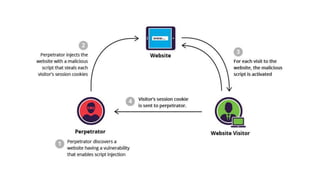
The document discusses various software security issues including insecure interaction between components like SQL injection and cross-site scripting (XSS). It also discusses risky resource management issues like buffer overflows. Additionally, it discusses porous defenses like missing authentication. The document emphasizes the importance of filtering all untrusted inputs and outputs to prevent attacks like XSS that could allow altering of user data or behavior. It provides recommendations for secure coding practices like prepared statements and output encoding to prevent attacks on programs that display external data.