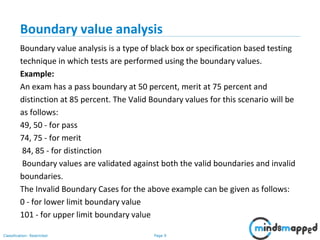
The document provides an overview of test case design and techniques in software testing, focusing on black-box and white-box methods. It details various testing techniques such as equivalence partitioning, boundary value analysis, and path testing, along with the structures and documentation required for effective test cases. Additionally, the document discusses the objectives of good test cases and the advantages of employing systematic testing strategies.