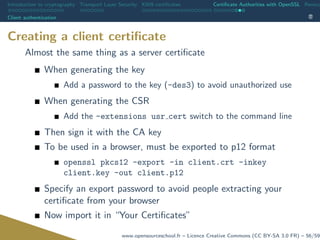
The document outlines the establishment of the Open Source School in France, which aims to address the growing demand for skills in the open-source software sector supported by a government grant of €1.4 million. It offers a range of educational programs in open-source technologies for both initial training and continuing education, catering to the high number of unfilled positions in the field. The document also covers essential topics in cryptography and transport layer security (TLS), including the importance of public key infrastructure and secure communication methods.








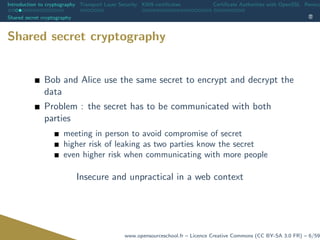




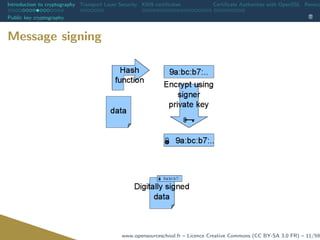
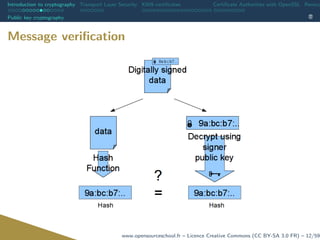

































![Introduction to cryptography Transport Layer Security X509 certificates Certificate Authorities with OpenSSL Revoca
Configuring the CA
Configuring the CA
Create a section at the end of /etc/ssl/openssl.cnf
[ my ca ]
d i r = /home/ formation /my ca
database = $ d i r / index . t x t
n e w c e r t s d i r = $ d i r / newcerts
c e r t i f i c a t e = $ d i r / c a c e r t . pem
s e r i a l = $ d i r / s e r i a l
p r i v a t e k e y = $ d i r / p r i v a t e / cakey . pem
RANDFILE = $ d i r / p r i v a t e /. rand
d e f a u l t d a y s = 365
d e f a u l t c r l d a y s= 30
default md = md5
p o l i c y = p o l i c y a n y t h i n g
e m a i l i n d n = no
name opt = c a d e f a u l t
c e r t o p t = c a d e f a u l t
c o p y e x t e n s i o n s = none
www.opensourceschool.fr – Licence Creative Commons (CC BY-SA 3.0 FR) – 50/59](https://image.slidesharecdn.com/02-osstheoryandpractice-160526155616-180725085254/85/SSL-Theory-and-practice-53-320.jpg)