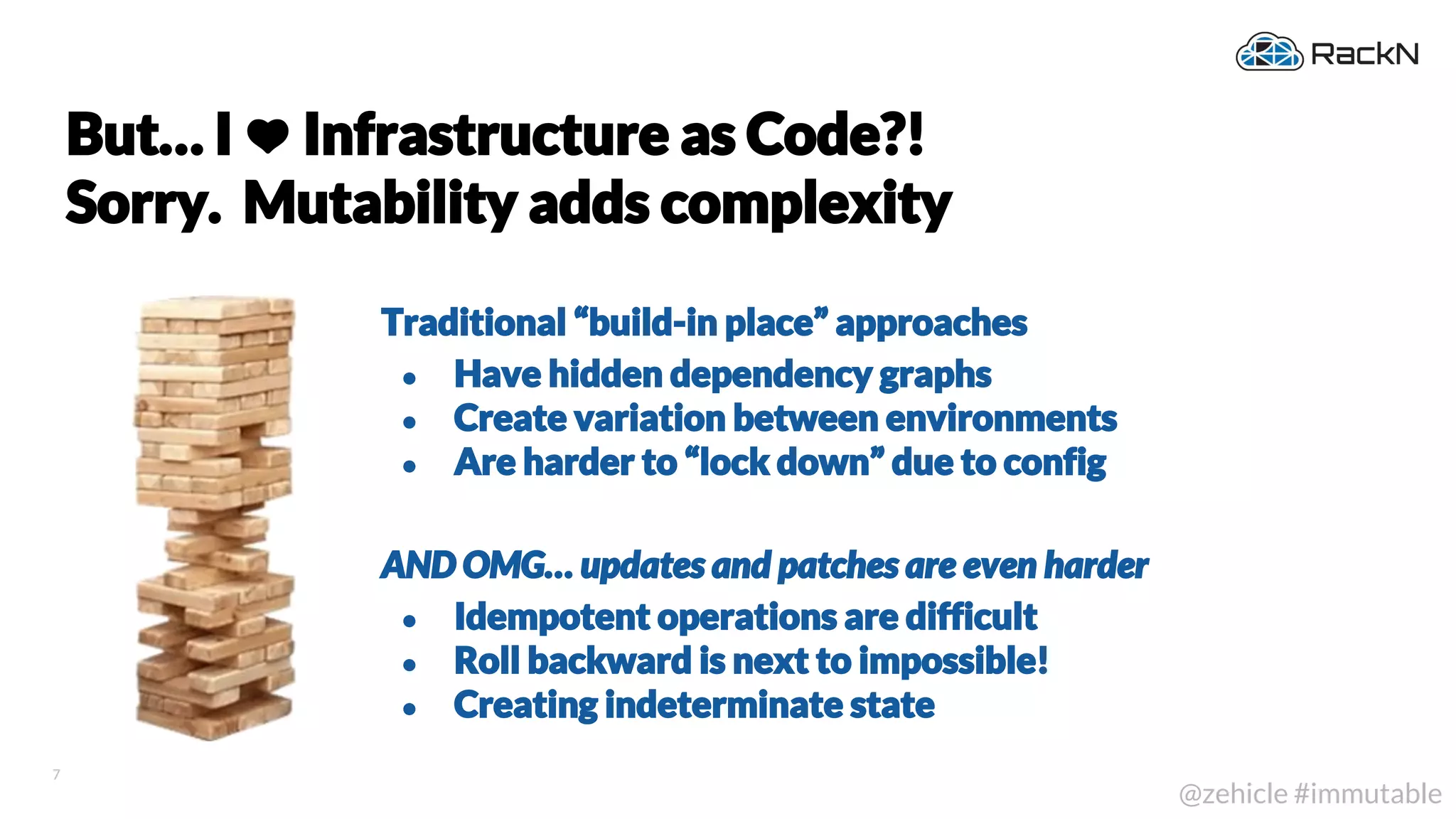
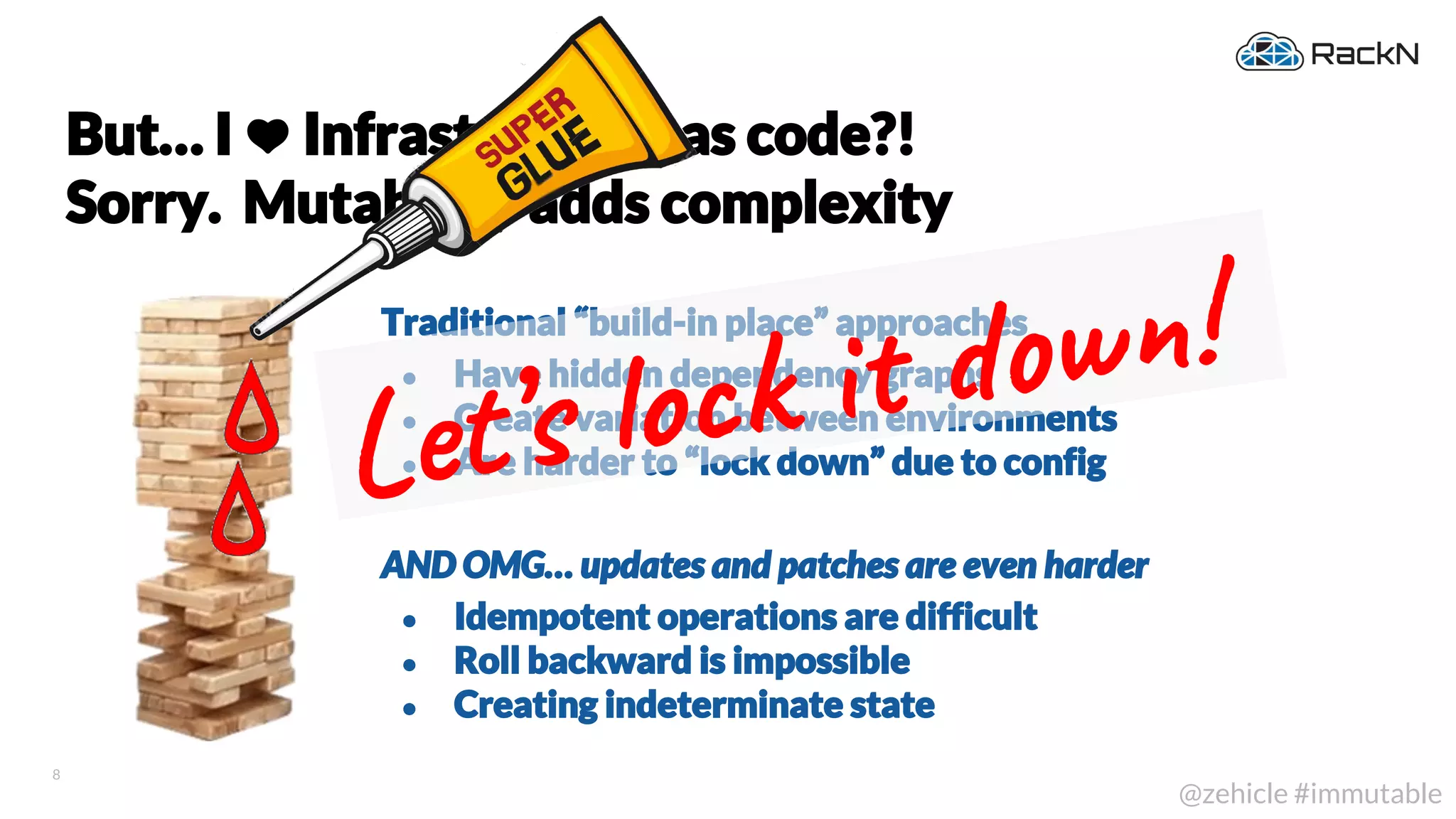
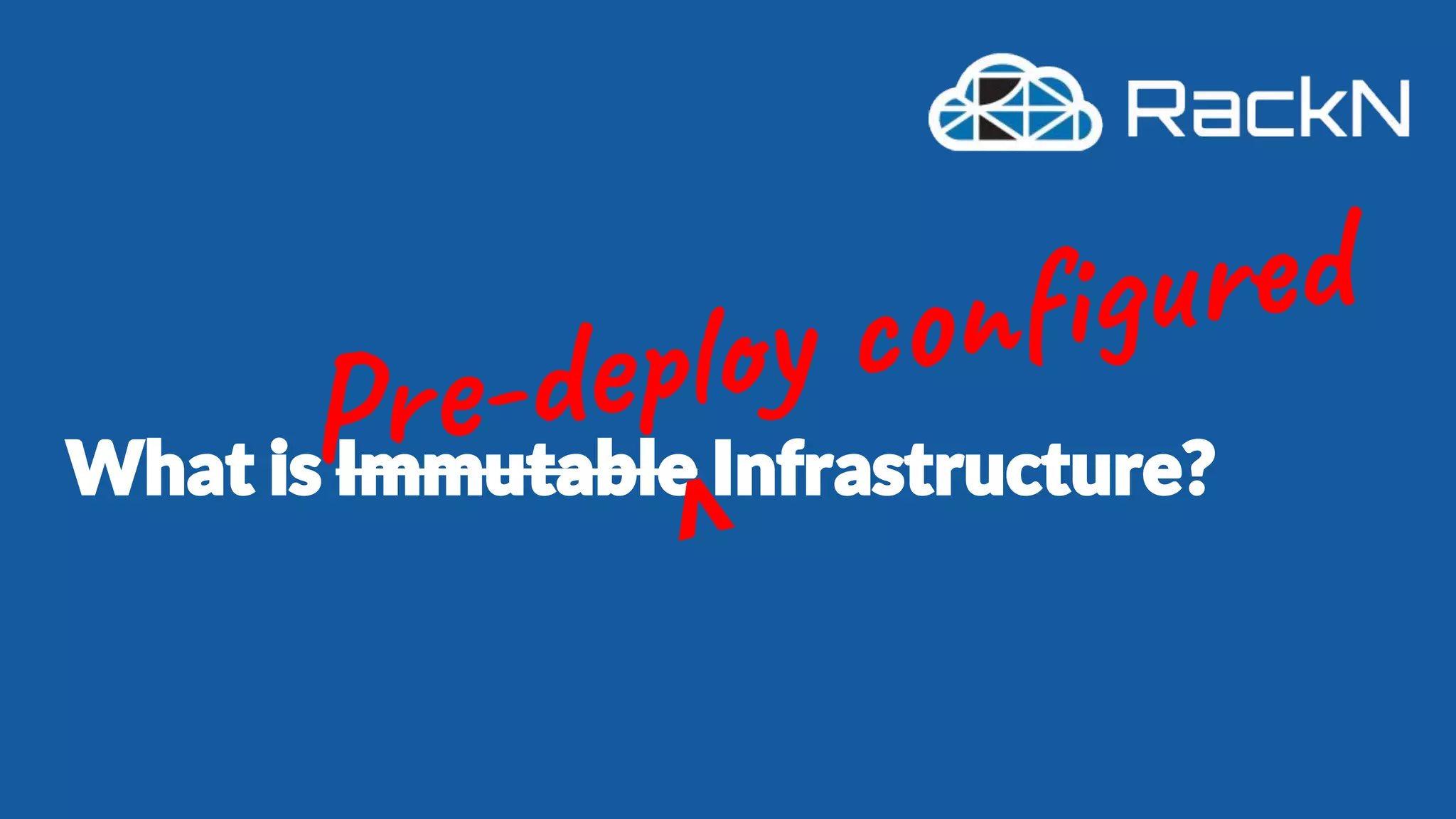
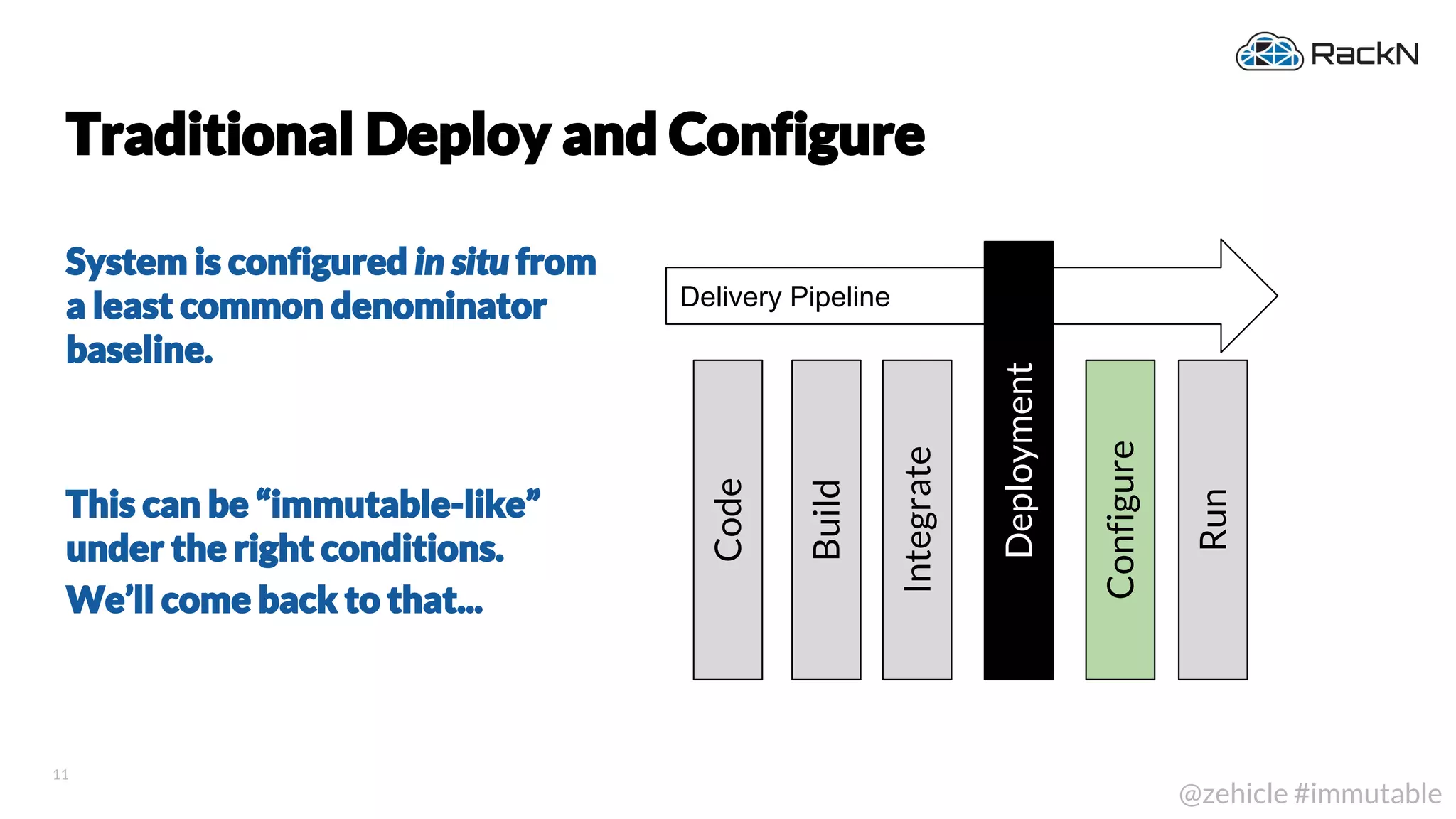
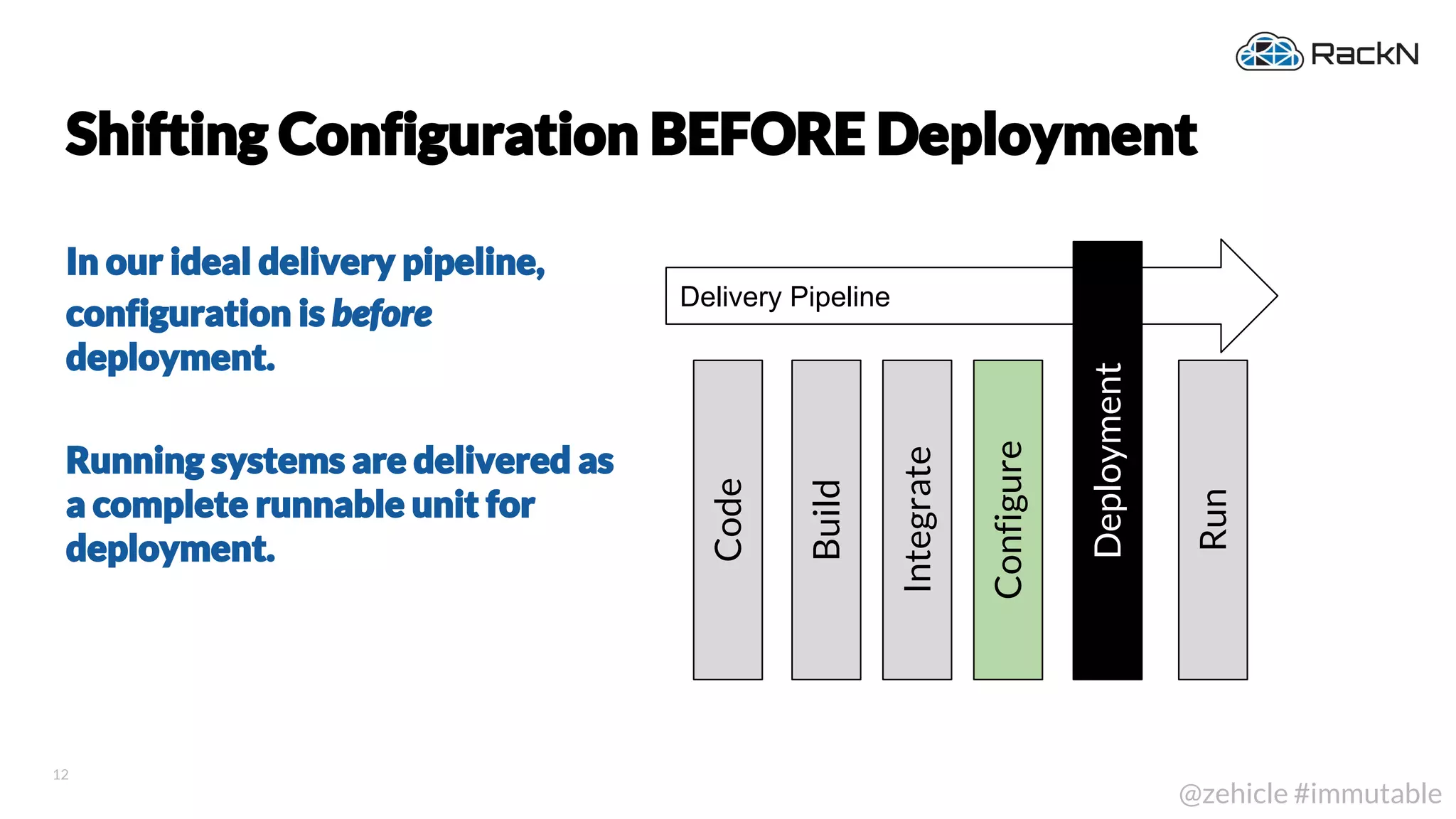
