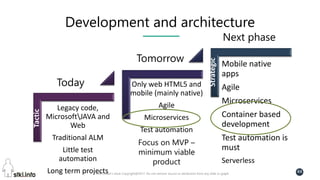
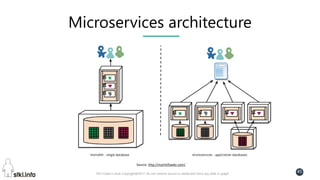
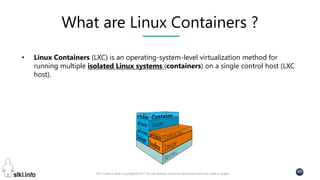
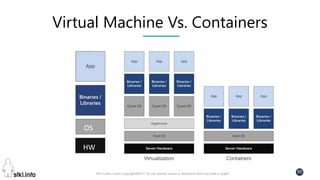
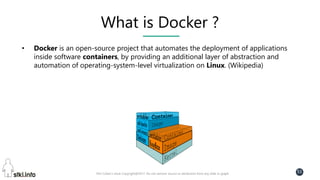
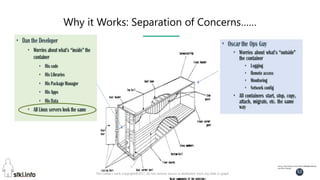
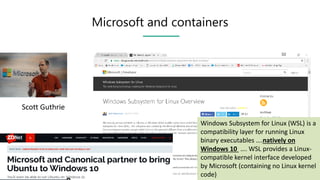
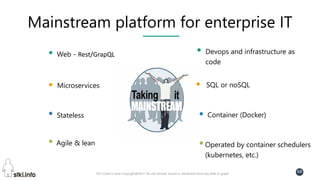
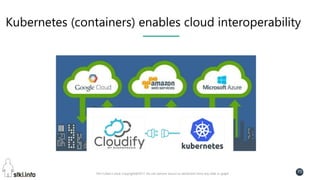
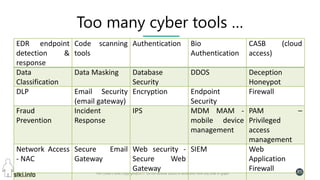
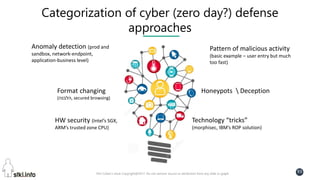
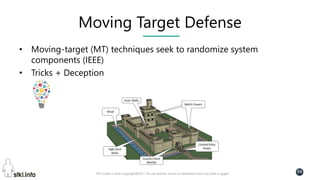
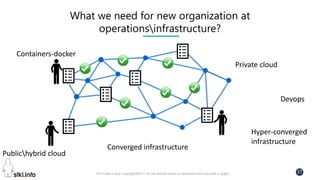
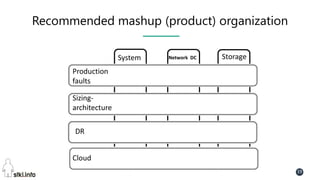
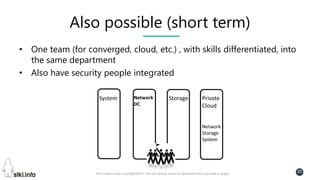
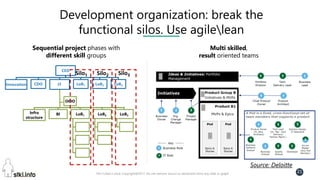
This document contains slides from a presentation on modern delivery and cybersecurity for enterprise IT. The presentation covers many topics including organizational changes needed to adopt new technologies like microservices, containers, and cloud computing. It discusses moving from traditional monolithic applications to microservices architectures and container-based development. The slides also address infrastructure changes like converged, hyper-converged, and software-defined infrastructure. Middleware, development practices, and security topics are also covered at a high-level.













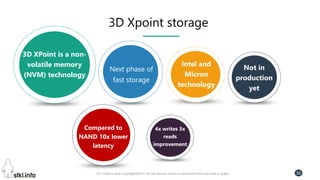
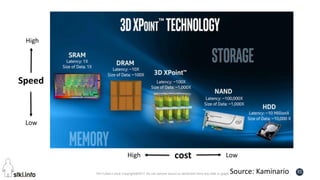
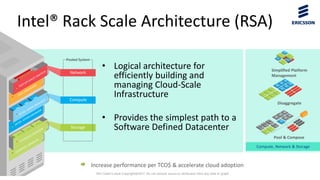
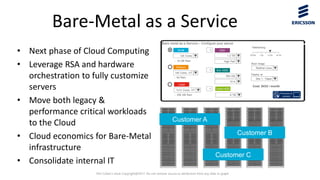


![Pini Cohen’s work Copyright@2017. Do not remove source or attribution from any slide or graph
42
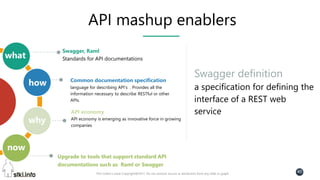
Swagger basic example
• For basic function http://host/greetings/hello/world that returns 'Hello
world‘, basic swagger will be:
{ "swaggerVersion": "1.2", "apis": [ {
"path": "http://localhost:8000/listings/greetings",
"description": "Generating greetings in our application."
} ] }
More at:
https://github.com/OAI/OpenAPI-
Specification/wiki/Hello-World-
Sample](https://image.slidesharecdn.com/summit2017cyberdeliveryv4longversion-170328054345/85/Summit-2017-cyber-delivery-v4-long-version-42-320.jpg)