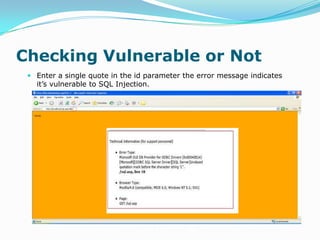
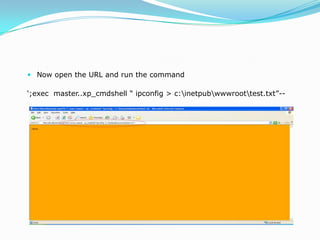
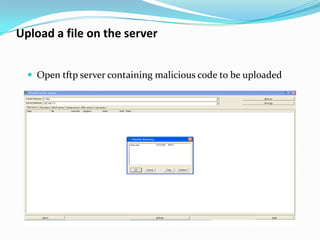
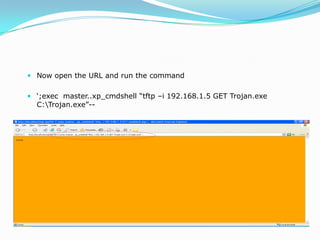
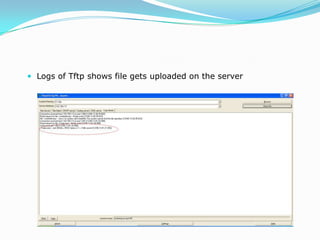
This document discusses advanced SQL injection techniques. It begins by defining SQL injection as injecting SQL commands into a database through an application. Many applications and programming languages are vulnerable if they use user input in SQL statements. Stored procedures like xp_cmdshell in Microsoft SQL Server allow executing operating system commands, which can be exploited. The document demonstrates SQL injection on a vulnerable ASP site connected to SQL Server 2000 to execute commands like ipconfig and upload a file via tftp.