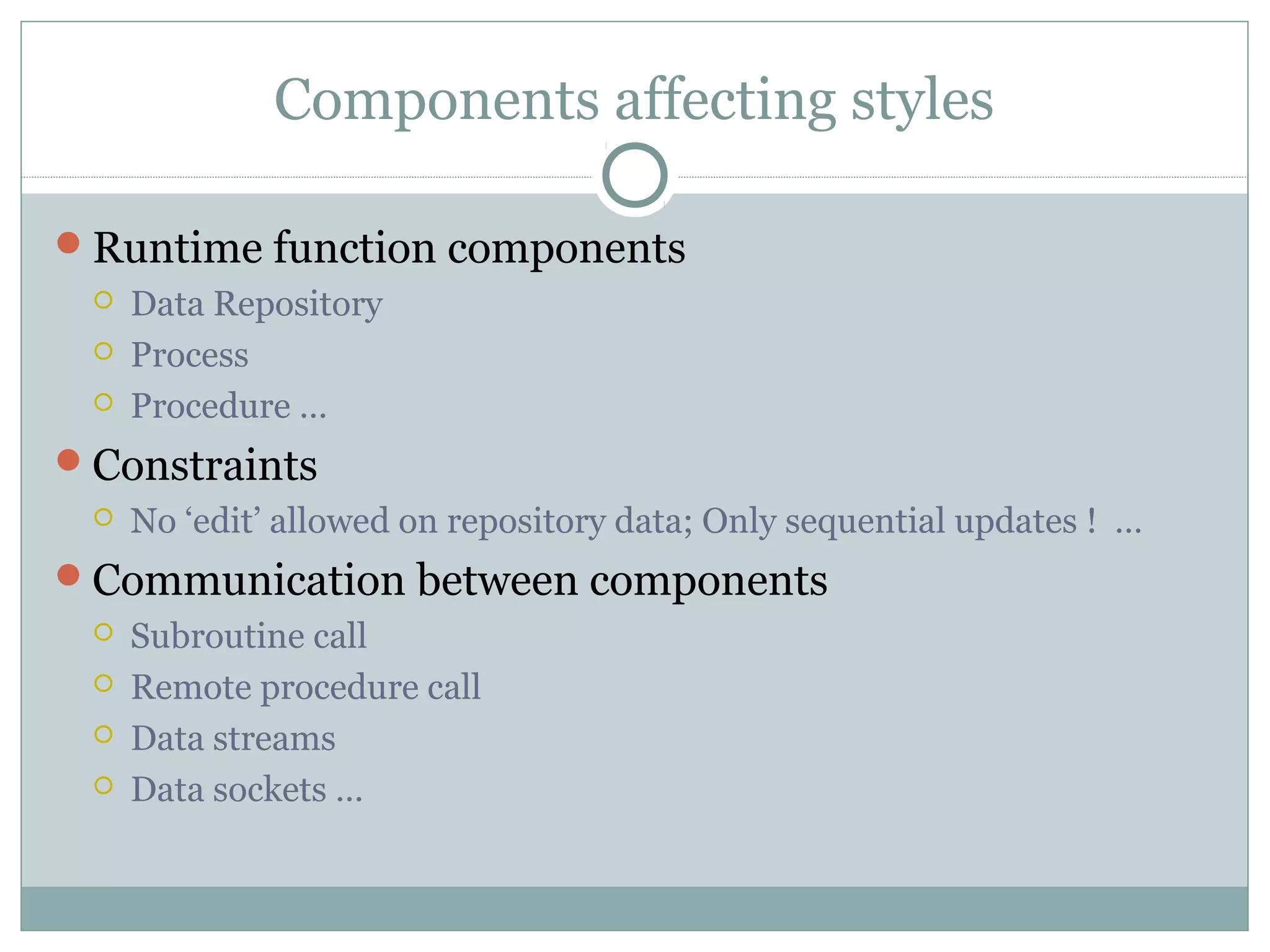
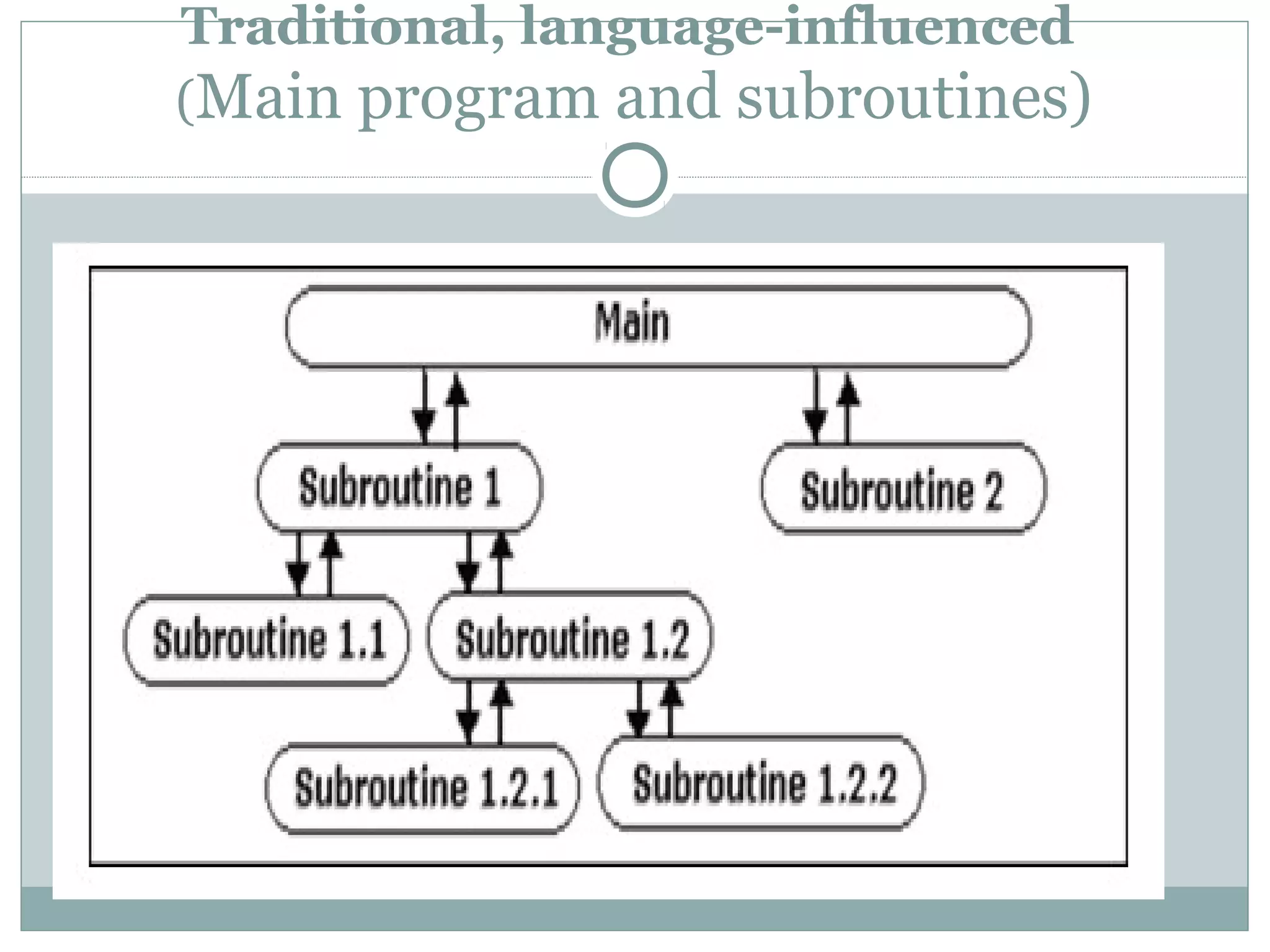
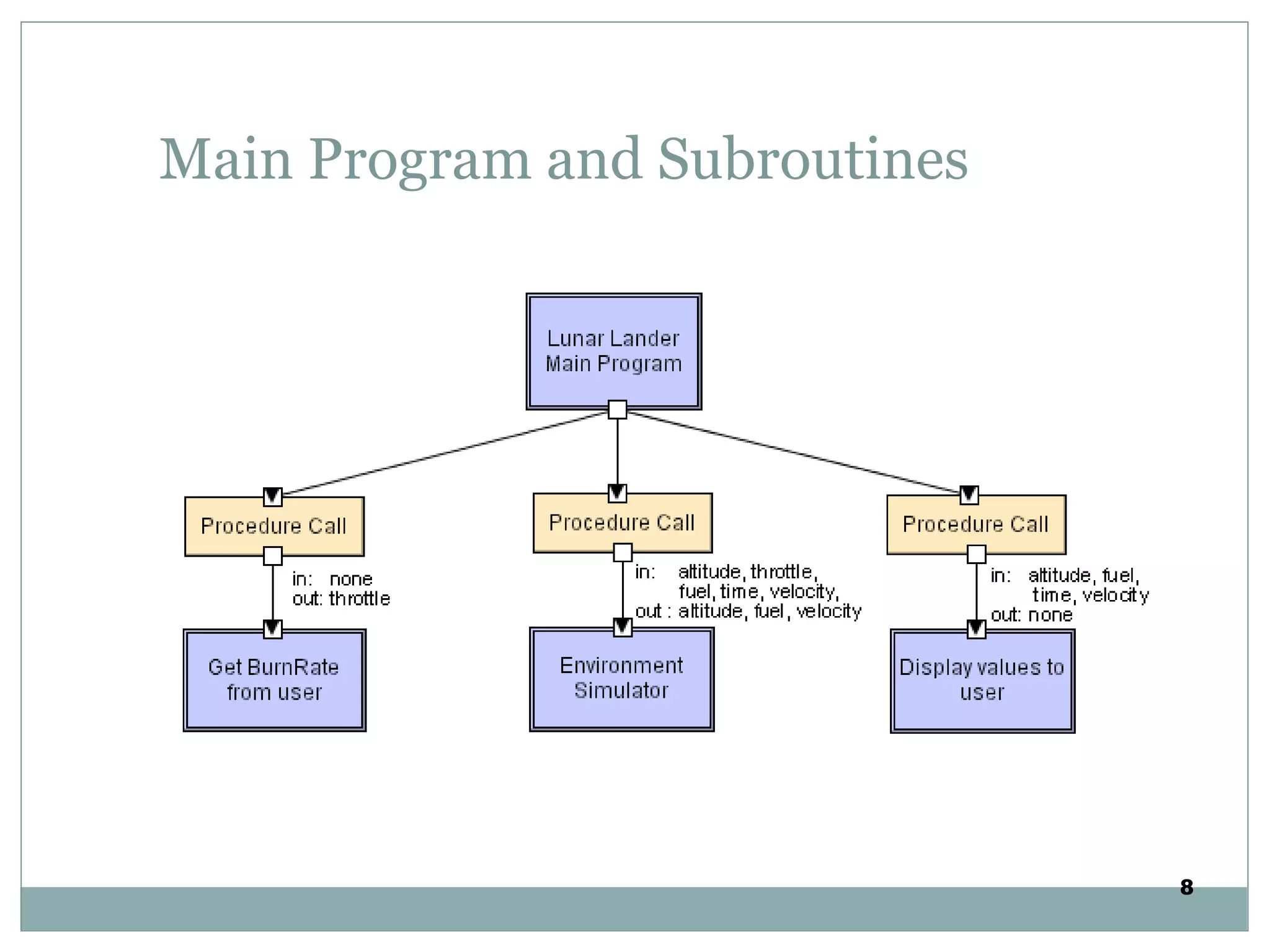
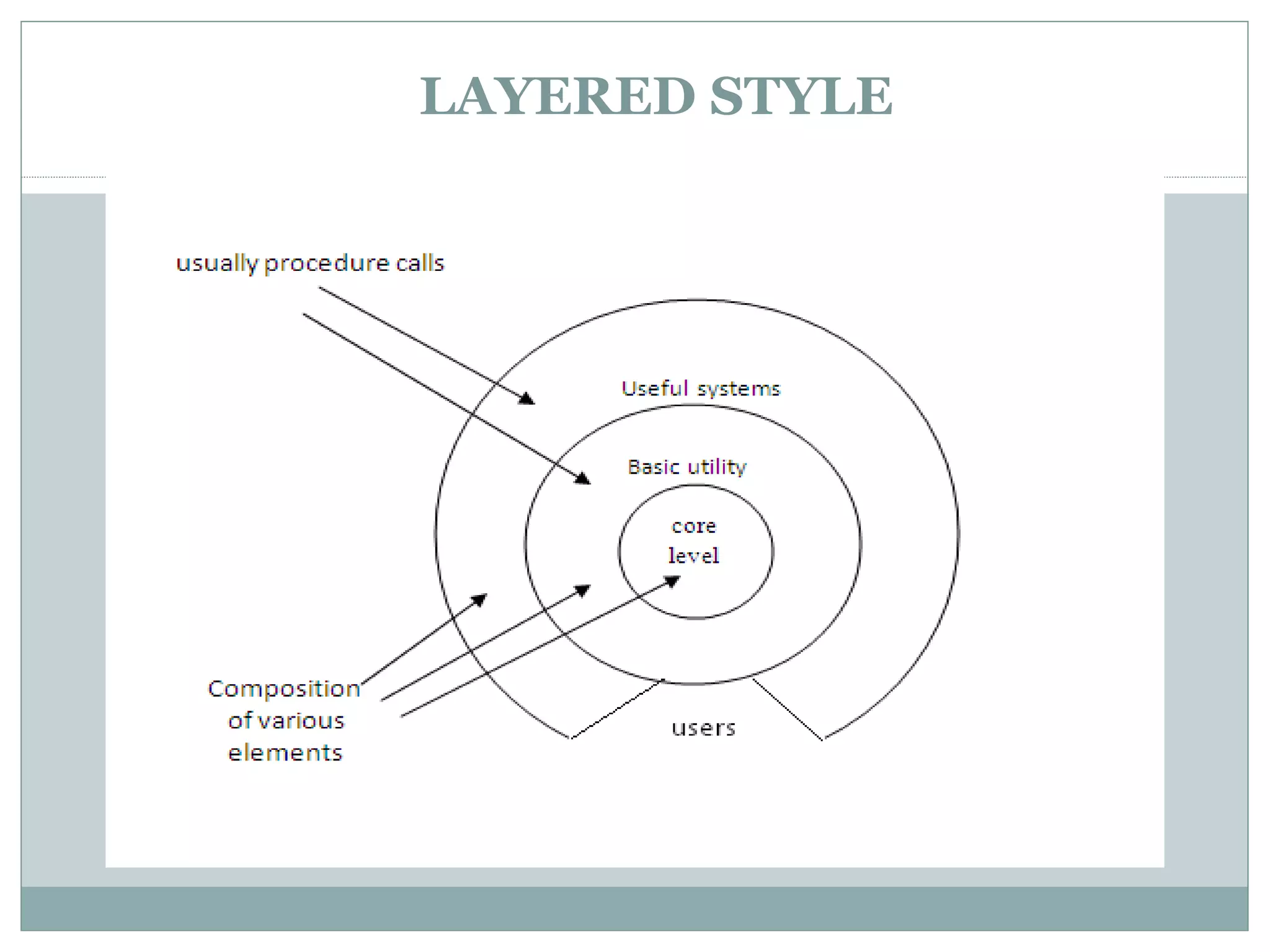
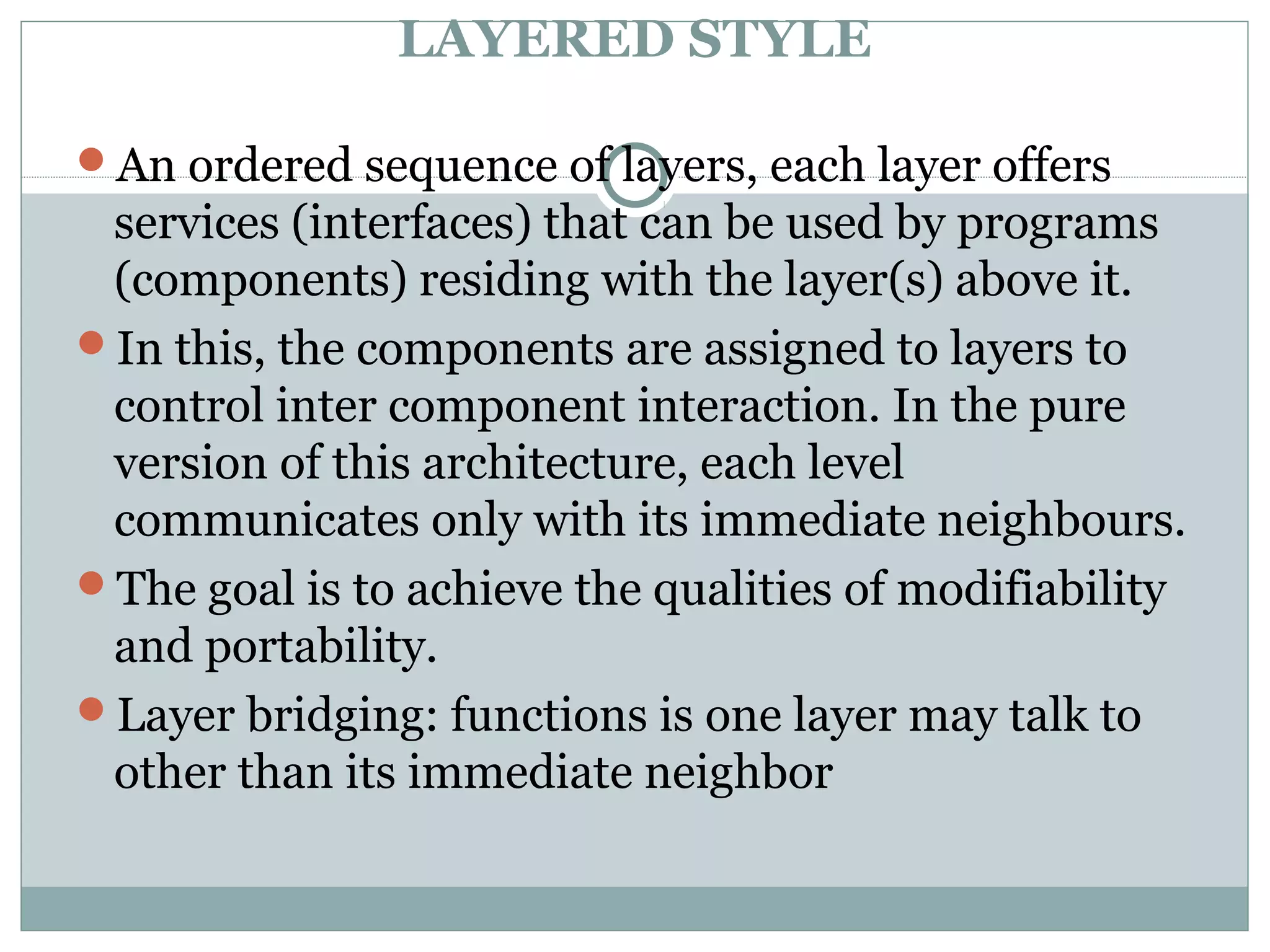