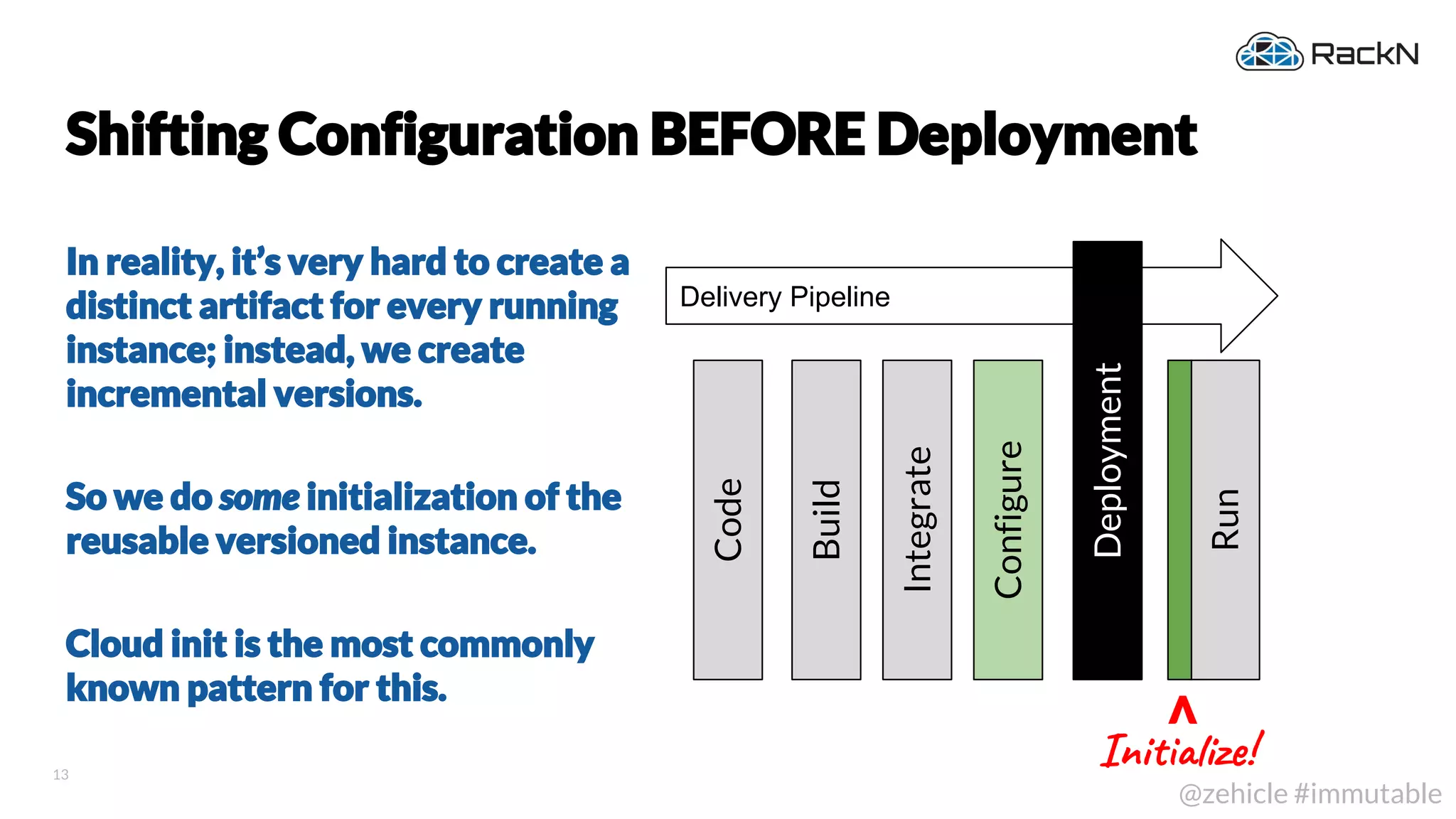
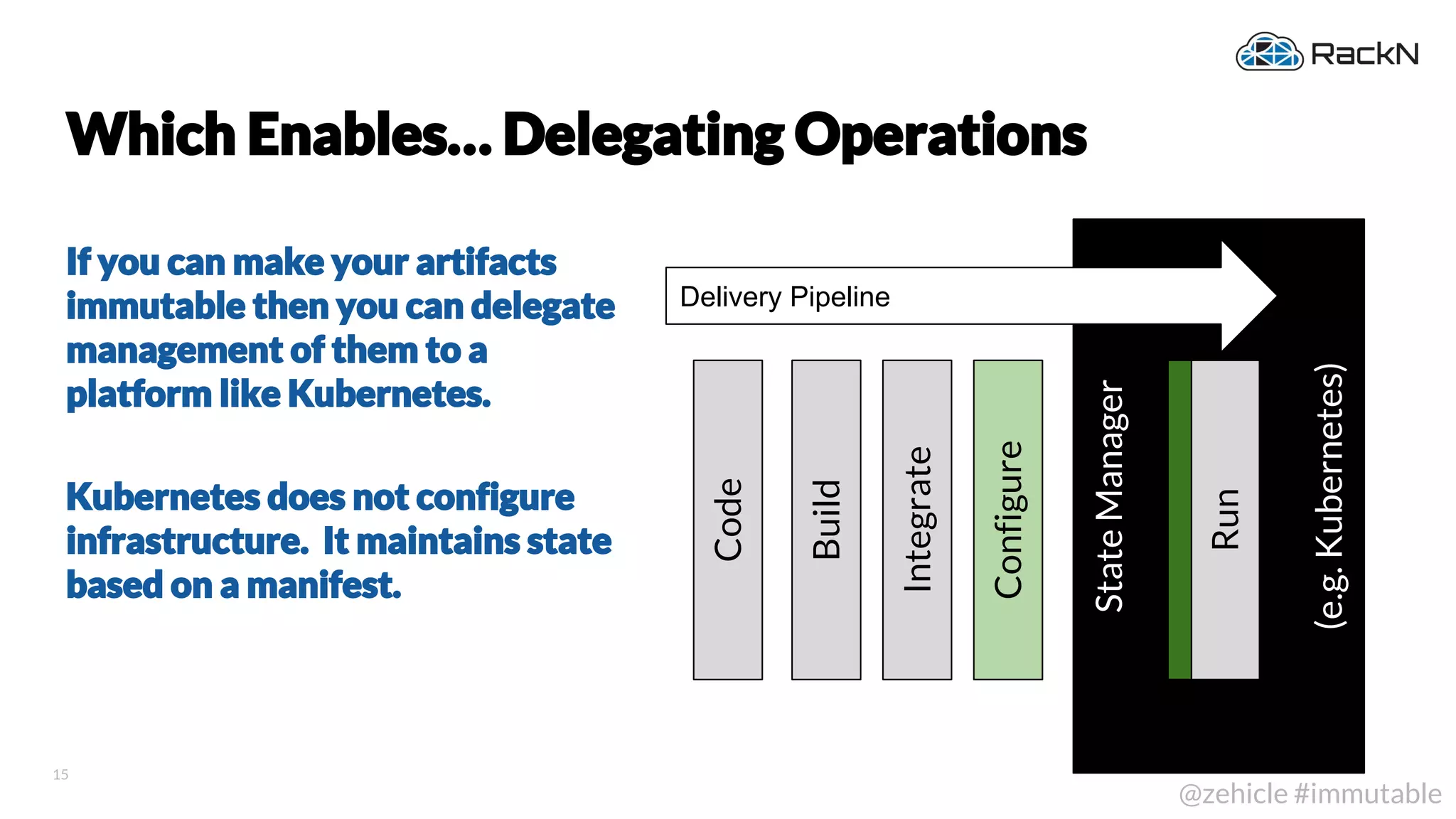
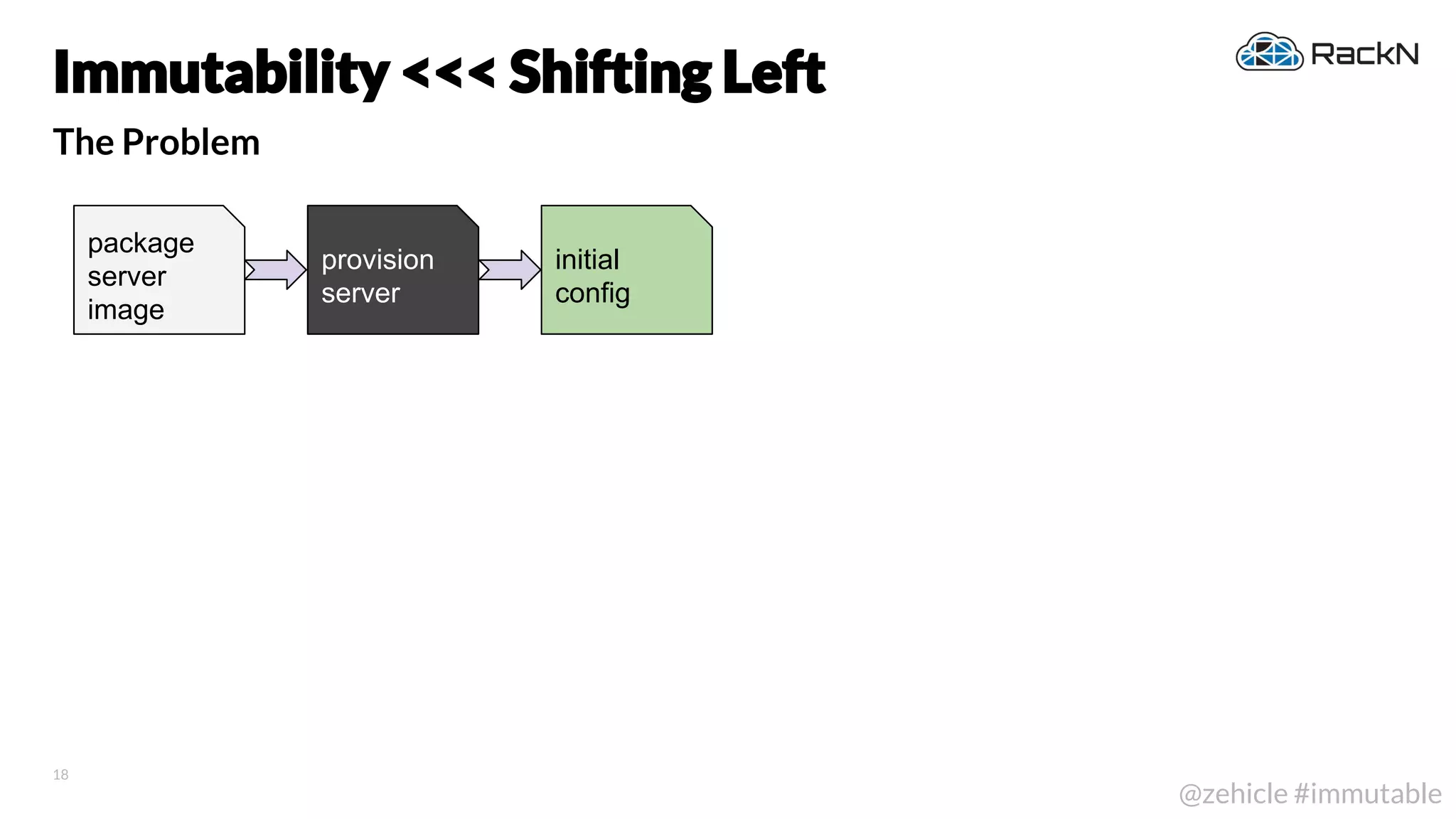
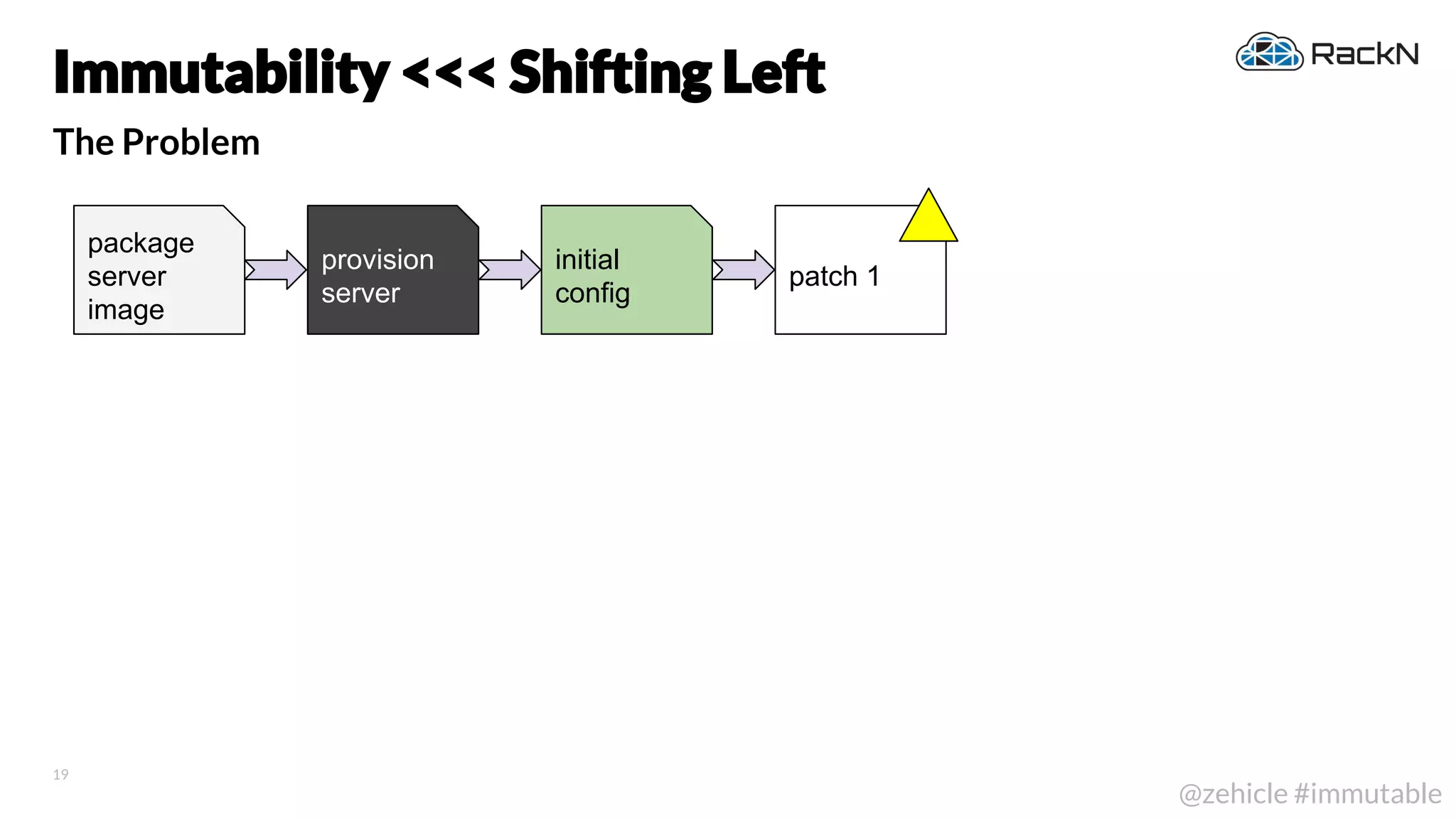
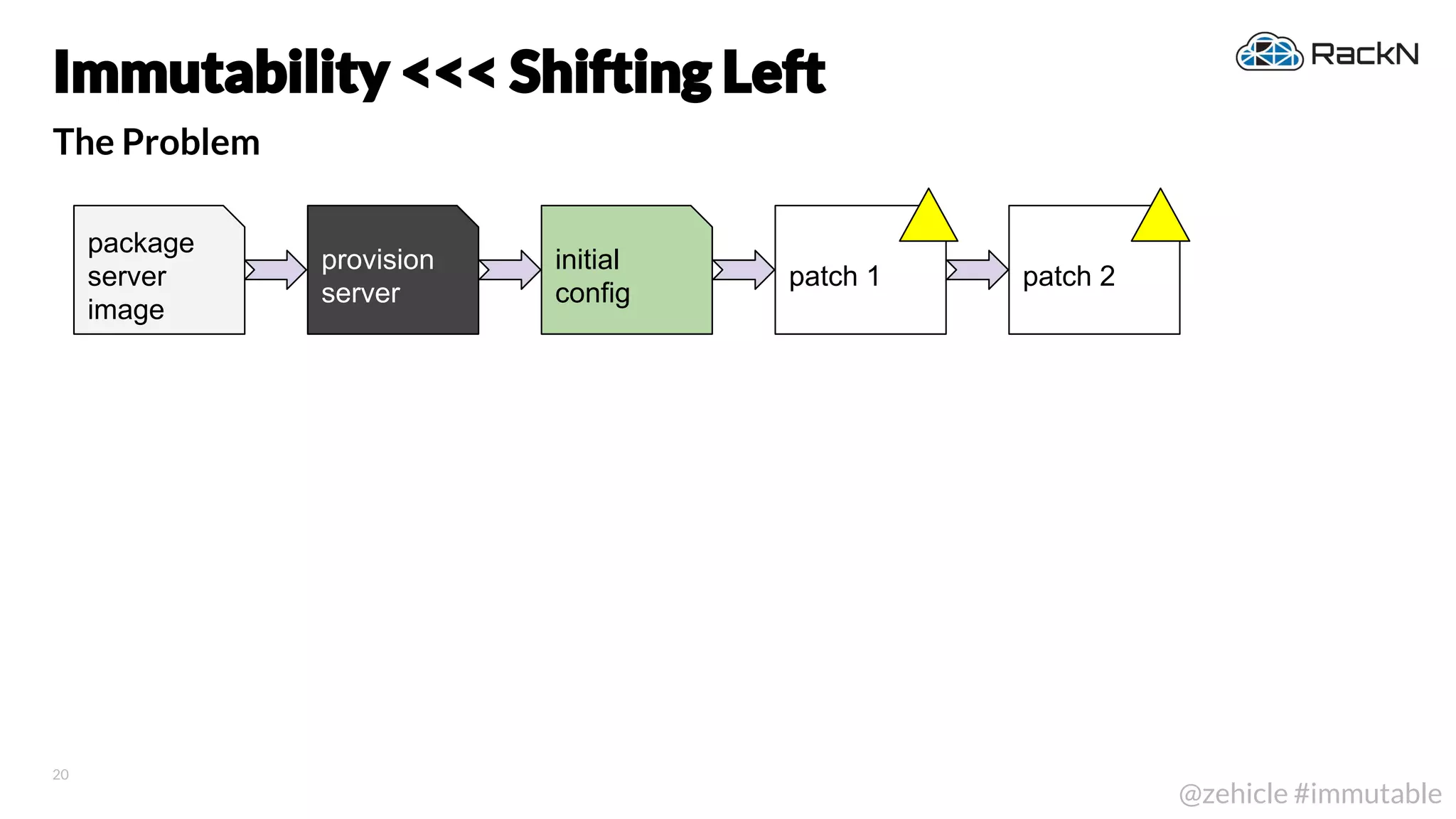
