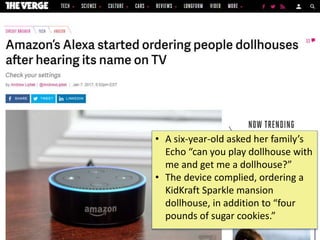
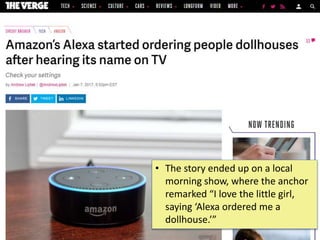
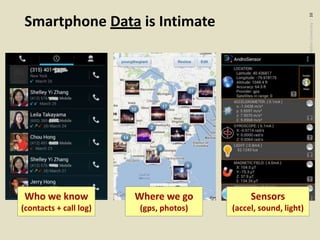
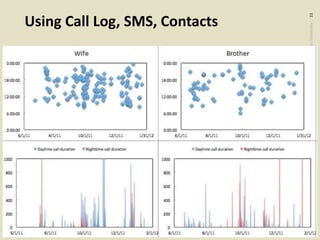
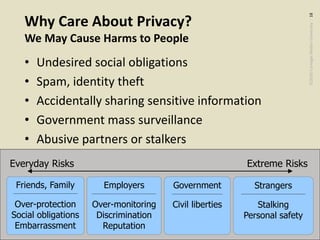
The document discusses the evolution toward ubiquitous computing and the significance of privacy in mobile sensing systems. It highlights privacy concerns related to smartphones, which collect intimate data about users, and the risks associated with data misuse. Design challenges for privacy are noted, including scalability, emergent behaviors, and the need for better user interfaces to facilitate informed consent and usage.









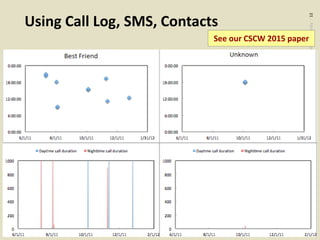
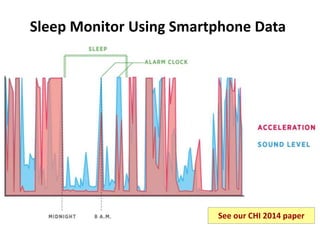



![©2020CarnegieMellonUniversity:20
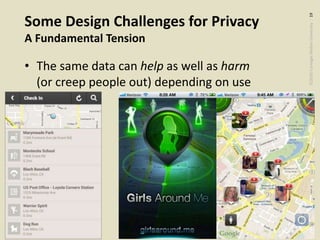
Some Design Challenges for Privacy
Very Strong Incentives to Keep Collecting More Data
• “[An analyst at Target] was able to identify about
25 products that… allowed him to assign each
shopper a ‘pregnancy prediction’ score. [H]e
could also estimate her due date to within a small
window, so Target could send coupons timed to
very specific stages of her pregnancy.” (NYTimes)
• Companies: More data -> Better ads and services
• Government: More data -> More national security](https://image.slidesharecdn.com/privacy-for-mobile-sensing-systems-oct2020-201021025354/85/Privacy-for-Mobile-Sensing-Systems-20-320.jpg)