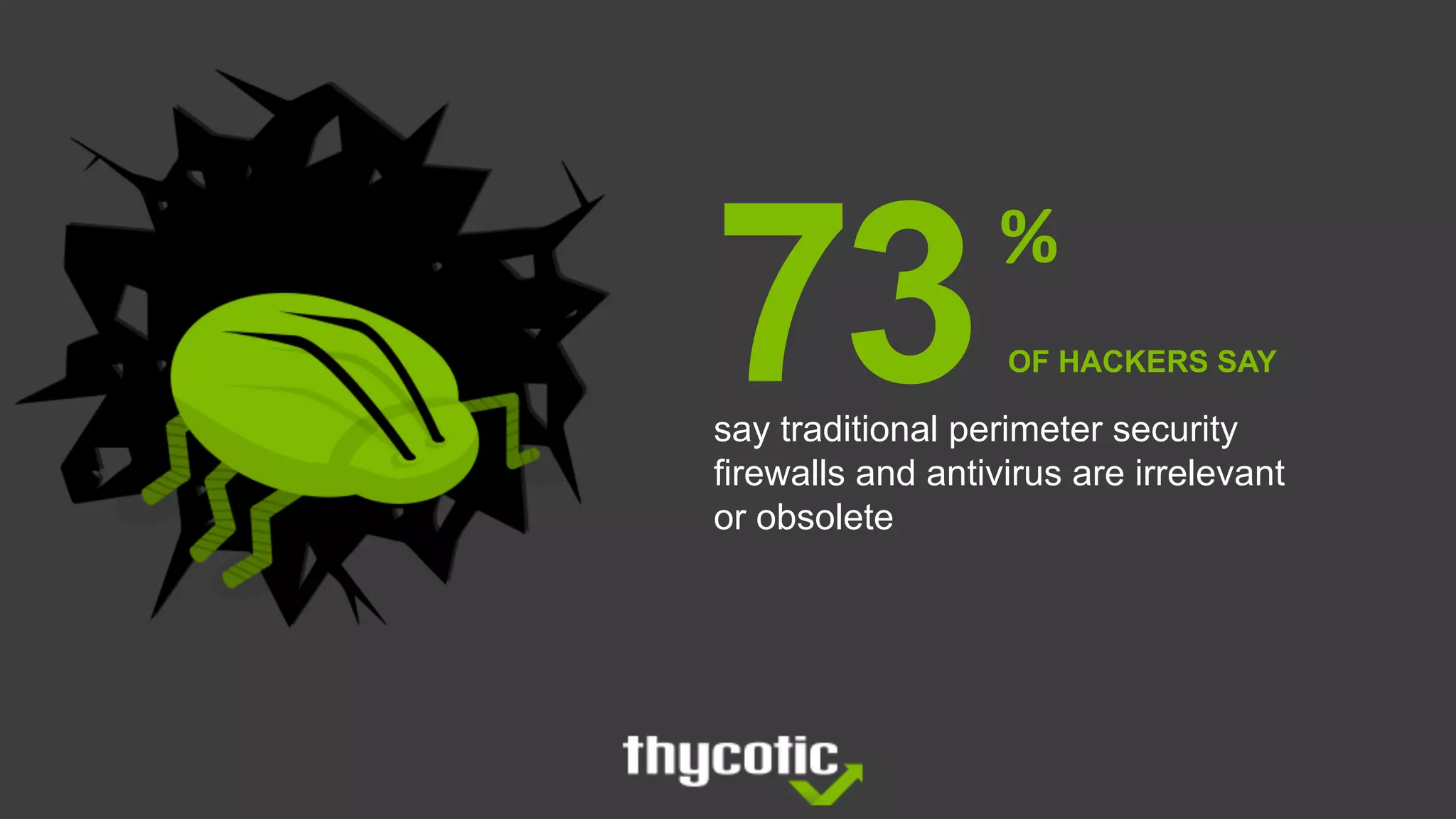
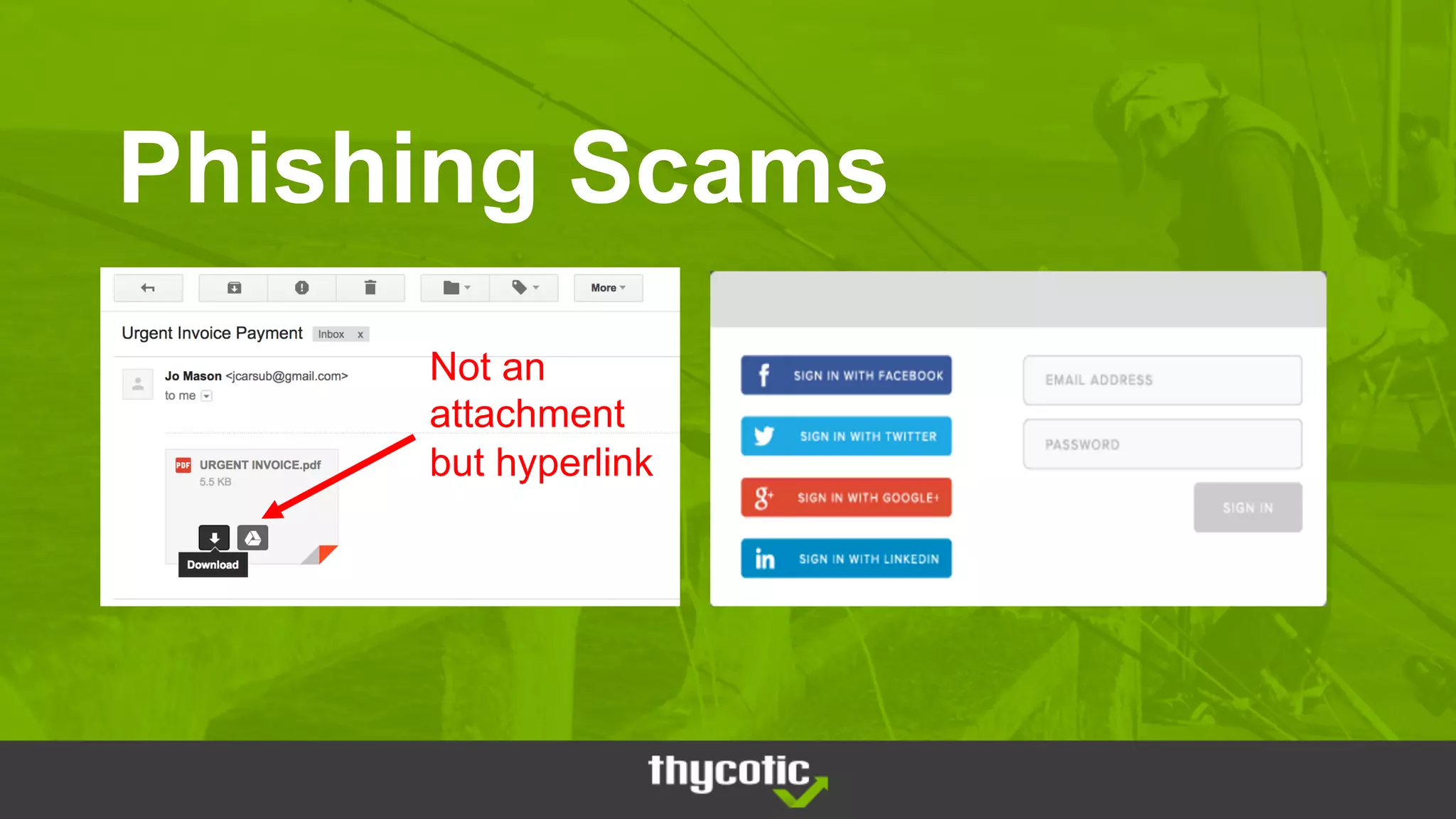
The document discusses insights from the Black Hat Conference 2018 regarding privileged access management (PAM) and cybersecurity vulnerabilities. It highlights that 50% of hackers successfully compromised Windows OS, primarily using social engineering and exploiting password re-use. Recommendations for enhancing defenses include adopting a zero trust posture, avoiding reliance solely on group policy for security, and applying the principle of least privilege.