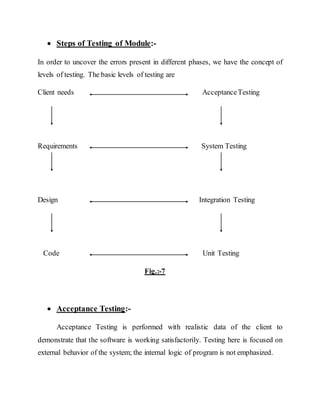
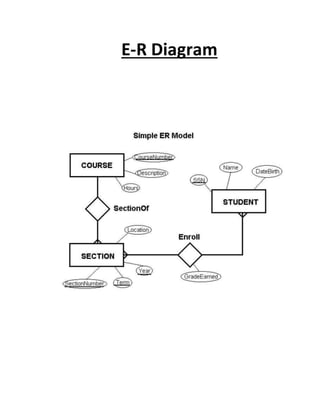
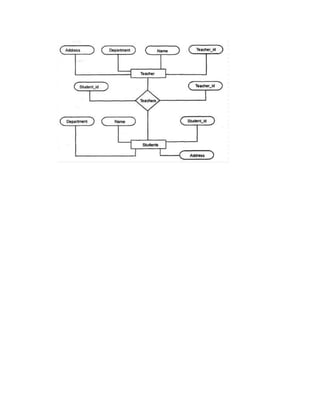
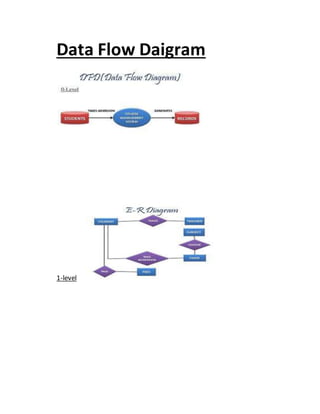
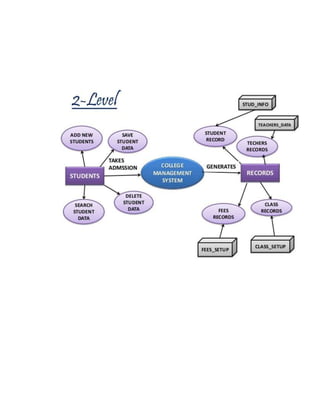
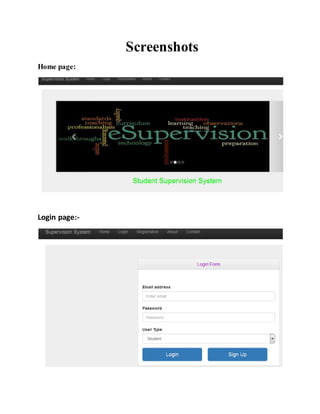
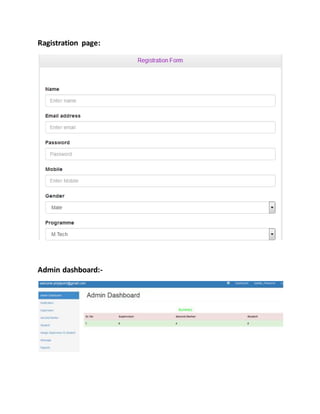
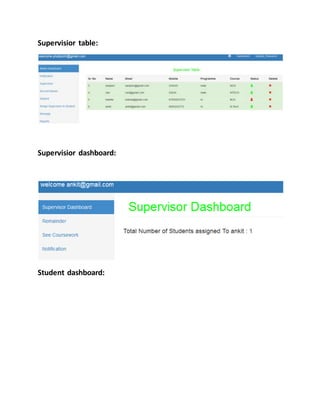
This document provides a summary of the software development life cycle for the "Student Supervision System" project. It describes the typical phases of a project including initiation, concept development, planning, requirements analysis, design, development, integration and testing, implementation, and operations and maintenance. The goal is to develop a system to automate the manual student supervision processes currently in use through planning and implementing the necessary phases of the software development life cycle.




































![.theme-showcase.navbar .container {
width: auto;
}
</style>
<meta charset="utf-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="width=device-width, initial-scale=1">
<!-- The above 3 meta tags *must* come firstin the head; any other head
content must come *after* these tags -->
<meta name="description" content="">
<meta name="author" content="">
<link rel="icon" href="../../favicon.ico">
<title>Student Supervision System</title>
<!-- Bootstrap core CSS -->
<link href="css/bootstrap.min.css"rel="stylesheet">
<!-- Bootstrap theme -->
<link href="css/bootstrap-theme.min.css" rel="stylesheet">
<!-- Just for debugging purposes. Don'tactually copy these 2 lines! -->
<!--[if lt IE9]><script src="../../assets/js/ie8-responsive-file-
warning.js"></script><![endif]-->](https://image.slidesharecdn.com/gauravreport-161029061633/85/student-supervision-system-45-320.jpg)
![<scriptsrc="js/ie-emulation-modes-warning.js"></script>
<link rel="stylesheet"
href="http://maxcdn.bootstrapcdn.com/bootstrap/3.3.4/css/bootstrap.min.css">
<script
src="https://ajax.googleapis.com/ajax/libs/jquery/1.11.1/jquery.min.js"></script>
<script
src="http://maxcdn.bootstrapcdn.com/bootstrap/3.3.4/js/bootstrap.min.js"></sc
ript>
<!-- HTML5 shim and Respond.js for IE8 supportof HTML5 elements and media
queries -->
<!--[if lt IE9]>
<script
src="https://oss.maxcdn.com/html5shiv/3.7.2/html5shiv.min.js"></script>
<script src="https://oss.maxcdn.com/respond/1.4.2/respond.min.js"></script>
<![endif]-->
</head>
<body role="document">
<!-- Fixed navbar -->
<nav class="navbar navbar-inversenavbar-fixed-top">
<div class="container">
<div class="navbar-header">](https://image.slidesharecdn.com/gauravreport-161029061633/85/student-supervision-system-46-320.jpg)

