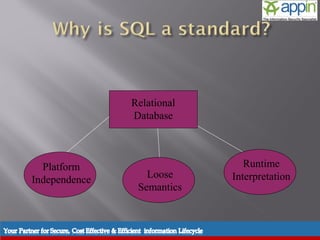
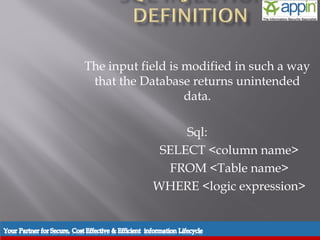
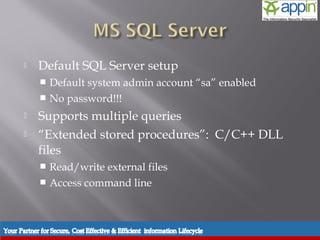
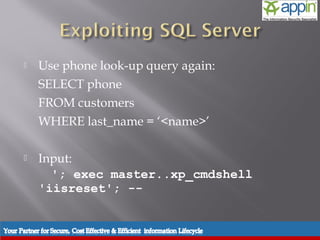
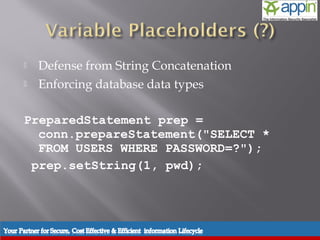
The document discusses SQL injection, including background, techniques used in attacks, prevention methods, and includes a demonstration. It describes how SQL injection works by modifying SQL queries in a way that returns unintended data. It provides examples of different types of SQL injection attacks and techniques used by attackers. It also outlines various prevention methods that can be used, including input validation, prepared statements, and limiting user privileges and access rights.















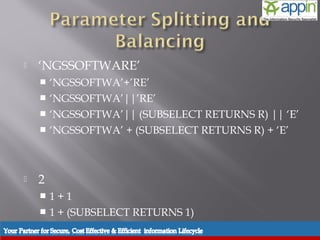
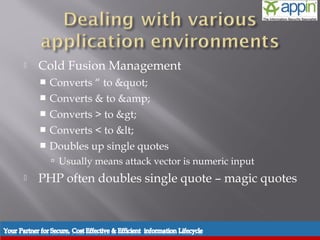
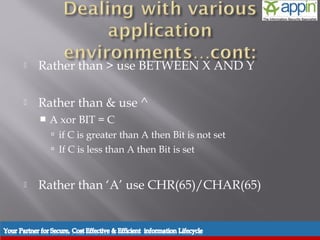









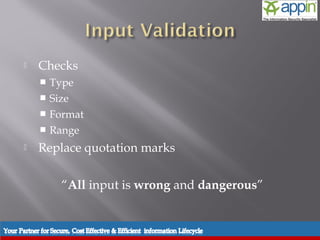
![ Built in character rejection
$sql = “SELECT * FROM Users WHERE ID =
‘” . $_GET[‘id’] . “’”;
$sql = “SELECT * FROM Users WHERE ID
=” .
mysql_real_escape_string($_GET[‘id’]);
$result = mysql_query($sql);
Introduction Background Techniques Prevention Demo Conclusions Questions](https://image.slidesharecdn.com/sql-121023085648-phpapp01/85/Sql-37-320.jpg)





![ UrlScan v3.0
restricts the types of HTTP requests that IIS will
process
[SQL Injection Headers]
AppliesTo=.asp,.aspx
[SQL Injection Headers Strings]
--
@ ; also catches @@
alter
delete
drop
exec
insert
alert tcp $EXTERNAL_NET any -> $HTTP_SERVERS $HTTP_PORTS
(msg:"SQL Injection "; flow:to_server,established;
uricontent:".php | .aspx | .asp";
pcre:"/(%27)|(')|(--)|(%23)|(#)/i";
classtype:Web-application-attack; sid:9099; rev:5;)
SNORT
Create rule to check for SQL attack](https://image.slidesharecdn.com/sql-121023085648-phpapp01/85/Sql-44-320.jpg)




