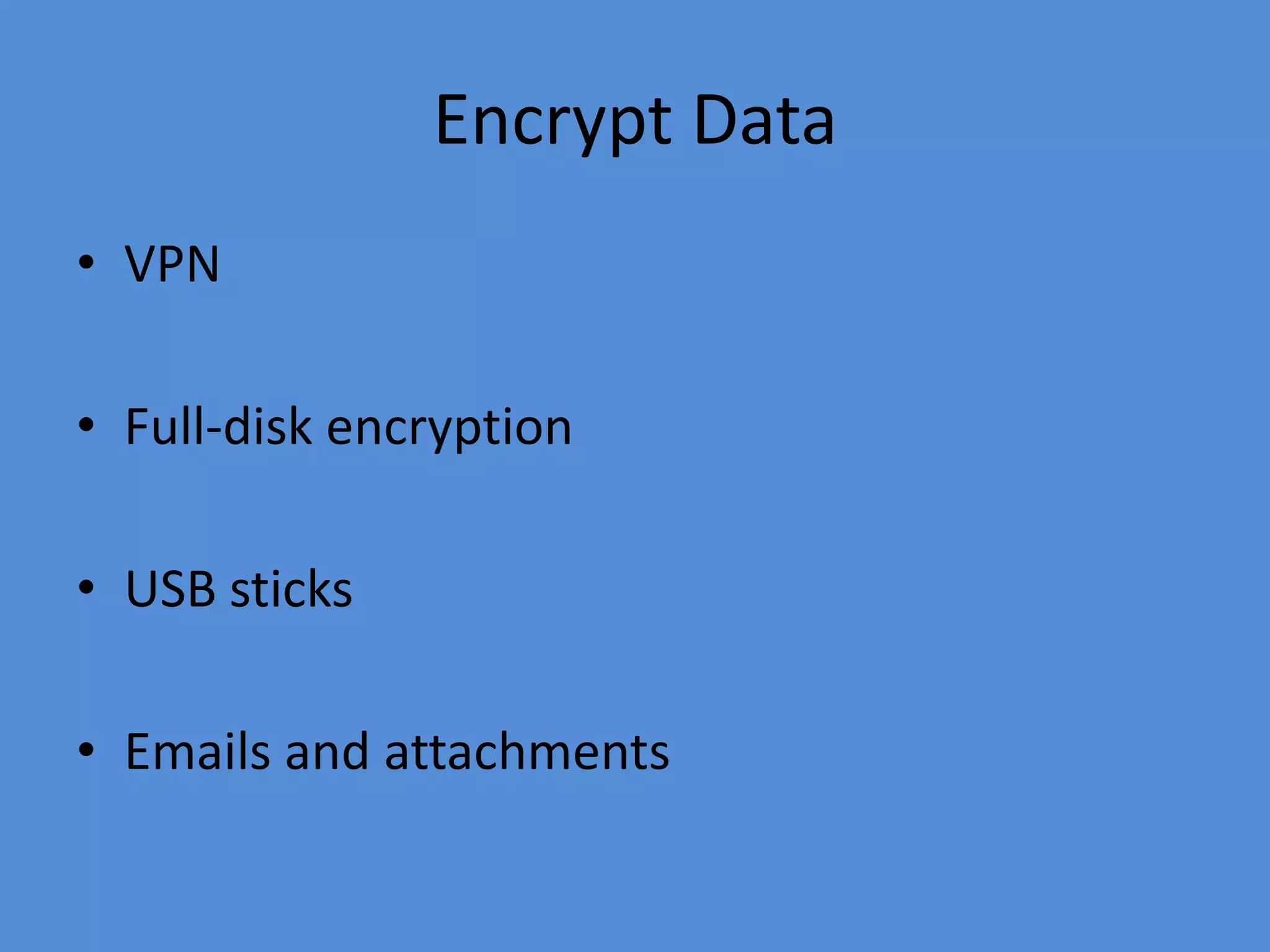
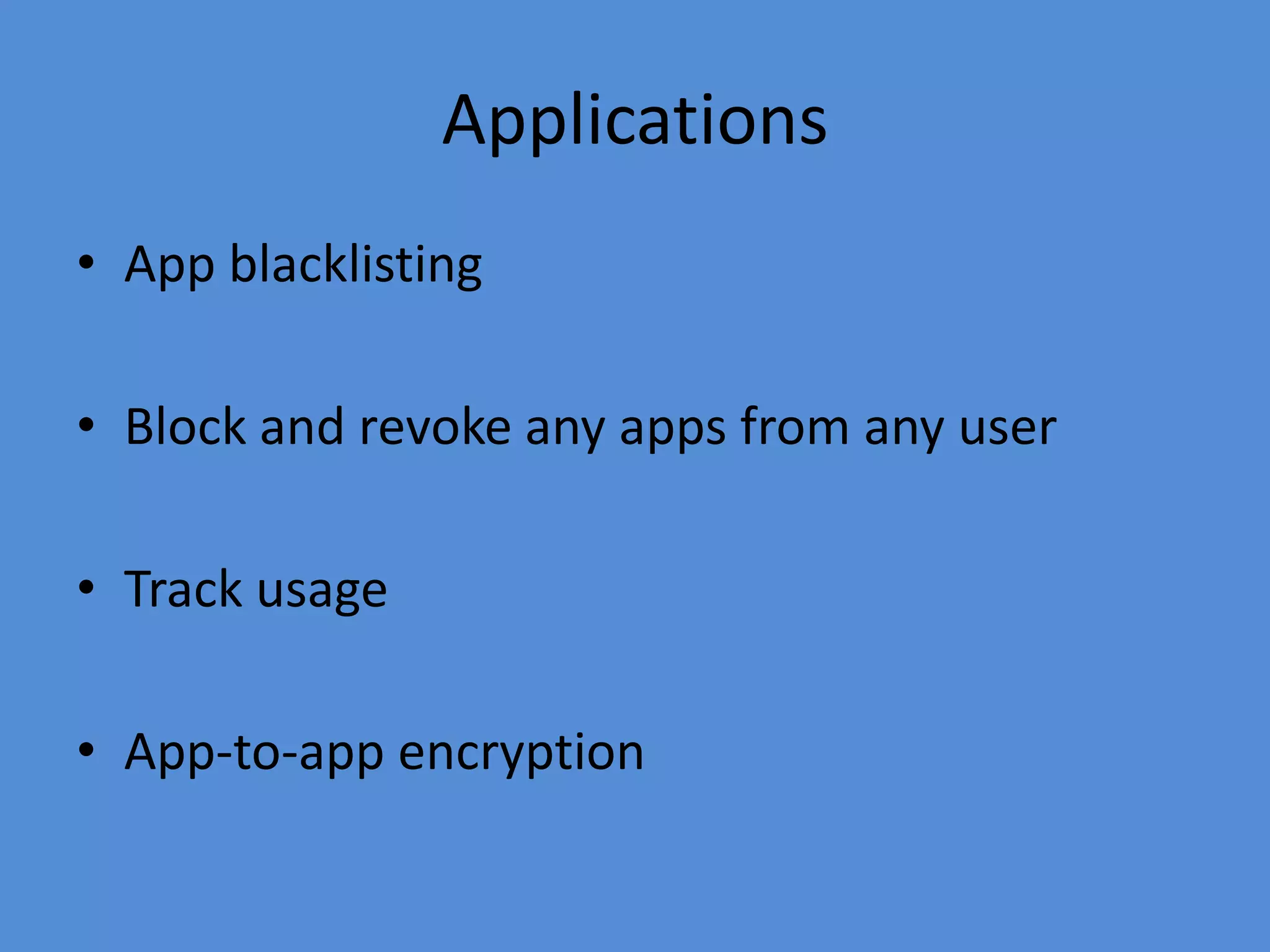
This document discusses the threats to intellectual property in the digital age and provides recommendations for what companies can do to protect themselves. It notes that IP is increasingly being compromised due to the rise of mobile devices and remote work. It recommends that companies implement encryption, mobile device management, data access restrictions, remote wiping, data leakage prevention, attribute-based access controls, and employee training to help secure their intellectual property. Regular software updates, firewalls, and following basic security principles are also important protective measures.