![<div class="container theme-showcase" role="main">
<!-- Main jumbotron for a primary marketing messageor call to action -->
<div class="jumbotron">
<?php
@$opt=$_REQUEST['option'];
if($opt!="")
{
if($opt=="newuser")
{
include('regis.php');
}
if($opt=="login")
{
include('login.php');
}
if($opt=="about")
{
include('about.php');
}
if($opt=="contact")](https://image.slidesharecdn.com/gauravreport-161029061633/85/student-supervision-system-48-320.jpg)



![LOGIN PAGE:-
<?php
require('config.php');
extract($_POST);
if(isset($signup))
{
if($user==1)
{
$que=mysql_query("selectemail,pass fromstudentwhere
email='$eid' and pass=password('$pass')");
$row=mysql_num_rows($que);
if($row)
{
$_SESSION['student']=$eid;
echo "<script>window.location='student'</script>";
}
else
{
$err="<fontcolor='red'>Invalid Student Login</font>";
}](https://image.slidesharecdn.com/gauravreport-161029061633/85/student-supervision-system-52-320.jpg)
![}
//for Supervision
if($user==2)
{
$que=mysql_query("selectemail,pass,status fromsupervisorwhere
email='$eid' and pass=password('$pass')");
$row=mysql_num_rows($que);
if($row)
{
$status=mysql_fetch_assoc($que);
if($status['status']==1)
{
$err="<fontcolor='red'>Your account is not activated yet by
admin</font>";
}
else
{
$_SESSION['supervisior']=$eid;
echo "<script>window.location='Supervisor'</script>";
}
}
else](https://image.slidesharecdn.com/gauravreport-161029061633/85/student-supervision-system-53-320.jpg)
![{
$err="<fontcolor='red'>Invalid Supervisor Login</font>";
}
}
//for Second Marker
if($user==3)
{
$que=mysql_query("selectemail,pass,status fromsecond_marker
whereemail='$eid' and pass=password('$pass')");
$row=mysql_num_rows($que);
if($row)
{
$status=mysql_fetch_assoc($que);
if($status['status']==1)
{
$err="<fontcolor='red'>Your account is not activated yet by
admin</font>";
}
else
{
$_SESSION['second_marker']=$eid;](https://image.slidesharecdn.com/gauravreport-161029061633/85/student-supervision-system-54-320.jpg)
![echo "<script>window.location='second_marker'</script>";
}
}
else
{
$err="<fontcolor='red'>Invalid Second marker Login</font>";
}
}
//for Admin
if($user==4)
{
$que=mysql_query("selectemail,pass fromadmin where
email='$eid' and pass='$pass'");
$row=mysql_num_rows($que);
if($row)
{
$_SESSION['admin']=$eid;
echo "<script>window.location='admin'</script>";
}
else
{](https://image.slidesharecdn.com/gauravreport-161029061633/85/student-supervision-system-55-320.jpg)






![<form method="post">
<div class="form-group">
<label for="exampleInputEmail1"><?php echo @$err;?></label>
</div>
<div class="form-group">
<label for="exampleInputEmail1">Name</label>
<input type="text" class="form-control" name="n" placeholder="Enter name"
pattern="[a-z A-Z]*" required>
</div>
<div class="form-group">
<label for="exampleInputEmail1">Emailaddress</label>
<input type="email" class="form-control" name="e" id="exampleInputEmail1"
placeholder="Enter email" required>
</div>
<div class="form-group">
<label for="exampleInputPassword1">Password</label>
<input type="password" class="form-control" name="pass"
id="exampleInputPassword1" placeholder="Password" >
</div>
<div class="form-group">](https://image.slidesharecdn.com/gauravreport-161029061633/85/student-supervision-system-62-320.jpg)
![<label for="exampleInputEmail1">Mobile</label>
<input type="text" class="form-control" name="mob" maxlength="13" required
pattern="[0-9 + ]*" placeholder="Enter Mobile" >
</div>
<!--<div class="form-group">
<label for="exampleInputEmail1">Gender</label>
<div class="radio">
<label>
<input type="radio" name="g" value="m">
Male
<input type="radio" name="g" value="f">
Female
</label>
</div></div>-->
<div class="form-group">
<label for="exampleInputEmail1">Gender</label>
<select class="form-control" name="g">
<option value="m">Male</option>](https://image.slidesharecdn.com/gauravreport-161029061633/85/student-supervision-system-63-320.jpg)




![require('config.php');
extract($_POST);
if(isset($signup))
{
echo $user." ".$eid." ".$pass;
if($user==1)
{
$que=mysql_query("selectemail,pass fromstudentwhere
email='$eid' and pass='$pass'");
$row=mysql_num_rows($que);
if($row)
{
$_SESSION['student']=$eid;
echo "<script>window.location='student'</script>";
}
else
{
$err="<fontcolor='red'>Invalid Student Login</font>";
}
}](https://image.slidesharecdn.com/gauravreport-161029061633/85/student-supervision-system-68-320.jpg)