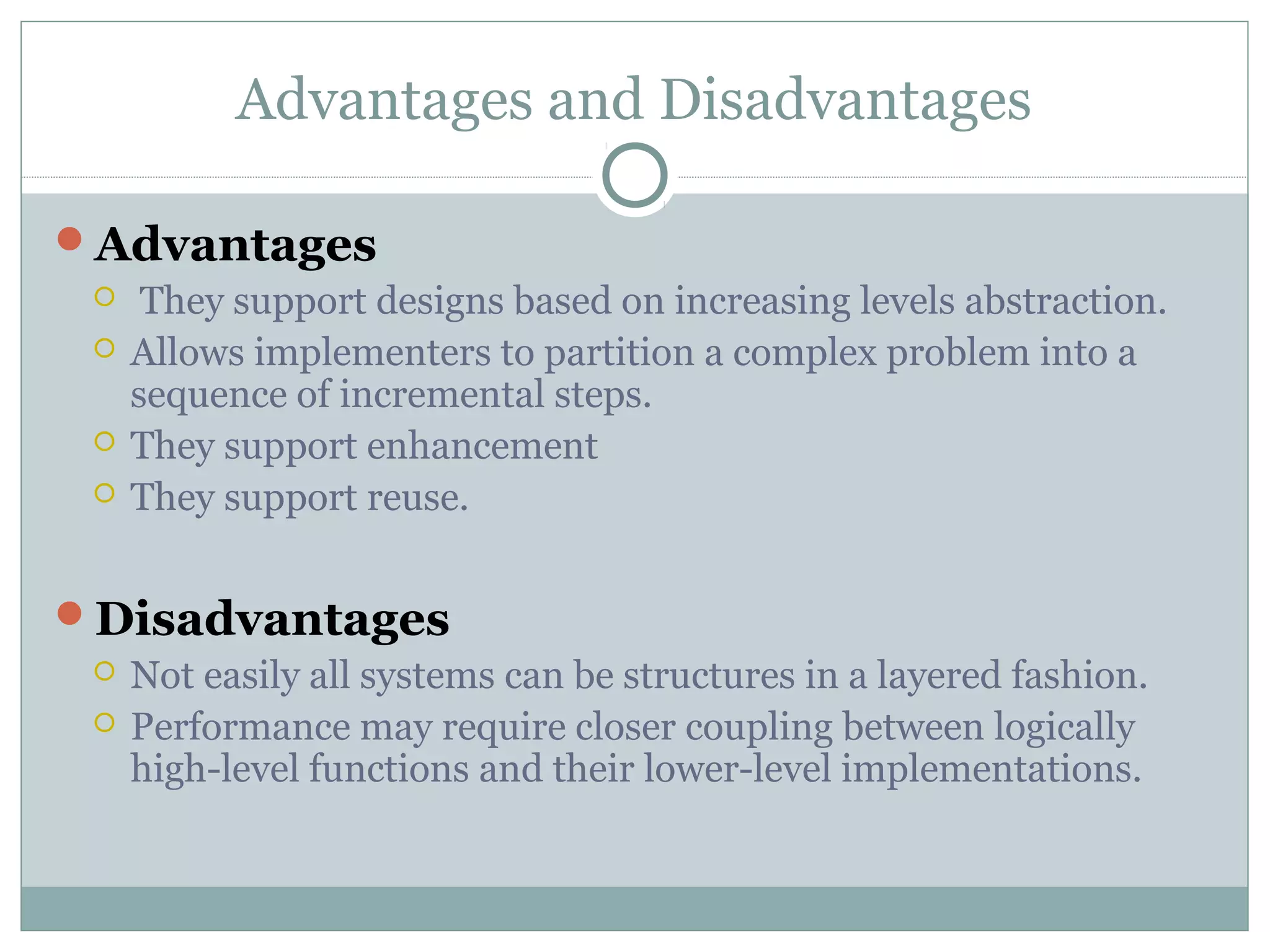
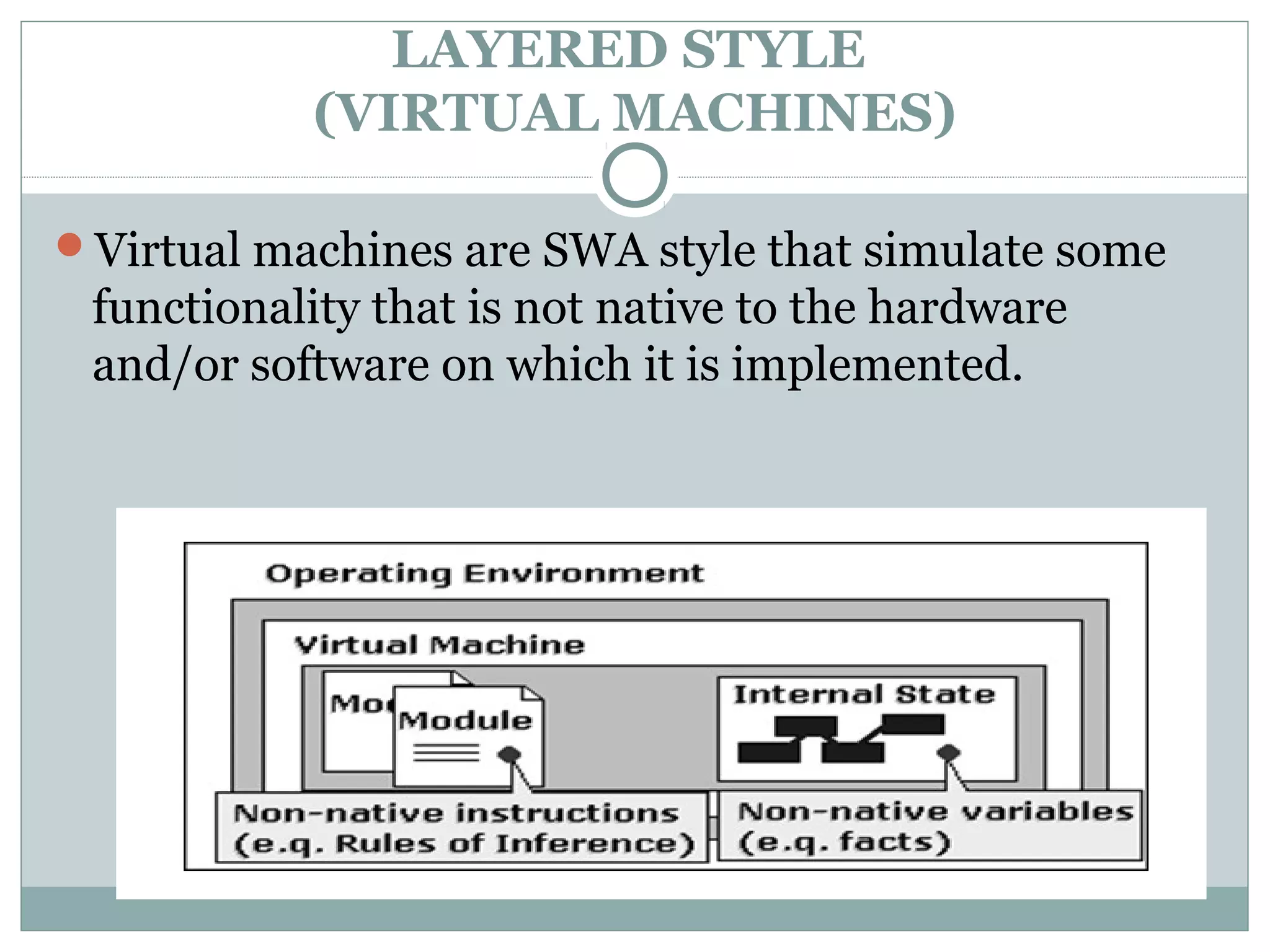
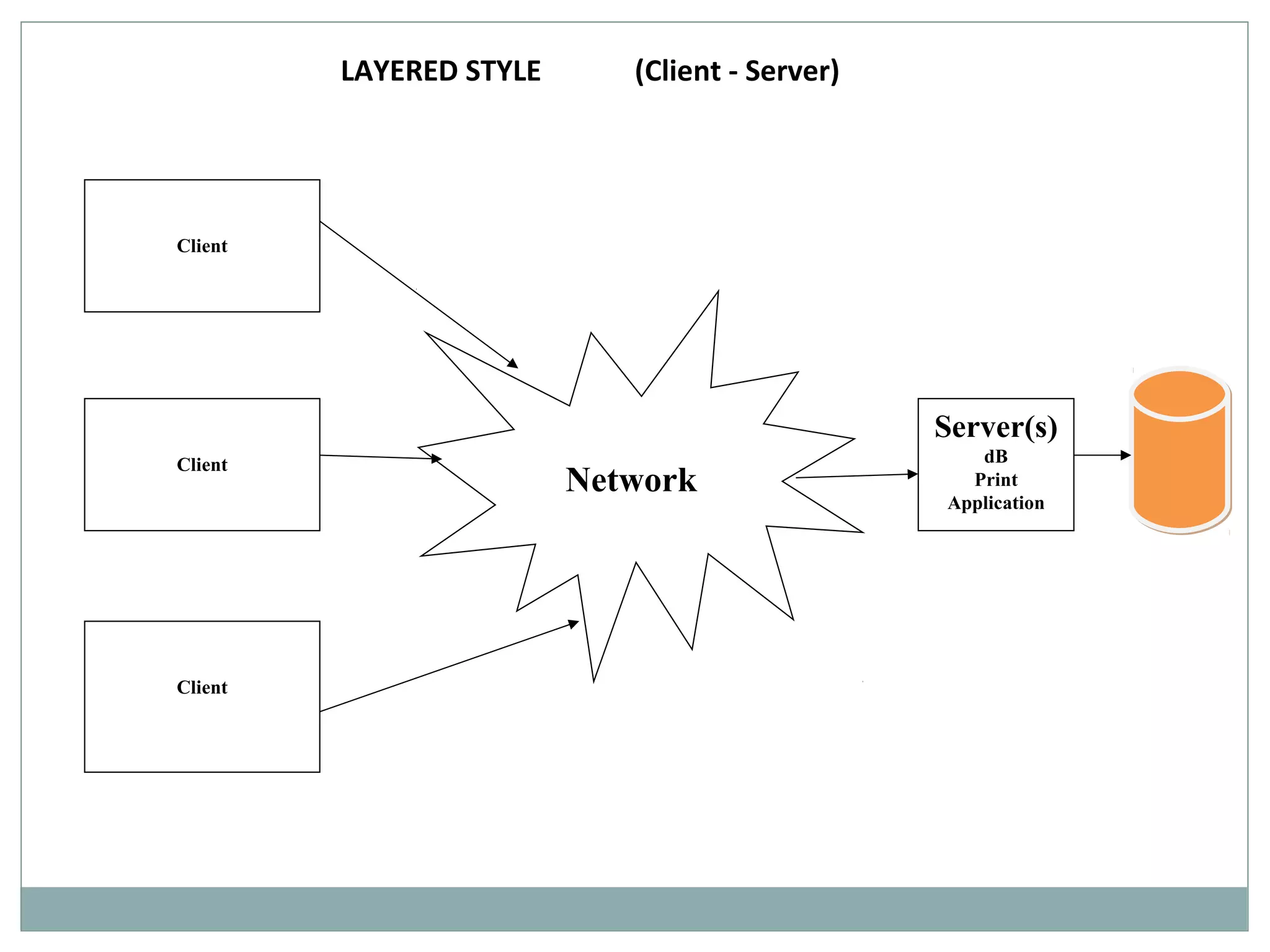
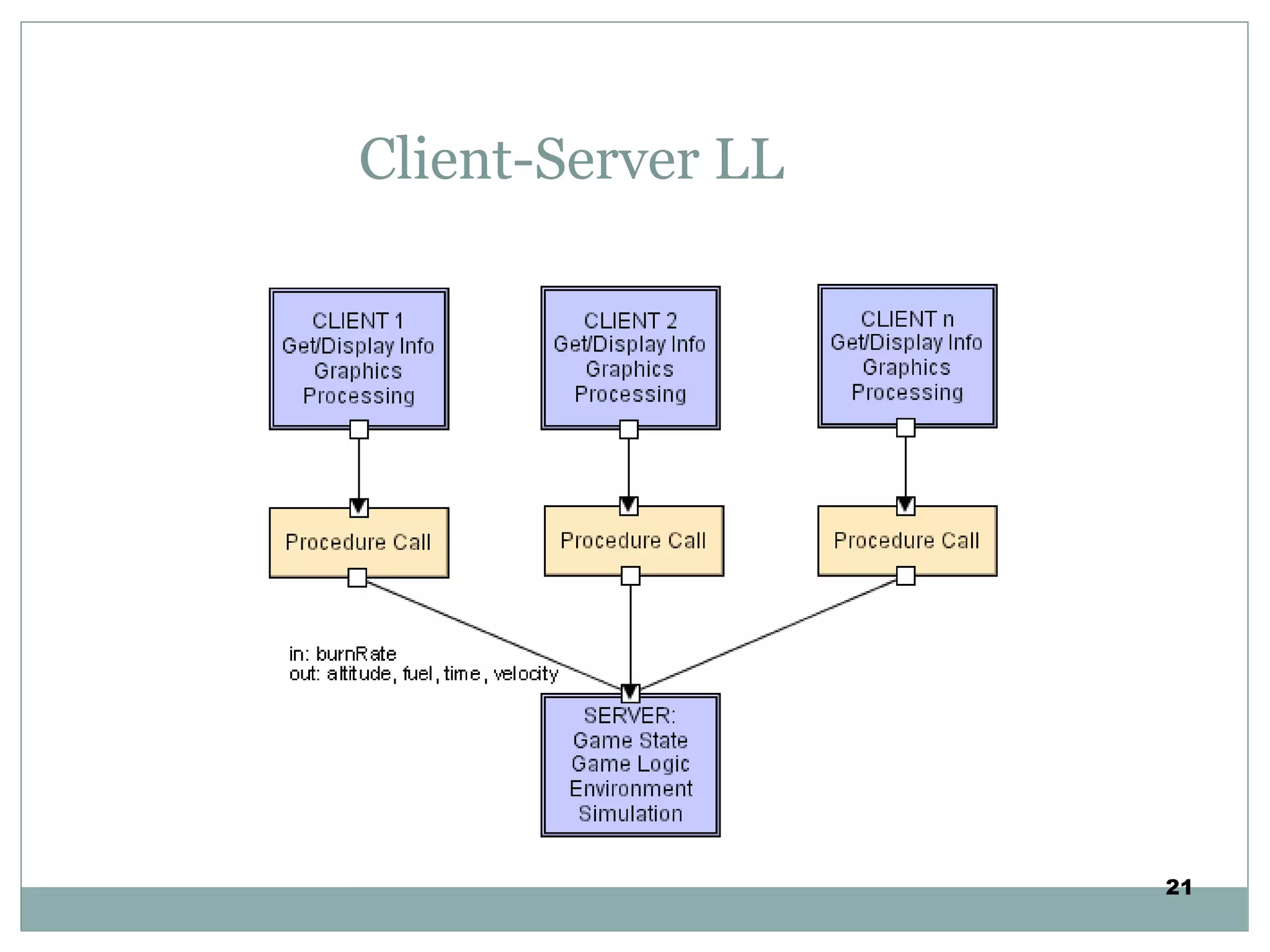