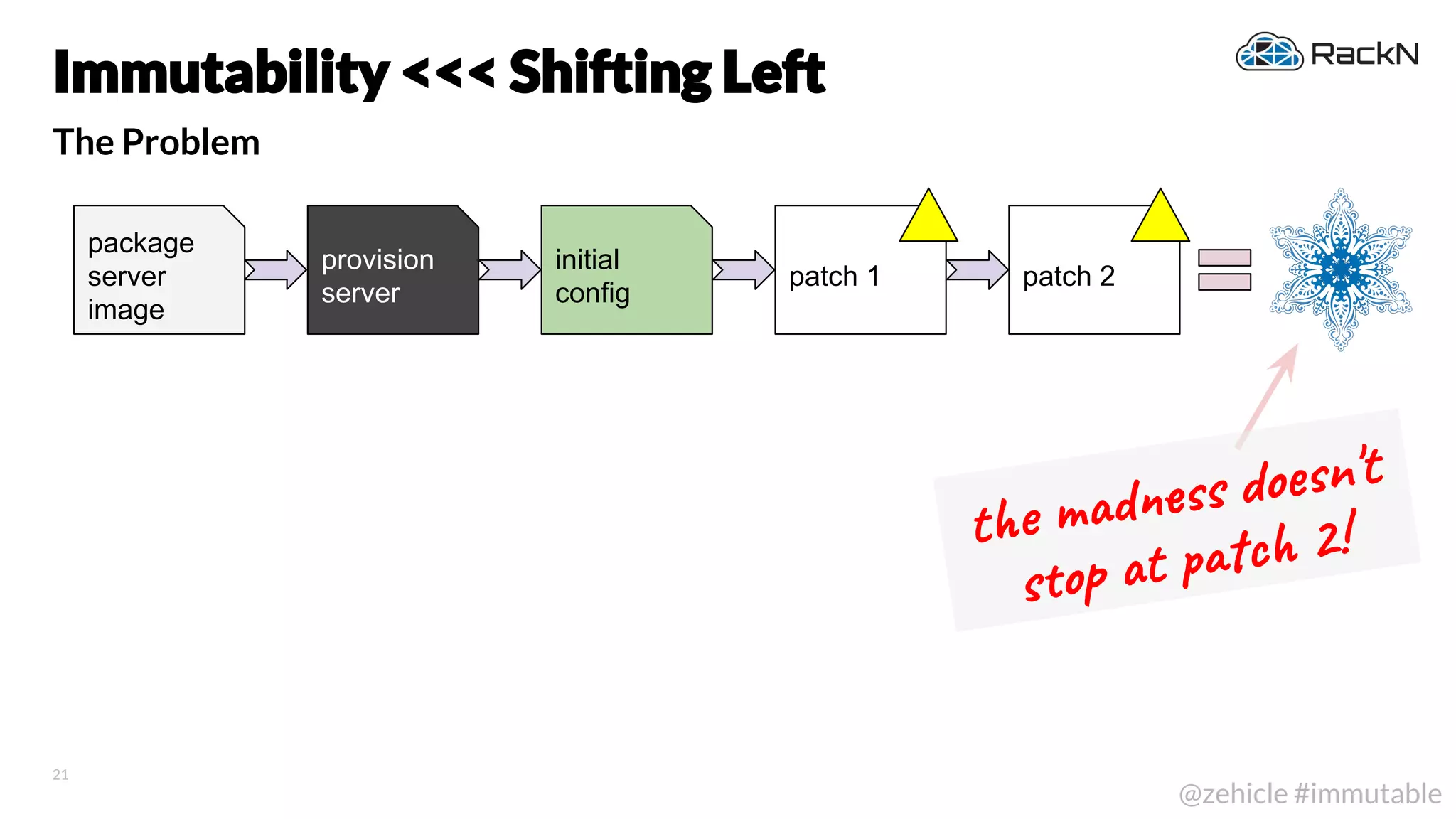
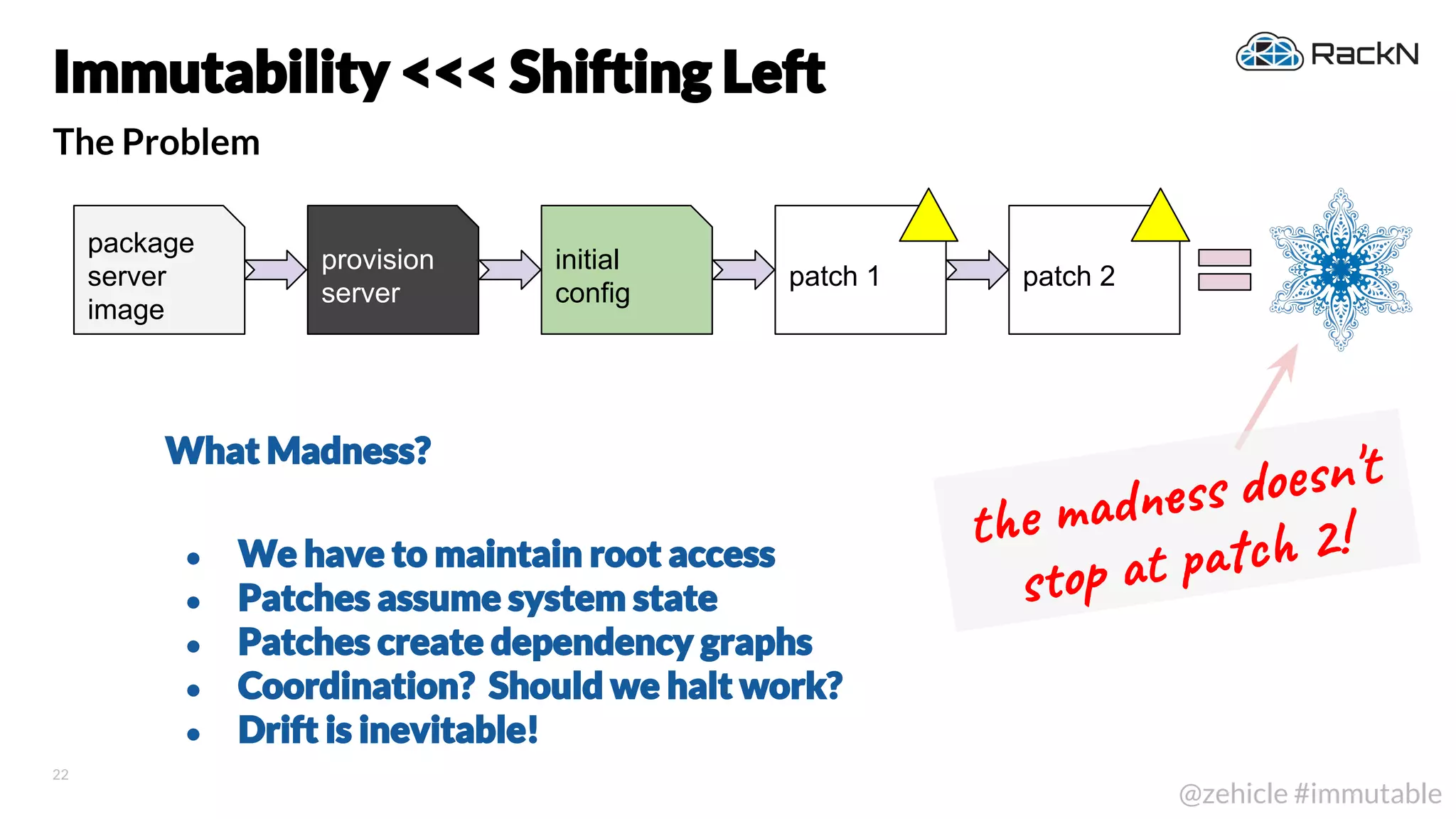
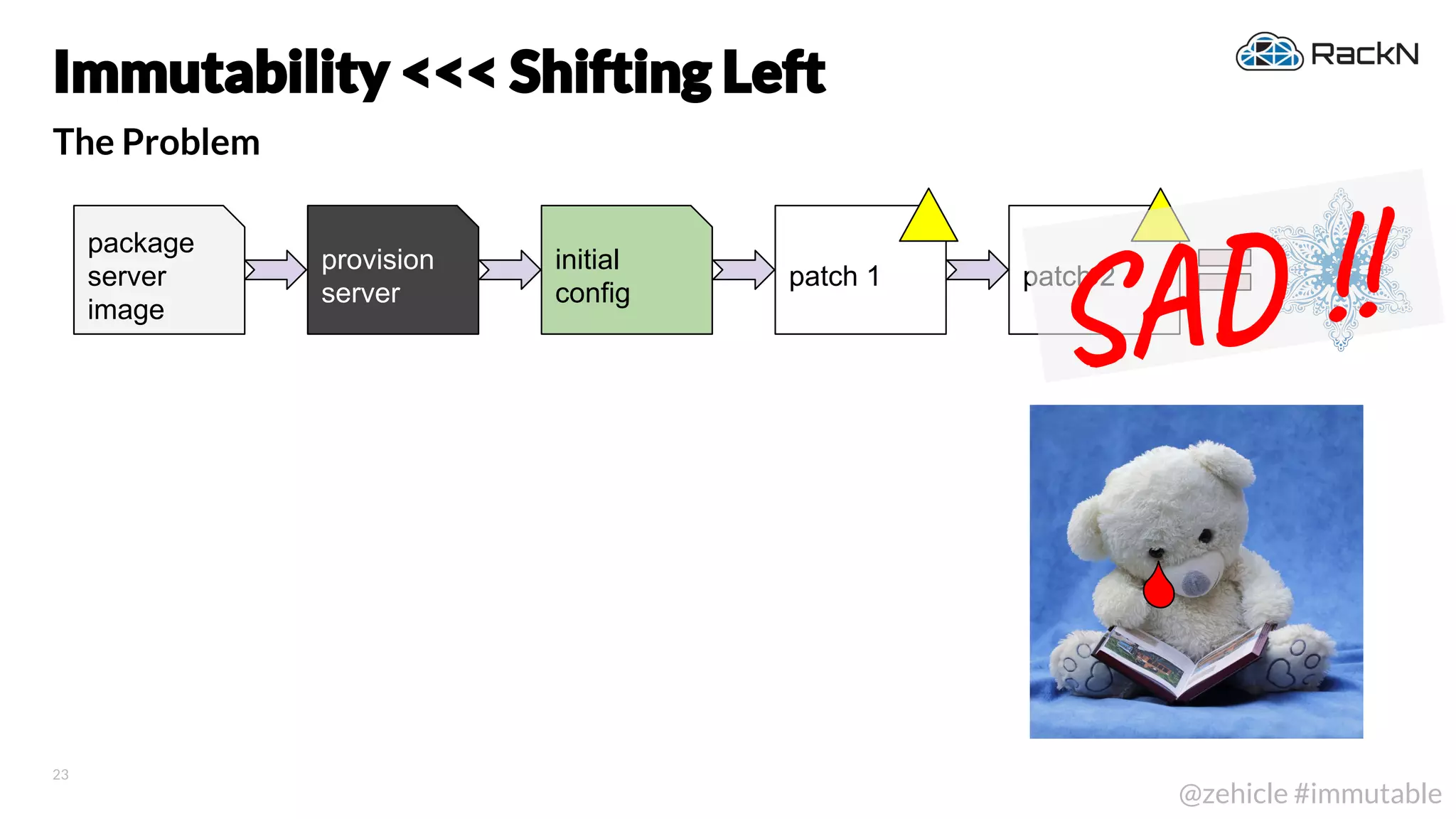
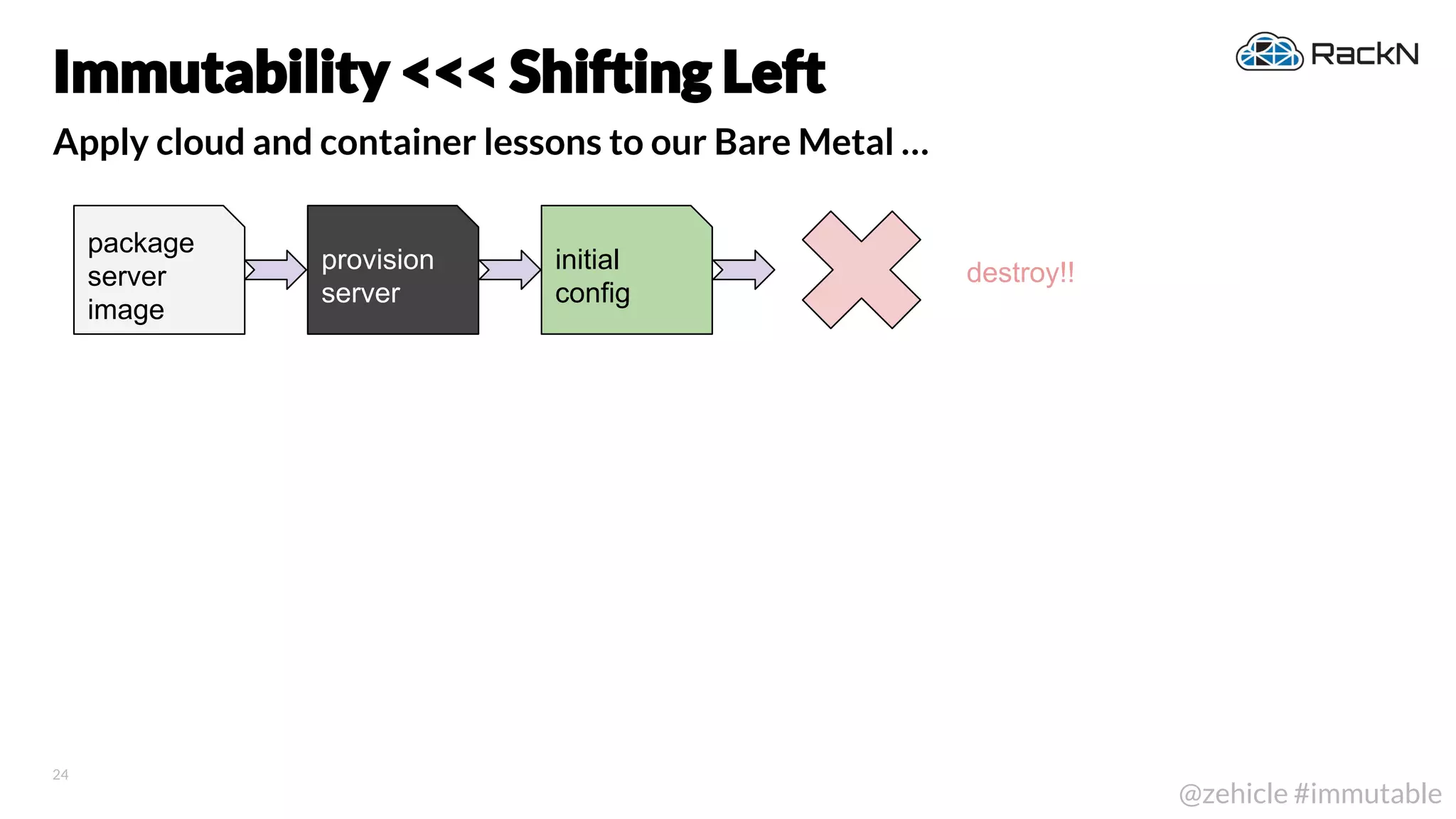
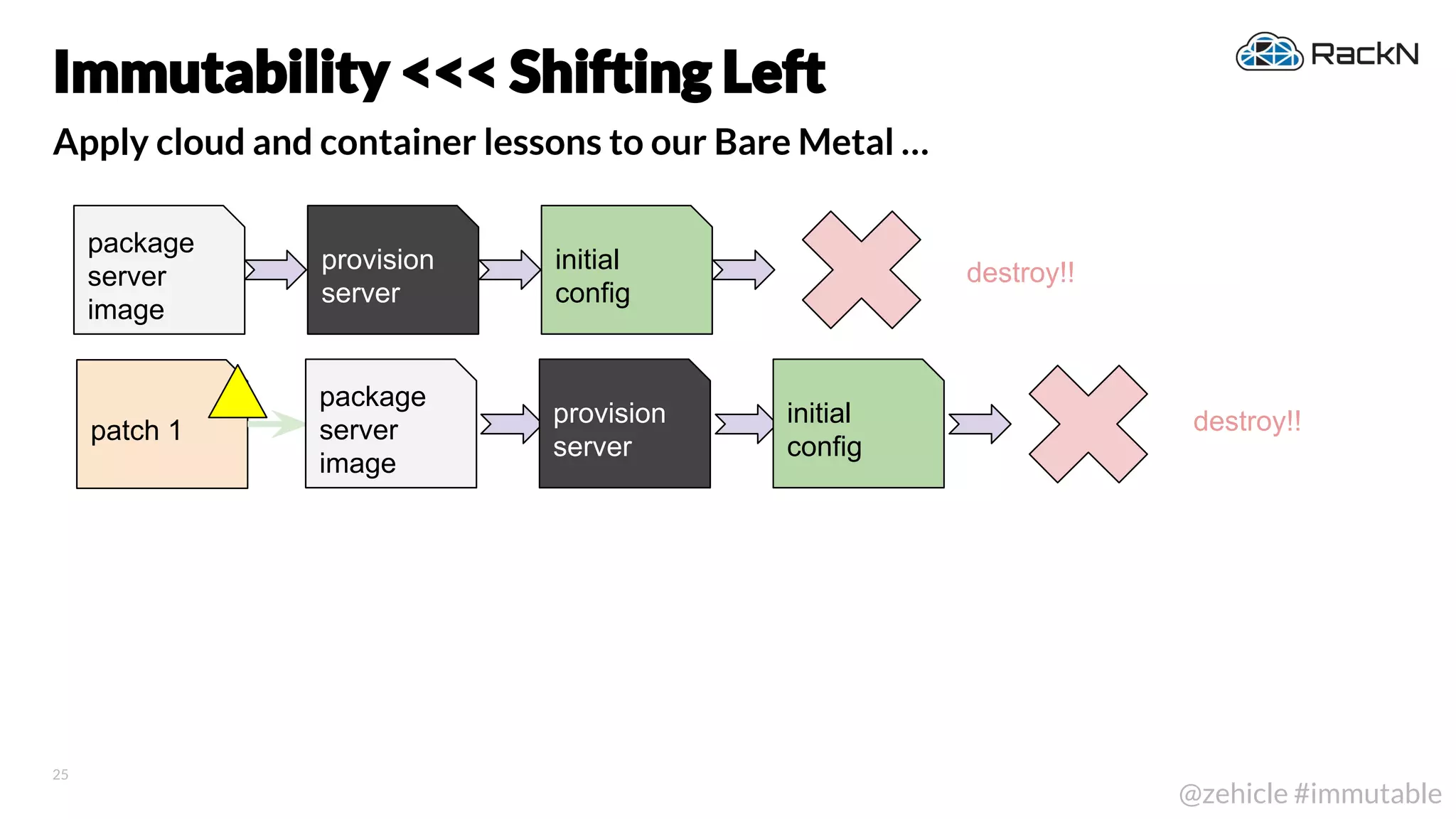
