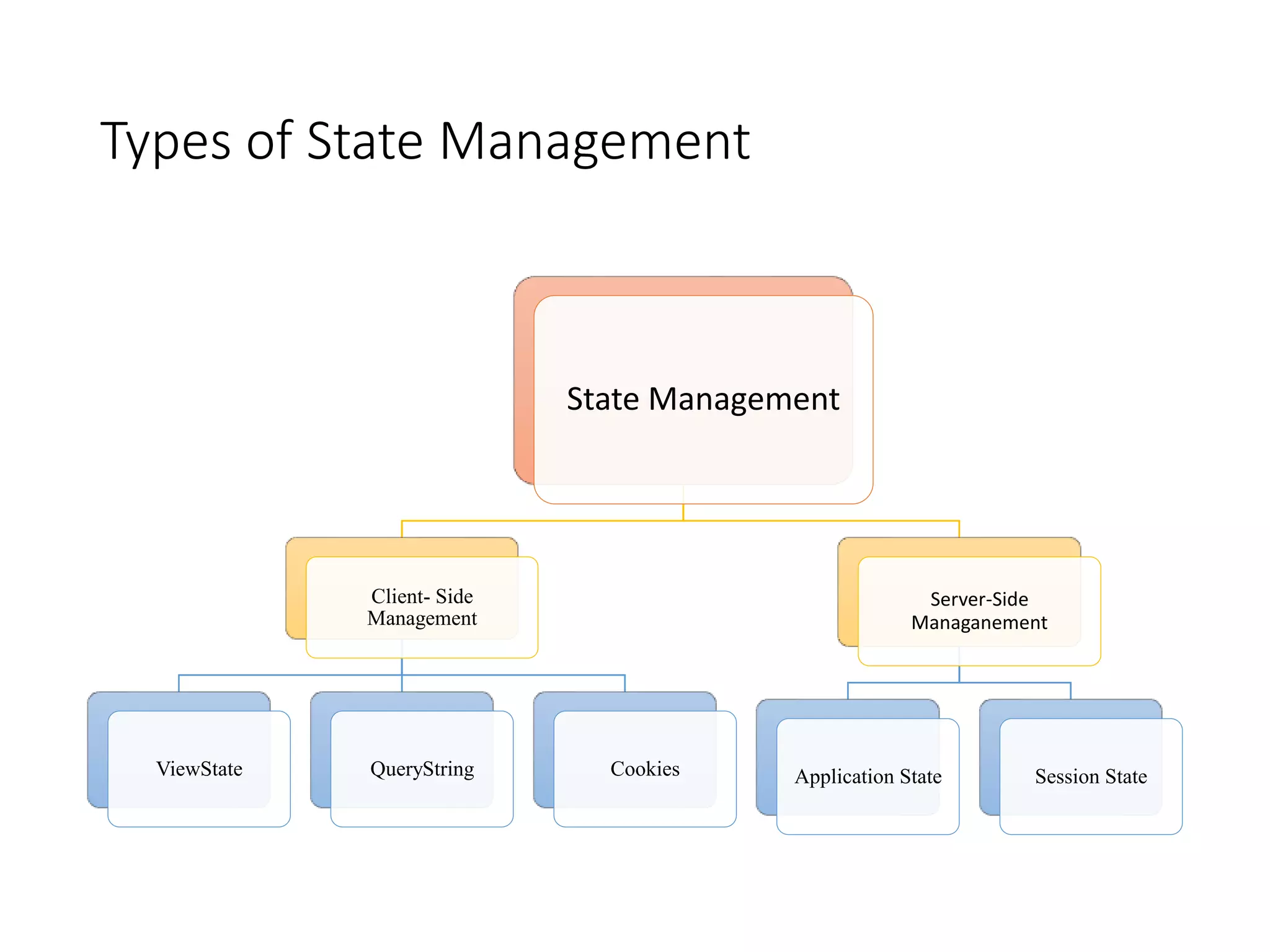
This document discusses state management in ASP.NET web applications. It begins by explaining that browsers are generally stateless and do not remember information between requests. It then discusses how state management preserves information in ASP.NET applications using techniques like view state, cookies, query strings, application state, and session state. It provides details on different state management techniques, including advantages and disadvantages of client-side techniques like view state, cookies, and query strings versus server-side techniques.








![How to store the value in ViewState?
• ViewState stores the value in a Key/Value pair basis.
Syntax
ViewState[“KeyName”] = Object / String .etc.](https://image.slidesharecdn.com/statemanagement-220911173306-3f42aebb/75/State-Management-pptx-14-2048.jpg)






![Sending Only One Querystring Value
• Sender Page:
Response.Redirect(“PageName+Keyname=Value”);
• Receiver Page:
Str = Request.QueryString[“Keyname”];](https://image.slidesharecdn.com/statemanagement-220911173306-3f42aebb/75/State-Management-pptx-23-2048.jpg)
![Sending More Than One Querystring Value
• Sender Page:
Response.Redirect(“PageName+Keyname1=Value1&KeyName2=
Value2”);
• Receiver Page:
Str1 = Request.QueryString[“Keyname1”];
Str2 = Request.QueryString[“Keyname2”];](https://image.slidesharecdn.com/statemanagement-220911173306-3f42aebb/75/State-Management-pptx-24-2048.jpg)




![Continue…
• Store Value:
HttpCookie Cookiename = new HttpCookie(“Storecookiename”);
Cookiename.Values[“Keyname”] = Value;
Cookiename.Expires = DateTime.Now.AddDays(1);
Response.Cookies.Add(Cookiename);
• Fetch Value:
Variable name = Request.Cookies[“Storecookiename”].Values["KeyName"].ToString();](https://image.slidesharecdn.com/statemanagement-220911173306-3f42aebb/75/State-Management-pptx-29-2048.jpg)

