This document provides an overview of Terraform and infrastructure as code using Terraform. It discusses what Terraform is, how to get started with Terraform including initializing a Terraform configuration, planning and applying changes, variables, modules, providers and resources. It also covers Terraform state and locking state for multi-user collaboration.



![FullStack Developers Israel
TERRAFORM | GETTING STARTED
INFRASTRUCTURE AS CODE
Infrastructure as code (IaC) is the process of managing and
provisioning computer data centers through machine-
readable definition files, rather than physical hardware
configuration or interactive configuration tools.[1] The IT
infrastructure meant by this comprises both physical
equipment such as bare-metal servers as well as virtual
machines and associated configuration resources. The
definitions may be in a version control system. It can use
either scripts or declarative definitions, rather than manual
processes, but the term is more often used to promote
declarative approaches.](https://image.slidesharecdn.com/terraform-101-181024154730/85/Terraform-101-4-320.jpg)





![FullStack Developers Israel
TERRAFORM | GETTING STARTED
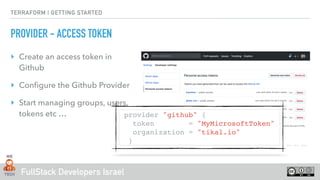
RESOURCES
1 # Configure the PagerDuty provider
2 provider "pagerduty" {
3 token = “MyPgToken"
4 }
5
6 # Create a PagerDuty team
7 resource "pagerduty_team" "engineering" {
8 name = "Engineering"
9 description = "All engineering"
10 }
11
12 # Create a PagerDuty user and add it to a team
13 resource "pagerduty_user" “tikal_io” {
14 name = “Haggai Philip Zagury"
15 email = “hagzag@tikalk.com”
16 teams = ["${pagerduty_team.engineering.id}"]
17 }](https://image.slidesharecdn.com/terraform-101-181024154730/85/Terraform-101-11-320.jpg)











![FullStack Developers Israel
TERRAFORM | GETTING STARTED
IN OUR SCENARIO - BETWEEN “PLAN” & “DESTROY”
1 {
2 "version": 3,
3 "terraform_version": "0.11.7",
4 "serial": 3,
5 "lineage": "d6a3fc33-4869-c90f-6adb-c21947133250",
6 "modules": [
7 {
8 "path": [
9 "root"
10 ],
11 "outputs": {},
12 "resources": {
13 "github_membership.user": {
14 "type": "github_membership",
15 "depends_on": [],
16 "primary": {
17 "id": "tikalio:shellegtk",
18 "attributes": {
19 "id": "tikalio:shellegtk",
20 "role": "member",
21 "username": "shellegtk"
22 },
23 "meta": {},
24 "tainted": false
25 },
26 "deposed": [],
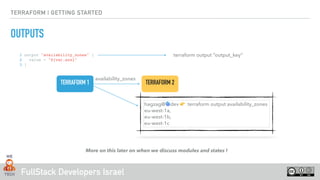
Our Infrastructure has a state and a version !
‣ By default terraform state is
stored locally under
terraform.tfstate file and can be
shared via git { but there are
better ways … }](https://image.slidesharecdn.com/terraform-101-181024154730/85/Terraform-101-30-320.jpg)



![FullStack Developers Israel
TERRAFORM | GETTING STARTED
STATE LOCK
‣ terraform plan [better]
terraform.tfstate
In memory terraform.tfstate
🌀bob 👉 terraform plan
Acquiring state lock. This may take a few moments...
Refreshing Terraform state in-memory prior to plan...
The refreshed state will be used to calculate this plan,
but will not be persisted to local or remote state
storage.
🌀bob 👉 terraform apply
Acquiring state lock. This may take a few moments...
🌀ann 👉 terraform plan
Acquiring state lock. This may take a few moments...
This plan is locked by user <bob ….>
User A cannot get / update the state until
User B had released the lock in the Dynamodb table](https://image.slidesharecdn.com/terraform-101-181024154730/85/Terraform-101-34-320.jpg)
![FullStack Developers Israel
TERRAFORM | GETTING STARTED
STATE + LOCK - CONSUL
‣ terraform plan [better]
terraform.tfstate
In memory terraform.tfstate
🌀bob 👉 terraform plan
Acquiring state lock. This may take a few moments...
Refreshing Terraform state in-memory prior to plan...
The refreshed state will be used to calculate this plan,
but will not be persisted to local or remote state
storage.
🌀bob 👉 terraform apply
Acquiring state lock. This may take a few moments...
🌀ann 👉 terraform plan
Acquiring state lock. This may take a few moments...
This plan is locked by user xxxx ….
User A cannot get / update the state until
User B had released the lock in the Dynamodb table](https://image.slidesharecdn.com/terraform-101-181024154730/85/Terraform-101-35-320.jpg)





![FullStack Developers Israel
TERRAFORM | GETTING STARTED
A terraform “module” is basically a set of reusable terror files !
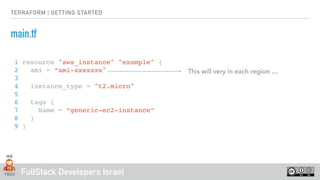
This will very in each region …
data "aws_ami" "centos" {
owners = ["679593333241"]
most_recent = true
filter {
name = "name"
values = ["CentOS Linux 7 x86_64 HVM EBS *"]
}
filter {
name = "architecture"
values = ["x86_64"]
}
filter {
name = "root-device-type"
values = ["ebs"]
}
}](https://image.slidesharecdn.com/terraform-101-181024154730/85/Terraform-101-45-320.jpg)
![FullStack Developers Israel
TERRAFORM | GETTING STARTED
A terraform “module” is basically a set of reusable terror files !
This will very in each region …
data "aws_ami" "ubuntu" {
most_recent = true
filter {
name = "name"
values = ["ubuntu/images/hvm-ssd/ubuntu-xenial-16.04-amd64-server
}
filter {
name = "virtualization-type"
values = ["hvm"]
}
owners = ["099720109477"] # Canonical
}](https://image.slidesharecdn.com/terraform-101-181024154730/85/Terraform-101-46-320.jpg)