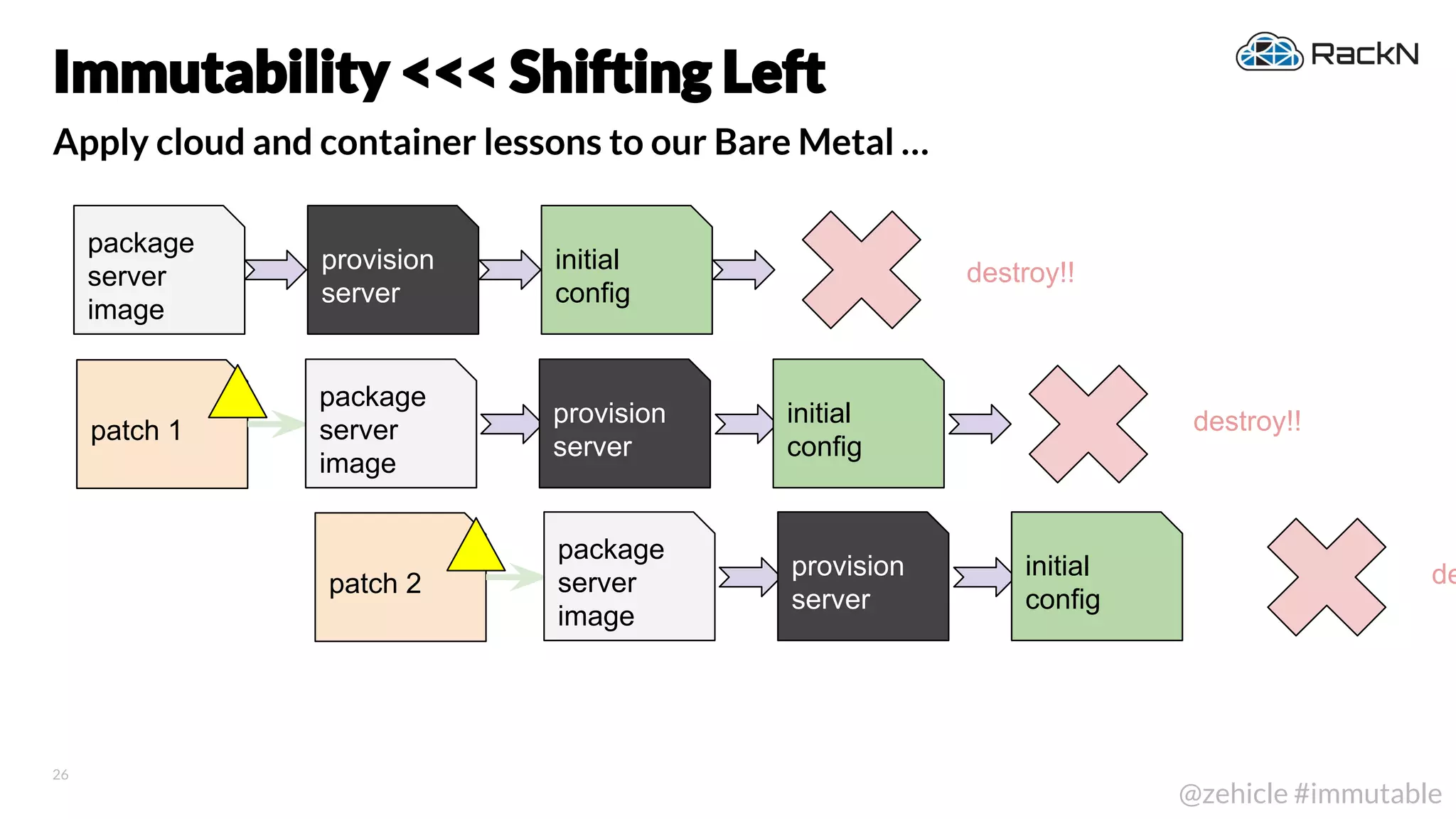
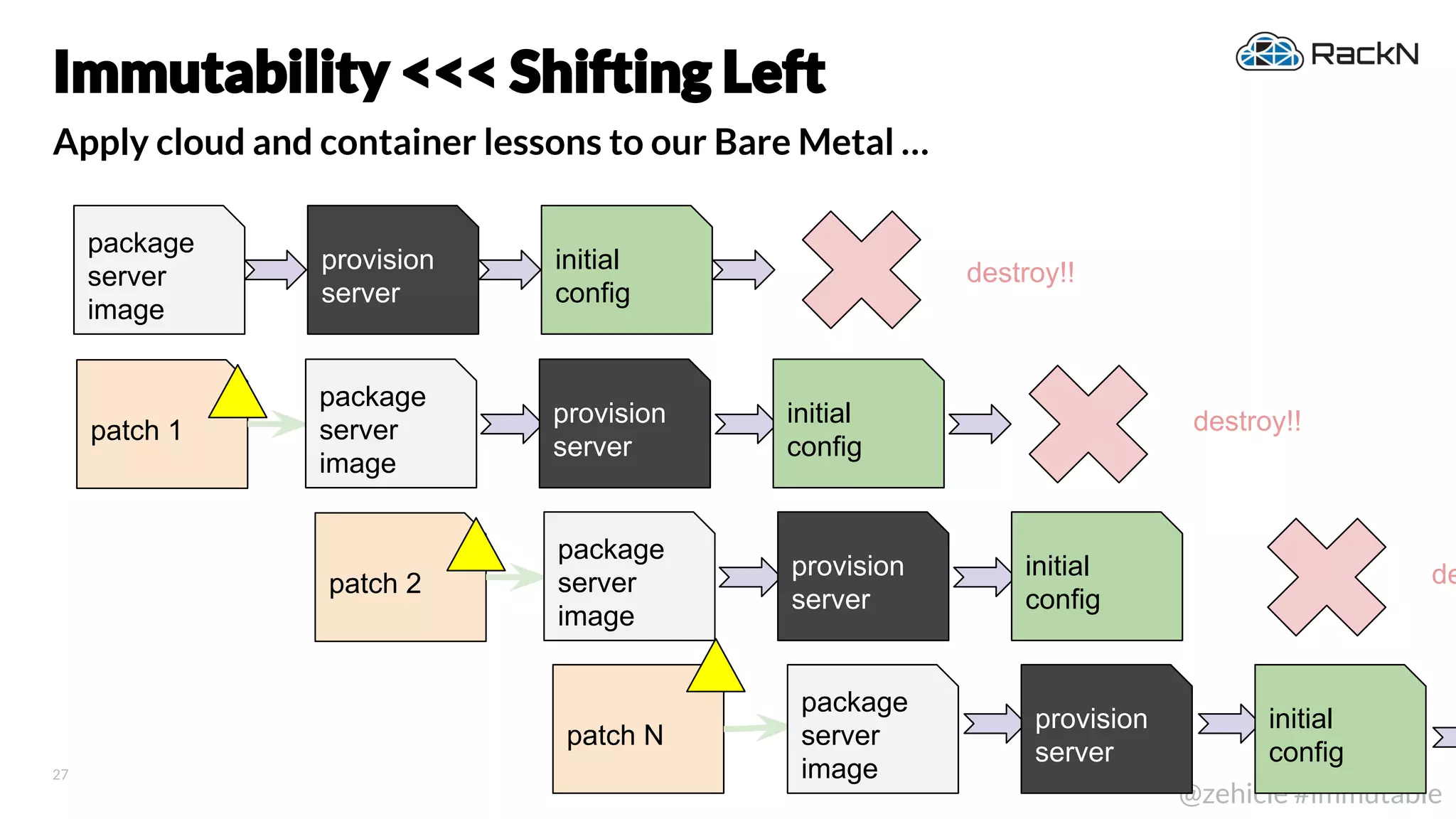
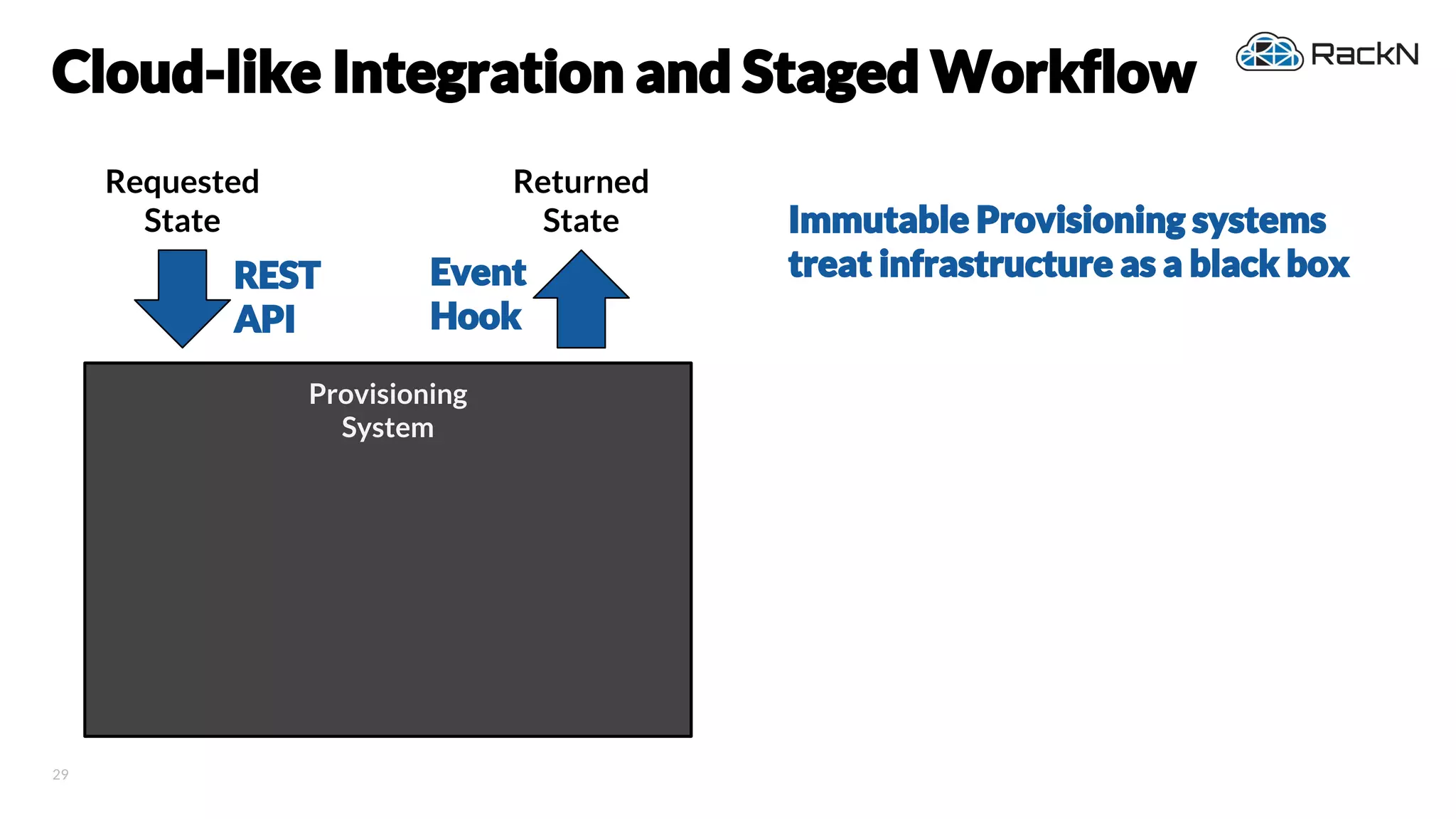
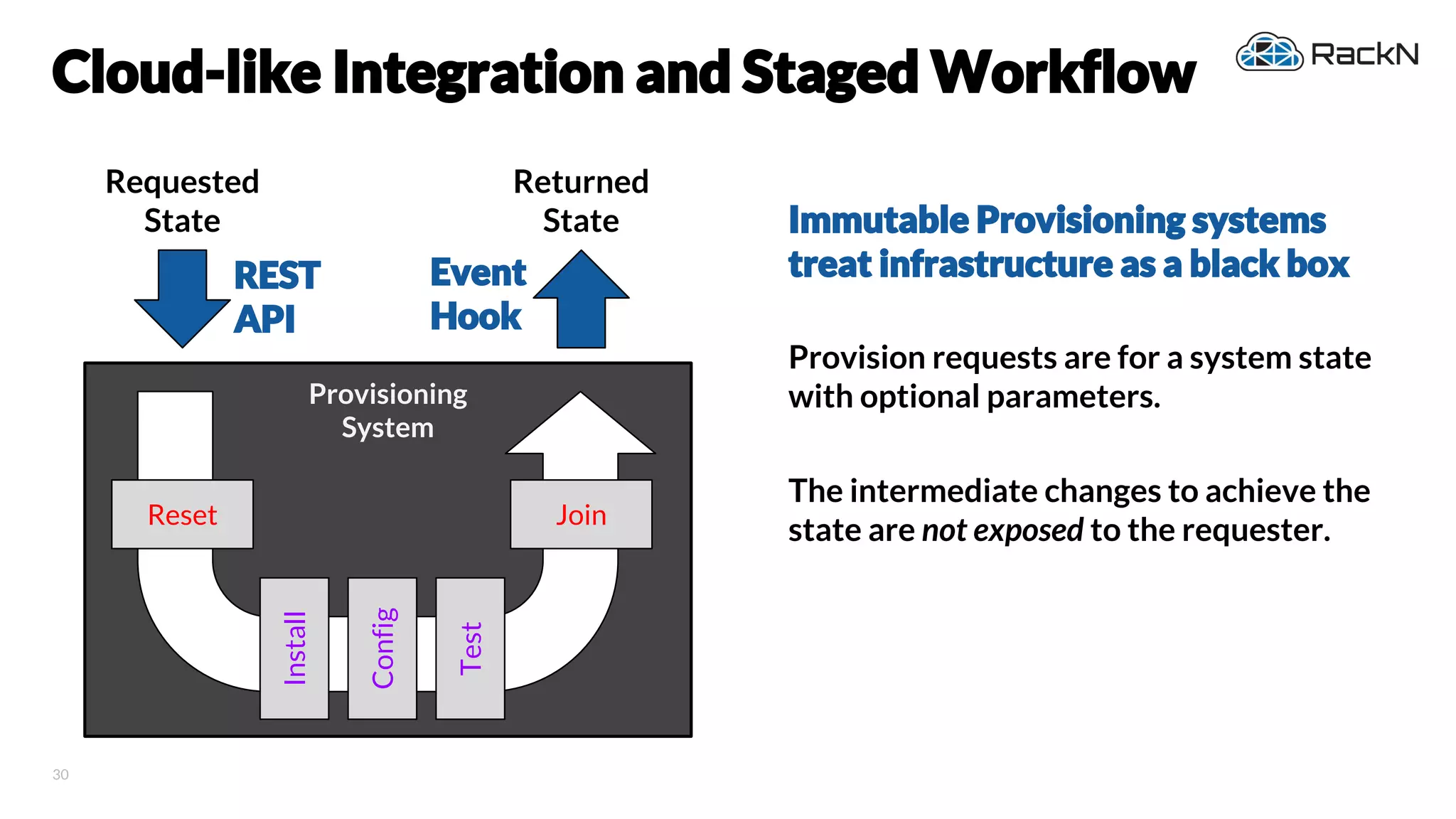
