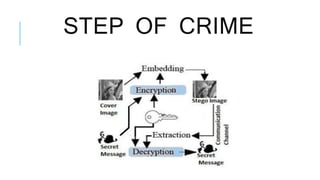
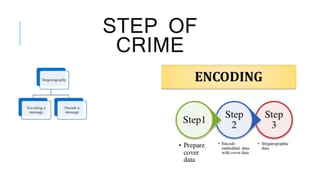
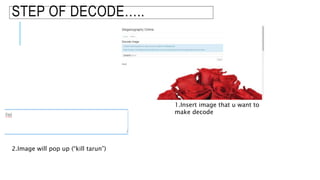
Steganography is a technique for hiding secret data within other non-secret data. It can be used alongside cryptography to further enhance security. Steganography techniques can hide data in images, video, or audio files by making small changes that are imperceptible to human senses. The hidden data could be used to protect copyrighted materials or allow unauthorized viewing of content. Information hiding through steganography or other methods can conceal communicating parties' identities, the occurrence of communications, or the content of transmitted data from attackers at different stages of a crime or attack.