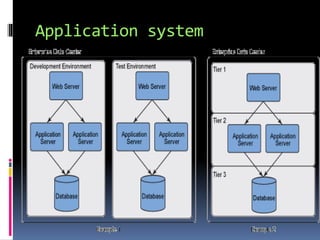
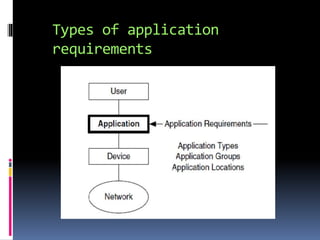
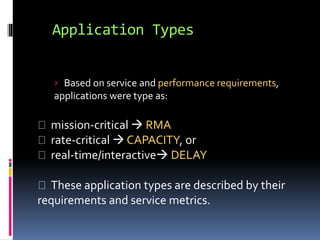
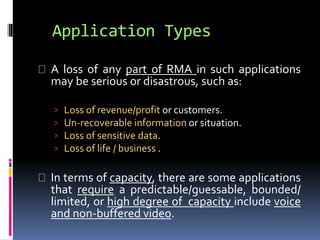
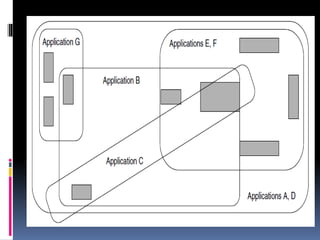
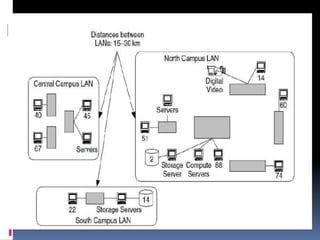
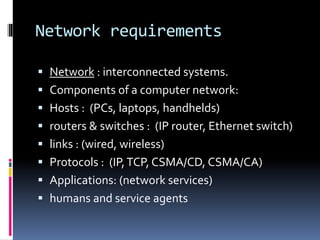
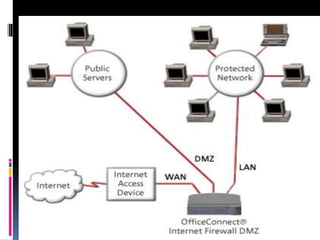
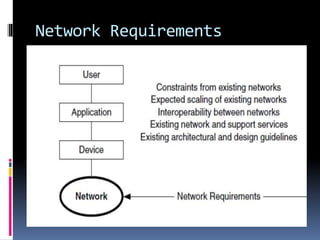
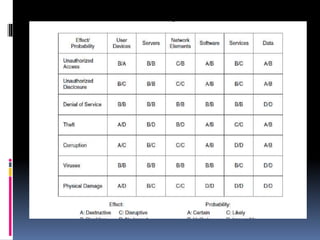
This document discusses application requirements for computer networks. It defines application requirements as requirements determined from application information, experience, or testing that represent what is needed by applications. It provides examples of different types of application requirements like web page requests, database transactions, messaging protocols, and API calls. It also discusses how to classify applications based on service and performance requirements into categories like mission-critical, rate-critical, and real-time/interactive applications. Finally, it describes the different tiers in an application system including the web, application, and database tiers.