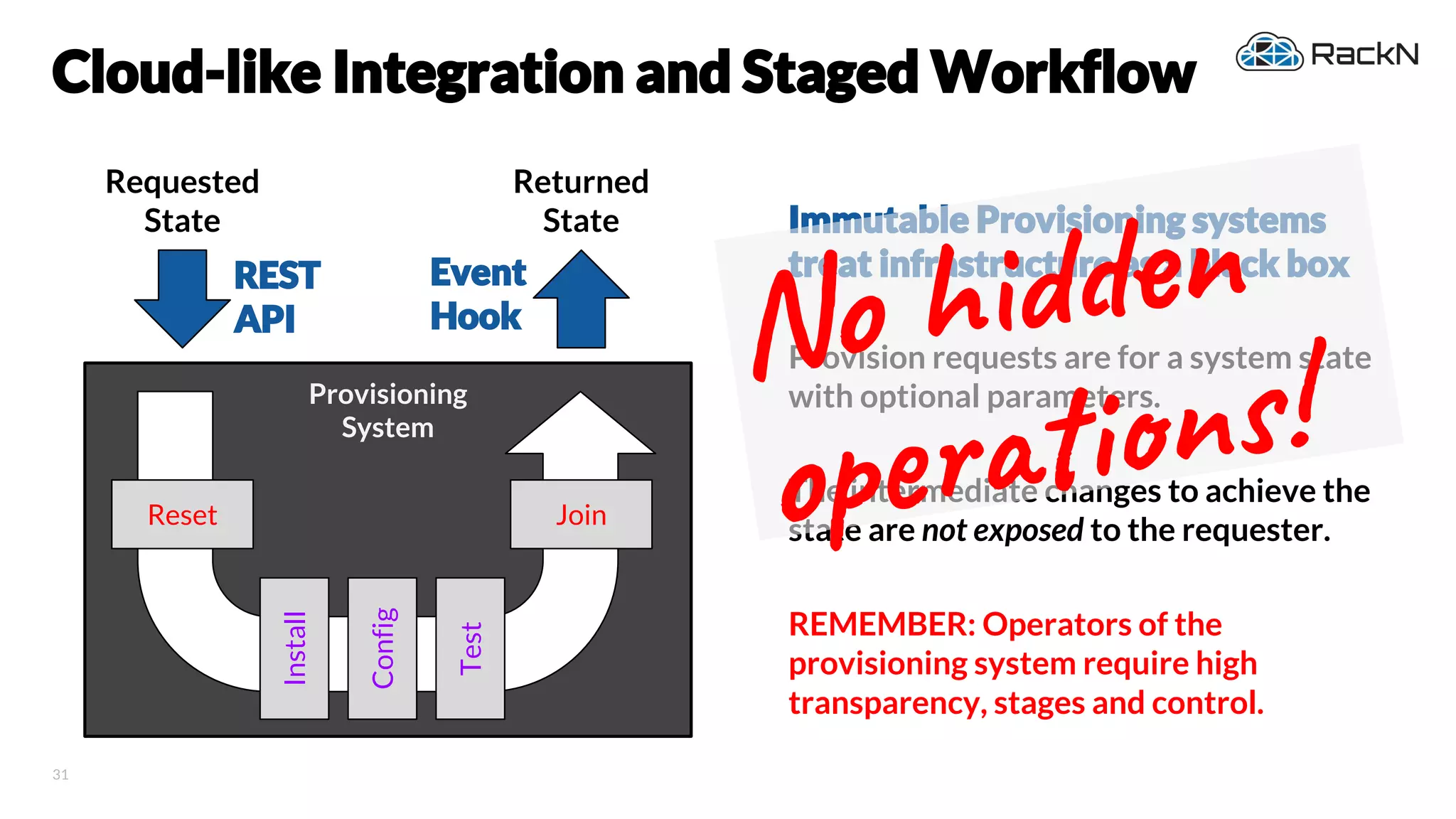
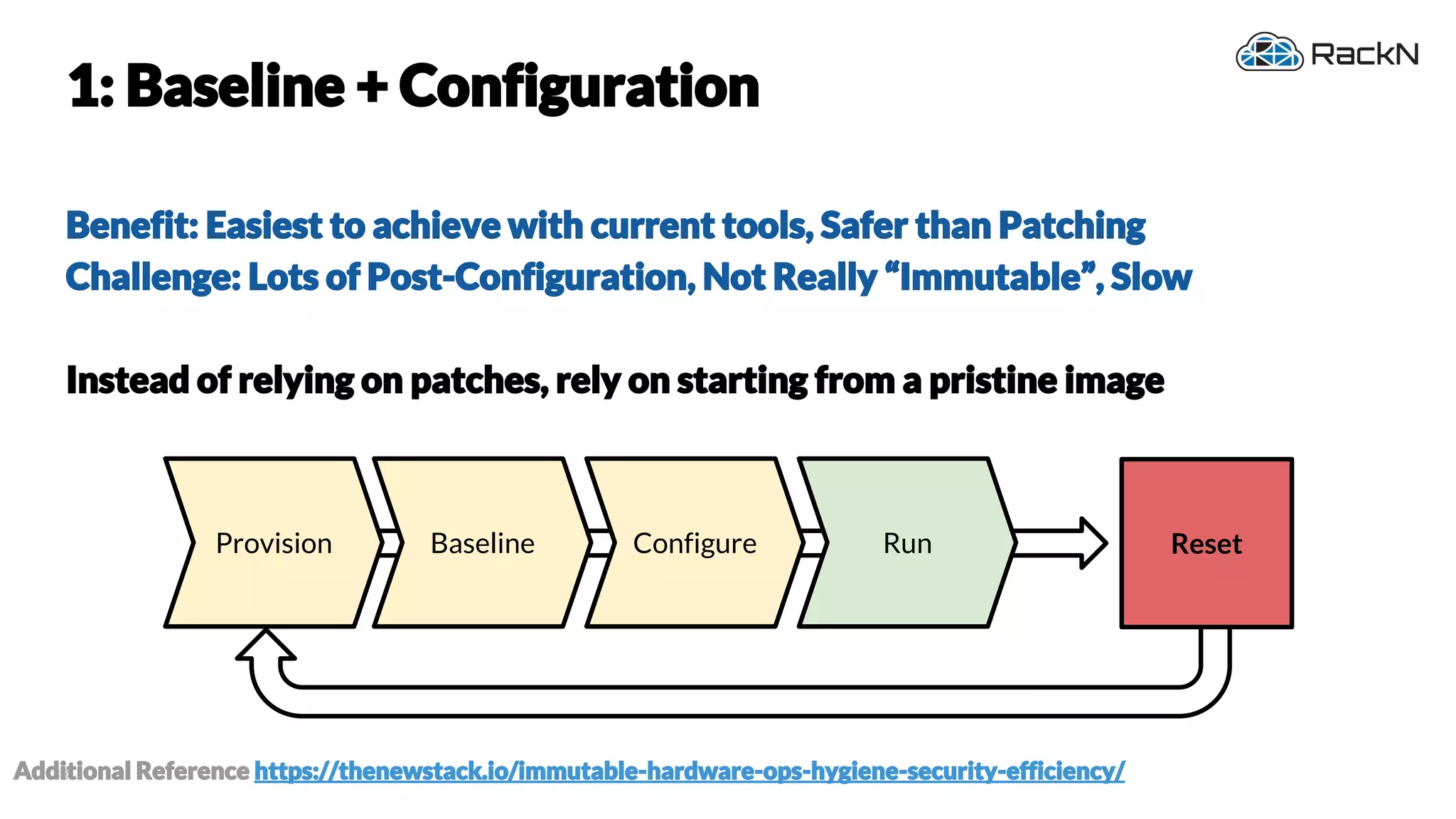
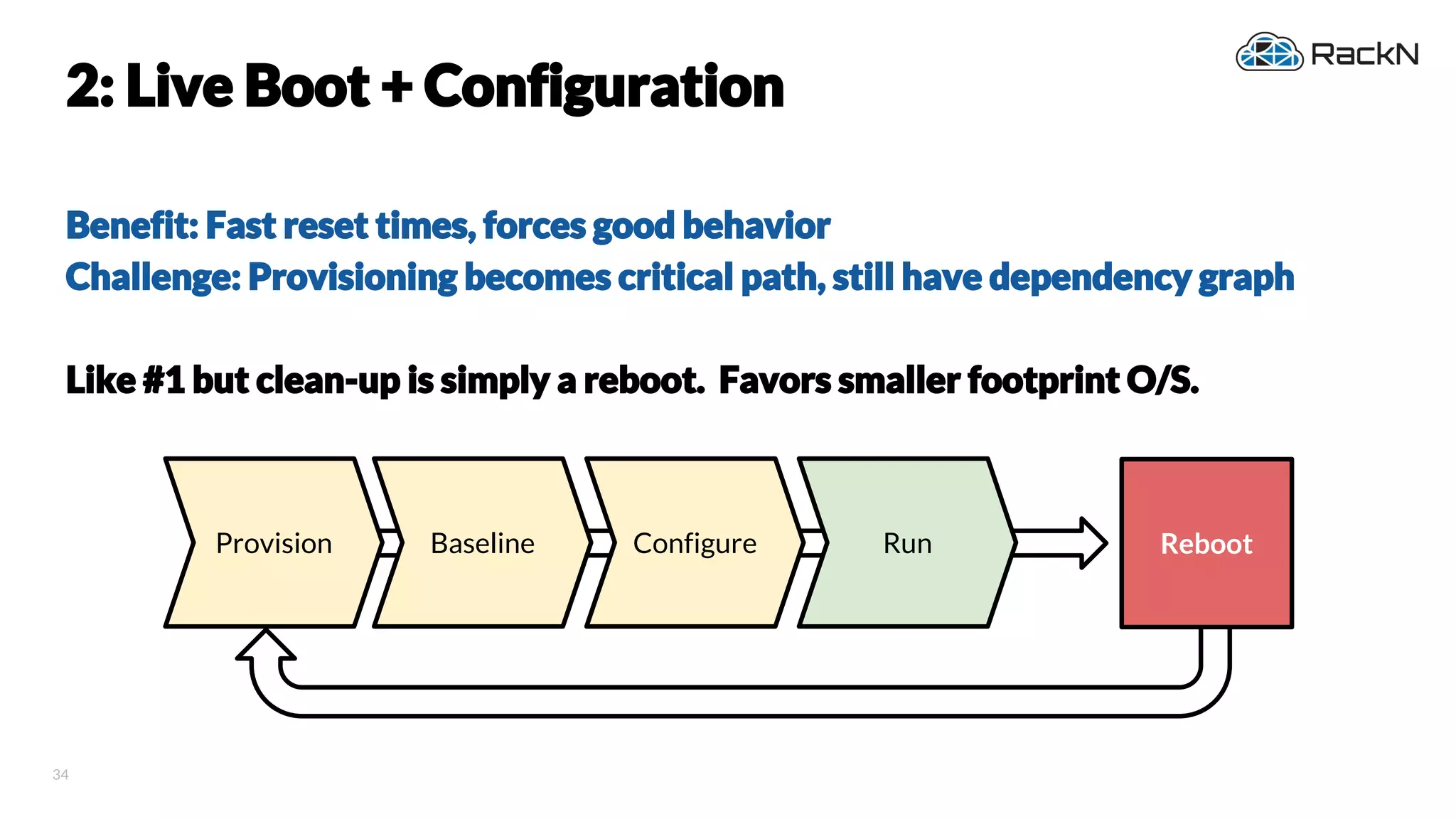
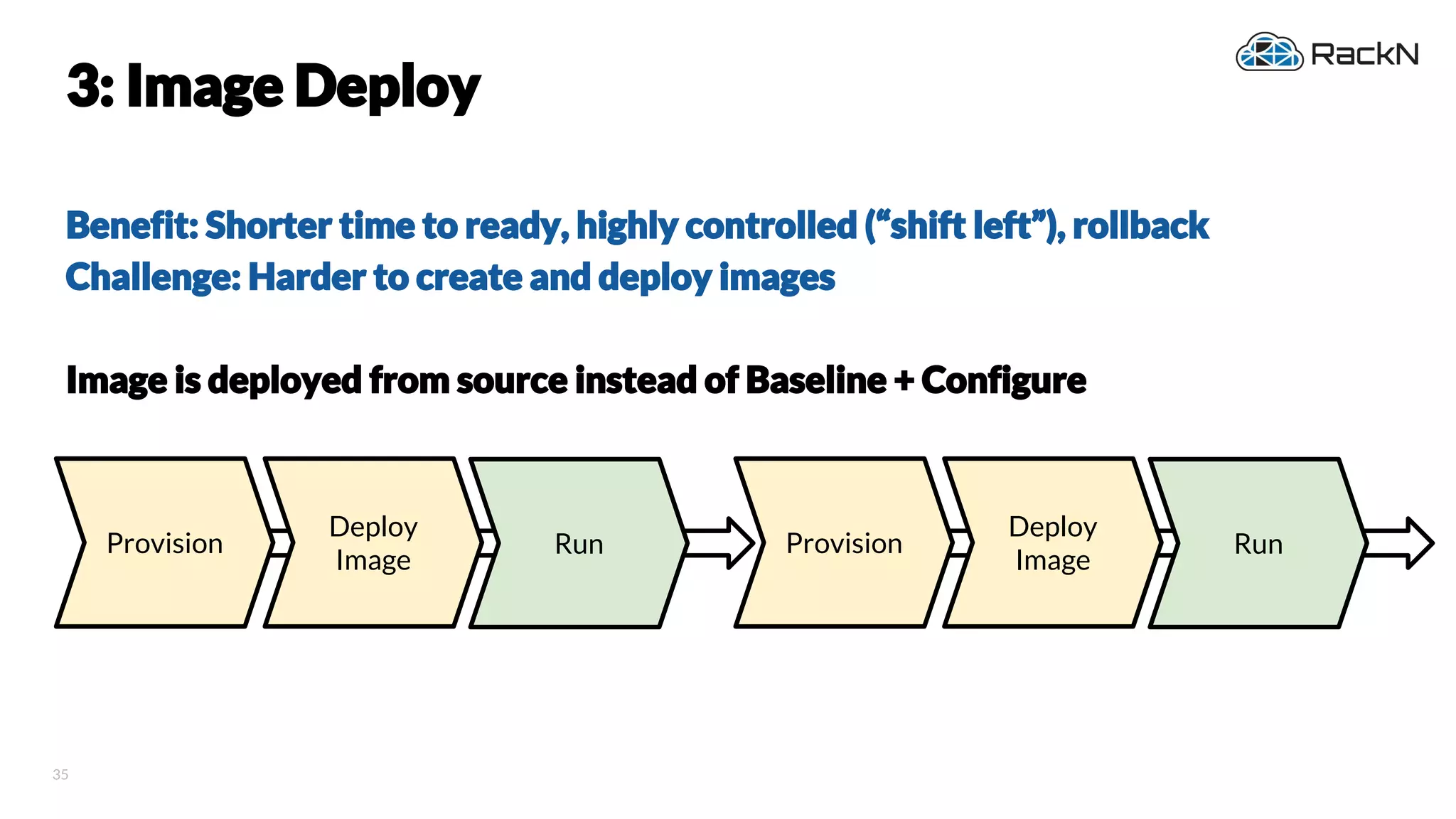
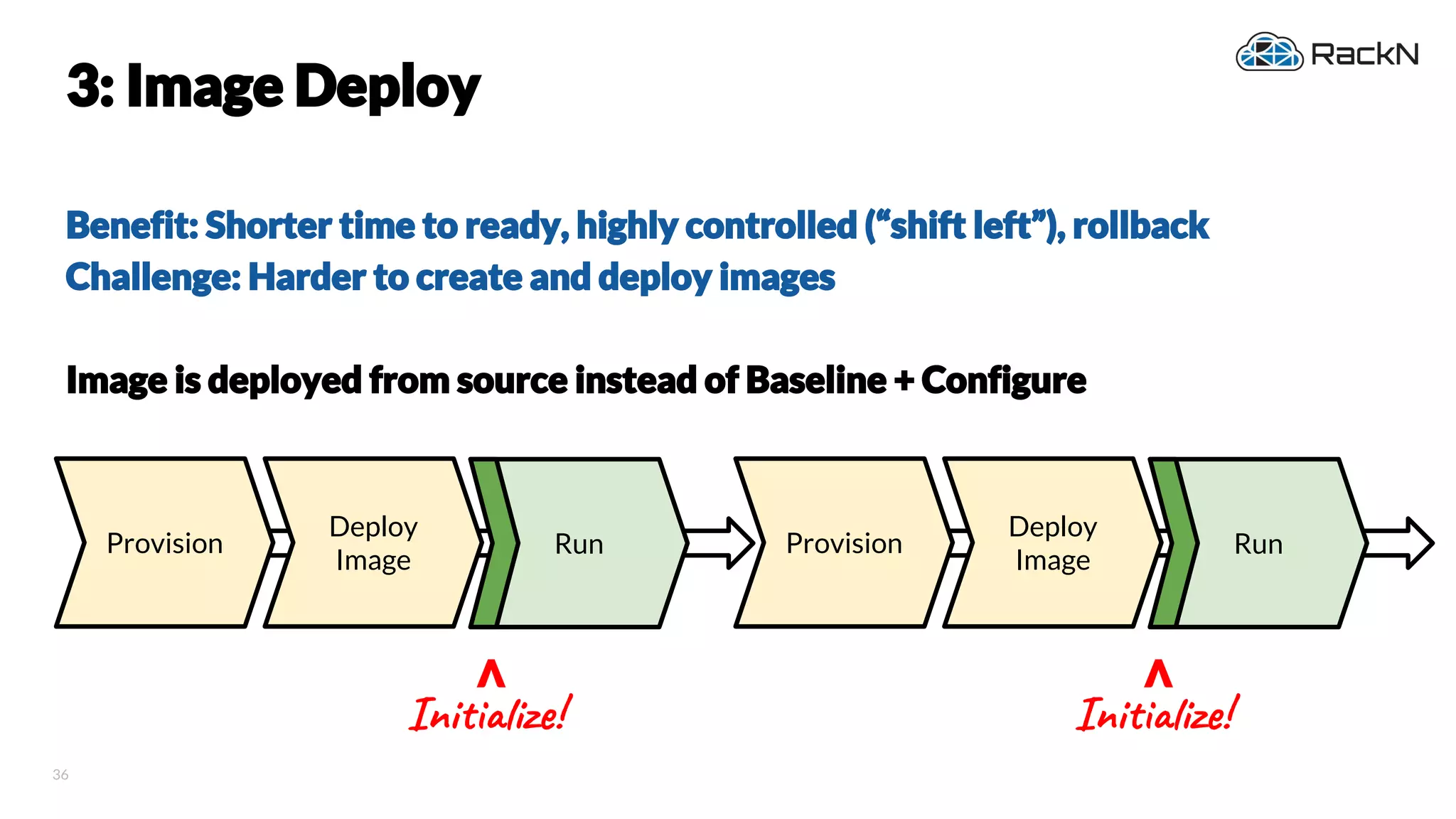
