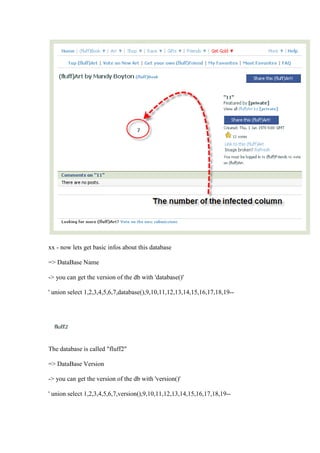
This document provides an introduction to exploiting SQL injection vulnerabilities. It explains how to determine the number of columns in a database, extract basic information like the database name, version, and user. It also demonstrates how to read the contents of tables and columns using the information_schema and how to load files from the server filesystem. The document concludes by noting that SQL injection vulnerabilities are common and important to prevent.
![Exploiting Web 2.0 , Real Life SQL I JECTIO
Author : AlpHaNiX
contact : AlpHa[AT]Hacker[DOT]BZ
HomePage : NullArea.Net
-----------------------------------------------
–= summary =–
0x000 - NULL
0x001 - Introduction
0x010 - Global Exploiting
0x011 - Exploiting The Bug
0x101 - Conclusion
0x110 - HelpFull links
------------------------------------------------------
0x001 - Introduction :
SQL Injection is a technique allow you to exploit
a web vulnerablity to extract content of the database
and show it for the injector thanks to an error while the
request ....
------------------------------------------------------
0x010 - Global Exploiting :
Exploiting The SQL Injection Vulnerabilty
To Exploit This Vulnerabilty You Got to have the following
conditions :
1- Null the querry
2- Get The Number of columns
-> To null the querry its enough to add something that doesnt](https://image.slidesharecdn.com/sqlinjection-151123131605-lva1-app6891/75/Sql-injection-1-2048.jpg)