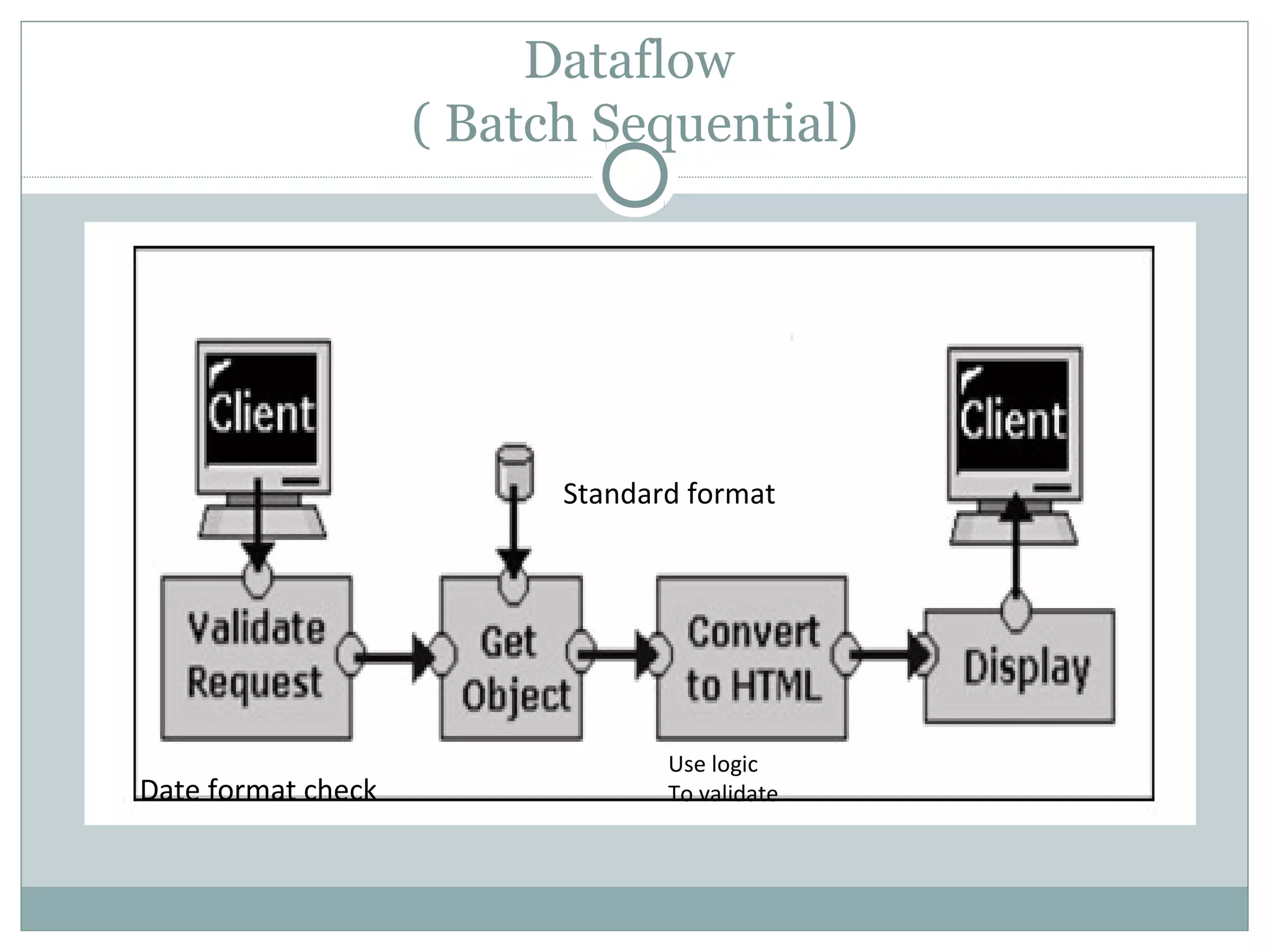
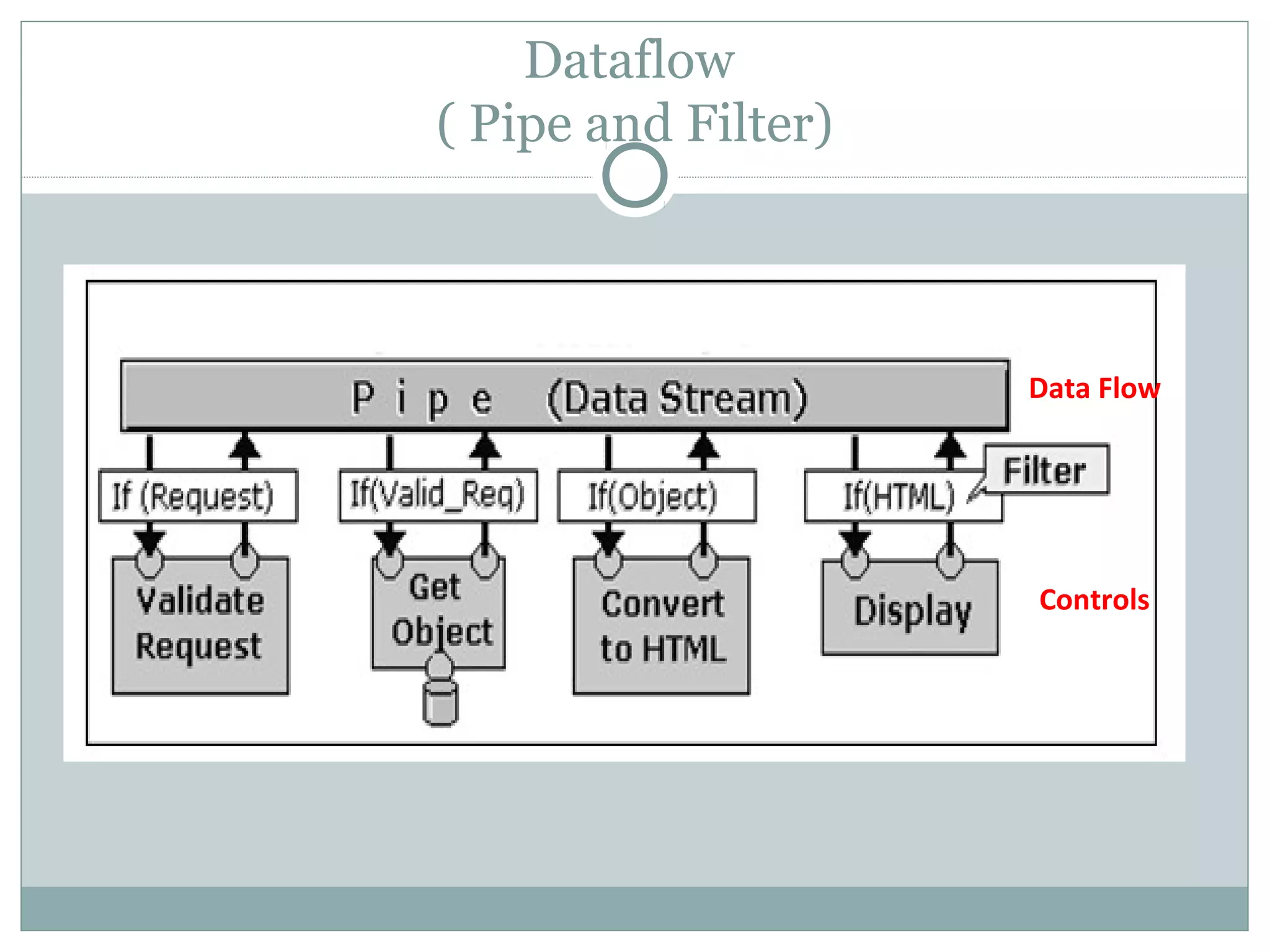
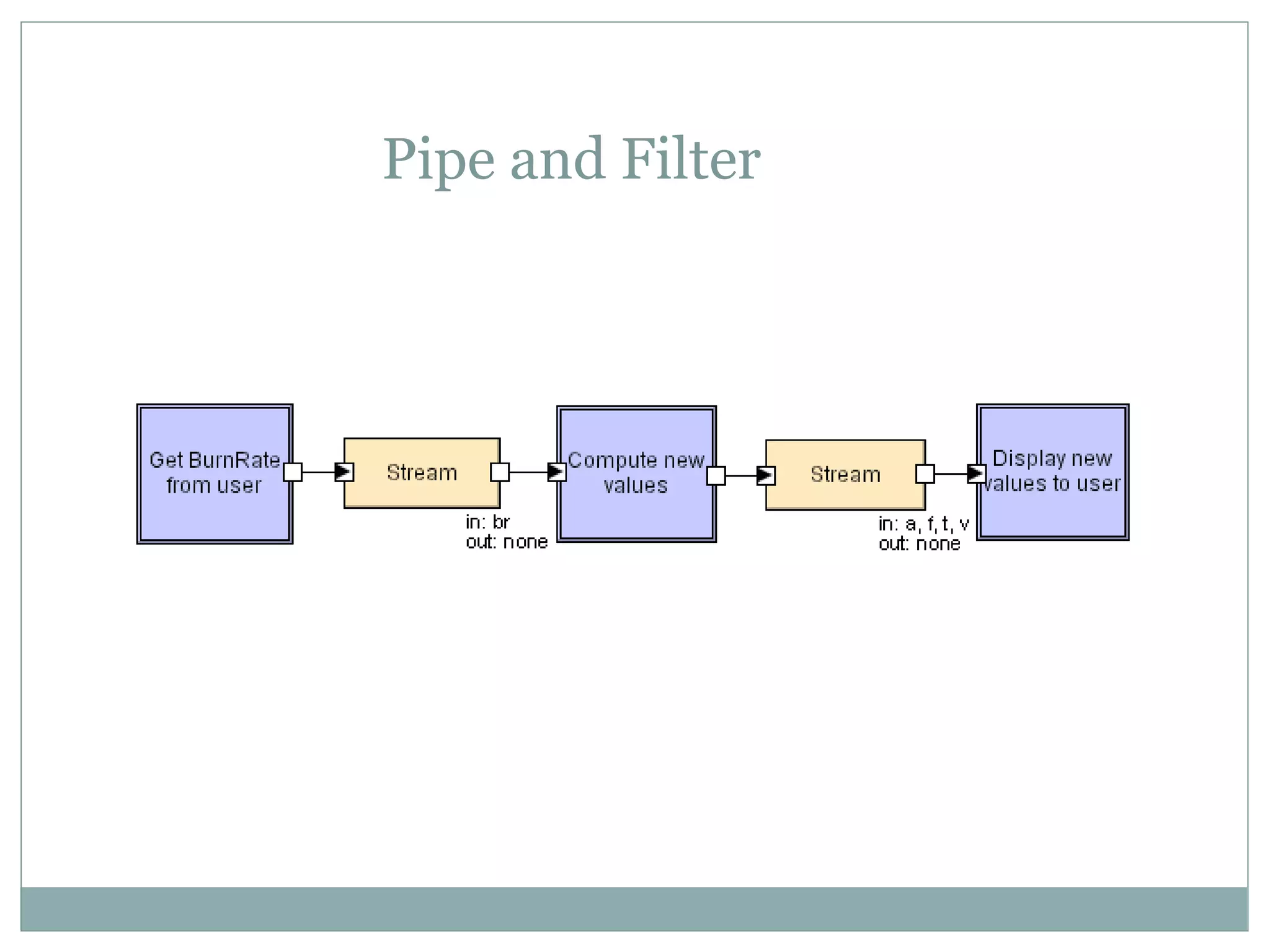
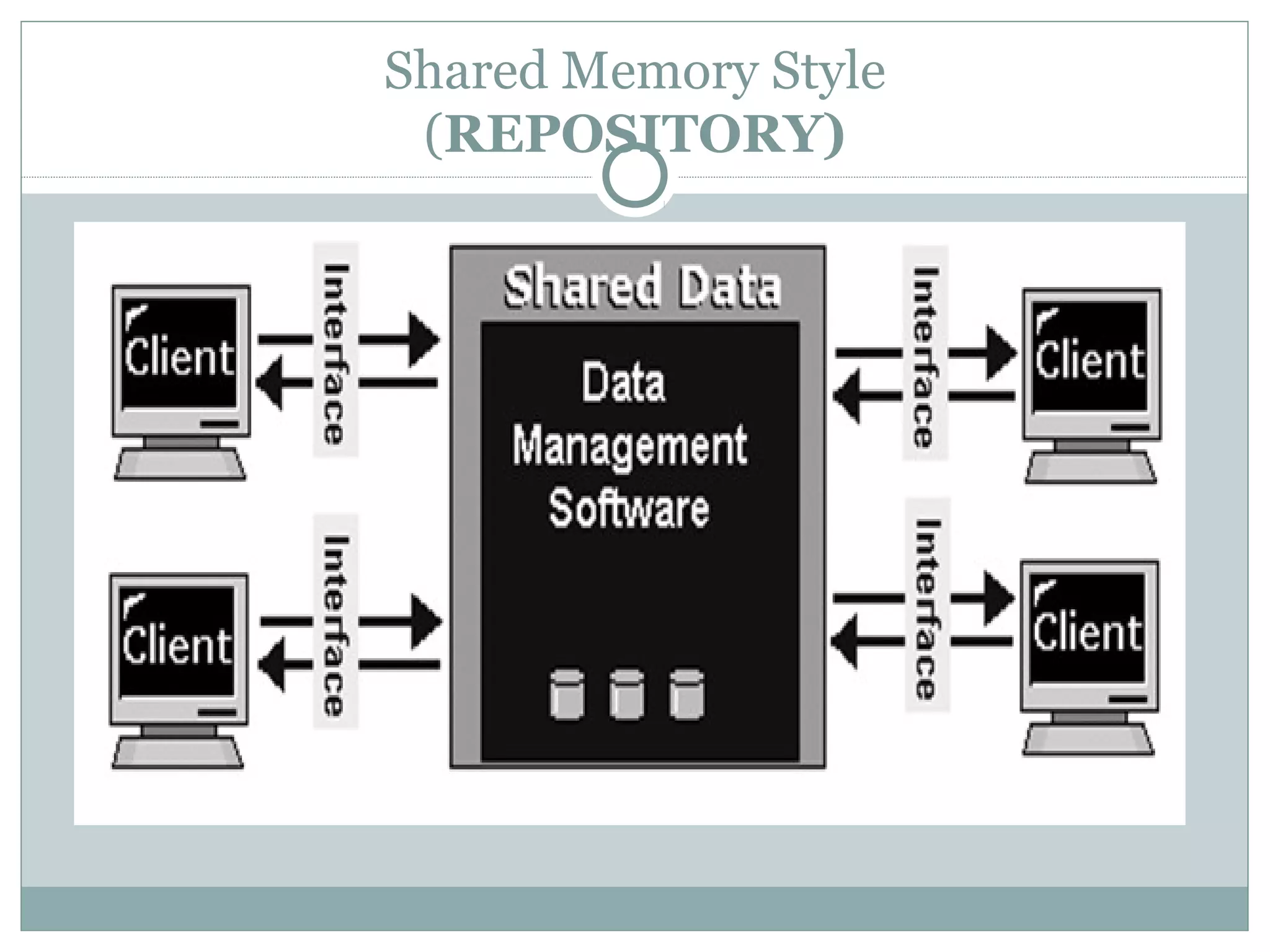
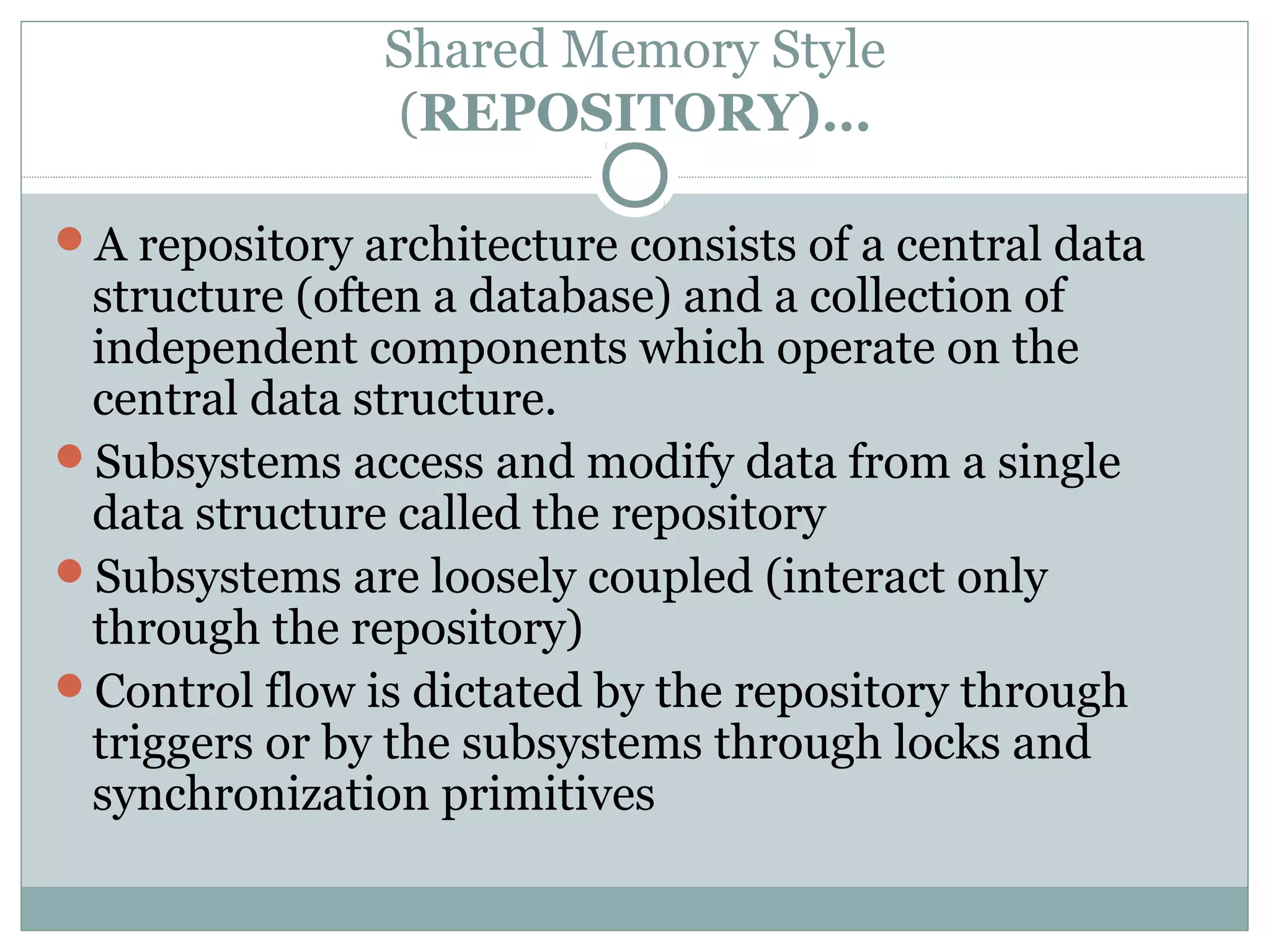