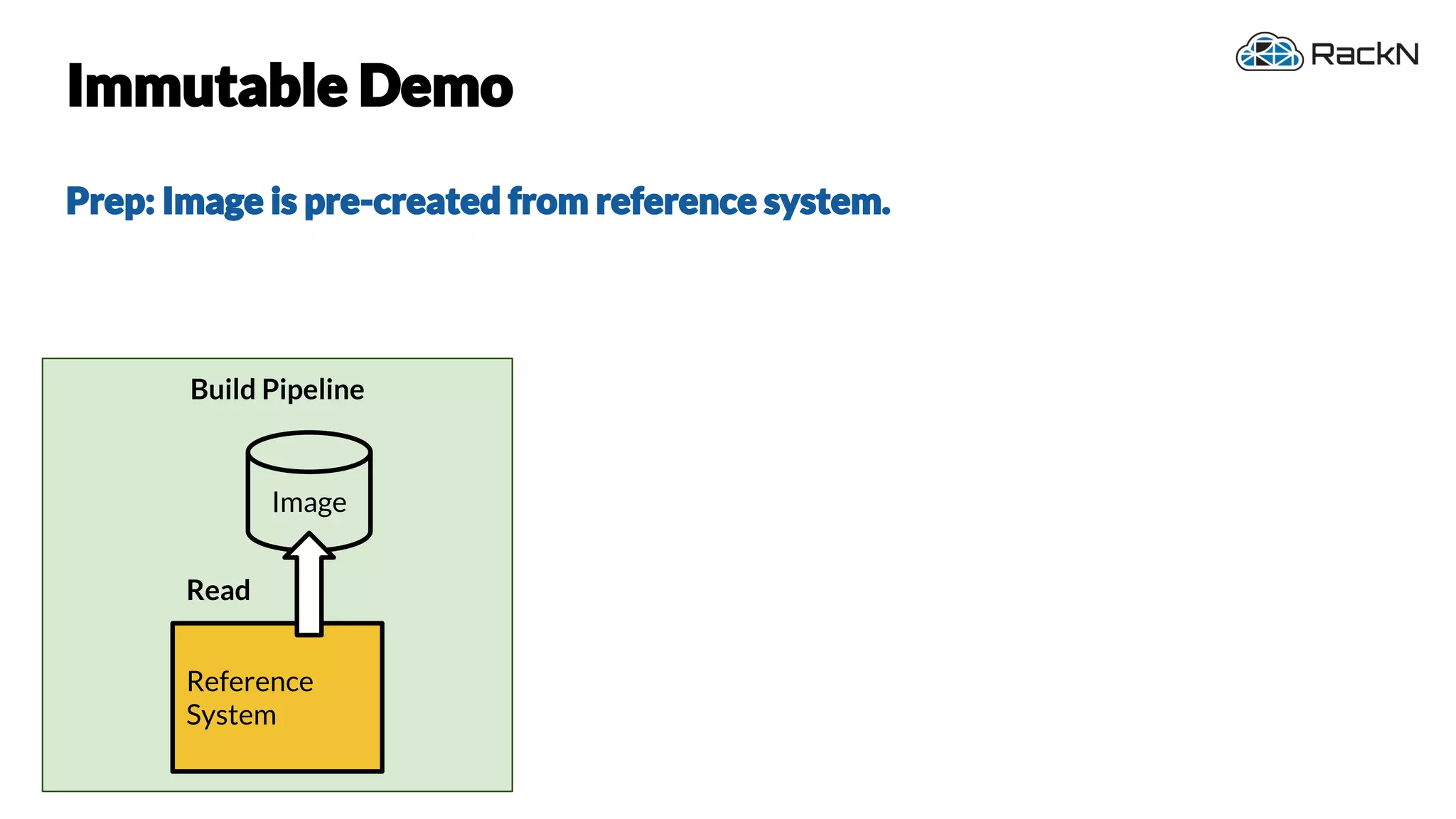
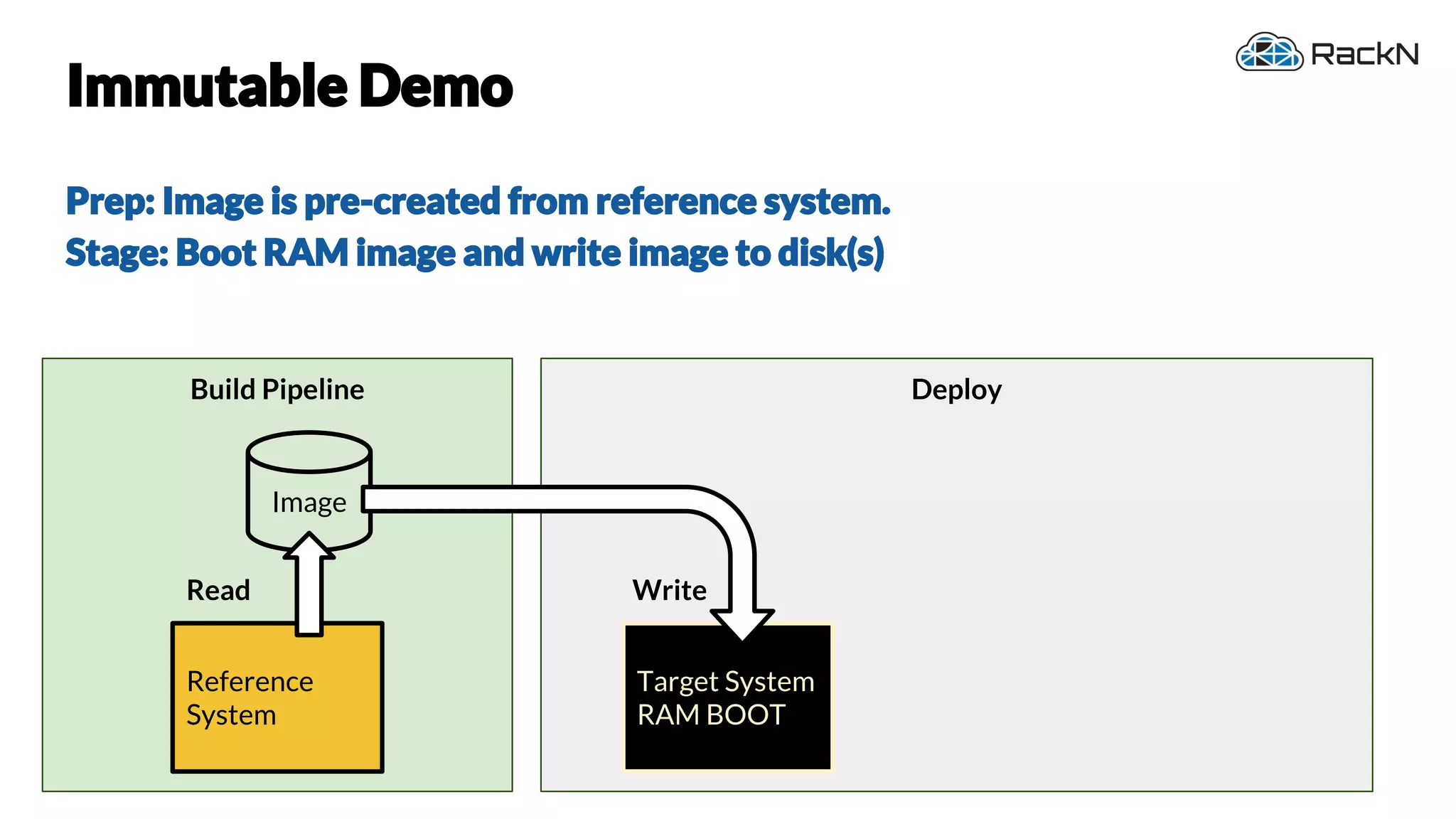
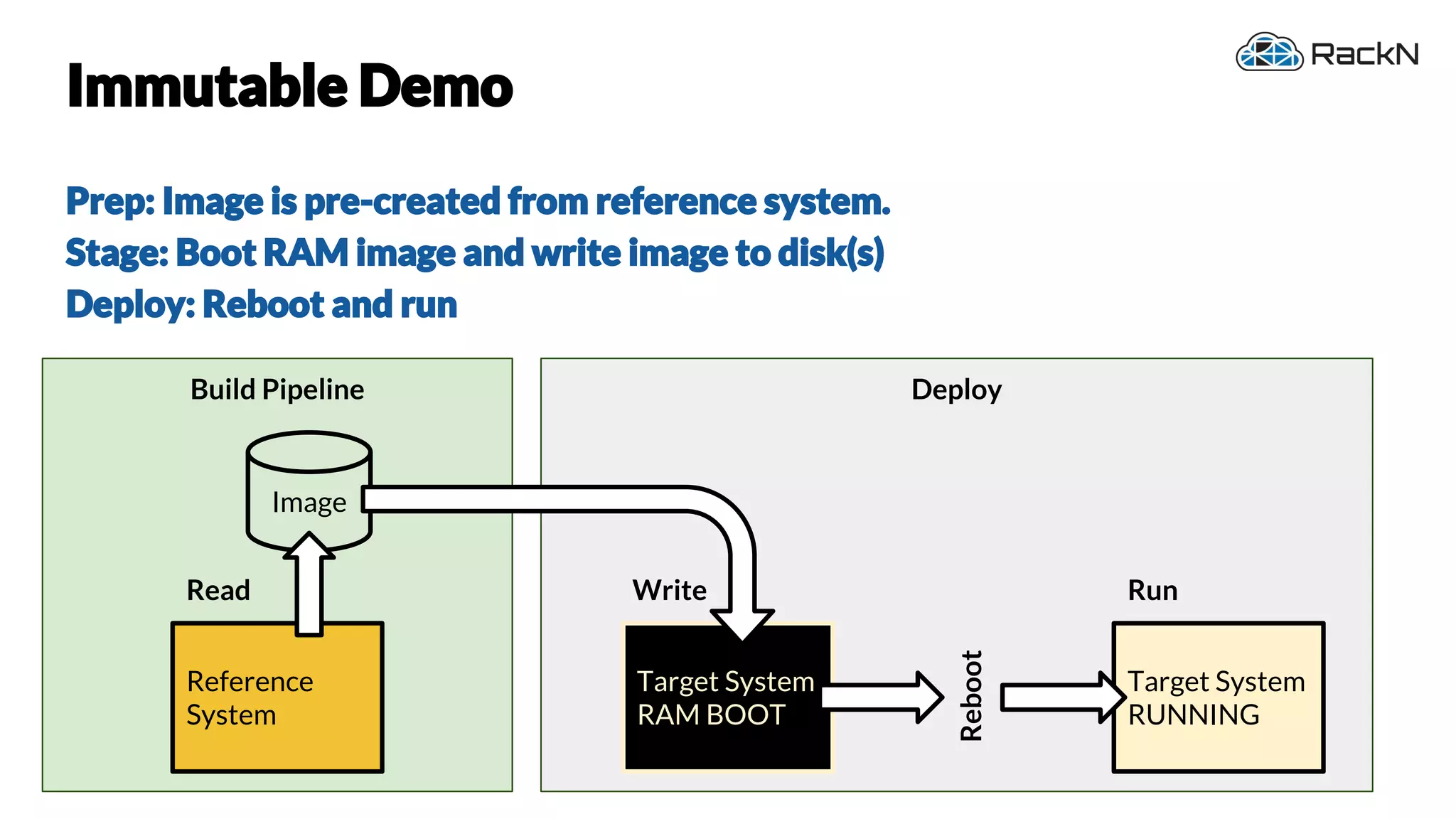
The document discusses the concept of immutable infrastructure and the challenges of configuration management in traditional deployment processes. It emphasizes the shift towards immutable designs that enable faster, safer, and more scalable operations by treating infrastructure as code and allowing platforms like Kubernetes to manage state. Additionally, it highlights different provisioning methodologies and the importance of image creation within automation build processes.