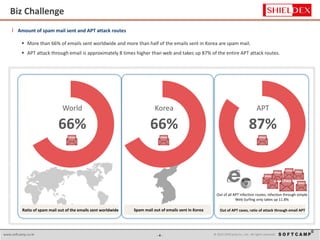
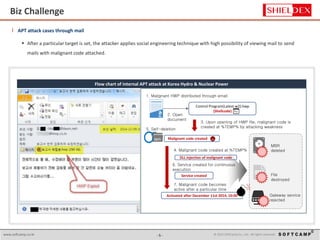
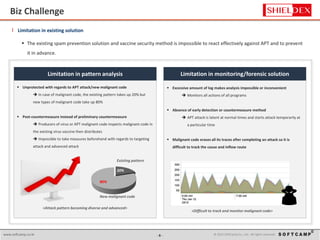
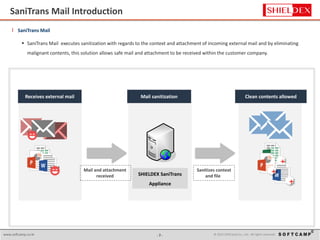
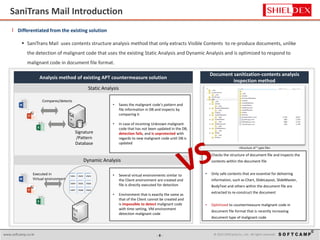
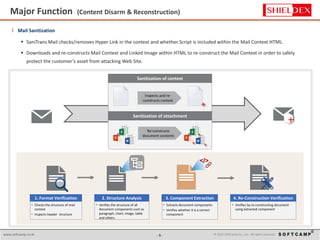
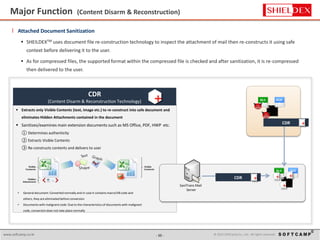
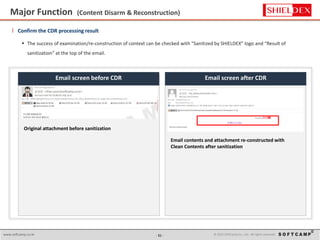
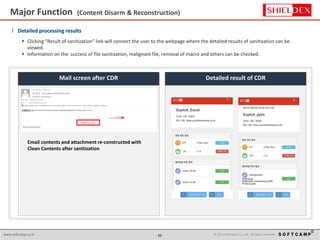
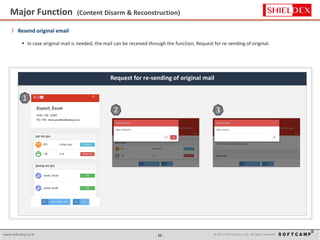
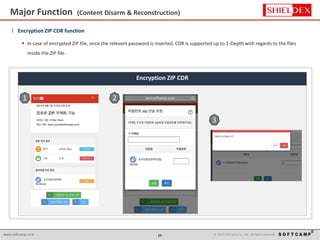
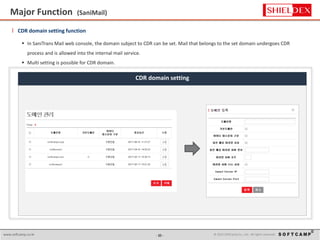
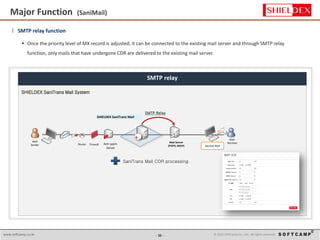
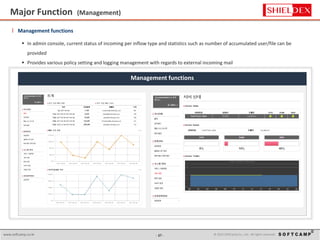
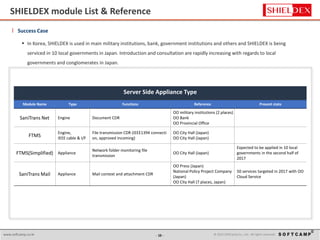
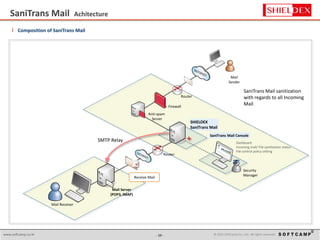
The document discusses the increasing threat of Advanced Persistent Threats (APTs) via email, highlighting significant attack instances from 2010 to 2012. It introduces Sanitrans Mail, a solution designed to sanitize email contents and attachments, thereby protecting organizations from malicious code. The solution offers advanced content disarm and reconstruction methods compared to traditional spam prevention techniques, ensuring the safe delivery of emails.