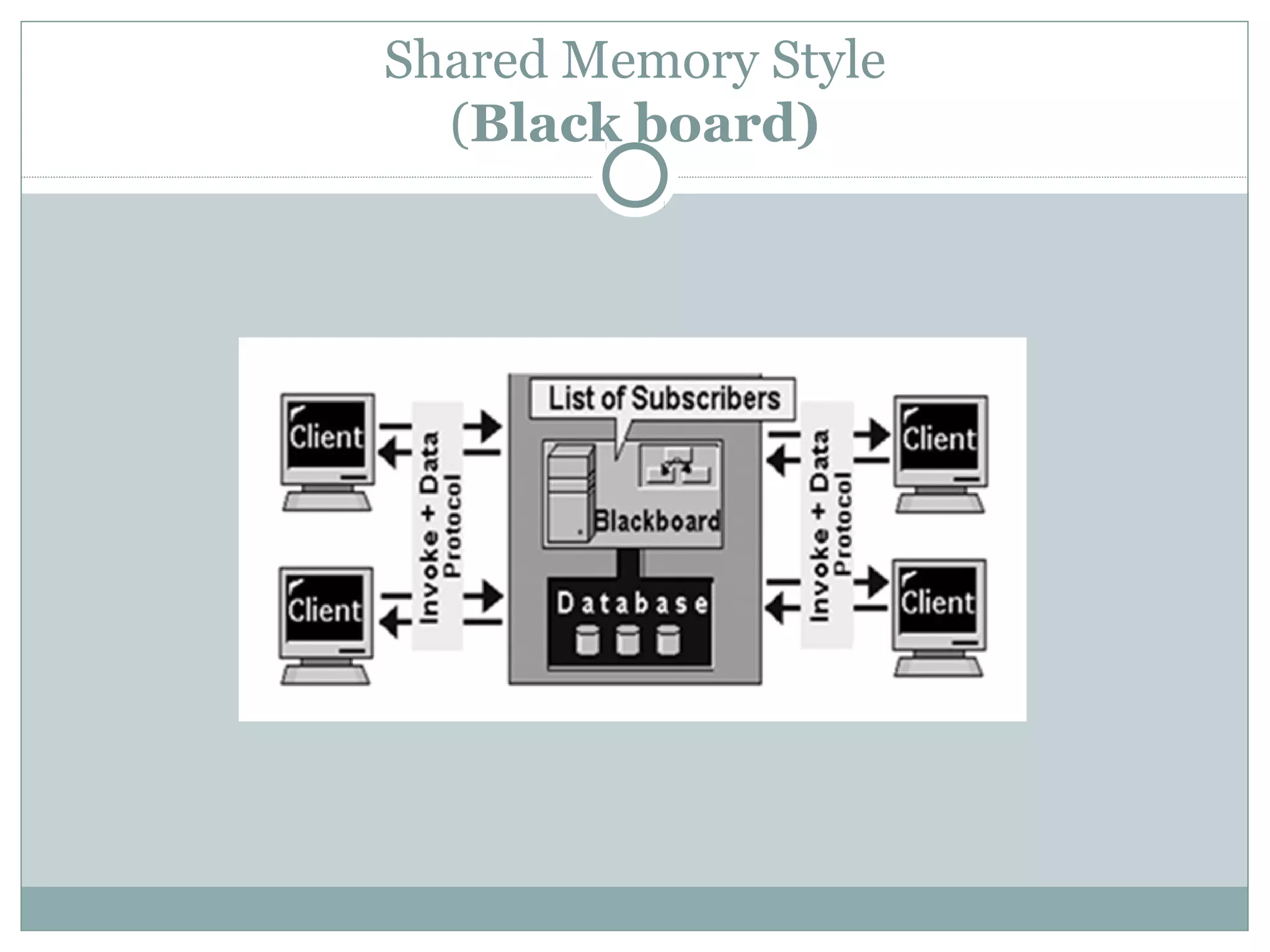
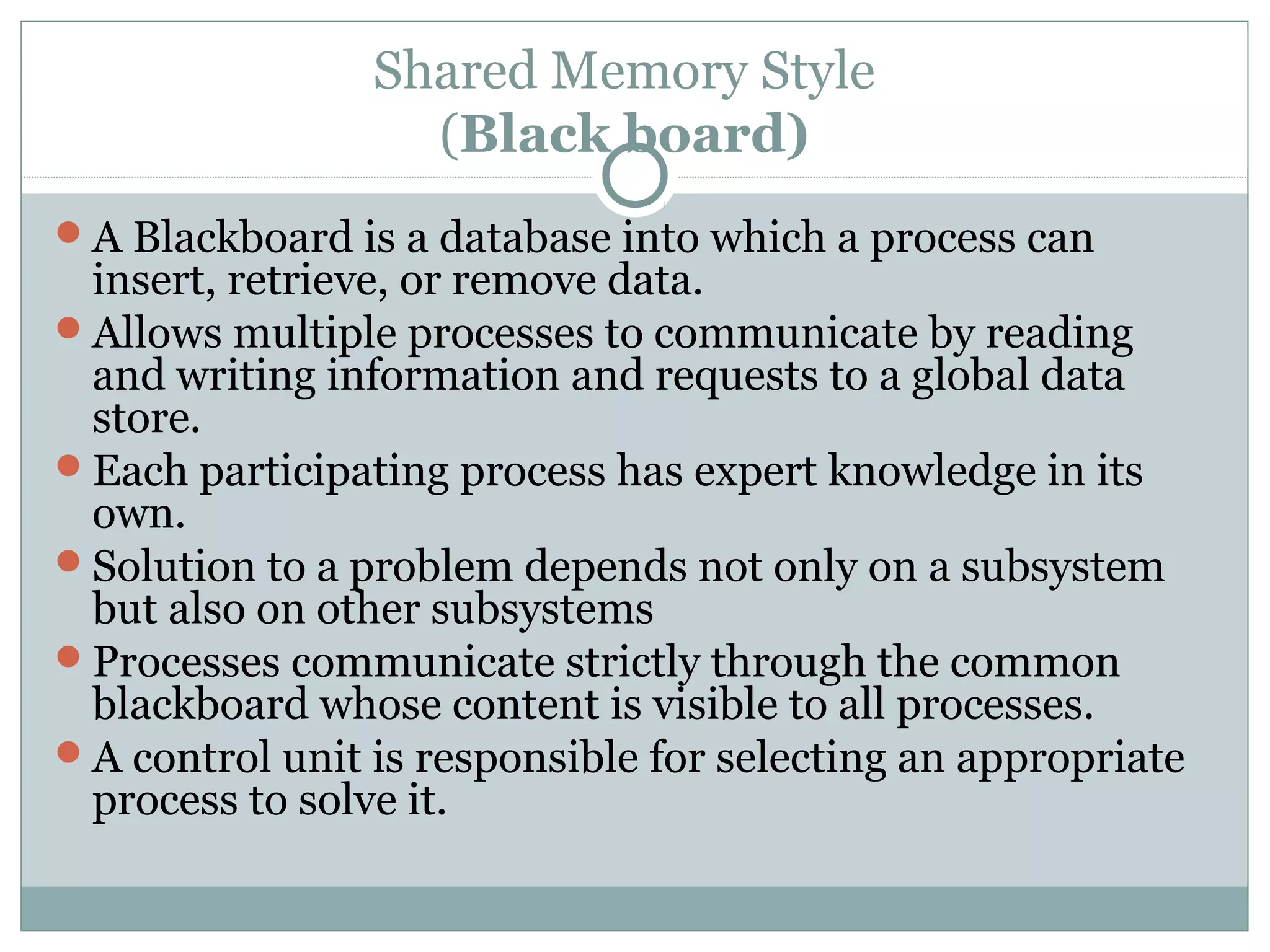
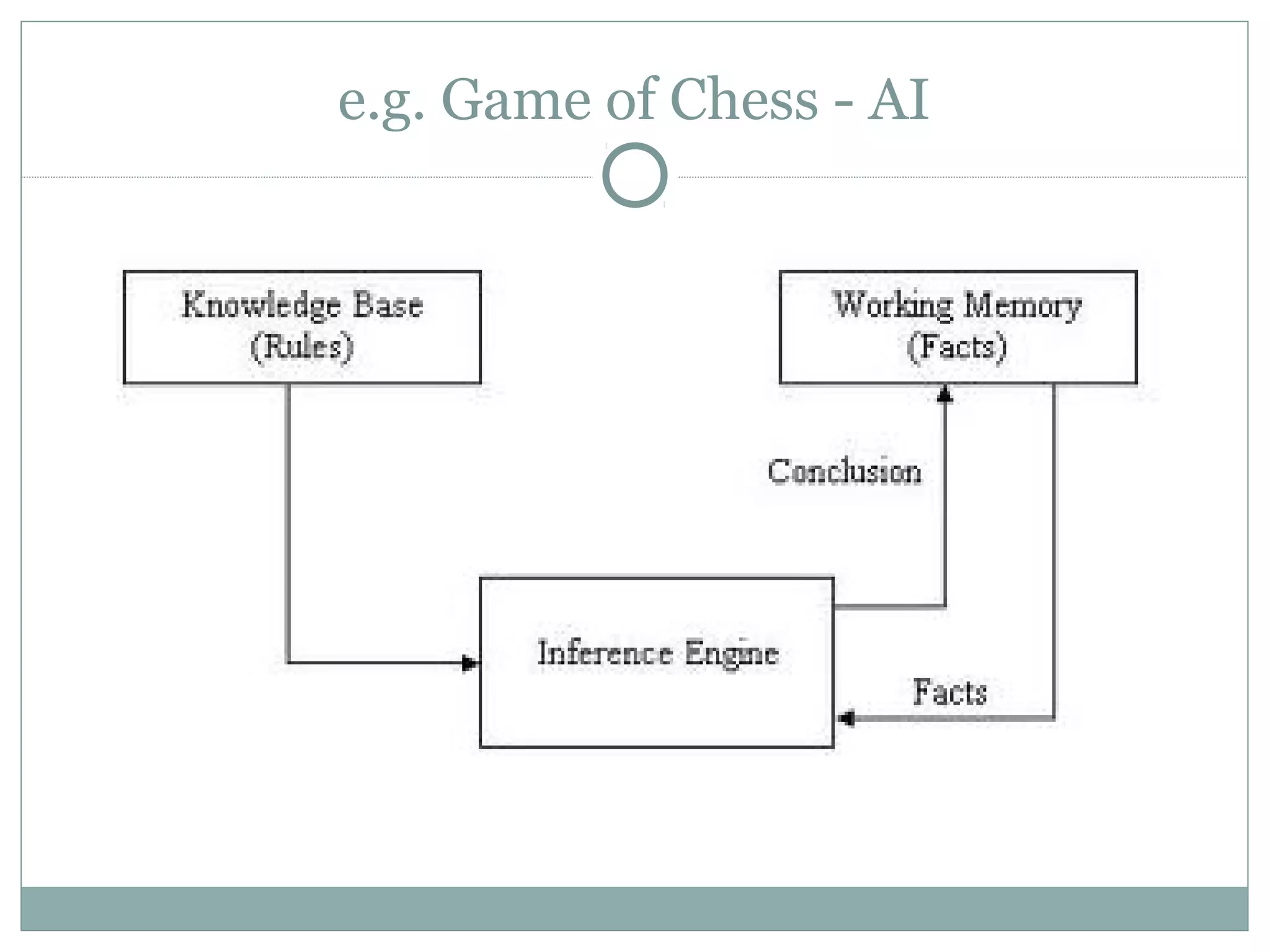
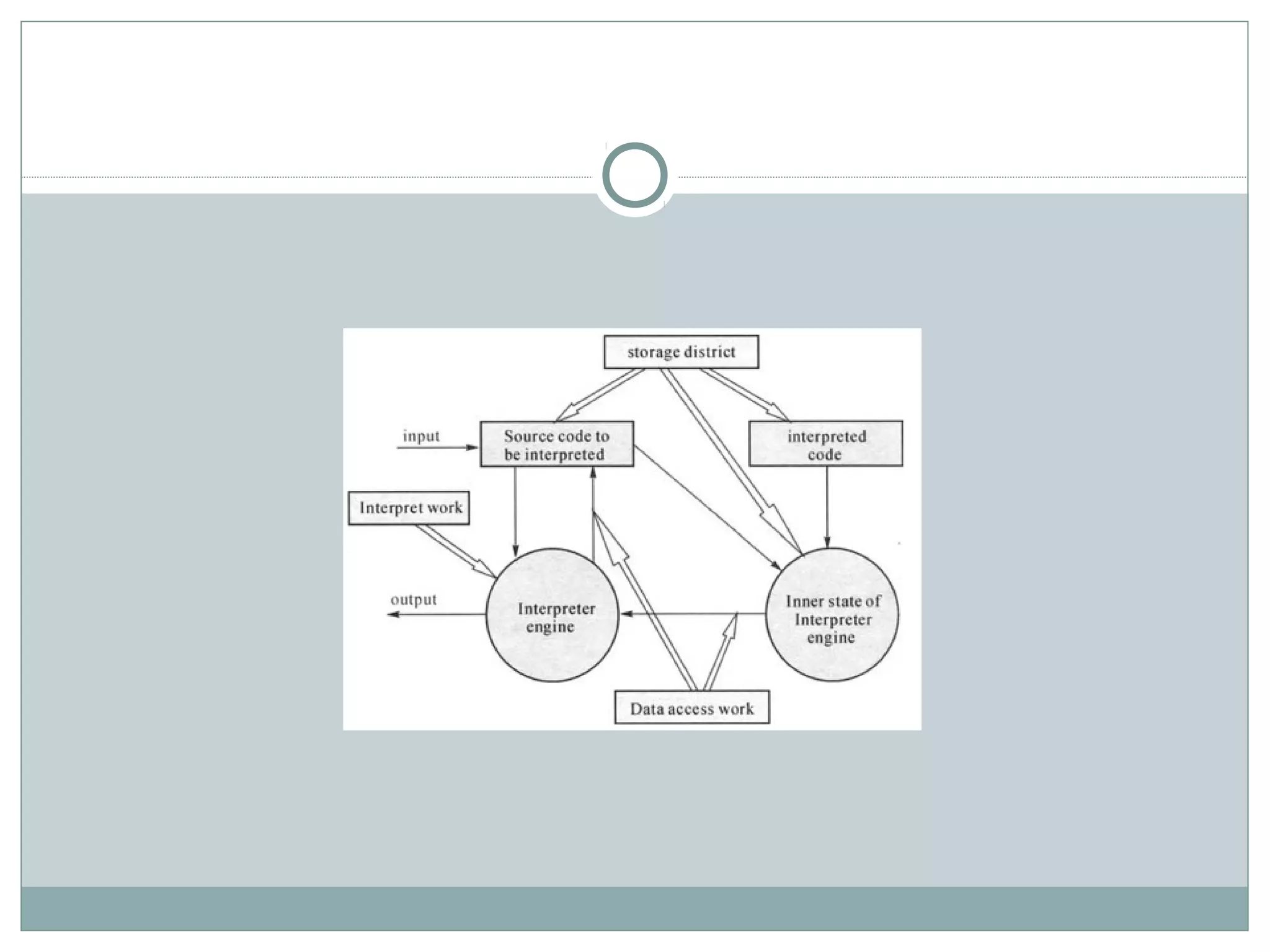
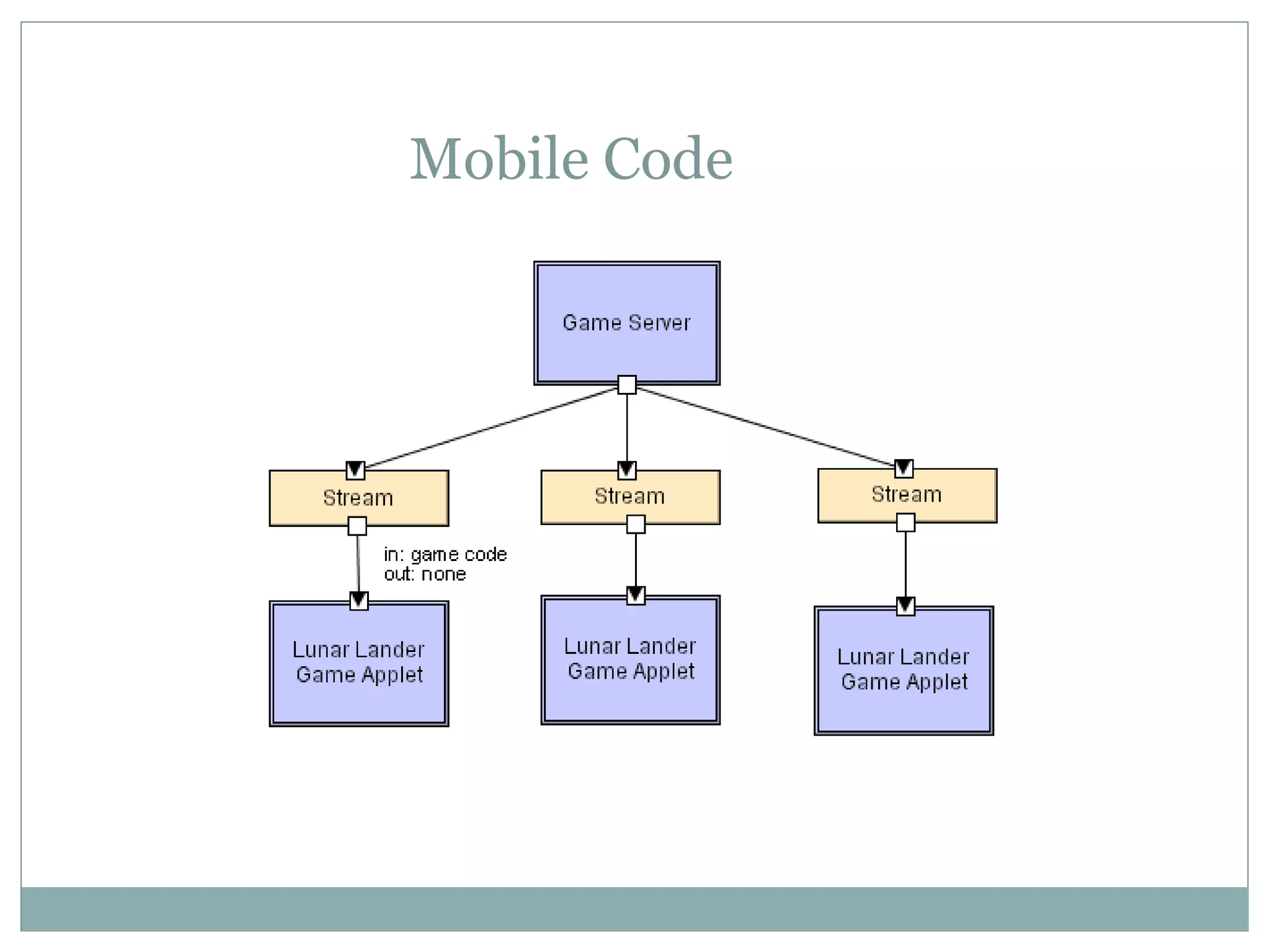
