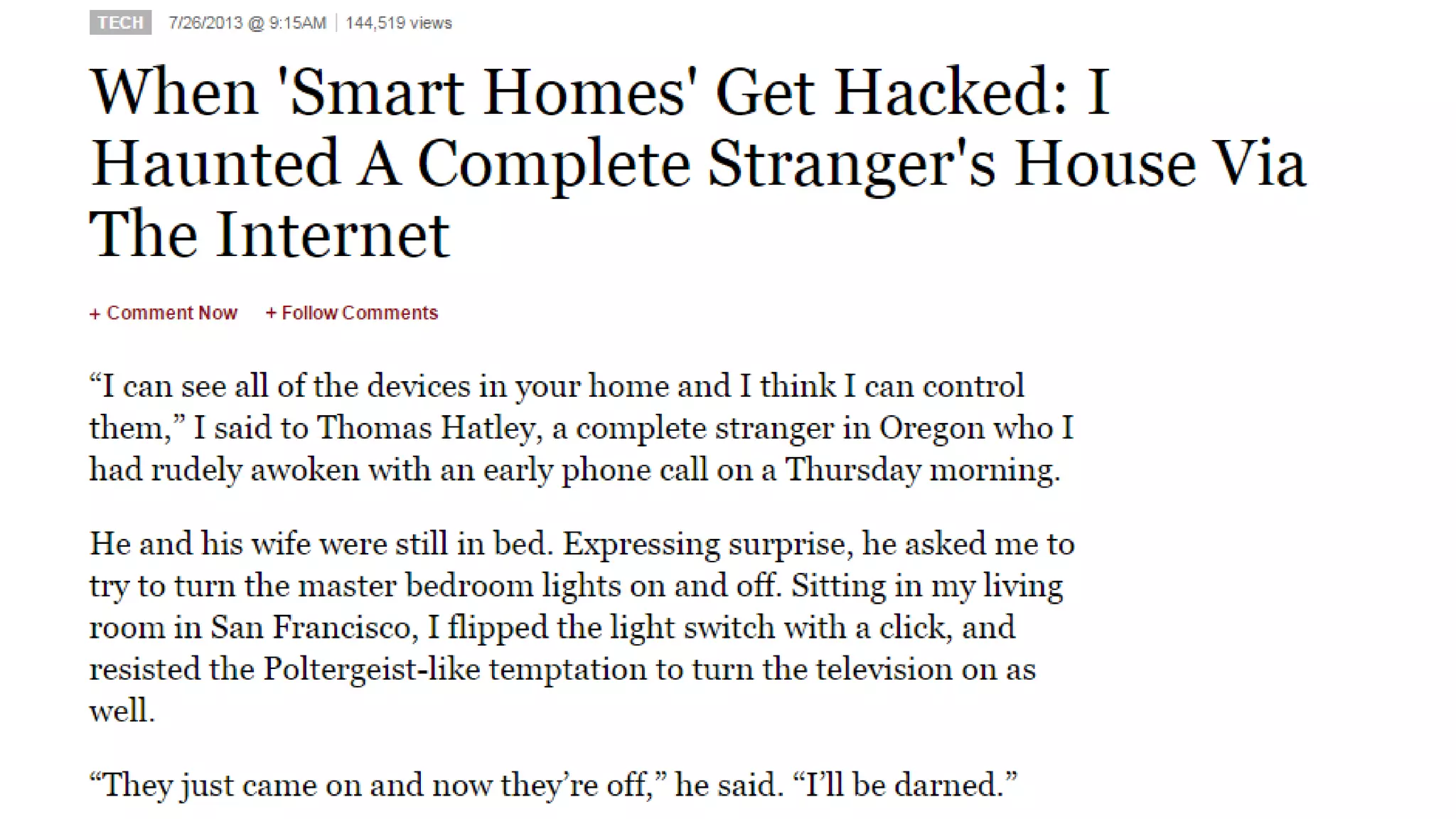
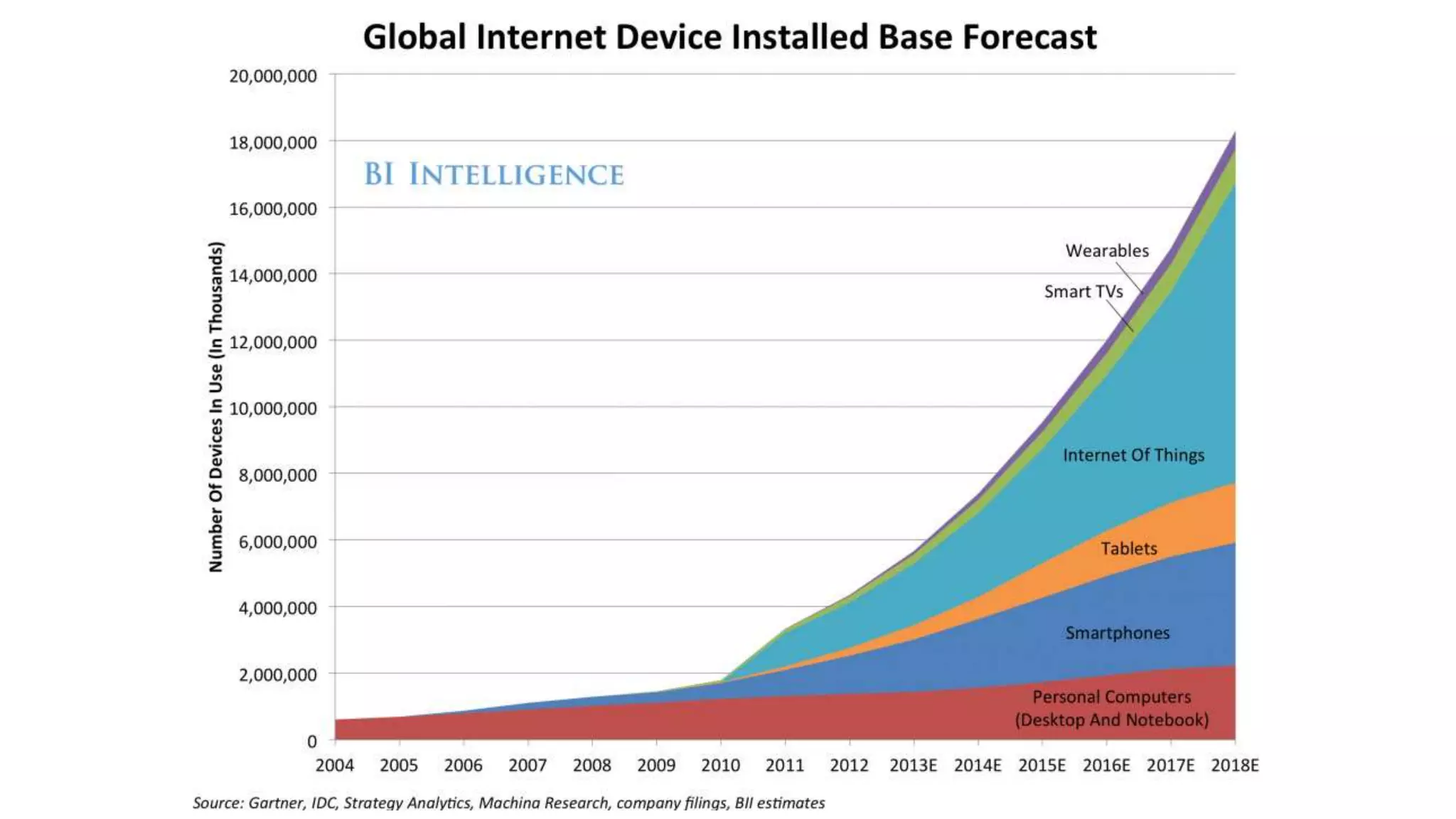
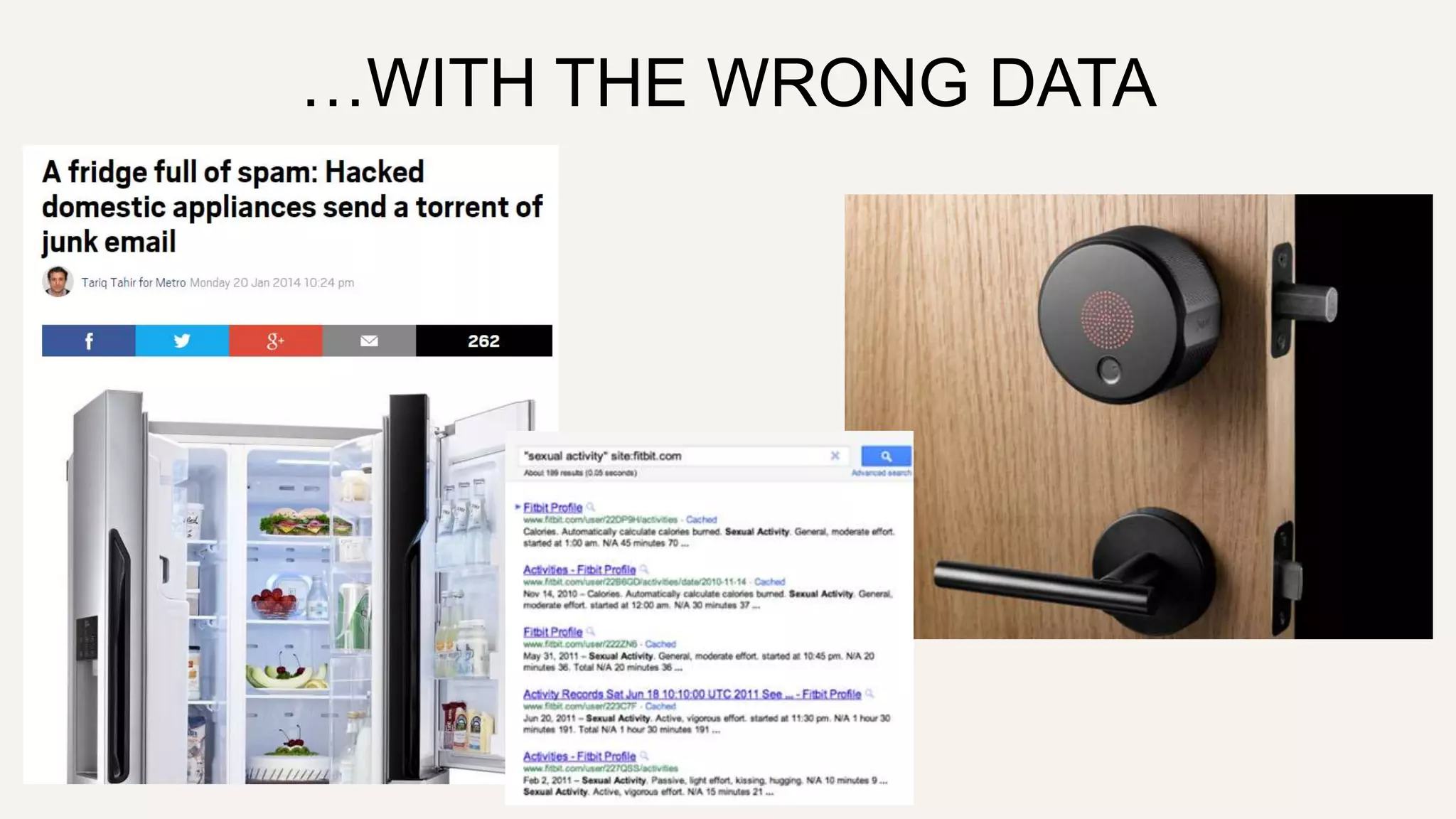
This document summarizes privacy and security considerations related to Internet of Things (IoT) devices and wearables. It notes that IoT devices collect a large amount of user data, which can be valuable but also creepy if used or stolen improperly. It advocates for a privacy by design approach where security and privacy are embedded in products from the start through practices like data proportionality, privacy as the default, end-to-end security, and transparency to build user trust.