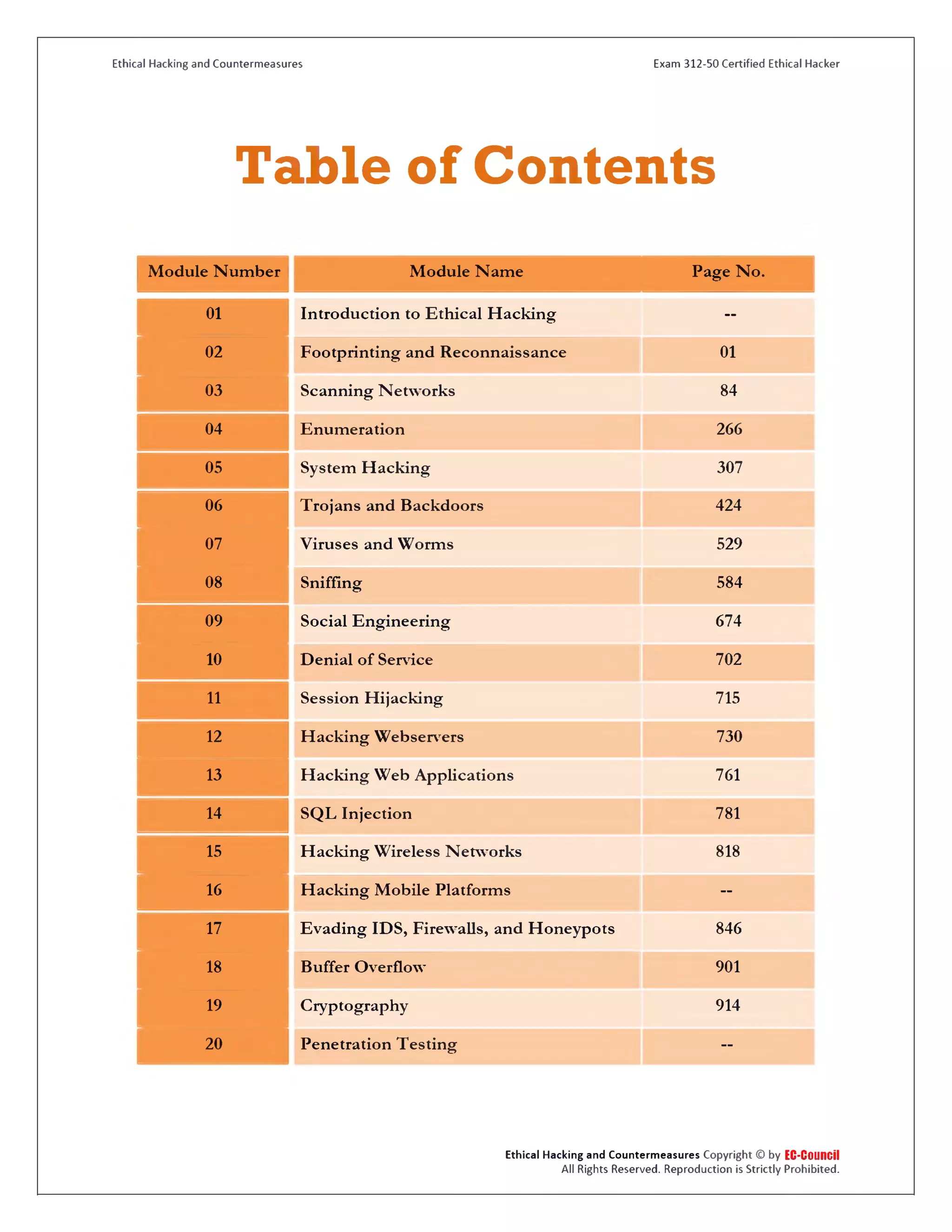
This document provides an overview and table of contents for an ethical hacking and countermeasures lab manual. It contains 20 modules that cover topics like footprinting, scanning networks, system hacking, social engineering, cryptography, and penetration testing. The document states that the courseware was developed through extensive research and contributions from subject matter experts. It also notes that while the document may reference other security solutions, these should not be considered endorsements. Reproduction of the contents is strictly prohibited except as allowed under copyright law.