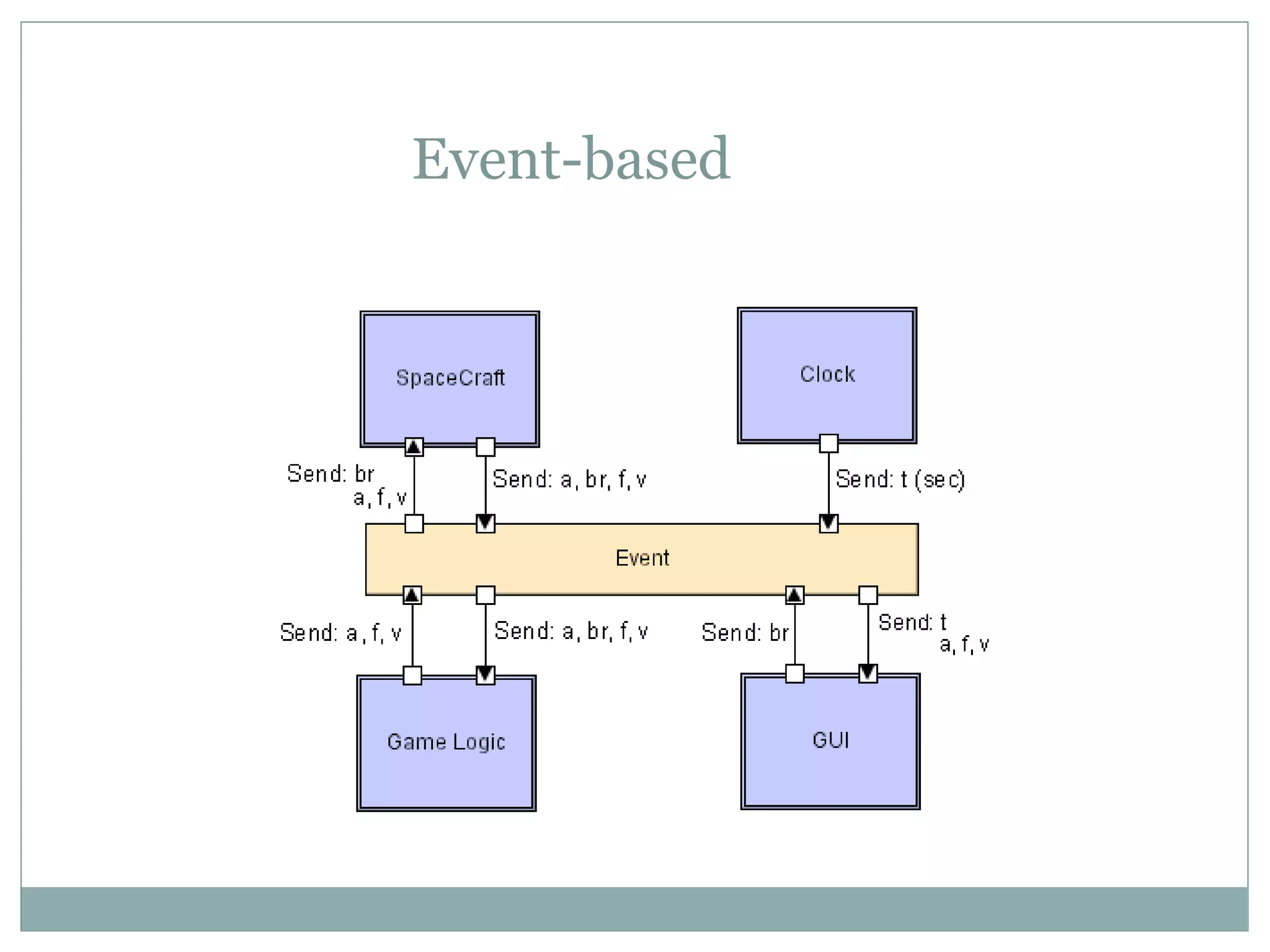
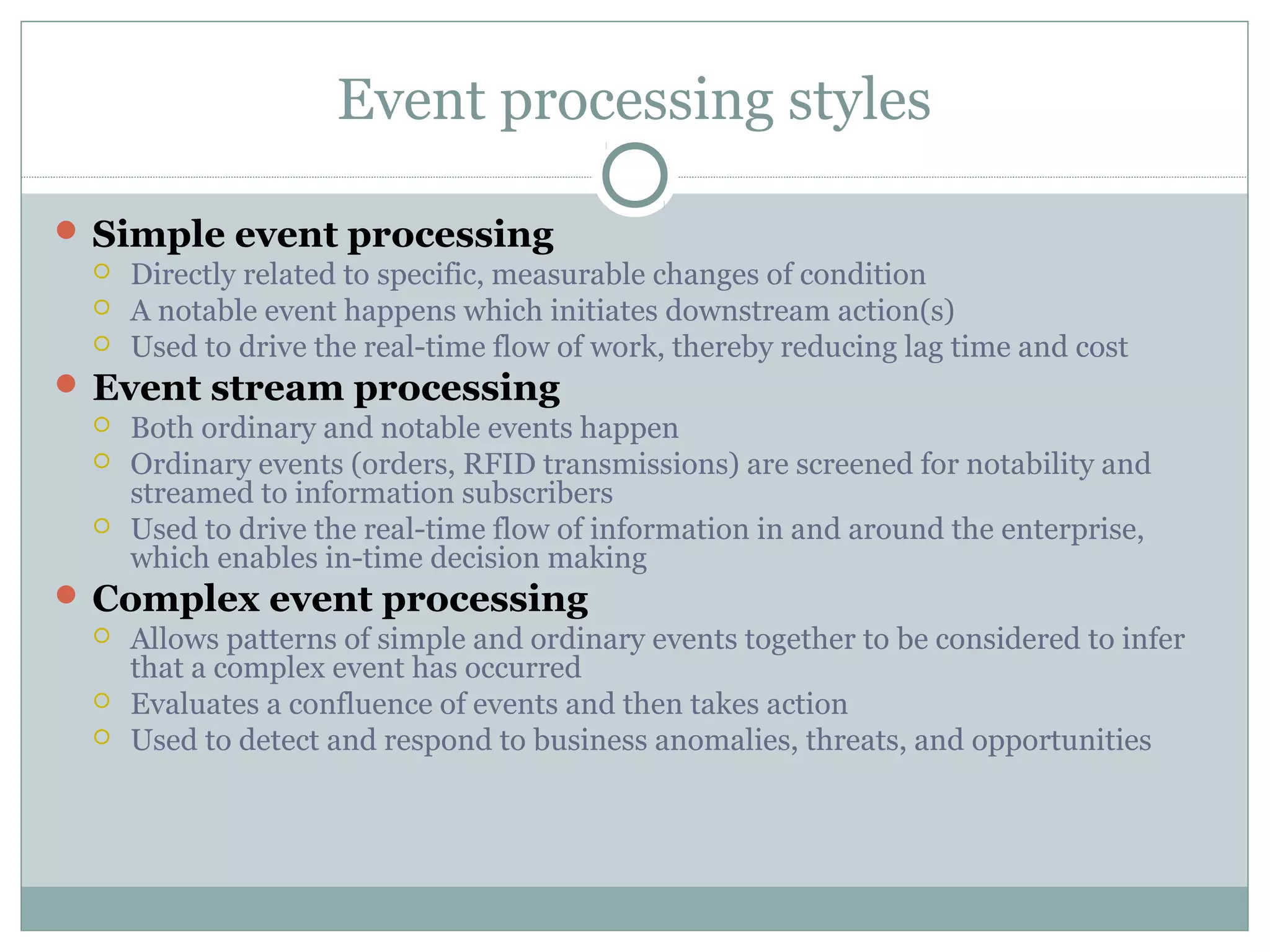
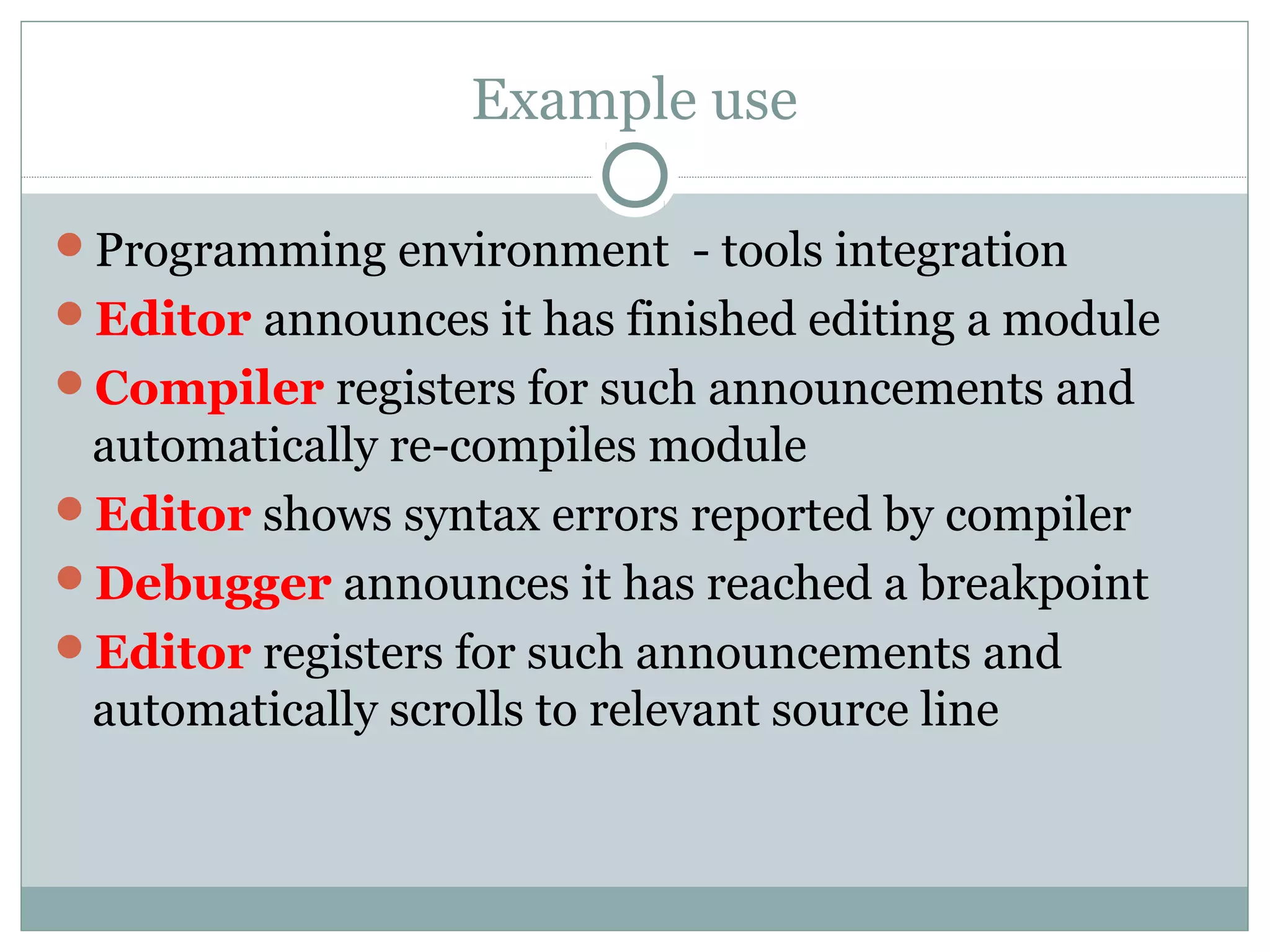
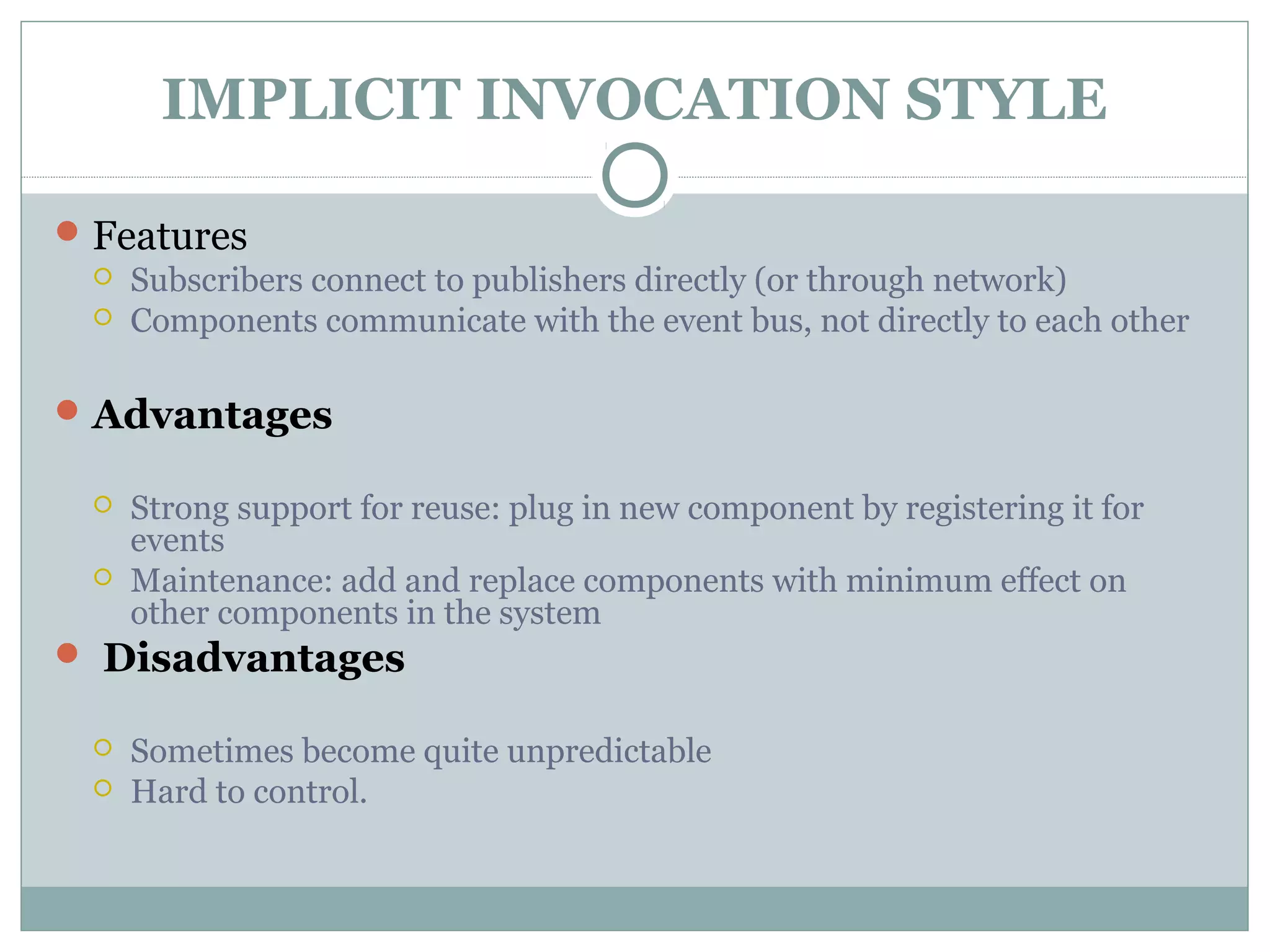
