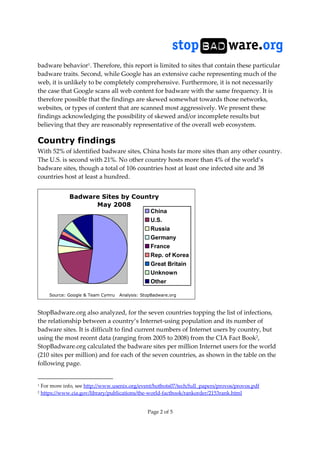
This document summarizes an analysis of over 200,000 websites engaged in badware behavior according to Google's Safe Browsing initiative. The analysis found that over half of infected sites were located in China, with the top three Chinese network blocks accounting for 68% of infections in that country. In contrast, infected sites in the US were more distributed. Compared to the previous year, the total number of infected sites increased, likely due to expanded scanning and increased malware distribution through websites.