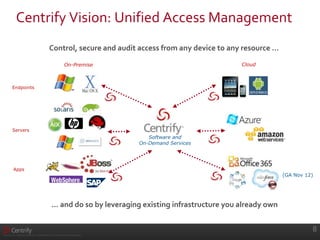
Centrify provides software that secures access to systems, devices, and apps from any endpoint. It delivers unified access control, auditing, and analytics by leveraging existing Active Directory infrastructure. This addresses trends of increasing IT heterogeneity, hybrid cloud/on-premise environments, and rising compliance needs. Centrify offers single sign-on and granular role-based access control to over 300 non-Microsoft systems via Active Directory. It also provides complete user activity auditing and analytics to analyze security risks.