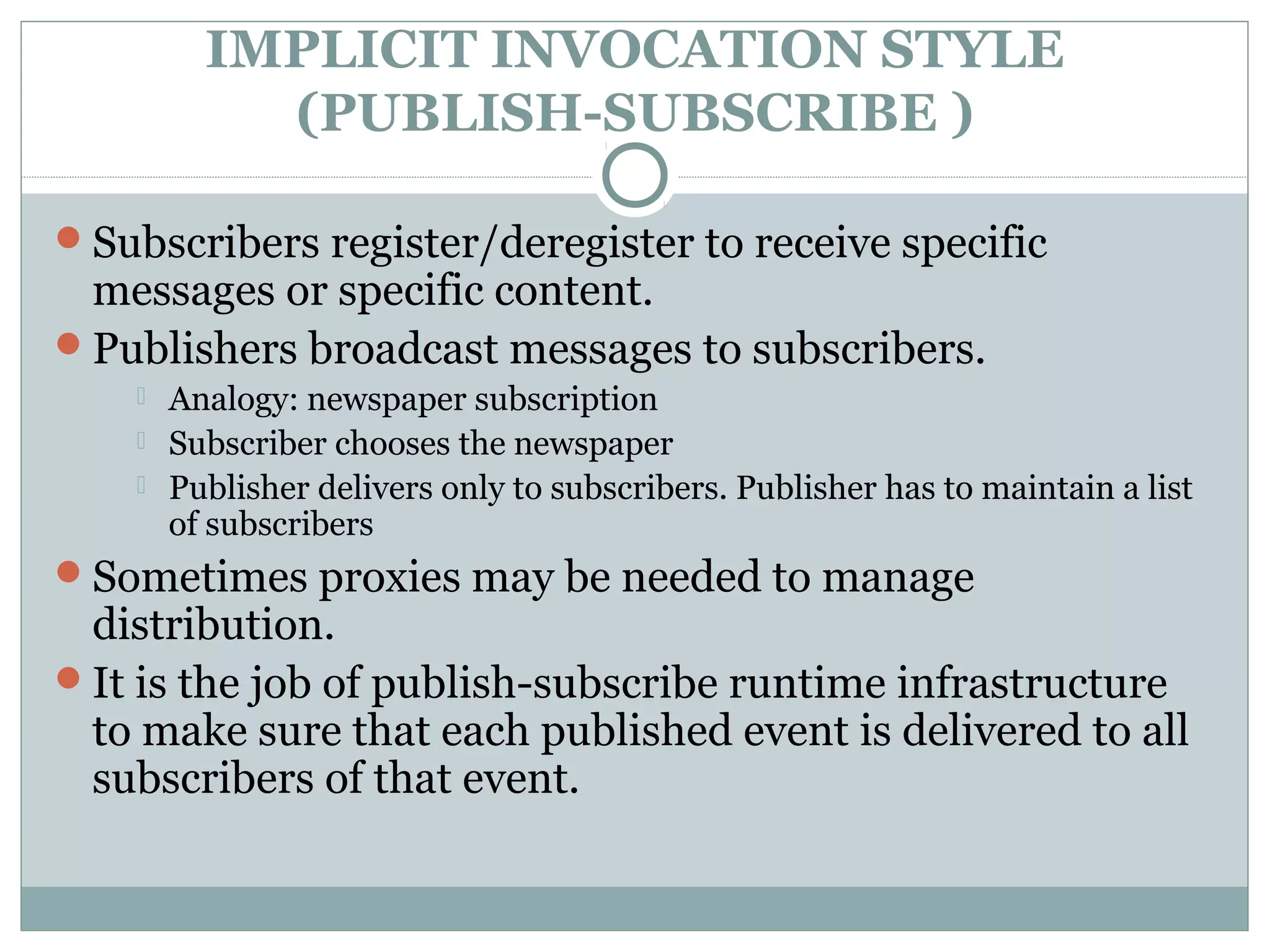
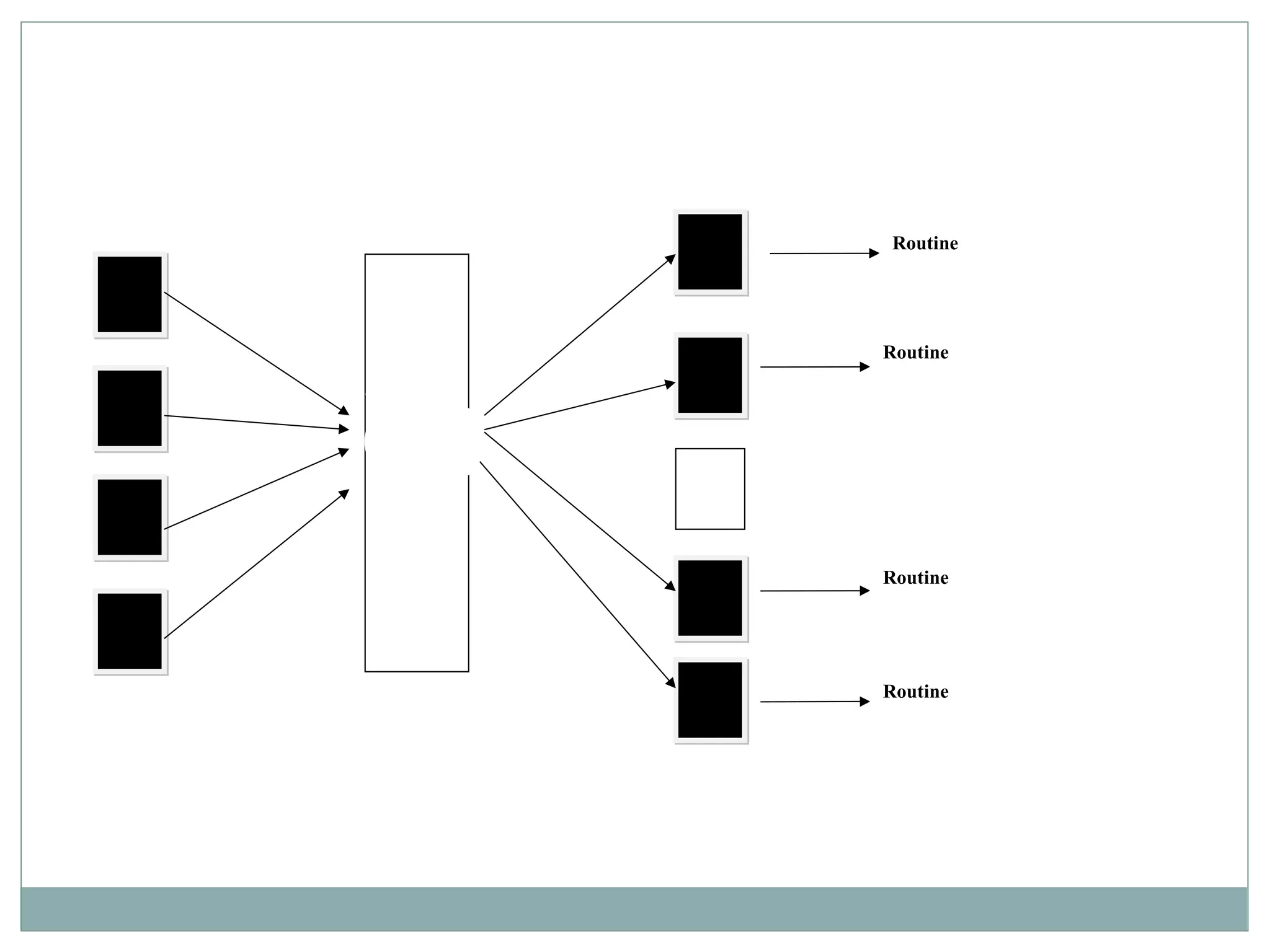
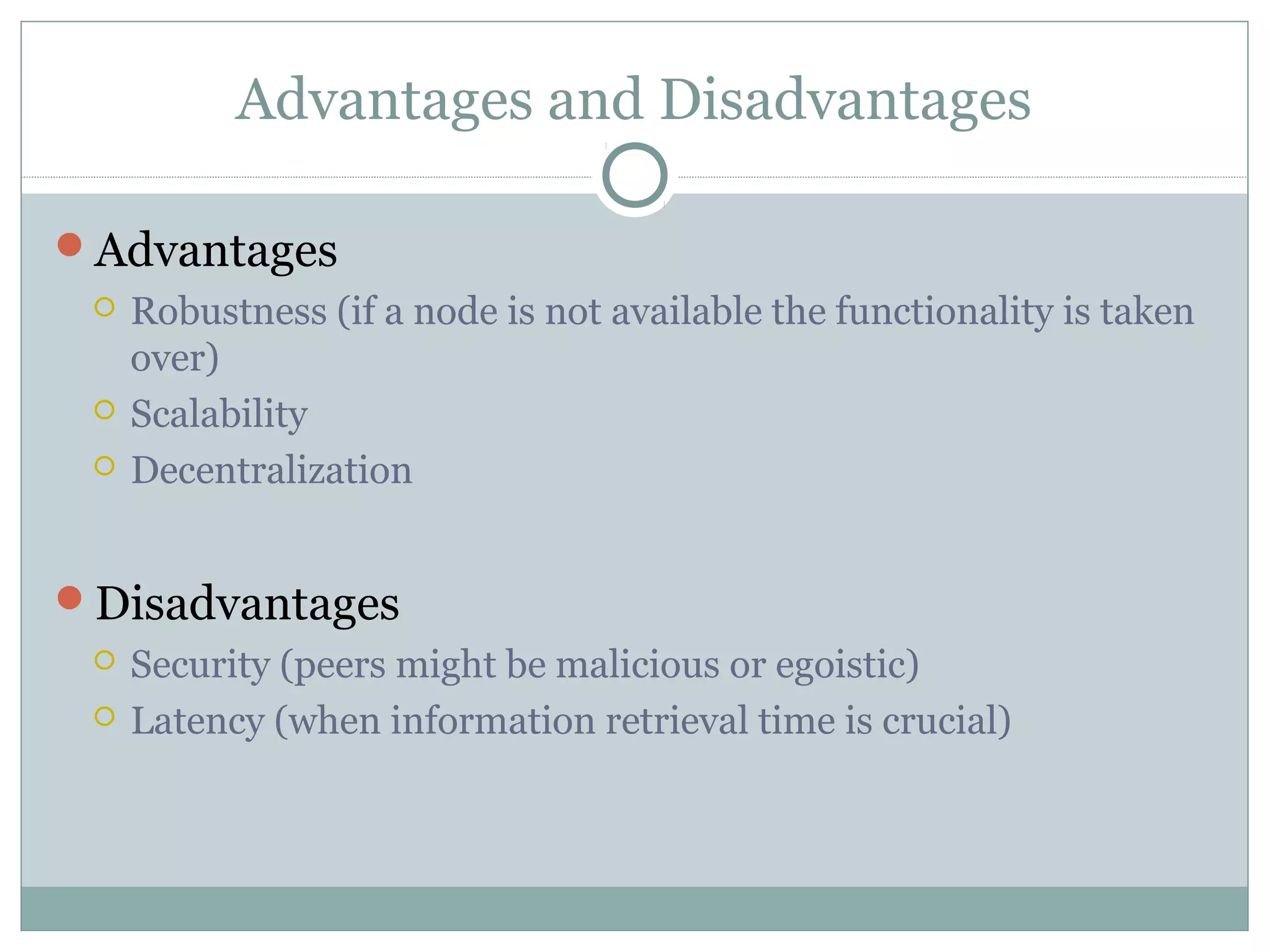
The document discusses various architectural styles used in software design. It describes styles such as main program and subroutines, object-oriented, layered, client-server, data-flow, shared memory, interpreter, and implicit invocation. Each style has different components, communication methods, and advantages/disadvantages for managing complexity and promoting qualities like reuse and modifiability. Common examples of each style are also provided.